Zorton Win 8 Protection 2014
![]() Written by Tomas Meskauskas on (updated)
Written by Tomas Meskauskas on (updated)
What is Zorton Win 8 Protection 2014?
Zorton Win 8 Protection 2014 is a fake security scanner originating from a family of rogue antivirus software called Braviax/FakeRean.
This program was developed by cyber criminals to scare PC users into believing that their computers are infected with high-risk malware and then coerce them into purchasing a 'full version' of Zorton Win 8 Protection 2014 to supposedly eliminate the threats.
This rogue program performs no scans for computer security infections - it merely imitates this process and then displays a false detection list. Furthermore, this malicious software modifies the operating system, disables execution of installed programs, and disables the Task Manager.
When computers are infected with Zorton Win 8 Protection 2014, users are unable to access Internet - this rogue program blocks access to websites, reports that they are infected, and then offers to run a security scan.
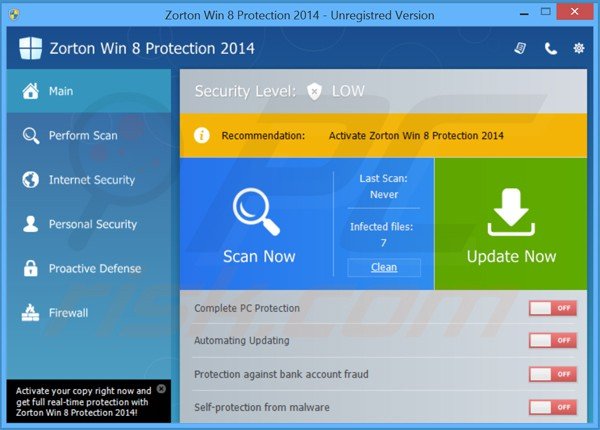
This program has a professional-look user interface, however, any similarities with legitimate antivirus programs end at this point. Zorton Win 8 Protection 2014 holds no virus scan engine or virus definition database - it simply generates and displays identical virus detection lists and warning pop-ups on all computers infiltrated.
This fake security scanner is capable of changing its name (all rogue antivirus programs from the Braviax/FakeRean family have this ability). For example, an infected computer running the Windows 7 operating system will appear as Zorton Win 7 Antivirus 2014 or Zorton Win 7 Protection 2014.
Zorton Win 8 Protection 2014 is a scam created by cyber criminals, the sole purpose of which is to sell a useless license key, which supposedly eliminates security infections (that do not actually exist on the user's computer).
None of the information displayed by this program should be trusted (including fake security scans, fake malware detection lists, or fake security warning messages). Commonly, bogus antivirus programs from the Braviax/FakeRean family are proliferated using Trojans and fake online security scanners.
If you discover a website displaying a security warning message or security scan claiming that your PC is infected, do not download any software offered - this is a popular method employed by cyber criminals to distribute their rogue antivirus programs.
If your PC is infiltrated with Zorton Win 8 Protection 2014, use the removal guide provided to eliminate this scam from your computer.
