News Archive May 2013
Table of contents:
- Skype is being used to spread malware
- Latest Email-Based Malware Infections
- Facebook Accounts Hijacked
- Zero-Day IE8 Exploit
- Facebook App spoofing still unpatched
- DDOS Services for hire
- Newegg spam campaign
- Skype…not so private anymore?
- Chinese Hackers Compromise U.S. Weapons Designs
Skype is being used to spread malware
03.05.13
Skype is a proprietary voice-over-Internet Protocol service, it's a very popular online chat service which has nearly 700 million users all over the world. Recently Skype has been targeted by Cyber criminals who had plans to use this service as their malware distribution channel. Earlier this week (on October the 8th) Skype users have been warned about a new worm which spreads spam messages (for example: lol is this your new profile pic? etc.) and in such way tricks unsuspecting computer users into clicking links which lead to malicious websites distributing Trojans, ransomware infections and viruses. Most commonly links in such messages lead to Trojans which are used to steal computer user's passwords. The worst thing talking about this Skype malware is that Skype users are not aware that links posted by their contacts could lead to malicious websites or infected executable.
While social networks users have already seen such scam strategies being used in the past Skype users tend to trust links that they are given by their contacts and click on them. Such user behavior makes Skype a very wanted target for Cyber criminals to distribute their malware or ransomware infections.
To protect your PC from such security infections you should use cautious when you receive a link from your contact in Skype which looks unexpected or strange.
Furthermore you should always keep your Skype software up-to-date, and don't forget to use a legitimate antivirus and antispyware programs. While the distribution of such spam messages seems to be stopped, Cyber criminals recently started another malware distribution campaign related to Skype. This time Cyber criminals doesn't use Skype to post their deceptive messages which leads to Trojans, now they changed their tactics and they are sending email messages which states that your Skype password has been recently changed. Example of such deceptive email message:

Text in this message:
Hi there,
Password successfully changed
Your new Skype password has been set.
You can now view your attached call history and instructions how to change your account settings. If the changes described above are accurate,
no further action is needed. If anything doesn't look right, follow the link below to make changes: Restore password
Talk soon,
The people at Skype
Another spam message that is being distributed by Cyber criminals looks like the one in the screenshot below.
Note that links in this particular message leads to Blackhole exploit kit.
If a computer users would click on any of the links in this spam email message their computers would get infected with Trojans. Be sure to delete such message if you have received one.

Text in this message:
Hi there,
You have a new voicemail
Sign in to Skype to listen to the message.
If you no longer want to receive email alerts about new voicemails, unsubscribe now.
Talk soon,
The people at Skype
If you have received such email message in your inbox you shouldn't trust it. This is a deceptive message which actually were send by Cyber criminals who are hoping that you will fall for this trickery and you will open the attachment that comes with this email. If you would extract the attached zip file and double click the file that was in the archive you computer would be infected with a Trojan infection which enables Cyber criminals to remotely access your PC.
Always use cautious when opening attachments that comes with email messages.
If you have opened the attachment from this deceptive spam email you should scan your computer with legitimate antivirus and antispyware programs.
Latest Email-Based Malware Infections
04.05.13
Email messages have always been a popular source of malware infections. Cyber criminals who are responsible for creating and distributing malware using infected email attachments or malicious links are striving to create a sense of urgency and make their fake email messages appear legitimate. Fake Email messages are used to trick unsuspecting PC users into clicking on the malicious links or to download infected Email attachments. Most commonly such rogue email messages exploits the names of various legitimate companies and organizations, moreover Cyber criminals are stealing the graphics of such well known brand names and embeds them in their malicious Email messages.
Recent research shows that most commonly Cyber criminals are exploiting the names of FedEx, Ups, DHL, Bank of America and Hewlett-Packard in their Email based malware attacks.
The main purpose of such rogue Email messages is to infiltrate user's computer with Trojans capable of stealing personal information, ransomware infections or fake antivirus programs.
In most cases infected Email attachments comes as .zip files, however .exe and .pdf infected files are also very common.
