Internet Security - designed to protect
![]() Written by Tomas Meskauskas on (updated)
Written by Tomas Meskauskas on (updated)
What is Internet Security?
'Internet Security designed to protect' is a rogue computer program derived from the same family of misleading programs as Internet Security 2012, Privacy Protection, and many others. Internet Security is installed on users' systems using various rogue methods, and commonly, these fake security programs are proliferated using Trojans and 'exploit kits'.
Firstly, the Trojan infects the system via any detected security vulnerabilities (for example, within Flash, Java, etc.), and then it downloads and installs the Internet Security software without the user's permission. After Internet Security is installed on your PC, it performs a fake security scan and displays a wide variety of fake security warning pop-ups.
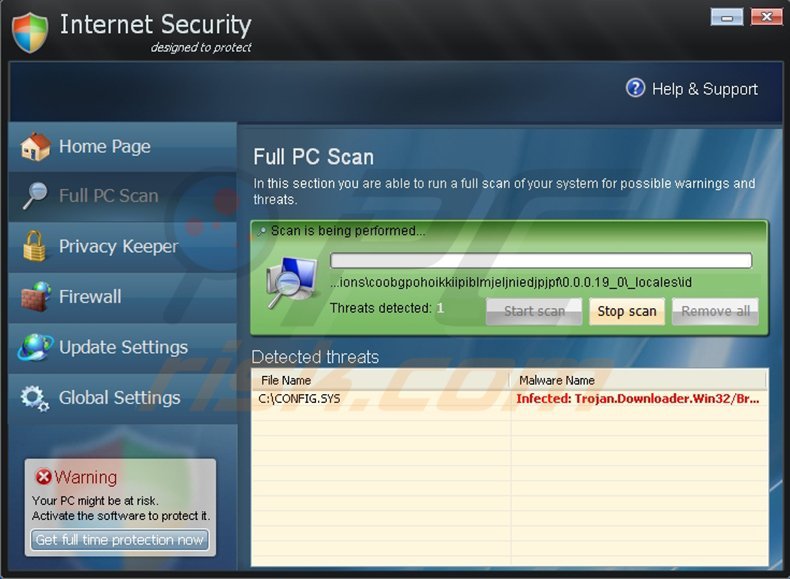
This rogue security scanner should not be trusted, and moreover, you should not pay for the 'full version'. This is a scam, and paying for the license key is equivalent to sending your money to cyber criminals.
Note that by paying for this scam, you not only send your money to criminals, but also divulge your banking information - a situation that could result in further money stolen from your credit card account.
The Internet Security 'designed to protect' rogue antivirus software originates from a family called FakeRean (similar to Win 8 Antivirus 2013 and Win 7 Antivirus 2013). The correct way to deal with this bogus software is to eliminate it from your computer.
Internet Security "designed to protect" is developed to scare unsuspecting users into believing that their computers have serious security-related infections. In fact, Internet Security "designed to protect" has nothing in common with legitimate antivirus programs and the 'scans' performed by this program are fake.
Internet Security is a scam that attempts to sell a non-existent 'full version'. If you click the 'Remove All' button after the 'security scan' performed by this rogue software, you are redirected to a website and encouraged to, firstly, enter your banking information, and secondly, purchase a license for the software in order to remove the 'detected' security threats.
Be aware that the only security threat you should be worried about is Internet Security itself. Ignore the security scans and warning messages displayed by this rogue program and remove it from your computer.
If you have already paid the license fee for Internet Security 'designed to protect', contact your credit card company and dispute the charges, explaining that you have been tricked into purchasing a fake computer antivirus program. To remove this rogue from your computer, use the removal guide provided.
Note that Internet Security 'designed to protect' desktop icons sometimes use the following names: Internet Security Pro, Internet Security Pro 2013, Internet Security 2014, etc. This removal guide is relevant when dealing with any variant of this fake antivirus program.
Fake security warning messages such as this are displayed by Internet Security 'designed to protect':
"Your PC might be at risk. Activate the software to protect it."
"Attention! We strongly recommend that you activate for the safety and faster running of your PC"
"Security Warning! Malicious program has been detected. Click here to protect your computer"
"File is infected by W32/Blaster.worm Please activate to protect your computer""Firewall Warning Hidden file transfer to remote host has been detected Internet Security has detected a leak of your file through the Internet. We strongly recommend that you block the attack immediately."
"Internet Security "designed to protect" has found 36 useless and UNWANTED files on your computer! Potentially dangerous files were found on your system during the last scan! It is strongly recommended that you remove them immediately"
"Activate Internet Security "designed to protect", make your PC free from all kinds of threats"
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Quick menu:
- What is Internet Security?
- STEP 1. Remove Internet Security using a registration key.
- STEP 2. Remove Internet Security using Safe Mode with Networking.
