News Archive January 2014
![]() Written by Karolis Liucveikis on (updated)
Written by Karolis Liucveikis on (updated)
Table of contents:
- More Banking Malware
- NSA Quantum Computers Similar to Sci-Fi Novel
- Bitcoin Malware Affects Yahoo! Users
- New App Could Invade Your Privacy Anywhere
- Hackers Target Neiman Marcus
- New Versions of Zeus on the Rise
- Baby Monitors Easily Hacked
- The Media Isn’t the Only Group Attacking Obamacare
- The 'Mobile Surge' Unveiled
- Counterfeit Card Shops Reaching All-Time Highs
More Banking Malware
06.01.14
Security experts recently uncovered a new form of malware directed at banking customers. Unlike many of the banking related scams previously covered on this blog, this new threat is not a phishing scam. Instead, this program installs adware that automatically injects advertisements into search results. The software supposedly comes from Trust Financial Group; a small company located in Oklahoma. The handful of financial professionals actually associated with the Trust Financial Group are not suspected in this malware attack. Rather, it appears that hackers are using the name of a real financial institution to encourage users to download software that appears to be legitimate.
Users that visit the compromised URL hxxp://trustfinancial.org are discreetly redirected to a page showing a blurred version of a loan document. Users are then prompted to download special software to view the loan document. The malware has appeared in Windows Installer as “Search Smarted and Search Assistor” and “Secure Documents Viewer.” Both versions are signed by a verified publisher known as Access Financial Solutions. All of the domain names associated with this scam are registered anonymously so it is unclear who is behind this attack so far.
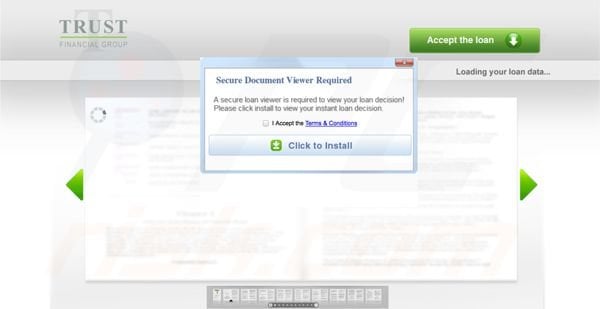
The only other information available at this time is that the ads originate from a domain known as hxxp://ez-input.info. Although the primary focus of the malware appears to be advertisements, this software could have other purposes as well; many of which may not currently be active.
Botnets, for instance, are commonly distributed as less serious forms of malware that lie relatively dormant until called upon by the hackers in control of the malware.
This scam is especially disturbing because it focuses on the financial system. By using financial companies (whether real or created), the hackers can overcome some of the skepticism normally practiced by Internet users. The fact that the software is signed by a verified publisher is also concerning as most malware does not share this important characteristic. Make sure your anti-virus software is up-to-date as this malware variant is detected by most current virus definitions. If the malware is not detected by your AV software, look under Programs & Features for an application known as Best Tool Bar or similar.
Uninstalling this application should remove the adware without any residual effects; however, the full reach of this adware attack is still unknown and further complications could arise in the future.
As usual, do not download any software program that you do not need or from a company that you do not currently do business with. Make sure your computer has the latest AV and OS updates to further protect your machine from this threat.
NSA Quantum Computers Similar to Sci-Fi Novel
08.01.14
As information from infamous NSA whistleblower Edward Snowden continues to destroy the reputation of the NSA, this latest leak is reminiscent of a popular Dan Brown novel in which the NSA has a secret supercomputer capable of cracking any encryption algorithm in the world. In the book, the NSA denies the existence of any such machine, but hidden underground lies a massive supercomputer cooled by freon gas that can decipher even the most complex encryption algorithms in a matter of minutes. In this case, it appears that the truth is very close to the fiction. Recent leaks prove that the NSA has spent at least $80 million researching and developing a quantum computer capable of breaking any code.
