News Archive September 2014
![]() Written by Karolis Liucveikis on (updated)
Written by Karolis Liucveikis on (updated)
Table of contents:
- Malvertising and Fileless Malware Join Forces
- Is the Game Really Over for Gameover Zeus?
- A Small - But Powerful - Banking Trojan is Even More Dangerous
- New Malware Targeting Gamers' STEAM Accounts
- Cross Platform Malware Toolkit Targets Windows, Linux and ARM-based Machines
- DDoS Attacks Becoming More Aggressive and Using New Tactics
Malvertising and Fileless Malware Join Forces
04.09.14
Recently, this blog covered the alarming increase in fileless malware such as Poweliks. This dangerous new type of malware is undetectable by most modern antivirus solutions because the malware does not actually install any files to the computer hard drive (installing files is a red flag for most antivirus programs). Fileless malware isn’t exactly new but the problem has always been that the malware disappears after the computer is rebooted. Newer variations like Poweliks have figured out a way to load themselves via system registry entries every time the machine is booted resulting in persistent fileless malware that is almost impossible to detect and just as difficult to remove.
Another type of fileless malware is known as the Angler Exploit Kit. This kit is actually a Web-based attack tool that injects malicious code directly into the Web browser using vulnerabilities in common browser plug-ins including Flash, Java and Microsoft Silverlight. Since Angler doesn’t install any files on the machine, most antivirus solutions do not detect a problem. Once the door has been opened, however, other malware variants like the Rerdom backdoor Trojan can be installed without the knowledge of the victim. The Angler Exploit Kit has found a new medium to spread thanks to malvertising. Malvertising works by spreading malware through advertisements often found on websites.
These advertisements are hosted on a different server than the website itself through companies like AppNexus. This online ad network was recently used to spread Angler on a variety of high profile websites including deviantart.com, eBay and Photobucket.
Visitors to these sites didn’t have to click on the ad to fall victim to Angler. Once the malware-laden advertisement loads on screen, Angler goes to work looking for an exploit to drop its payload. Known as a drive-by download attack, the victim never knows that anything is happening.
Meanwhile, however, dangerous Trojans are being downloaded and installed without being detected by most popular antivirus solutions. This latest attack was also interesting because it made use of retargeting — a technique that stores tracking data (like cookies) to show ads based on Web browser history. The use of retargeting makes it much more difficult for site owners to identify rogue content because the results one visitor sees are different from what another visitor sees. In other words, it’s nearly impossible to duplicate the rogue content.
The hackers behind this attack also leveraged the real-time bidding process typically used by legitimate advertisers to decide in real-time which ads will be shown to a visitor based on geographical location and browsing history. Unfortunately, there is no way to avoid attacks like this right now.
Popular ad blocking software usually “whitelists” certain ad agencies anyway meaning that there is still a chance that malware-infected advertisements end up on your browser. At this point, it is up to online ad networks like AppNexus to be more vigilant about the content being served from their network to protect consumers from threats like this.
Is the Game Really Over for Gameover Zeus?
12.09.14
A couple months ago this blog reported that the Gameover Zeus botnet — a notoriously dangerous Trojan responsible for distributing Cryptolocker ransomware — was shut down by an international task force code named Operation Tovar. This task force included members of the U.S. Department of Justice, multiple law enforcement offices, foreign government agencies and private security firms from around the world. The goal was to destroy the Command and Control servers responsible for sending instructions to millions of infected PCs and for the most part, the operation was considered a success.
Unfortunately, Operation Tovar was unable to catch the hacker behind the attack. Many people attribute this to a press leak the day before the raid which gave the hacker time to escape. Not only did the mastermind of the Gameover Zeus botnet escape but Operation Tovar only removed the Command and Control servers from the picture. In other words, millions of machines around the world are still infected with this Trojan simply waiting for a new command structure to be implemented. Security experts agree that the person behind Gameover (Evgeniy Mikhailovich Bogachev) is already building a replacement infrastructure capable of controlling all the machines already infected.
This new version of Gameover could go live at any time and will most likely contain new features that would make the Gameover and Cryptolocker duo even more dangerous.