To create a sense of urgency Cyber criminals are using such words as "alert", "notification", "needs urgent attention", "transaction is completed" etc.
Some of the most commonly used security infections in email messages:
Blackhole Exploit Kit - Security infection which takes advantage of unpatched exploits and injects user's computer with banking Trojans, key-loggers etc.
Cridex Trojan - Security threat capable of capturing online banking credentials entered via Internet browsers, can download and execute files etc.
Dapato Trojan - Installs malicious software on the infected operating system. Commonly installs a backdoor which allows remote access to infected systems.
Zeus Trojan - Attempts to steal confidential information, online credentials and banking details
Some of the most widely spread malicious email messages from the last couple of weeks:
Fake DHL Notification:
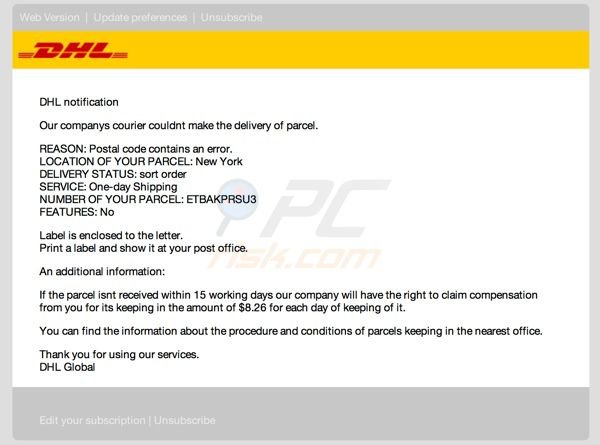
Deceptive message which is used to trick computer users into opening an infected attachment:
DHL notification
Our companies cowrie couldn't make the delivery of parcel.
REASON: Postal code contains as error.
LOCATION OF YOUR PARCEL: New York
DELIVERY STATUS: sort order
SERVICE: One-day Shipping
NUMBER OF YOUR PARCELS: ETBAKPRSU3
FEATURES: No
Label is enclosed to the letter.
Print a label and show it at your Post office.
An additional information:
If the parches isn't received within 15 working days our company will have the right to claim compensation from you for it's keeping in the amount of $8.26 for each day of keeping of it.
You can find the information about the procedure and the conditions of parcels keeping in the nearest office.
Thank you for using our services.
DHL Global
Fake UPS "We were not able to delivery the postal package" notification:
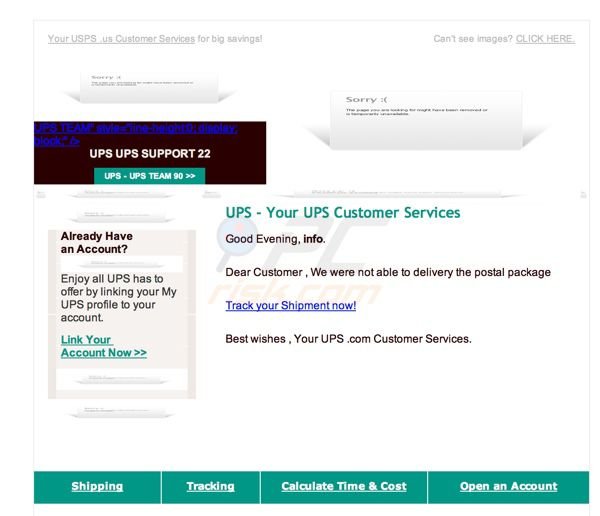
Deceptive message which is used to trick computer users into clicking on malicious links:
UPS - Your UPS Customer Services
Good Evening, ___
Dear Customer, We were not able to delivery the postal package
Track your Shipment now!
Best wishes, Your UPS.com Customer Services.