This means email encryption programs, passwords and personal information would no longer be safe from the prying eyes of the US Government. A quantum computer is capable of processing information much faster than a conventional binary computer. Traditionally, computer code is a combination of “1s” and “0s” that instruct the computer. In a quantum computer, however, information can be stored as a “1”, “0” or any other state in between. The amount of data a quantum computer can consume is astronomical compared to the binary machines currently used by most people.
Armed with a quantum computer, the NSA (which is already tied into the Internet backbone) could easily intercept and read any and all transmissions from practically anywhere in the world.
Corporate, government and private communications would have no protection against a computer powerful enough to break any algorithm in such a short period of time. Of course, the NSA argues that such technology is required to prevent terrorist attacks and similar tragedies.

That said, it was only a couple months ago that documentation was revealed proving that NSA employees were spying on their significant others using the tools and information available within NSA headquarters. As usual, the truth lies somewhere in the details.
Although the documents leaked by Snowden do not indicate how far into this process the NSA actually is, anybody’s guess is good right now.
It could very well be that the NSA already has this technology up and running. After all, quantum computers are already available. Google, Lockheed Martin and NASA already own quantum computers purchased from D-Wave Systems for $10 million dollars each.
The NSA claims that these machines are not powerful enough for cryptographic duties, but most people aren’t taking the NSA’s word for anything these days.
If it hasn’t happened already, the addition of quantum technology to the NSA arsenal is sure to come. When that day arrives, there is nothing that will protect communications (both personal and professional) from the eyes of government unless the same quantum technology can be applied to encryption algorithms in the future.
Bitcoin Malware Affects Yahoo! Users
09.01.14
Bitcoin is a cryptocurrency that first gained notoriety as the payment method of choice for hackers and other cyber criminals. This blog has documented the extensive use of Bitcoins on The Silk Road (an underground drug marketplace that has since been taken down by the FBI), but it seems that Bitcoins are still on the rise. Even mainstream media sources such as CNBC have been watching the Bitcoin rise in value to a high of nearly $1,200 USD each in recent months. Currently, Bitcoins are worth approximately $845 USD each. One of the things that makes Bitcoin an attractive alternative currency is a lack of regulation. Anyone can create Bitcoins through a process called mining. Mining uses a computer (or specialized processors designed exclusively for mining) to solve complex mathematical algorithms. Once the algorithm is solved, that machine earns a block of Bitcoins. The problem is that as Bitcoins are released, the algorithm to get more becomes increasingly more difficult.
At this point, it is very difficult for most people to successfully mine Bitcoins without investing millions of dollars in equipment. At least that was the case until a hacker developed a malware variant that turns infected machines in Bitcoin miners. Hackers have realized that it is far less expensive to use the joint computing power of other people’s machines to mine Bitcoins. Between equipment costs and power consumption, a legal mining operation can cost thousands of dollars per month to be successful. You can think of this malware as a botnet designed to create Bitcoins rather than DDOS attacks and many of the more common uses of botnets that occur regularly.

It appears that the popular search engine Yahoo! was recently compromised by this malware. Hackers were able to embed the malicious code in advertisements served from Yahoo’s European site. Over 1 million computers have been infected with this mining malware. Since the mining process is so processor-intensive, many infected computers are practically useless while the software is discreetly running in the background.
Most antivirus programs can detect this malware variant; although AV software that has not been updated recently may not catch it during installation.
There are quite a few IP addresses associated with this mining operation - all of which should be blocked through your firewall or router as well. Some of these IP addresses include:
hxxp://goodsdatums.in
hxxp://locationmaking.in
hxxp://mejudge.in
hxxp://operatedalone.in
hxxp://blistartoncom.org
hxxp://doesexisted.in
hxxp://formsgained.in
hxxp://funnyboobsonline.org
Although this form of malware is unlikely to steal personal information like so many others, an infected computer could be completely unusable while a mining operation is underway.
