News Archive August 2014
![]() Written by Karolis Liucveikis on (updated)
Written by Karolis Liucveikis on (updated)
Table of contents:
- Cryptolocker Finally Decrypted for Free
- Unsecured Remote Access Tool Leaves Millions of Computers Vulnerable
- New Malware Variation Hides Exclusively in System Registry
- Hackers Use Ebola Virus to Lure Victims
- Backoff - A Dangerous POS Malware Strain
- Old (but powerful) Malware Updated with New Tricks
Cryptolocker Finally Decrypted for Free
02.08.14
This blog has covered the assorted iterations of powerful ransomware in detail. While there have been many dangerous variations in the last several months, few (if any) have been as damaging and feared as Cryptolocker. Originally spotted nearly one year ago, Cryptolocker is a type of malware that uses extremely strong encryption to lock files and folders on a victim’s computer. Infected machines typically display a warning to users that their files have been locked and can only be retrieved by sending money — usually in the form of Bitcoins — to the hackers behind the scam. Victims are usually only given approximately 72 hours to comply before the ransom doubles or even triples. Unlike many malware variants, Cryptolocker and similar ransomware programs cannot be removed without the encryption key. In other words, no antivirus software or malware removal tool can help unlock the files.
This means even computer-savvy individuals can do nothing to save important files and folders without forking over a ransom which is often hundreds of dollars or more. For those victims who were unwilling or unable to pay the ransom after infection, the wait is over. Two security firms — California-based FireEye and Fox-IT in the Netherlands — have come together and created a new website called decryptcryptolocker.com. By providing an email address and just one of the encrypted files to this new website, the service will email a link that victims can use to download a recovery program capable of decrypting all affected files without losing anything and perhaps more importantly, without costing a dime.
This free service has been made possible because the Netherlands-based Fox-IT was able to recover the private keys used by the cybercriminals behind the Cryptolocker scam.
These are the same keys given to victims after paying the ransom. Although neither security company is willing to disclose how exactly the private encryption keys were recovered, experts believe they were found during Operation Tovar, an international effort aimed at dismantling the botnet responsible for distributing Cryptolocker in June.

Operation Tovar was also responsible for shutting down the notorious GameOver Zeus botnet — a malware network that infected over one million machines worldwide that was used to distribute all sorts of malware, including Cryptolocker. Those behind the free decryption software reiterate that the service only works to decrypt files infected with Cryptolocker specifically. Other variations such as CryptoDefense and CryptoWall are unaffected by this service. That said, Cryptolocker is believed to have the largest market share when it comes to ransomware.
In October of last year alone over 150,000 machines were infected and the total number of systems infected by this malware is estimated to be above 300,000 (although it could be significantly higher).
Fox-IT states that only 1.3% of all Cryptolocker victims actually paid a ransom after infection meaning that hundreds of thousands could benefit from this new service. Unfortunately, many victims probably gave up hope of recovering their files months ago and reformatted their machines. For those who still have an active Cryptolocker infection, however, the new service available at decryptcryptolocker.com is certainly good news.
Unsecured Remote Access Tool Leaves Millions of Computers Vulnerable
08.08.14
This blog often focuses on malware threats that leave PCs vulnerable to attack from hackers located around the world. Unfortunately, there are also tools built into the Windows operating system that can be equally dangerous if not managed properly. One of these tools is a remote access tool known as Virtual Network Computing, or VNC. VNC is a useful tool often used to remotely share a desktop with another person. Colleagues can collaborate in real time using VNC technology and it is also used extensively by network administrators to remotely diagnose and fix software issues on the local machine. Many software companies also leverage VNC to perform software demonstrations for customers located throughout the world.
The drawback to powerful networking tools like VNC is that it becomes very easy for hackers to access machines where steps to secure the tool with a strong, unique password have not been taken. Without even these basic protections in place, computer systems can be compromised easily. In some cases, hackers are simply interested in eavesdropping on current browsing sessions but in more extreme cases the affected machines can be completely taken over and used for a variety of cybercriminal activities.