Examples of fake security warning messages displayed by Zorton Win 8 Protection 2014:
“System security threat was detected. Viruses and/or spyware may be damaging your system now. Prevent infection and data loss or stealing by running a free security scan”
“Zorton Win 8 Protection 2014 has blocked a program from accessing the internet - This program is infected with Trojan-BNK.Win32.Keylogger.gen Private data can be stolen by third parties, including credit card details and passwords”
“Zorton Win 8 Protection 2014 Alert - System Hacked! Unknown program is scanning your system registry right now! Identity theft detected”
“Tracking software found! Your PC activity is being monitored. Possible spyware infection. Your data security may be compromised. Sensitive data can be stolen. Prevent damage now by completing a security scan”
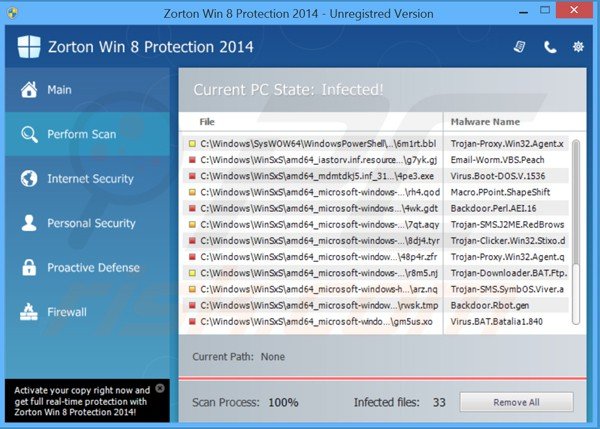
Zorton Win 8 Protection 2014 rogue antivirus software performing a fake computer security scan:
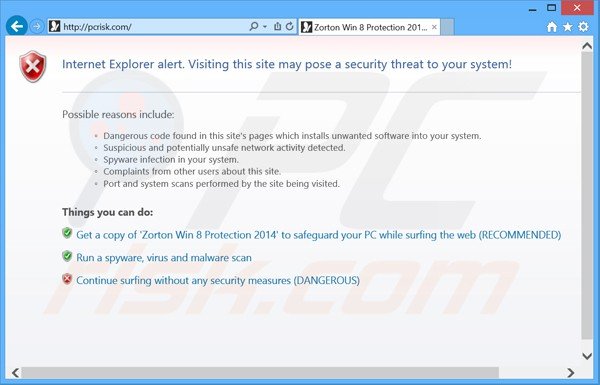
Zorton Win 8 Protection 2014 blocking Internet access:
Internet Explorer alert. Visiting this site may pose a security threat to your system!
Possible reasons include:
Dangerous code found in this site’s pages which installs unwanted software into your system.
Suspicious and potentially unwanted network activity detected.
Spyware infection in your system.
Complaints from other users about this site.
Port and system scans performed by the site being visited.Things you can do:
Get a copy of “Zorton Win 8 Protection 2014” to safeguard your PC while surfing the web (RECOMMENDED)
Run a spyware, virus and malware scan
Continue surfing without any security measures (DANGEROUS)
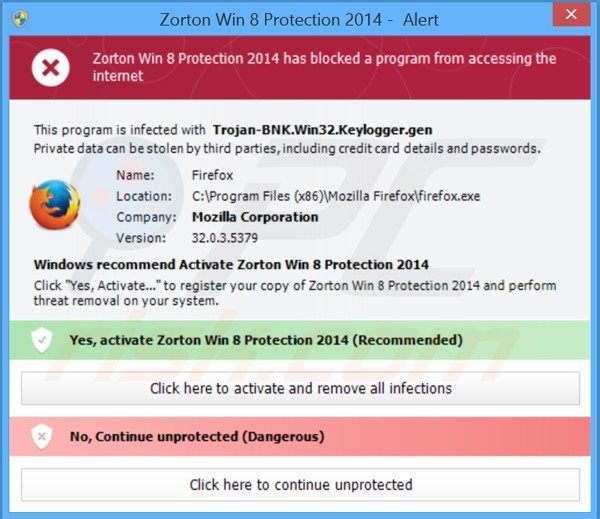
Zorton Win 8 Protection 2014 blocking execution of installed programs:
Zorton Win 8 Protection 2014 has blocked a program from accessing the Internet. This program is infected with Trojan-BNK.Win32.Keylogger.gen Private data can be stolen by third parties, including credit card detail and passwords.