Most mining programs use the computer’s video card (GPU) to calculate algorithms and this can lead to video card failure relatively easily.
As usual, make sure your AV software and OS are fully updated to prevent infection from this malware variation. Slow performance may be the only indication of infection and steps should be taken to remove this threat as soon as possible.
New App Could Invade Your Privacy Anywhere
11.01.14
A new mobile application has been released that could invade your privacy no matter where you are or what social media privacy settings you have in place. NameTag is a revolutionary application created by FacialNetwork.com. The app relies on powerful facial recognition software to provide information to app users instantly using a smartphone or the increasingly popular Google Glass. When the app spots a person using the camera already included with practically every smart device, the facial recognition software kicks in and immediately matches the “target” individual with any relevant social media information including contact information, interests, hobbies, passions and practically anything else you can think of.
Although the app is very interesting and the creators say NameTag could turn social media upside down, the problem is that there is no way for people to opt out of this latest privacy breach...unless, of course, you use NameTag to opt out. Everyone else is at the whim of anyone using this software. Many privacy advocates are concerned that this app could be used by less-than-ideal people.
In some circles, the app is already being referred to as “the stalker app” because complete strangers can find out a lot of personal information just by taking your picture.
The creators of the app, however, argue that the information presented to NameTag users is publicly available information that is not protected by any current domestic or foreign laws. Currently, most of the data is mined from social media sites including Facebook, Twitter, Google+ and LinkedIn; however, FacialNetwork is working to incorporate data from popular dating sites including Plenty of Fish, OK Cupid and Match.
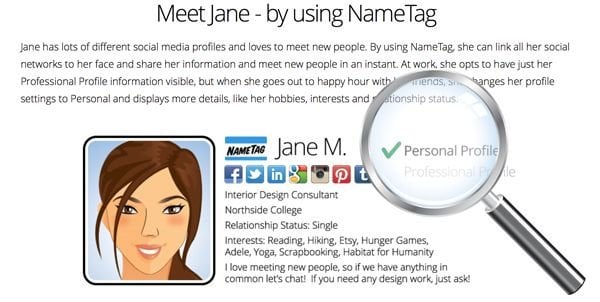
It seems that very few people (if any) will be completely safe from the prying eyes of anyone using the NameTag application. Keep in mind that a beta version of the app has been released for Google Glass, but the iOS and Android variations are still under development. Interestingly enough, Google officially does not support facial recognition in Google Glass (yet). Despite this, FacialNetwork developers have made it work and there doesn’t seem to be any limit to the definition of social media anymore.
If you want to protect yourself from a privacy invasion, the only thing you can do right now is create a free NameTag account and opt out completely or at least limit the information available to other app users.
As this technology becomes more mainstream, some form of legislation will likely be needed to keep “stalkers” and other unscrupulous people from abusing the publicly available information provided by NameTag and other facial recognition applications still under development. Remember, anything you post online is easily accessible in most cases. Probably the best preventative measure is to monitor carefully everything you post online because it might just come back to bite you thanks to NameTag and its powerful facial recognition algorithm.
Hackers Target Neiman Marcus
13.01.14
Just as the Target credit card theft case comes to a close (where approximately 40 million credit card numbers were stolen during the holiday shopping season), it appears that the high-end retail store Neiman Marcus is now in hot water with customers for a similar breach. Earlier this week, the retailer announced it was working with the US Secret Service to track an apparent security breach that has unknown consequences as of this writing. What is known is that sometime in mid-December Neiman Marcus was made aware of potentially unauthorized transactions by its credit card processor. After notifying law enforcement officials, the retailer also began a private forensic investigation to uncover the compromise and thwart any future losses as a result of this theft.