Bank of America fake root certificate:
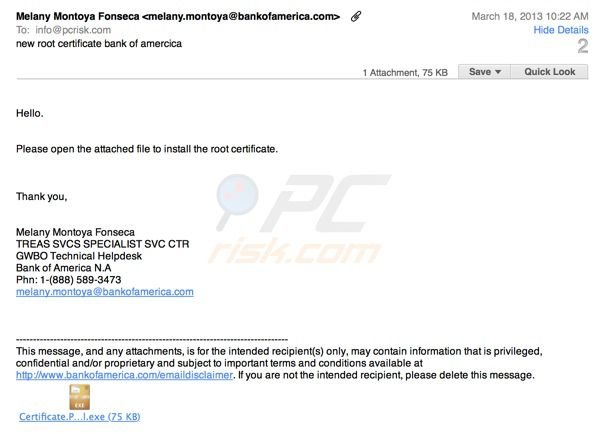
Fake message which is used to trick Internet users into opening an infected attachment:
Hello,
Please open the attached file to install the root certificate.
Thank you,
Melany Montoya Forseca
TRES SVCS SPECIALIST SVC CTR
GWBO Technical Helpdesk
Bank of America N.A
Phn: 1-(888) 589-3473
melany.montoya@bankofamerica.com
This message, and any attachments, is for the intended recipient(s) only, may contain information that is privileged, confidential and/or proprietary and subject to important terms and conditions available at www.bankofamerica.com/emaildisclamer If you are not the intended recipient, please delete this message.
Bank of America fake ACH transaction notice:
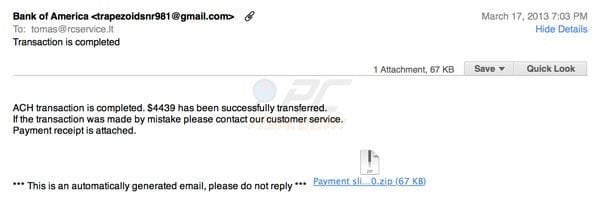
Deceptive message used to trick computer users into opening an infected attachment:
ACH transaction is completed. $4439 has been successfully transferred.
If the transaction was made by mistake please contact our customer service.
Payment receipt is attached.
***This is an automatically generated email, please do not reply***
HP scanner document scam:
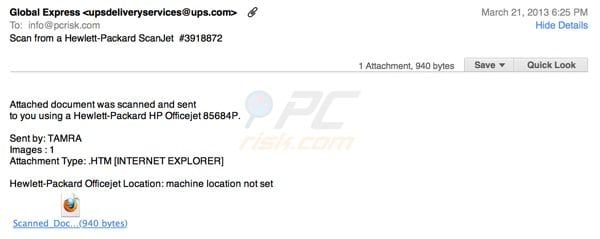
Fake message used to trick computer users into opening an infected attachment:
Scan from a Hewlett-Packard ScanJet #3918872
Attached document was scanned and sent to you using a Hewlett-Packard HP Officejet 85684P.
Sent by: TAMRA
Images: 1
Attachment Type: HTM [Internet Explorer]
Hewlett-Packard Officejet Location: machine location not set
Infected email message "explosions at Boston marathon" - spreads Trojan to gain remote access to infected computers:

As you can see from the following examples Cyber criminals are exploiting the names of well known companies and organizations as well as taking advantage of braking news.
They create their deceptive email messages to make them appear as they are legitimate and needs urgent attention.
How one can avoid email-based malware?
1. Don't open email attachment if it came from an unknown sender. The best decision would be to delete such email message.
2. If the email message was send by a trusted and known source but you didn't expect it - contact the sender to confirm that the attachment is legitimate (don't reply to the email message - use the phone or their support email).
3. Avoid opening attachments with doc, .xls, .exe .htm extensions - such files may have executable code and could potentially infect your computer with malware (prior to opening such files contact the sender and ask if the attachment is legitimate).
4. Use legitimate antivirus programs.
Facebook Accounts Hijacked
13.05.13
With over one billion registered users, Facebook has become a prime target for hackers. Microsoft has issued a warning about a new threat to the social media giant capable of hijacking individual Facebook accounts. The malware, known as Trojan:JS/Febipos.A, was first detected in Brazil and reported on Friday in a Microsoft security bulletin. The Trojan works by disguising itself as a legitimate browser extension for both Google Chrome and Mozilla Firefox. The malware even tries to update itself like a benign extension would. The program is typically installed by TrojanDropper:Win32/Febipos.A.