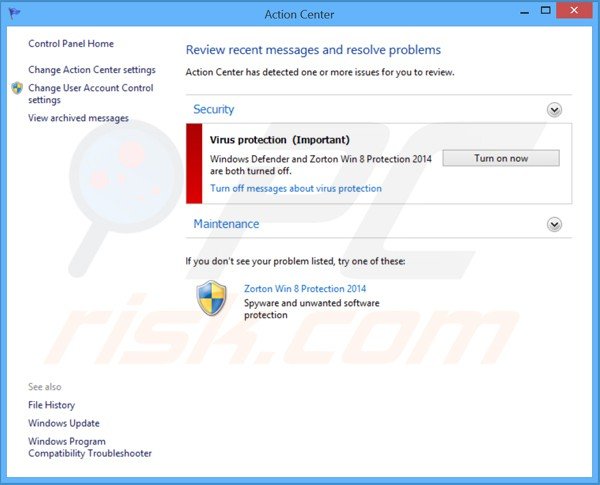
Zorton Win 8 Protection 2014 displaying a fake Windows Action Center:
Action Center has detected one or more issues for you to review. Windows Defender and Zorton Win 8 Protection 2014 are both turned off.
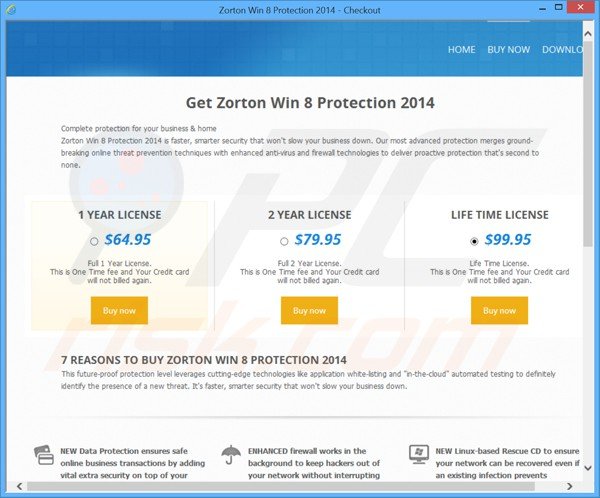
A website used by cyber criminals to scam computer users into purchasing a license key for the Zorton Win 8 Protection 2014 fake antivirus program:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Quick menu:
- What is Zorton Win 8 Protection 2014?
- STEP 1. Remove Zorton Win 8 Protection 2014 using Safe Mode with Networking.
- STEP 2. Optional Zorton Win 8 Protection 2014 removal method.
- STEP 3. Manual Zorton Win 8 Protection 2014 removal.
Zorton Win 8 Protection 2014 removal:
Go to the Windows 8 Start Screen, type Advanced. In the search results, select Settings. Click Advanced Startup options. In the opened "General PC Settings" window, select Advanced Startup. Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu".
Click the "Troubleshoot" button, then click the "Advanced options" button. In the advanced option screen, click "Startup settings". Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press "5" to boot in Safe Mode with Networking.
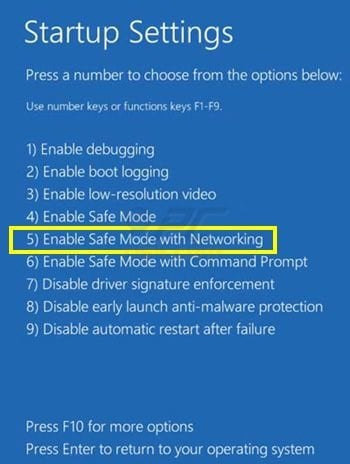
Video showing how to start Windows 8 in "Safe Mode with Networking":
After booting your computer in Safe Mode with Networking, try downloading and running the recommended antimalware software. If the download is blocked, follow the instructions presented below.
IMPORTANT! Zorton Win 8 Protection 2014 rogue antivirus damages Windows Security Center and Windows Defender services. After removing this fake antivirus program, download the registry fixes presented below. After downloading, double-click each and click Yes (when asked to merge data).