At this time, Neiman Marcus has not released any information about the number of customers who may be affected by this breach, but some credit cards were fraudulently used shortly after customers made legitimate purchases at Neiman Marcus stores around the country. The private forensic investigation team hired by Neiman Marcus Group has already made information security changes to limit further theft; however, it is unclear at this time (based on the Neiman Marcus Group official statement about the incident) what actually caused the breach. In fact, the official statement does not even confirm that the breach has been fixed at this time.
If you have shopped at Neiman Marcus any time in the last year, it is advisable to check your credit card statements for any signs of fraud – at least until more information about this breach is made publicly available.
Although there is no evidence to suggest the same hackers responsible for the Target attack covered on this blog last month are responsible for the Neiman Marcus breach, both attacks did occur at the same time.

Both attacks focused on the credit card information of retail customers in large department stores and just like the Target attack, it seems that Neiman Marcus was completely unaware of the breach until the company was notified by the credit card processor that suspicious activity might be occurring.
As convenient as plastic has become as a payment medium, these attacks prove that the existing payment processing system is still lacking basic IT security functionality.
Perhaps even more alarming is that affected retailers do not seem overly concerned about fixing these issues. Since the infamous TJX credit card theft a few years ago, retailers should be more concerned about the integrity of their networks, yet they continue to put consumer financial information at risk.
If you have shopped at Neiman Marcus and notice any suspicious charges, contact your card issuer right away to report the fraud and prevent further financial loss.
Unfortunately, this wave of theft is outside the consumer’s control. The only real way to protect your financial information while shopping is to pay with cash; something that many people simply do not practice anymore.
New Versions of Zeus on the Rise
15.01.14
Zeus is a dangerous banking Trojan designed to record the keystrokes of unsuspecting users while they log into secure sites including online bank and credit card accounts. The username and password combinations are then sent to hackers who can quickly clean out these accounts (usually by wiring the funds to Russia or the Ukraine). This blog has covered Zeus in the past, but it appears a new version of this dangerous malware is on the loose. Although the actual malware is relatively unchanged, hackers have been looking for new ways to trick potential victims into downloading the software. One of the most popular attack methods is known as drive-by downloading. This refers to a compromised website using known vulnerabilities in Java to install malware such as Zeus without the knowledge or consent of the user. Specifically, the Blackhole exploit kit is often used to drop Zeus on a computer.
Blackhole targets hundreds of vulnerabilities in Java and if one is found, Zeus is instantly loaded into the machine. Lately, hackers have also started using the BitDefender name to disguise the malware as a popular antivirus product. Although hackers often spoof known brands to attract victims, the BitDefender spoof is unique because it represents a significant spike in malware circulating the Internet.
In the last two weeks alone, over 40,000 unique Zeus files were discovered throughout the Web; most of them hosted on US-based websites that have been hijacked using simple website exploits to gain access to servers.
In addition to spoofing BitDefender antivirus products, hackers have also been using a spam email campaign with Zeus attached as a download or by directing users to a website where Zeus is hosted. Many of these spoofed emails appear to come from popular retailers including Wal-Mart, Costco and Best Buy.
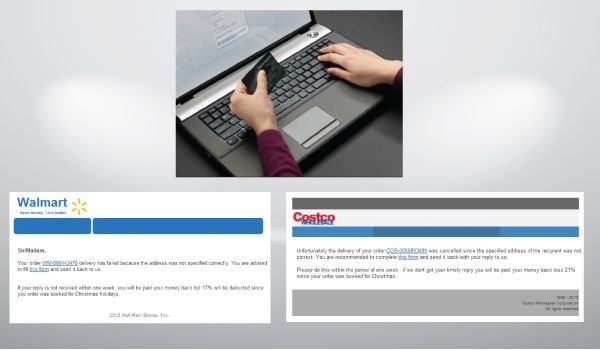
The attachment will often come as a zip file with an executable (.exe) file embedded in the zipped folder. Many email clients (such as Gmail) block the transmission of any .exe file within Gmail, but other email clients do not have these protections in place.