Once installed, the program will download an updated version of itself onto the affected machine. The infected machine will not show any obvious signs of malware. Instead, the program checks if the computer is currently logged into a Facebook account. If detection is successful, Trojan:JS/Febipos.A will attempt to download a configuration file that includes a list of commands for the fake browser plugin. The program is capable of liking pages, sharing, chatting with the account holder’s friends, joining groups, and posting status updates.
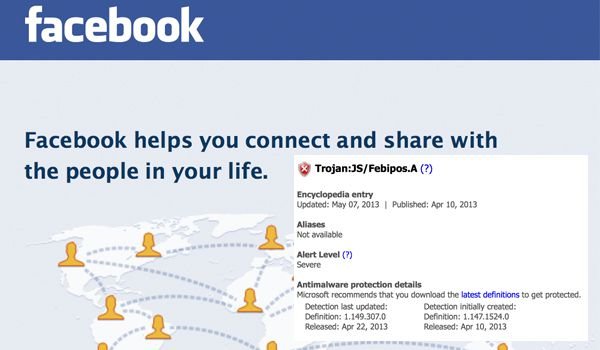
The initial infection posted messages stating “15 year-old victim of bullying commits suicide after showing her breasts on Facebook.” Automated comments range from (in Portuguese – English translation shown) “Sorry guys, but this is ridiculous!!!” to “I don’t have a new car, I don’t have spare cash, but I get really close…” according to the official Microsoft security bulletin. Variants of the original malware have already been reported. One such program includes commands to post explicit messages in Portuguese. These posts also include links to other Facebook pages.
Microsoft reported that even while analyzing the malware, a large number of likes and shares continued to be reported meaning that the program is still infecting new machines.
Specifically, in just a few hours over 400 new page “likes” were recorded. Increases in the number of shared links and comments were also noted during this time. Many of the URLs contained within the initial config file have already been blocked by Facebook and the suspect pages removed. However; those behind this malware can change the behavior of the Trojan at any time. The commands can be changed an unlimited number of times until the infection has been isolated and the source shut down. The messages, URLs, and general behavior of the program depend on the config file which is not downloaded until the malware has already embedded itself on a machine. At this time, it is not clear how the infection is spreading or the exact number of machines that have fallen victim to the Trojan.
At this time, the infection seems to be centralized in Brazil; however, Microsoft stated that the code can easily be modified to target other geographical areas as well.
Microsoft claims that the latest version of Security Essentials detects this malware. Presumably, other antivirus software definitions do as well. In any event, the best method of protection from this threat is to only download browser extensions from trusted sources such as the Chrome Web Store or Add-ons for Firefox until the source of this threat has been determined. Make sure your antivirus protection is updated regularly and look for any suspicious activity on Facebook if infection has already occurred.
Zero-Day IE8 Exploit
13.05.13
Last week, Microsoft confirmed reports of a vulnerability in Internet Explorer 8 allowing remote access to the operating system in Windows XP and above. This also includes all current versions of Windows Server up to 2008 R2. The exploit relies on a previously unknown hole in Internet Explorer that allows for remote code execution (as confirmed by Microsoft). The exploit has already been used successfully against the U.S. Department of Labor website. A script on several DOL web pages redirected users to a site serving a remote access Trojan to visitors. Specifically, the attack targeted Department of Energy workers that were attempting to access the Site Exposure Matrices. These pages communicate information about toxic substances encounter at nuclear sites as well as possible side effects.
These infected machines could be located within nuclear facilities and allow the attacker the same access as the current user. The site has been cleaned up but remains offline at this time while the DOL completes its investigation into the attack.
An official statement released has stated that no loss or compromise of information is evidenced at this time.