One of these possible features is a “self-destruct” feature that would automatically encrypt or erase data on an infected machine if the malware is unable to communicate with a Command and Control server for a set period of time. If a feature like this had been implemented in the first version of Gameover, millions of computers and all the data stored on them would have been useless after Operation Tovar destroyed the botnet.

While the original Gameover creator works to resurrect this profitable piece of malware, a variation of this Trojan has already appeared on the Web. Approximately five weeks after Operation Tovar, a variant was spotted in a spam email campaign that shared approximately 90% of its code with the original Gameover Trojan. The primary difference is that the new version doesn’t rely on peer-to-peer networking.
Instead, this version uses something known as fast-flux hosting — a round robin technique designed to make the system more resilient in the event of a takedown.
Evidence of this new version suggests that the criminals responsible for Gameover — a botnet which has stolen over $100 million around the world — are attempting to rebuild the infrastructure from the ground up taking extra time to build a more versatile Trojan botnet that can’t be stopped even if one or more Command and Control servers are taken down. It’s important to note that any new versions of this malware are being spread via spam email campaigns (at least for now).
Protecting yourself is as simple as avoiding unsolicited emails. Both links within the email and attachments can contain this version of Gameover.
Although the once powerful malware network and the criminals behind it are still only lurking in the shadows, it might not be too long before Gameover is making headlines again as a new and improved Trojan specifically designed to circumvent the events that led to its demise earlier this year.
A Small - But Powerful - Banking Trojan is Even More Dangerous
14.09.14
A banking Trojan known as Tiny Banker, or Tinba, was first discovered over two years ago when it infected thousands of computers in Turkey. The malware is extremely small at only 20 Kb (hence the name) and is capable of injecting rogue HTML fields into websites when it has detected that the victim has navigated to an online banking site. The injected HTML fields typically ask users for sensitive personal and financial information – information not usually required on most online banking portals. Recently, anti-virus and security security company Avast analyzed a new version of Tiny Banker that appears to target customers in the United States. Specifically, Tinba is now programmed to target major U.S. banks including Wells Fargo and Bank of America.
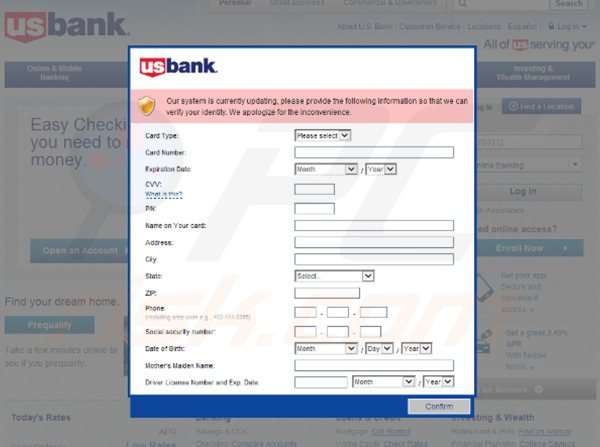
This could signal trouble for many American PC users who frequently use online banking services to check balances, pay bills and perform money transfers among other tasks. When Tiny Banker was observed working on an infected machine at the Wells Fargo online banking portal, victims were first warned that a security update required that they input additional information to continue.
This information included a credit card number, expiration date, three digit CVC code, the person's address, Social Security number, mother's maiden name, driver's license number and its expiration date. In other words, everything a hacker would need to steal the identity of the victim.
This malware is especially dangerous because it works inside the Web browser while the victim is actually on the targeted banking website. It looks like a legitimate request, but of course, the real bank already has all of this information and would never ask for this information (especially via the Internet). It appears that Tiny Banker is currently being distributed via the Rig exploit kit.
This malware kit was discovered a few months ago and works by exploiting vulnerabilities commonly found in Internet Explorer, Java, Adobe Flash and Microsoft Silverlight. These attacks are initiated when a compromised website has JavaScript injected into its HTML code by hackers.
Once a visitor lands on an infected page, Rig tests various known vulnerabilities until its payload (in this case Tiny Banker) can be deployed onto the machine without the knowledge of the victim.