Never download or install anything via email or the Internet without trusting the source completely.
A Zeus infection can be difficult to detect and even more difficult to remove. The malware is known to disable Windows Firewall and Security Center; potentially opening up the computer to further attack. Zeus was specifically designed to hide from antivirus software, but most reputable AV solutions provide protection from most Zeus flavors. Nonetheless, bank accounts often do not have the same consumer protections against fraud normally associated with credit cards. This means the loss of your savings or checking accounts could be permanent because of a Zeus attack. Make sure your AV software is fully updated. Also, remember to check your OS for critical system updates that may protect against many of the exploits used to install Zeus in the first place.
Baby Monitors Easily Hacked
21.01.14
A software vulnerability has been discovered that allows hackers to access webcams, IP surveillance cameras and even baby monitors. The vulnerability enables remote viewing of cached and live video footage as long as the hacker knows the IP address of the device. All affected devices are manufactured by Foscam, a Chinese company that manufactures millions of these products every year. The issue was discovered earlier this week after camera experts discussing hardware on Foscam’s support forum realized that the web interface for many of these products can be accessed simply by clicking “OK” when prompted for a username and password. News of web cameras being hacked through vulnerabilities in Flash and Java are nothing new, but this exploit is different because surveillance cameras and baby monitors are also affected.
The implications of this glitch are potentially far-reaching and alarming. The company’s tech support division has confirmed that the bug exists in all Foscam MJPEG cameras running the .54 version of the firmware.
Foscam stated publicly that it plans to release an updated software version (.55) later this week addressing this vulnerability; however, this firmware needs to be flashed to the device.
Unfortunately, this remains a confusing task for many users not accustomed to manually updating flash based devices. At this time, models that are known to be affected by this vulnerability include: FI8904W, FI8905E, FI8905W, FI8906W, FI8907W, FI8909W, FI8910E, FI8910W, FI8916W, FI8918W, and FI8919W. Beta versions of .55 have already been released and apparently there is a problem with the firmware installation freezing during the update process. This is bad news for everyone; especially less tech-savvy individuals who may have difficulty completing the update at all barring a revised release from Foscam.

A camera enthusiast has posted a workaround for this vulnerability until the official firmware update is released later this week. This individual advises that could result in the camera freezing if too many failed login attempts occur; leaving the camera useless until it is power cycled manually.
The news of this vulnerability comes on the heels of another Foscam vulnerability discovered last summer. During that incident, a hacker reportedly gained access to a baby monitor and began shouting obscenities at a sleeping toddler.
Prior to that, webcams manufactured by TRENDnet were also found to be vulnerable to a similar attack. Although these attacks require hackers to know the exact IP address of the device, there are tools available throughout the Internet that help locate IP addresses not normally listed in search results. SHODAN, for example, is a specialized search engine useful for locating devices not typically indexed by search engines like Google and Yahoo.
If you currently use one of the models affected by this vulnerability and you are concerned about the privacy of your family, the best course of action is to disconnect the camera from the network.
Once the official update has been released and verified as working properly, instructions for the update process can be found on Foscam’s support website.
The Media Isn’t the Only Group Attacking Obamacare
22.01.14
It’s no secret that healthcare.gov, the site responsible for signing citizens up for the Affordable Care Act, has been under fire since its launch. The site has been plagued with design flaws that have literally crippled the site on many occasions; prompting an onslaught of criticism from citizens and the media alike. Recently, a computer security consulting firm testified before Congress. The same firm also testified last year when the site first went live. In this testimony, the focus was on the fact that out of 20 blatant security flaws uncovered last year, only half of one has been addressed. In other words, it’s “business as usual” according to TrustedSec CEO David Kennedy. At the time of this writing, there are approximately 40 potentially dangerous security flaws associated with healthcare.gov and the government has done little to nothing to address these potentially serious security concerns.