As many as nine other sites were also targeted with most of the focus being on energy related organizations. One such company is a large European company specializing in the aerospace, defense, and security industries. Non-profit groups and institutions have also been targeted. Although no group has taken official responsibilities for the exploit, many experts believe the Chinese hacking group known as DeepPanda is at fault. If this is the work of DeepPanda, many believe that this is only a small portion of an advanced exploit kit still under development.
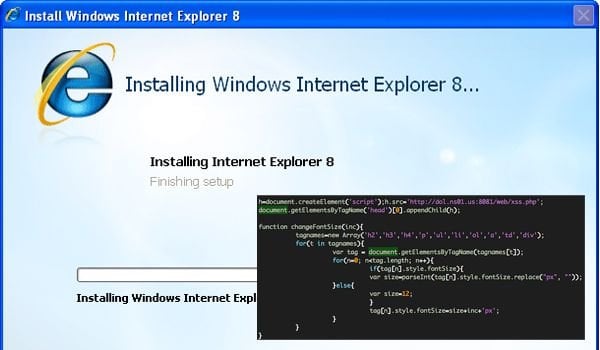
The exploit has already been made available for the Metasploit Framework (a penetration testing tool) and could soon make its way into the mainstream cybercrime market.
Analysis of the initial log data suggests that visitors from 37 different countries browsed compromised websites before detection.
Many (as much as71%) of these visitors were from the United States. AlienVault reported that the compromised web page used advanced reconnaissance techniques to collect information about the machines visiting the site. This information included what antivirus software was installed, browser plug-in data, the version of Adobe Flash currently installed, and the current Java version running. The code even attempts to disable certain antivirus products. The payload was also found to be encrypted using base64 in an attempt to bypass existing security measures.
Experts recommend using a different browser until this vulnerability has been patched by Microsoft.
If operating on XP, the only option is to roll back to IE7. Windows Vista and 7 users can upgrade the browser to IE9 to avoid falling victim to this exploit. Windows Server users operate in a restricted mode by default known as Enhanced Security Configuration. Restricted Zone disables scripts and ActiveX controls and will mitigate the risk to these systems. Fortunately, Microsoft’s next security patch is reported to address this vulnerability. Even if the patch does not reach Tuesday’s deadline, there is already a Fix it tool offered by Microsoft to temporarily fix the issue until an official security patch can be released.
Facebook App spoofing still unpatched
17.05.13
Although there are many unpatched flaws in Facebook security, an especially dangerous one that remains vulnerable allows hackers to spoof the content of any Facebook app with ease. Using this exploit, hackers are able to create spoofed wall posts from any trusted Facebook app imaginable. To the user, the content looks completely legitimate but the contents of the spoofed page can be anything but harmless. The vulnerability is capable of spoofing any app but some of the common ones that have already been spoofed successfully include Saavn, Candy Crush, Spotify, and Pinterest to name a few. No matter what app is actually spoofed, the content appears to be from the specified app and typically does not raise any alarms for the user as a result.
This vulnerability relies on the way in which Facebook allows apps to automatically post content on behalf of users.
Facebook uses a publishing method known as stream.publish. This dialog contains parameters for app_id and attachment (swfsr, imgsrc, href) that can be used by hackers to inject malicious content while appearing to be from a legitimate app. Simply using the app_id value of a known Facebook application and providing attachment parameters is all that is required to perform this hack.
Each Facebook app is assigned a unique app_id parameter which can easily be injected into a malicious wall post.
Facebook does have some degree of protection in place for these types of attacks. However, Break Security has demonstrated that by simply removing the href parameter from the stream.publish dialog a hacker can bypass the security measures in place and successfully spoof the app.