Internet Security "designed to protect" removal:
Step 1
Before downloading: Click the "Get full protection now" button located at the bottom left corner of the main window of Internet Security "designed to protect", in the registration window enter a dummy email address, and in the registration key field, enter Y68REW-T76FD1-U3VCF5A, and then click "Confirm activation":
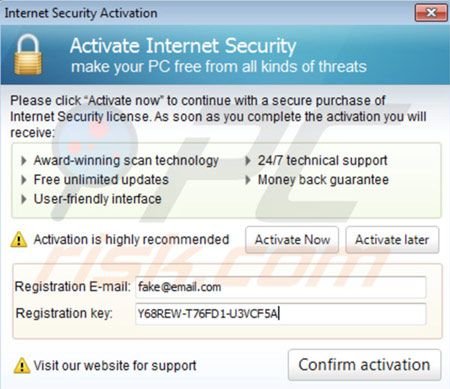
Successful registration of Internet Security "designed to protect":
Internet Security "designed to protect" after successful registration:
Please note that registering Internet Security "designed to protect" will not remove it, it will simply enable execution of programs and some other Windows features. This step is optional, however, since it can make the removal process less complicated. To completely remove Internet Security "designed to protect" from your PC, proceed to the next step.
Step 2
Download recommended malware removal software to completely remove Internet Security "designed to protect" from your computer.
NOTE: If you cannot run or download the removal tool, download the registry fix file. It enables execution of applications. Click on the link below, and when download completes, click run, click yes, and then OK.
Download registry fix:
Windows 7 users:
Windows XP users:
Windows 8 users:
Windows Vista users:
If you cannot install the anti-spyware software, try to download a custom anti-spyware software installer built by our technicians to bypass spyware infections and install security software regardless.
Optional method (browser access disabled):
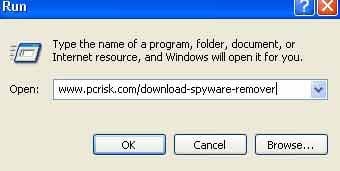
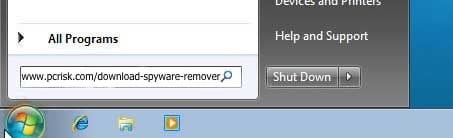
If you cannot access your Internet browsers (Internet Explorer, Google Chrome, or Mozilla Firefox): Click Start then click Run. (Click Windows logo in Windows 7 and Windows Vista)
In Windows XP, When the Run dialogue appears, enter this text, www.pcrisk.com/download-spyware-remover, and then press ENTER. In Windows 7 and Windows Vista, type this text directly into the search field and then press ENTER.
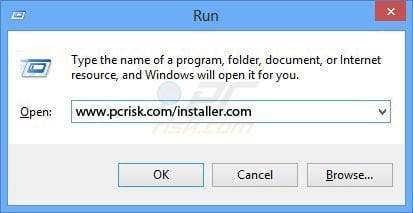
Windows 8 users: On your keyboard, press Windows key + R, The Run window will pop up. In the opened "Run" window type: www.pcrisk.com/installer.com and then press ENTER
After pressing enter, the "File Download" dialog of the recommended malware removal software will appear. Click Run and follow the on-screen instructions.
Internet Security "designed to protect" removal using Safe Mode with Networking:
1. Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer starting process press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, then select Safe Mode with Networking from the list.
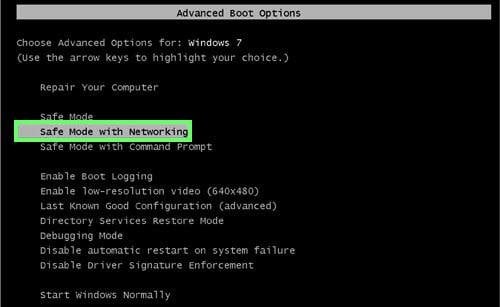
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Go to the Windows 8 Start Screen, type Advanced, in the search results select Settings. Click on Advanced Startup options, in the opened "General PC Settings" window select Advanced Startup. Click on the "Restart now" button. Your computer will now restart into "Advanced Startup options menu".
Click on the "Troubleshoot" button, then click on "Advanced options" button. In the advanced option screen click on "Startup settings". Click on the "Restart" button. Your PC will restart into the Startup Settings screen. Press "5" to boot in Safe Mode with Command Prompt.