Another security expert, Ed Skoudis, was quoted as saying that the healthcare.gov site “is a breach waiting to happen.” He went on to say that the types of vulnerabilities present are the exact security flaws usually targeted by large hacking groups when conducting large scale breaches. In fact, experts agree that a breach may have already happened, but cannot confirm whether or not a breach has occurred at this time. There two primary security flaws in the website’s design.
One vulnerability could allow hackers to steal sensitive personal information directly from the site database while the other exploits the the trusted connection between client machines and the server hosting the site.
The second vulnerability could leave visitors’ machines susceptible to remote access. Data loss, identity theft and malware-infected computers are all possible because proper IT security procedures were ignored in the government’s rush to get the site live in time for last year’s enrollment period. Perhaps most disturbing is the fact that the government has been aware of these flaws for months and yet still has not taken action to correct these potentially dangerous issues.

Despite the outcry from security experts throughout the country, the Centers for Medicare & Medicaid Services (CMS) maintains that the core functionality of the site meets or exceeds the standards set forth by the Federal Information Security Management Act; however, it is unclear what CMS meant by “core functionality,” how data is managed after a secure user session or if any steps have been taken to rectify potential issues brought to light in Congress hearings. The delicate nature of the information shared on this site as users enroll in various healthcare plans is certainly a concern. As the government continues to ramp up surveillance efforts, it’s interesting that the security of citizens’ personal information is such a low priority.
Until these vulnerabilities have been addressed, be extremely vigilant while using the site, make sure all OS, web browser and add-ons are updated and verify the functionality of your antivirus solution.
Also, keep a close eye on bank statements and your credit report for unusual activity; especially if you have used this site to enroll in a health plan already.
The 'Mobile Surge' Unveiled
25.01.14
The latest secret documents released by NSA whistleblower Edward Snowden show just how far the NSA and other international agencies are willing to go when collecting personal data from unsuspecting citizens. In a program referred to as the “mobile surge,” the NSA and even Britain’s Government Communication Headquarters have been collecting personal information from users of popular mobile applications including Rovio’s Angry Birds, Google Maps, Facebook and Twitter. Although it has long been suspected that government agencies snoop through social media sites, these latest reports prove that even playing your favorite iOS or Android game could provide the NSA with a lot of information you probably don’t want to share with just anyone.
Age, location, daily habits, contact lists and much more are accessible using backdoors in these popular applications. While the NSA is accustomed to taking heat for some of its questionable practices, it’s interesting that these documents reveal a distinct cooperative effort between the NSA and the British government. In fact, it appears the two agencies were actually trading “recipes” for collecting information from various sources commonly referred to as “leaky apps.” The leak also demonstrates some fatal flaws in popular mobile operating systems. Android, for instance, uploads approximately 500 lines of collectable data into the network every time the OS is updated.
Although it is unclear what this data is actually used for, the mobile surge demonstrates that government agencies around the world are capable of piecing together the lives of civilians using data mined from mobile apps.
Location data from Google Maps, contacts and associates from Facebook and Twitter...the list goes on and on. The documents released by Snowden prove that the NSA collects data from all Americans; not just “persons of interest.” Even though the documents do not disclose the exact methods used to extract information from leaky apps, one of the most heavily used techniques appears to be cookies.

Cookies have been used for years on Internet-connected computers as a way to track users as they move throughout the Internet. The leaked documents do not mention any knowledge, involvement or cooperation on the part of mobile app creators. Rovio recently made a public statement denying any and all prior knowledge of these activities; despite the company’s breakout game Angry Birds being one of the apps specifically mentioned in the NSA documents. Seemingly unrelated, however nearly as alarming, is Rovio’s own data collection policies. The company targets in-game advertisements based on ancillary data harvested from the smartphone or tablet where the app is installed. Is it possible that the NSA has a backdoor into this very same data stream? Unfortunately, it is unclear at this time.