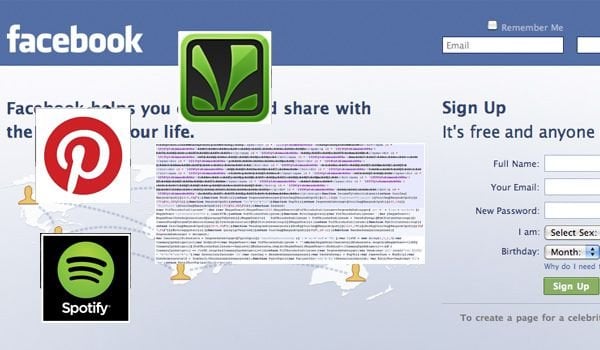
Earlier this year, Facebook did update the stream.publish dialog and introduced some new parameters using Feed Dialog to publish content. The addition of these four new parameters has made the vulnerability arguably more dangerous because of the increased options available to hackers when modifying them.
The link parameter allows hackers to inject a malicious external link.
This could redirect users to a phishing site, executable file, or Zero day exploit. The picture parameter allows for spoofing content with an image. This technique will only work for spoofing wall posts as the image will not display correctly on a user’s newsfeed. The caption parameter allows attackers to choose “where” the content came from even though the content could be located anywhere. For example, the post could be made to appear as though it came from Facebook.com, Zynga.com, or Ownerappdomain.com. The name parameter is responsible for the title displayed in the spoofed post.
When a Facebook user clicks on the title, they are unknowingly redirected to a malicious website automatically.
Located within the Facebook app development options is the “Stream post URL security” option. If left unchecked by a developer, the hacker can use any remotely uploaded swf file as the attachment parameter. The danger is that when clicking a link on the spoofed page, a user may inadvertently execute the swf file from an external website on his or her machine. The implications of this unpatched vulnerability include remote malware installation and social engineering of Facebook users by phishing for passwords to Facebook as well as the apps these users believe they are interacting with.
DDOS Services for hire
18.05.13
Distributed Denial of Service (DDOS) attacks are nothing new. In the past few years, there has been an increase in these still-effective attacks. Services allowing customers to rent “bot nets” for stress testing used to be found exclusively in the hacking underground. These services have recently shifted and started openly advertising across the Internet. These services, known as “booter” or “stressor” products, launch DDOS attacks against networks to supposedly test the security measures in place. These means that anyone can pay a nominal fee to rent large amounts of bandwidth and channel them against practically any server they choose. Many of these sites share the same or similar source code and although they are not capable of taking down large, well-managed networks, small to medium web hosts should take note.
It is also worth noting that although these booter services often promise customers a variety of advanced attacks including Layer 7 attacks, SYN floods, and Apache memory exhaustion, a glitch in the code often means that reflected DNS and UDP flood attacks are the only methods used against a target. Typically known for a tough stance against web-based crime, PayPal seems to be the preferred payment method for most of these services (many of which are surprisingly U.S. based).
Although PayPal denies allowing these activities to take place under its watch, recent reports suggest otherwise.
The customer data of one popular booter service, asylumstresser.com, was recently leaked and the data has been evaluated by security experts. This service was responsible for as many as 10,000 online attacks within just a few days in March. The owner of the service, reported to be a 17 year old from the United States, as recently received over $35,000 in PayPal payments as a result of his service.
 Unfortunately, asylumstresser is the rule rather the exception. Using cookie cutter source code, it is relatively easy for someone to setup a similar service and hide behind disclaimers that protect the owner from litigation.
Unfortunately, asylumstresser is the rule rather the exception. Using cookie cutter source code, it is relatively easy for someone to setup a similar service and hide behind disclaimers that protect the owner from litigation.
The same old “I am not responsible for what illegal actions people may use my service for” argument seems to keep these products running and the perpetrators safe.
Even though the service offers a Skype resolver service specifically designed to locate the IP address of anyone using Skype, the service purports to be only designed for stress testing systems owned or operated by the customer. Asylumstresser also has YouTube ads that talk about the service’s ability to “take down” competitors servers. Like many other facets of technology, there is no clear law dictating what liability the owner of one of these sites may carry.
When recently interviewed, the administrator of this service blames poor network management on the existence of his service.