The number of computers worldwide without proper VNC protections in place is unknown at this time, but a recent scan done by security experts proves that the number is likely to run into the millions.
In just one hour, a scan run across the Internet on port 5900 (the port used exclusively by VNC for remote access) located over 30,000 machines that had no password protecting the VNC tool at all — let alone machines with weak or easily guessed passwords. This quick scan was able to locate and acquire screenshots from machines in various industries including POS systems, pharmacies, power companies, gas stations and assorted technology companies. Other screenshots caught people doing everything from checking Facebook to playing video games to shopping on Amazon.
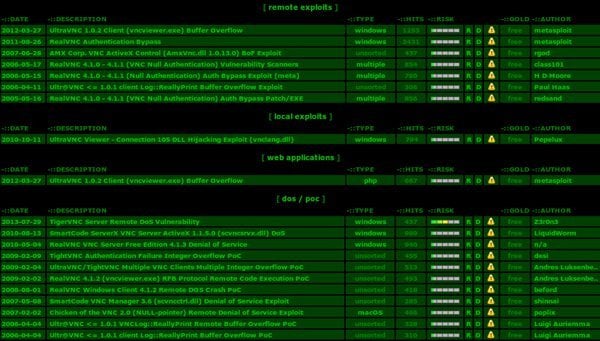
None of the victims even knew anything was amiss while the VNC port was active. The researchers even went so far as to contact one of the pharmacies located during the quick port scan and informed them that protected customer information was freely available as a direct result of the compromised VNC port. It’s important to realize that VNC can be used for more than just watching what someone else is doing online. The remote access tool (also known as a RAT) can also be used to take over computer systems entirely.
Theoretically, a hacker could use VNC to change system settings, browse through protected files and folders and even install malware — all without the knowledge or consent of the machine’s owner.
To protect your PC from becoming a victim of a VNC exploit, disable the service completely if it is not used. If VNC is used, configure the firewall to allow only specific IP addresses to connect. This is easiest when only one or two machines need remote access (such as a system administrator or other IT professional). If multiple computers need access, consider restricting access to computers within your Virtual Private Network (VPN). Of course, at the most basic level, using a strong, unique password is the single most effective way to protect any part of a computer system including VNC. This threat proves that sometimes the software tools embedded within the operating system can be used just as effectively as malware specifically designed to infiltrate systems by hackers, eavesdroppers and other people with less-than-honorable intentions.
New Malware Variation Hides Exclusively in System Registry
12.08.14
Poweliks is a new type of malware recently discovered by security experts that could mark the evolution of computer malware into something much harder to detect by modern antivirus tools. Poweliks attempts to evade detection and analysis by running exclusively within the system registry. It does not create any files on disk making it nearly impossible for current security software to detect the intrusion at all. While fileless malware only existing in the system memory isn’t a new idea, they have been relatively rare because these forms of malware typically don’t survive after a system reboot (when the memory is cleared). Poweliks is different because it is persistent across system reboots while still remaining fileless.
After infection, Poweliks creates a startup registry entry executing a legitimate Windows file (rundll.exe) before running some encoded Javascript. This code checks for the presence of Windows PowerShell on the system. If PowerShell isn’t found, Poweliks downloads and installs the program before decoding additional code that is actually a PowerShell script. The malware uses a trick to bypass default Windows system protection preventing the launch of unknown PowerShell scripts without user confirmation. Once past these system protections, the script decodes and executes a shellcode which injects a Dynamic Link Library (DLL) directly into system memory.
Once the rogue DLL is running in memory it connects with IP addresses in Kazakhstan to receive commands. These commands can download and install other malware depending on the hackers’ needs. It’s important to realize that throughout the entire process outlined above Poweliks doesn’t install anything to the machine’s hard drive. This makes it nearly impossible for most modern antivirus programs to detect the threat.