This program has been in effect since 2007 - well before smartphones became the mainstream devices of today. The report mentions that in a one month period, collected cell phone data produces over 8 million ‘people of interest’ and uses the combined computing power of at least 120 machines to process this information every month.
There is no way to protect yourself from these data collection policies other than to power off your mobile device altogether. President Obama recently called for NSA reform but cautioned that it could be years before any real changes are realized. As a result, the government will continue to spy on Americans using any means available...keep this in mind next time you log into your favorite mobile app.
Counterfeit Card Shops Reaching All-Time Highs
26.01.14
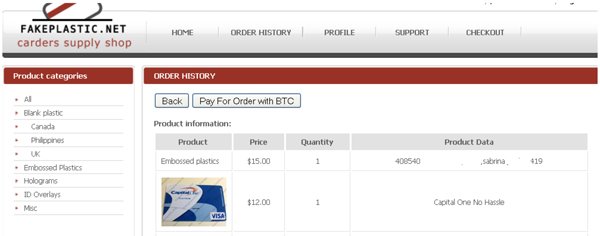
Federal authorities recently announced the arrest of 14 individuals suspected of operating a fraudulent credit card marketplace known as hxxp://fakeplastic.net. The leader of this website is Sean Roberson, a 39-year-old Florida man. In addition to selling high-quality counterfeit credit and debit cards, the site also offers holographic overlays used to create fake driver’s licenses. The FBI and US Postal Investigative Service have been investigating hxxp://fakeplastic.net since last year, but only recently gained access to the site’s server and discovered how the service actually works. The Postal Investigative Service became involved when it was discovered that counterfeit cards were being shipped via USPS delivery using a Click-n-Ship account registered to “Sam Adams.” The site has been selling stolen credit card information since April 2011.
Services offered by Roberson’s business included both embossed and unembossed credit cards, holographic stickers used to make counterfeit cards look more legitimate and over 35,000 holographic overlays used to create counterfeit driver’s licenses. In total, over 36,000 packages were sent via USPS to customers around the world. Federal statutes dictate that each stolen card carry an estimated value of $500. This equals almost $35 million in stolen funds in less than three years. It is estimated that Roberson pocketed close to $1.7 million from hxxp://fakeplastic.net since 2011.
Cash out crews are criminals using counterfeit debit and credit cards to make ATM withdrawals or purchase items directly at retail locations.
The specialized equipment needed to create realistic looking cards is extremely expensive, but services like fakeplastic have made it easy for criminals to purchase authentic-looking credit cards with stolen information encoded into the magnetic strips. This stolen information is usually obtained using a technique known as skimming. Recently, a multi-million dollar skimming operation was uncovered in the Southeast when multiple RaceTrac gas stations were infiltrated by a group of skimmers using high-tech bluetooth devices hidden in gas pumps.
These devices are capable of recording the magnetic strip data from any card used for “pay at the pump” services. The data is later collected by the hackers and sold to services like fakeplastic.
This skimming scam is estimated to be responsible for over $3 million in fraudulent charges and there are many others like it around the world.
The decreasing costs associated with manufacturing skimming devices has put services like Roberson’s in high demand. It seems that as quickly as the FBI takes down one site, five more just like it arise to fill the void in the market. Many of these sites are based outside the US (in areas of Russia and the Ukraine specifically) which makes prosecution difficult at best. Avoiding financial loss is nearly unavoidable as most skimming devices are not easily detected; however, you should never enter your PIN for a debit transaction unless absolutely necessary.
The PIN is also recorded by skimmers and can be used by cash out crews to empty checking and savings accounts via ATMs - arguably a more serious financial burden than fraudulent credit card charges that are easily reversed once the fraud has been detected.
The fact that sites like hxxp://fakeplastic.net still exist demonstrate that credit card fraud is on the rise despite efforts by law enforcement to thwart these activities using any means necessary.

▼ Show Discussion