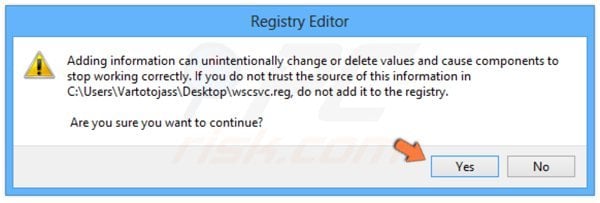
NOTE: If you cannot run the remover, try to right-click over it and select "Run as administrator". If the installation of the malware remover fails, or you cannot open the .exe files, try one of the alternative download locations below:
- Location 1 (the file is renamed to "iexplore.exe", since most spyware does not block this file)
- Location 2
If, after or before, removal of this fake antivirus program, you are unable to run any of your installed software, Zorton Win 8 Protection 2014 has modified your operating system's .exe file associations.
To fix this, download the registry fix (link below). Save it to your computer, double click it, click "Yes", and then "OK". After rebooting your PC, file associations should function normally.
If you cannot open your browser (Internet Explorer, Mozilla Firefox, Google Chrome):
Zorton Win 8 Protection 2014 hijacks Internet browsers, modifies registry settings, and disables execution of programs. In these cases, our developers have created a custom installer - useful when you are unable to browse the Internet or execute .exe files. It starts like an MS-Dos program, runs some registry fixes, and then initiates execution of an installer.
This installer was tested on the Windows 7, Windows Vista, and XP operating systems infected with the most common spyware infections.
To use this installer, right-click in the lower left corner of the screen, in the Quick Access Menu, select Run.
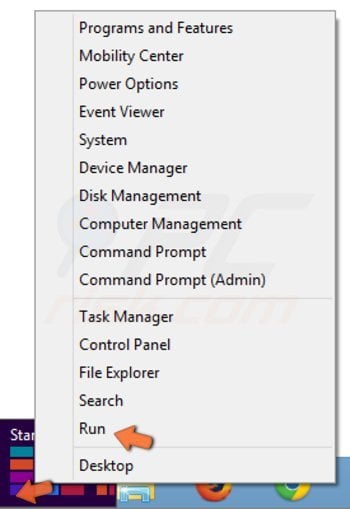
In the Search field, enter this link: www.pcrisk.com/installer.com and then press ENTER.
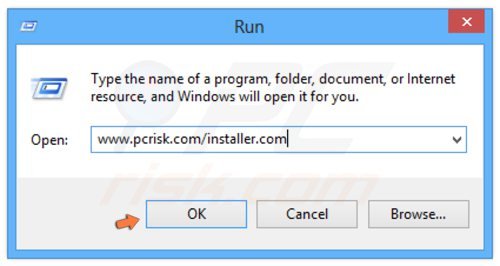
Zorton Win 8 Protection 2014 generates a fake warning after pressing ENTER. Please ignore this and click "No, stay unprotected..." on this message.
File download dialogue will appear reporting that you are downloading the file, installer.com. Click Run, wait for download to complete, and then follow the on-screen instructions. Windows may warn you that opening unknown files may be unsafe. Please ignore these warnings.
If your Internet browsers work, you can use this button to download the customized installer.
IMPORTANT! Zorton Win 8 Protection 2014 rogue antivirus damages Windows Security Center and Windows Defender services. After removing this fake antivirus program, download the registry fixes presented below. After downloading, double-click each and click Yes (when asked to merge data).
If installation or downloading fails:
If you are still unable to run or download the removal tool, download the registry fix file. It enables normal execution of applications and fixes web browser errors. Click on the link below, and when download completes, click run, click yes, and then OK.
If installation of the malware remover fails, try our Customized installer built by our technicians to bypass infections and install removers regardless.
If you cannot access your Internet browsers using the infected computer, use a clean system to download this remover and use removable media (such as a CD, USB, etc.) to transfer it to the infected PC.
Note that this rogue also blocks execution of programs. If you are using a clean PC to download the remover, also download the registry fix (download link below) provided. Transfer both files to the infected machine, first run the registry fix, and then run the full scan with the recommended remover.