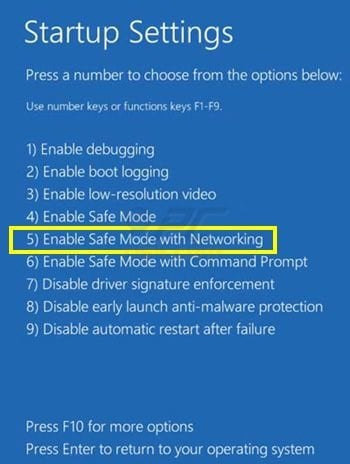
Video showing how to start Windows 8 in "Safe Mode with Networking":
2. Download the fix.reg file After saving the file to your desktop, double click fix.reg and then click YES to confirm.
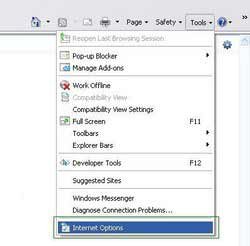
3. Open Internet Explorer, click Tools and select Internet Options. Select "Connections".
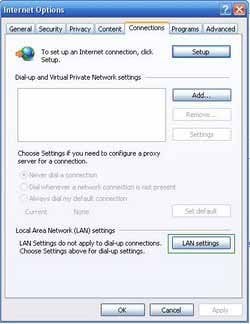
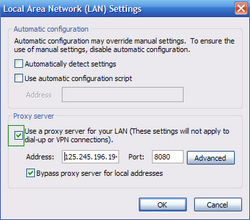
4.Click LAN settings, if 'Use a proxy server for your LAN' is checked, uncheck it and press OK.
5. Download legitimate anti-spyware software to fully remove Internet Security 'designed to protect' from your PC. Download recommended malware removal software to remove Internet Security designed to protect.
Other tools known to remove Internet Security 'designed to protect':
Summary:
The fake antivirus programs (also known as "rogue antivirus programs" or "scareware") are applications that tries to lure computer users into paying for their non-existent full versions to remove the supposedly detected security infections (although the computer is actually clean). These bogus programs are created by cyber criminals who design them to look as legitimate antivirus software. Most commonly rogue antivirus programs infiltrate user's computer using poop-up windows or alerts which appear when users surf the Internet. These deceptive messages trick users into downloading a rogue antivirus program on their computers. Other known tactics used to spread scareware include exploit kits, infected email messages, online ad networks, drive-by downloads, or even direct calls to user's offering free support.
A computer that is infected with a fake antivirus program might also have other malware installed on it as rogue antivirus programs often are bundled with Trojans and exploit kits. Noteworthy that additional malware that infiltrates user's operating system remains on victim's computer regardless of whether a payment for a non-existent full version of a fake antivirus program is made. Here are some examples of fake security warning messages that are used in fake antivirus distribution:
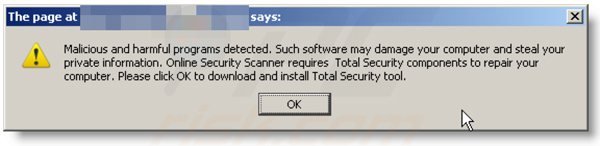
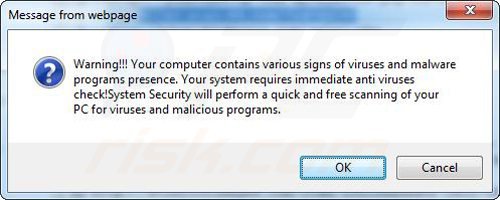
Computer users who are dealing with a rogue security software shouldn't buy it's full version. By paying for a license key of a fake antivirus program users would send their money and banking information to cyber criminals. Users who have already entered their credit card number (or other sensitive information) when asked by such bogus software should inform their credit card company that they have been tricked into buying a rogue security software. Screenshot of a web page used to lure computer users into paying for a non-existent full version of internet security rogue and other rogue antivirus programs:
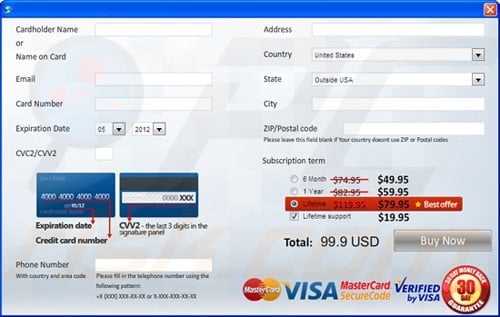
To protect your computer from internet security rogue and other rogue antivirus programs users should:
- Keep their operating system and all of the installed programs up-to-date.
- Use legitimate antivirus and anti-spyware programs.
- Use caution when clicking on links in social networking websites and email messages.
- Don't trust online pop-up messages which state that your computer is infected and offers you to download security software.
Symptoms indicating that your operating system is infected with a fake antivirus program:
- Intrusive security warning pop-up messages.
- Alerts asking to upgrade to a paid version of a program to remove the supposedly detected malware.
- Slow computer performance.
- Disabled Windows updates.
- Blocked Task Manager.
- Blocked Internet browsers or inability to visit legitimate antivirus vendor websites.
If you have additional information on internet security rogue or it's removal please share your knowledge in the comments section below.


▼ Show Discussion