Rig has also been used to deploy other dangerous payloads including CryptoWall, Gameover Zeus and a host of backdoor Trojans allowing for remote access to infected machines. Many current anti-virus products detect Rig and/or Tiny Banker assuming the security software is up-to-date. That said, the best way to prevent the potentially damaging effects of a Tiny Banker infection is to remain diligent while performing online banking transactions.
Remember that Wells Fargo, Bank of America or any other U.S. financial institution will never ask for personal information other than your user name and password to initiate an online banking session.
If additional information is requested, call the financial institution directly and confirm the required information before continuing. And as always, remove unnecessary browser plug-ins including Java and Flash unless they are absolutely needed. If they are, make sure all the latest security patches have been applied to prevent common exploits from working.
New Malware Targeting Gamers' STEAM Accounts
19.09.14
Twitch is a popular video game streaming site recently acquired by Amazon. According to Finnish security firm F-Secure, a rogue Twitch account is being used to launch a malware campaign targeting users of a popular game distribution platform known as Steam. The malware, called Eskimo, operates by sending automated spam messages from a Twitch account using the service's built-in chat function. Users receiving the rogue message are asked to click on a link which supposedly allows them to enter a raffle for sought-after items in Counter Strike: Global Offensive; a popular game distributed through Steam.
The link actually leads to a malicious website where victims are asked to enter their name and email address. This information doesn't actually go anywhere – it is simply a ploy to distract the user while Eskimo is downloaded via drive-by download in the background.
Distributed as a Windows binary file, Eskimo is able to instantly takeover the victim's Steam account without even knowing the password since the victim is already logged into Steam during the attack. Once active, Eskimo allows hackers to sell the victim's items (usually at a steep discount so they move quickly).
These funds can be used to purchase more valuable items which are then traded with the hacker's account. The malware can also take screen-shots of the infected account, add new friends, accept pending friend requests and even purchase items using the victim's money. These items are then traded to the hacker's account. Early iterations of Eskimo sold stolen items for a 12% discount. The most recent variant sells items for a 35% discount – most likely in an effort to move the stolen virtual merchandise faster.

At the time of this writing, the hacker(s) responsible for this attack have not been identified but victims already affected by Eskimo are reporting on Steam forums that most of the stolen goods are being sent to a Steam account by the name of Youni. In theory, finding the people behind this malware campaign shouldn't be too difficult as every Steam account is associated with a specific PC. That said, the hackers behind this attack most likely set up an anonymous machine to automate the theft process which could mean Eskimo continues to operate with impunity for some time before finally being shut down.
While it may seem like the virtual goods being stolen aren't as important as “real currency”, remember that these items are purchased using real money and represent an asset as much as cash sitting in a bank account.
Even though gamers tend to be more computer literate than the average PC user, Eskimo has proven that no one is safe from this type of attack. The profit generated by Eskimo for its creators isn't known at this time, but is likely in the tens of thousands of dollars already. Like any other drive-by download attack, the best way to avoid Eskimo is to steer clear of any links asking you to click outside of the page you are currently on. Also, these type of attacks rely on vulnerabilities in Web browser plug-ins – disable these plug-ins if not explicitly needed to avoid losing your money and valuable virtual gaming goods.
Cross Platform Malware Toolkit Targets Windows, Linux and ARM-based Machines
23.09.14
As more devices become Internet-ready – luring consumers with the dream of an automated lifestyle – new malware is being designed to take advantage of this technology trend. Smart thermostats and other appliances have even been used in large-scale Distributed Denial of Service (DDoS) attacks. In fact, one such attack was recently recorded at 215 Gbps and over 150 million packets per second. This DDoS attack was performed using a new malware toolkit known as Spike. Security experts have watched as the Spike Toolkit was ported from Windows, to Linux and even ARM-based platforms.
ARM is used with low power microprocessors commonly installed in new smart home appliances. Thermostats, home security systems and even refrigerators are now connected to the Internet. Similar to how a PC-based malware botnet infects thousands, or even millions, of computers, Spike is capable of launching massive targeted DDoS attacks from devices people don't often associate with malware.
The Spike Toolkit uses a variety of well-known DDoS tactics including synchronize (SYN) attacks, User Datagram Protocol (UDP) attacks, GET request flood attacks and many others.