Network security experts disagree and are pushing to make these people criminally liable although to date nothing has been done to thwart these disruptive attacks from occurring. Although it is true that basic network security knowledge and proper administration can stop most of these attacks with relative ease, it does not detract from the legal implications that should be imposed upon those running the services. It has become too easy for someone with little to no programming knowledge to launch attacks against the competition.
Newegg spam campaign
24.05.13
Newegg is a popular online retailer specializing in computer parts and equipment predominantly aimed at the DIY market. Recently, a very convincing spam email campaign has been discovered that has the potential of tricking even savvy computer users. The email starts with an attention grabbing subject. “Payment charged” will usually compel a user to click on the email. Once opened, the scam does an effective job of convincing recipients that the message is authentic.
The email looks exactly like something that would be sent by Newegg and it even comes complete with unique account numbers and sales orders numbers that appear to be automatically generated for each email sent out. The spam message usually includes a dialog similar to the following:

Dear Customer,
Thank you for shopping at Newegg.com.
We are happy to inform you that your order (Sales Order Number: XXXXX) has been successfully charged to your MasterCard and order verification is now complete.
If you have any questions, please use our LiveChat function or visit or Contact Us page.
Once you know, you Newegg.
Your Newegg.com Customer Service Team
Both of the links present in the email message actually redirect users to a variety of malicious URLS. Some of the URLs that have been embedded so far include:
productsbylifestyle(dot)com/news/developing-dollar-chance(dot)php
iechomobiliy(dot)com/news/developing-dollar-chance(dot)php
rs5636000(dot)de/mechanizes/index(dot)html
Once a victim has been successfully redirected to a compromised URL, the website will attempt to gain access and drop a payload of some sort into the machine.
It appears that this email scam is relying on the Blackhole exploit kit to infect machines.
First released on an underground Russian hacking forum, the Blackhole exploit kit is typically licensed to a user with specific customizations already in place. The Blackhole exploit uses obfuscated JavaScript to determine what vulnerabilities the machine has and then uses Pony, a dropper, to fetch the required binaries for the specific exploit attempt and the payload being deployed. In this case, the payload can be anything once an exploit has been used successfully.
Trojans are a common payload as are many other forms of malware.
Many of the exploits attempted by the Blackhole kit are older browser or Java vulnerabilities that are easily blocked when the latest updates are installed on the machine. However, the exploit kit can be modified easily by the developers and may include some Zero Day exploits as well. Typically, these added features depend on the amount the customer pays for the licensing agreement.
The domains and IPs associated with this latest spam run indicate that it is part of the “Amerika” spam ring.
This scam has recently created spoofed emails appearing to originate from the Walmart.com website and PayPal as well. Other recently reported assaults have spoofed emails from the Better Business Bureau, the United States Postal Service, and the payroll company ADP. Amerika appears to be using US-based servers at first glance but recent reports indicate that it may very well be a Russian based attack.
Skype…not so private anymore?
26.05.13
Skype has had the VOIP market in its pocket for a long time. With over 50 million people using Skype across a variety of mediums on a daily basis, Skype’s success is undisputed. Offering applications for Windows, Mac, iOS, and Android, consumers can stay connected via VOIP calls or video chat from just about anywhere in the world. The service uses a complex audio/video management system that has held a reputation for years as being very secure. According to many experts, that all changed on a fateful day in May of 2011 when Skype was acquired by Microsoft for $8.5 billion. Microsoft has made many improvements to the Skype platform since acquiring it almost two years ago. Recently, Skype for Linux was released giving Skype true cross-platform bragging rights.
Multiple updates have also been pushed to both the Windows and OSX platforms which included integration of Facebook calling.
Although perhaps not appreciated by many users, Microsoft has improved the in-app advertising campaign of the program for the free version of the program.
Consumers that have a paid subscription are not currently subjected to these advertisements but Microsoft has hinted at changing that in the near future. Another major change that Microsoft has made involves the Skype infrastructure. Originally created as a peer to peer service that was distributed amongst users, Microsoft has centralized much of the service into dedicated data centers around the world. Although this infrastructure change reduces bandwidth strain and improves stability, it is this centralization that has security experts worried about user privacy.