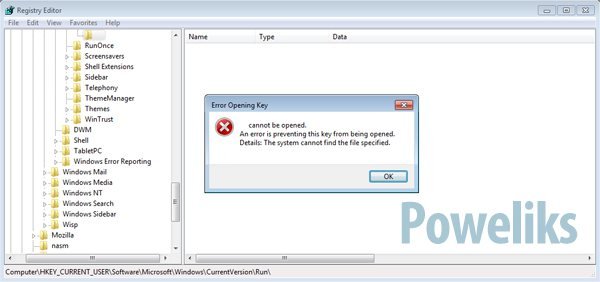
The malware further tries to evade detection by creating a startup registry key that is a non-ASCII character. This prevents the Windows registry editor tool (regedit) from displaying the rogue entry so it is almost impossible to locate even when manually trying to remove the threat. Poweliks has been spread via malicious Microsoft Word documents attached to spam emails in the past although the remote code execution vulnerability that allowed this to occur was patched by Microsoft over two years ago.
More recent versions of Poweliks have been distributed using common drive-by download attacks that rely on a host of zero-day Web exploits that typically target Flash and Java installations.
Security experts caution that other malware creators will begin adopting a similar technique to avoid detection from modern antivirus tools. To block this type of malware, an antivirus solution needs to catch the file before it is executed or antivirus manufacturers need to begin detecting the malware during execution. As a final step, in-registry surveillance could be used to detect unusual behavior. Unfortunately, most modern solutions aren’t setup to deal with these types of threats at this time and it could mean that Poweliks and other similar malware variations become more prevalent before a reliable way to stop them is incorporated into current antivirus solutions.
Hackers Use Ebola Virus to Lure Victims
15.08.14
Hackers are always looking for new ways to lure unsuspecting victims to malicious websites where all sorts of malware can be quickly downloaded and installed. Often, malware is distributed using a technique known as a drive-by download. During this type of attack, a malicious website runs through a list of known vulnerabilities in search of an exploit that can be used to install malicious software. While this type of attack isn’t new, hackers are constantly changing up tactics when it comes to luring potential victims to malicious websites in the first place. As people become increasingly wary of email campaigns designed to spread malware, it usually takes a very interesting or newsworthy story to entice the average email user to follow an unsolicited email link. In the last several months, hackers have used tragedy around the world in these malware email campaigns including war in other countries and the missing Malaysian Airlines Flight 370.
The latest trend comes in the form of emails discussing the Ebola virus epidemic. Perhaps most alarming is that four different versions of this scam have been spotted recently. The first, and most common scam, is an email that includes a fake report about the Ebola virus. The email asks that the victim click on a link to view the full report but the link actually leads to a malicious website that attempts to install the notorious Zbot Trojan. The second instance of the this scam purports to be from a telecommunications service and offers a detailed presentation of the Ebola virus in the form of an attachment.
Once opened, this attachment installs Trojan.Blueso on the victim’s machine. Although this relatively benign Trojan isn’t much to worry about by itself, the Trojan ultimately installs w32.Spyrat — a malware program that allows hackers to remotely control the infected PC and record from the webcam without the knowledge of the victim. The third variation of the Ebola scam talks about an experimental Ebola vaccine known as Zmapp. The email tells recipients that the Ebola virus has been cured and the message should be forwarded to all contacts. The attachment in this email contains Backdoor.Breut, malware capable of recording keystrokes and installing other malware remotely.