Almost all documented attacks where Spike was recently used target the United States and some parts of Asia. This threat is significant because it marks a transition in the way we look at – or at least should look at – network security at home and in the office. Traditionally, the only vulnerabilities in a network were Internet-connected computers susceptible to malware infection which could easily spread to the rest of the network, often bypassing many security features designed to stop such attacks.
Unfortunately, as more devices become Internet-ready, the number of possible network vulnerabilities has increased and more importantly, dictates that we completely re-evaluate many of the network security best-practices that have been the mainstay of PC security for years. Since most smart-home technology is based on ARM processing architecture often running stripped down versions of Linux to operate, there is very little, if any, anti-malware support for these systems. In other words, any device that is part of the so-called Internet of Things could be used as a mechanism for spreading malware throughout an otherwise secure home network. In the case of the Spike Toolkit, these devices are being leveraged as a new type of botnet, but the same technology could also be used as an easy entry point for a full network breach which could ultimately infect your PC(s) with even more dangerous malware including banking Trojans and key logging programs. Protecting yourself from Spike and similar malware variants is nearly impossible at this time.
Until manufacturers of smart home devices begin to build more robust security features into the base architecture, the best way to protect yourself from a security breach is to limit the number of devices connected to your network.
This is especially true of Internet-ready devices that aren't actually being used as part of a smart home configuration. Also, make sure that all PCs connected to the network are updated regularly to prevent the infection from spreading. Finally, installing a hardware firewall within your existing network infrastructure is an excellent way to prevent malware like Spike from penetrating your home LAN.
DDoS Attacks Becoming More Aggressive and Using New Tactics
26.09.14
A Distributed Denial of Service (DDoS) attack is nothing new. In fact, this technique has been used by hackers practically since the Internet came online and continues to be an effective way to disrupt network services. DDoS attacks have another purpose as well. The Gameover Zeus botnet was often installed on networks during massive DDoS attacks used to distract IT security personnel from the malware infection. By the time the DDoS attack would subside, Gameover was already installed and it could be days before the breach was even noticed. Perhaps the biggest drawback (from a hacker's perspective) to using a DDoS attack is that most common techniques used (such as synchronize (SYN) attacks, User Datagram Protocol (UDP) attacks, and GET request flood attacks) are extremely well-documented and easy to block once a network is properly configured.
Unfortunately, a new DDoS technique has been developed that could change all that. Known as a Network Time Protocol (NTP) Amplification attack, this new DDoS variant was recently used against popular online gaming sites with devastating results.
A NTP Amplification attack works when a hacker is able to compromise a publicly available NTP server. NTP is the oldest Internet protocol still in use and is designed to sync Internet-connected devices to within a few milliseconds of Coordinated Universal Time (UTC).
The problem is that the servers managing Network Time Protocol are extremely old and do not have hardware protections (such as rate limiting) built into the system. This makes NTP servers especially prone to attack. Security experts have long realized that a hacker could use a NTP server to generate attack traffic at a specific target, but until recently, no one had actually attempted it (at least not on a large enough scale to make it dangerous). The recent attacks against online gaming sites such as STEAM and War of Wizards proves not only that the concept works, but that NTP Amplification is a serious concern for Internet security. It's important to point out that NTP is implemented in all major operating systems, network infrastructure devices and embedded devices.
This means that as this technique is perfected, NTP could be leveraged in everything from PCs to smart phones and even smart home appliances to create devastatingly powerful DDoS attacks targeting networks around the world for profit. The ancient architecture currently supporting NTP is managed exclusively by volunteers led by the man who originally created the protocol, David Mills. This makes it difficult, from both a financial and labor perspective, to keep up with hackers and other cybercriminal organizations that often have plenty of cash to throw around in their quest for new illicit sources of revenue.
While DDoS attacks are more likely to target large enterprise-level network resources and not the typical home network, the development of this new DDoS attack vector could redefine the way we treat these types of attacks in the future.
And as more devices are released that still rely on this antiquated protocol, hackers know that the recent attacks on popular gaming websites is only the tip of the proverbial iceberg when it comes to what NTP Amplification attacks are capable of doing in the future.

▼ Show Discussion