Zorton Win 8 Protection 2014 removal (optional method):
Zorton Win 8 Protection 2014 rogue program blocks execution of all installed software - this makes its removal complicated. The best way to eliminate this rogue is to login to an unaffected user account and run a security scan from it. If available, login to a "Guest" account and follow the removal steps provided below. If your "Guest" user account is not activated, follow these steps:
Right-click in the lower left corner of the screen, in the Quick Access Menu, select Control Panel.
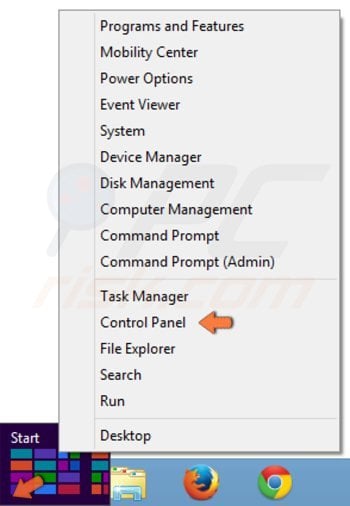
In the opened window, click "Change account type" (under "User Accounts and Family Safety").
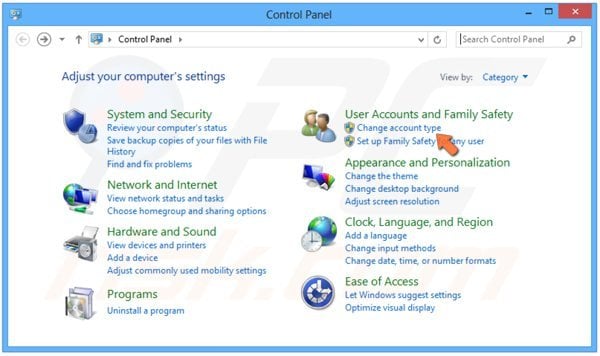
In the opened window, click "Guest".
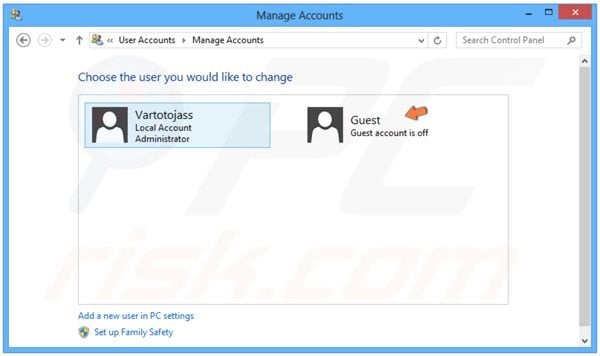
In the next window, click the "Turn On" button.
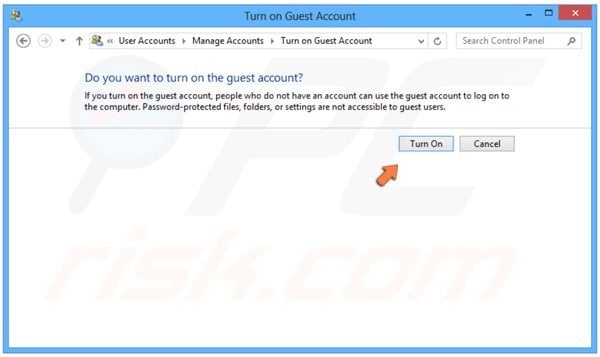
Restart your PC, when the Windows logon screen appears, select the "Guest" user, then continue with the removal steps provided below.
After logging into your Guest account, download recommended malware removal software and run a full system scan to completely eliminate this fake antivirus software from your PC.
Manual Zorton Win 8 Protection 2014 removal instructions
Some spyware can block downloading of spyware removers. If you cannot download it using the default location, try one of the alternative download locations below:
- Location 1 (the file is renamed to "iexplore.exe", since most spyware does not block this file)
- Location 2
If installation of the remover fails, try downloading the customized installer built by our technicians to bypass spyware infections. Download customized installer
If you still cannot download or run the spyware removing software, perform these steps:
Step 1
Download the registry fix for Zorton Win 8 Protection 2014 malware. This fix removes registry entries that disallow execution of programs in some variants of this spyware. To download it, click the link below. After downloading, double click win8_av_fix.reg file, click Yes, and then click OK.