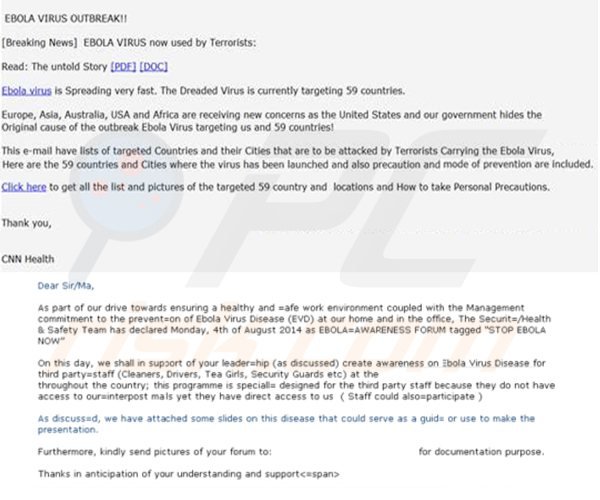
Finally, the fourth email scam is a fake CNN email campaign with a combination of “breaking Ebola news” and terrorism. The email contains a brief story complete with a link to see the rest of the story that supposedly includes a “How-to” link explaining precautions that should be taken to protect oneself from the Ebola virus. The link leads to a malicious website full of potential exploits that can download assorted payloads to vulnerable machines. The hackers behind these scams always use the same techniques to lure potential victims into installing malware via attachments or by visiting compromised websites. The difference, of course, is the news story the email supposedly explains. This week it’s Ebola but next week it could be something else entirely.
Protecting yourself from this threat is as simple as avoiding attachments from unsolicited emails and being vigilant about the website URLs you visit.
This is easily done with modern browsers by simply hovering over the link in question. If the email is supposedly from CNN, for instance, the link should go to the CNN website. In the case of these scams, the link actually leads to another website controlled by the hackers behind this scam. As always, keeping your machine OS and antivirus software updated is also an excellent way to protect the PC from many drive-by download malware campaigns.
Backoff - A Dangerous POS Malware Strain
16.08.14
Point-of-sale (POS) systems complete with credit card processing capabilities are everywhere from the gas pump to the local convenience store to your favorite clothing boutique. Unfortunately, hackers have begun targeting these POS systems around the world with specialized malware designed to extract personal payment information from thousands (and often millions) of people before the company affected by the malware even knows what happened. A recent Secret Service bulletin describes one of these malware variants known as Backoff. The announcement claims that at least seven POS vendors have confirmed having multiple clients affected by Backoff.
This means the estimated number of retailers affected could be well over 1,000 — a statistic which could spell big trouble for retailers as the busiest quarter for retailers fast approaches. This news comes as more and more retailers are attacked by POS-targeting malware. Most recently, UPS suffered from compromised customer data in 51 retail locations throughout the United States.
In recent months hundreds of large retailers have become victim to similar malware starting last year with the infamous Target breach responsible for compromising the personal financial details of over 40 million customers during the 2013 holiday shopping season.
Backoff is a type of malware known as a Random Access Memory (RAM) scraper. The malware searches through the system memory of the infected machine looking for credit card information. Once found (basically every time someone pays with a credit or debit card at checkout), the compromised credit card data is sent via the Internet to the cybercriminals behind the attack where they are used to commit fraud or in many cases are sold to other criminal organizations where the stolen data is then used for financial gain. The problem with current POS technology is that the credit card information is only encrypted once it enters the POS system database. Since malware like Backoff extracts the credit card data from system memory at the time payment is made the system hasn’t yet encrypted the sensitive data.

Essentially, this is the primary weakness of all current POS systems and the primary reason why they have become such easy targets for hackers. Also found the in the Secret Service report is the startling fact that until earlier this month the retailer POS systems affected by Backoff were unable to detect the malware using industry-standard antivirus solutions. Retailers are being urged to check with their current antivirus provider to ensure the software is capable of detecting Backoff and similar strains of malware now and into the future. Unfortunately, this type of malware is spread very easily using standard remote desktop tools coupled with the weak passwords that are so typically found in most large organizations.
Hackers are able to guess a poorly constructed password and install malware like Backoff in a matter of minutes without detection by security personnel or existing antivirus solutions.
What makes this especially difficult for consumers is that they have absolutely no control over the network and security protocols in place at a given retailer. Until more robust POS systems are developed, there are only two ways to protect yourself from these scams. First, pay for purchases with cash (although this presents its own set of risks). Second, using a prepaid credit card (purchased with cash) only loaded with enough funds to make necessary purchases protects your real credit card information from being intercepted. This is very similar to the idea of one-time use credit card numbers issued by many major credit cards companies to protect customers while making online purchases. Talk to your credit card company to discover options that may keep your information safe from the prying eyes of hackers using tools like Backoff.