The fear is that Microsoft has funneled all Skype traffic through its own data centers in an attempt to intercept every conversation. The US government, operating under the protection of the Patriot Act, has been known to request access to this type of information from all major communication service providers in recent years.
An independent German security firm has confirmed that every HTTPS URL sent over Skype is actively being checked by an IP address that is registered to the US Microsoft headquarters.
Microsoft’s response to this accusation is that scanning is performed to remove spam and phishing links from Skype messages using its Smart Screen algorithms. This response is not satisfactory to most considering that the Skype program actively removes these links on its own through the client interface. Even if the claims from Microsoft are true, the reality is that in order to properly sniff Skype requests, the entire message needs to be decrypted first.
Many users rely on Skype because of its “end to end” encryption methods.
Skype did offer end to end encryption when it still relied on a semi-distributed, peer to peer architecture. Unfortunately, Microsoft has taken this security measure away from users – even if they have the best intentions. It may be difficult to prove that Microsoft is working with the US government by providing message contents, however, the fact remains that the security of the service has been compromised by centralizing data transmissions through Microsoft owned data centers and the company’s admission to using Smart Screen technology to sniff for malicious URLs.
Chinese Hackers Compromise U.S. Weapons Designs
31.05.13
Chinese cybercriminals have made the news yet again. This time it appears that they have gained access to the Department of Defense systems that govern some of the U.S. Military’s weapons secrets. The Defense Science Board, a division of the Pentagon, released a confidential report that disclosed the leak and listed over two dozen weapons systems that were compromised during this attack. Even the public version of the report referred to the threat as serious and went so far as to compare the situation to the “nuclear threat of the Cold War.” Although the report did not reveal all weapons systems that were compromised, an advanced version of the Patriot missile system, the F/A-18 Hornet fighter jet, and the Black Hawk helicopter were all mentioned.
Missile defense systems currently deployed by the U.S. in Asia were also cited as being compromised in the attack. Although many of these systems are well-known throughout the world already, the inner workings of the designs, many of which are still classified, are now available to the Chinese for whatever purposes they desire. Just possessing this information will save the Chinese government decades of research and billions of dollars in development costs.
Earlier this year, President Obama demanded that the Chinese stop its cyber-espionage campaign.
Apparently, the demand went unnoticed as the attacks seem to be more frequent and more severe recently. The Pentagon pointed the finger at China last month regarding a string of intrusions that occurred in 2012 aimed at uncovering the U.S. Governments foreign policies and military plans.
 The exact group of people responsible for these attacks is still unknown. However, a large percentage of the recent attacks have been reportedly originating from an office building in Shanghai that is known to have ties to the People’s Liberation Army.
The exact group of people responsible for these attacks is still unknown. However, a large percentage of the recent attacks have been reportedly originating from an office building in Shanghai that is known to have ties to the People’s Liberation Army.
Even scarier is the fact that the government offices affected by these attacks are often not aware that an attack has even occurred until the FBI notifies them that there was a breach.
This is a testament to the advanced techniques being used by the Chinese to gather intelligence about the U.S Government, its policies, and now even its weapons. A Chinese Defence Ministry spokesperson has claimed that the Chinese government has no involvement with this latest series of attacks; however, this is often the stance taken by the Chinese in similar matters. Despite multiple warnings in recent years, the Chinese seem determined to reduce the U.S. military advantage through these cyber-espionage tactics.
A recent National Intelligence Estimate on these activities concluded that China is actively stealing intellectual property from U.S. companies and the military.
Even the recent Zero-Day IE8 watering hole attack on the Department of Energy has been traced back to suspected Chinese hackers working under orders of the government. Although these crimes form a long pattern that has gone on for years, this attack raises the bar in the shear depth of the breach and the classified information that has been compromised as a result. Without immediate action, the U.S. may have to consider a complete overall of the security measures in place that safeguard the very military secrets that make this nation secure.

▼ Show Discussion