Old (but powerful) Malware Updated with New Tricks
20.08.14
Reveton is an infamous malware strain part of the increasingly popular ransomware subset designed to lock computers or encrypt valuable data as a way to extort money from victims. Now that security researchers have discovered a way to decrypt one of the most notorious ransomware variants to date (Cryptolocker), it seems that hackers haven’t wasted any time looking for new ways to leverage old malware for new purposes. Unlike Cryptolocker, the original version of Reveton simply locked a victim’s computer to a specific splash screen and demanded payment to unlock the computer. Recently, however, security professionals have identified a new version of Reveton complete with two powerful password stealing programs making this malware variant even more dangerous than before.
The first and most dangerous password stealer now coupled to Reveton is called Pony Stealer. This powerful piece of code is capable of searching through the recent browser history of all popular Web browsers in an attempt to reverse engineer passwords and other personal information stored in encrypted form fields. Pony Stealer is also capable of searching through the local Windows machine for locally-stored passwords such as those used to unlock screensavers. This malware is also designed to steal Bitcoins and other cryptocurrencies by mimicking the “wallet” function of these platforms.
Once a victim enters their password into the fake wallet the information is sent to the hackers where it is quickly used to empty the virtual wallet of funds. Since there is no fraud protection in place for cryptocurrency the victim has no recourse once the money is gone.
Finally, Pony Stealer sifts through popular email clients and instant messaging programs looking for passwords or other useful information which is promptly sent to the hackers deploying the program. The second — albeit less powerful — password stealer embedded in this new version of Reveton is from the Papras malware family.
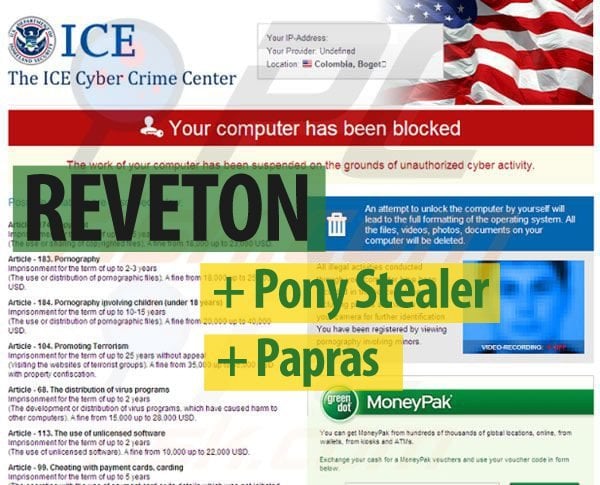
Although this strain is not nearly as efficient at stealing passwords as Pony Stealer, Papras was added because it is very good at disabling existing antivirus programs that might detect Reveton and block it from being installed in the first place. It also appears that Reveton now uses geolocation to target specific financial institutions in the area where the malware has been deployed. For example, in a version recently analyzed that targeted German victims, Reveton was preprogrammed to look for browser history pertaining to 17 German banks. The malware can be programmed to look for specific information in any geographical area depending on the needs of the hackers.
While Reveton is still primarily ransomware designed to scare people into paying a fine for supposedly breaking the law, the addition of these new tools (especially Pony Stealer) makes a dangerous (although slightly outdated) piece of malware even more alarming and capable of taking more from victims than just the extortion money demanded in the original version.
It’s worth noting that only one strain of this new version of Reveton has been identified so far but more could follow in the weeks and months to come depending on the success of the initial campaign. The best way to avoid infection is to make sure OS and antivirus updates are properly installed and to avoid unsolicited emails (as well as links or attachments contained within) as infection can be expensive and difficult to properly clean up.

▼ Show Discussion