Step 2
Some variants of this spyware modify the system proxy settings so that you are unable to access the Internet (or website addresses are redirected to malicious or phishing websites). To reset the proxy settings to default, download and run this tool:
Step 3
Zorton Win 8 Protection 2014 modifies the system Hosts file. The Hosts file is used to resolve canonical names of websites to IP addresses. When it is changed, the user may be redirected to malicious sites, despite seeing legitimate URLs in the address bar. It is difficult to determine if sites are genuine when the Hosts file is modified.
To fix this, download the Microsoft Fix It tool, which restores your Hosts file to the Windows default. Run this tool when downloaded and follow the on-screen instructions. Download link below:
Step 4
That's It! You can now try to download the Malware remover or install and run it if already downloaded.
IMPORTANT! Zorton Win 8 Protection 2014 rogue antivirus damages Windows Security Center and Windows Defender services. After removing this fake antivirus program, download the registry fixes presented below. After downloading, double-click each and click Yes (when asked to merge data).

Other tools known to remove Zorton Win 8 Protection 2014:
Summary:
The fake antivirus programs (also known as "rogue antivirus programs" or "scareware") are applications that tries to lure computer users into paying for their non-existent full versions to remove the supposedly detected security infections (although the computer is actually clean). These bogus programs are created by cyber criminals who design them to look as legitimate antivirus software. Most commonly rogue antivirus programs infiltrate user's computer using poop-up windows or alerts which appear when users surf the Internet. These deceptive messages trick users into downloading a rogue antivirus program on their computers. Other known tactics used to spread scareware include exploit kits, infected email messages, online ad networks, drive-by downloads, or even direct calls to user's offering free support.
A computer that is infected with a fake antivirus program might also have other malware installed on it as rogue antivirus programs often are bundled with Trojans and exploit kits. Noteworthy that additional malware that infiltrates user's operating system remains on victim's computer regardless of whether a payment for a non-existent full version of a fake antivirus program is made. Here are some examples of fake security warning messages that are used in fake antivirus distribution:
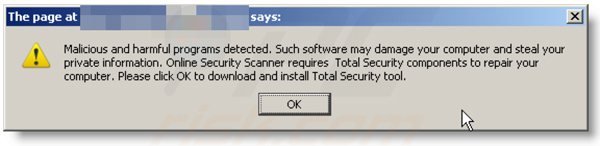
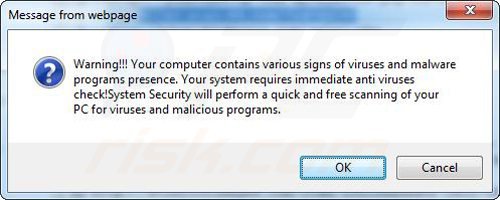
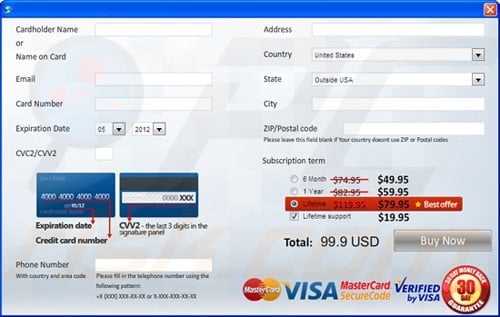
Computer users who are dealing with a rogue security software shouldn't buy it's full version. By paying for a license key of a fake antivirus program users would send their money and banking information to cyber criminals. Users who have already entered their credit card number (or other sensitive information) when asked by such bogus software should inform their credit card company that they have been tricked into buying a rogue security software. Screenshot of a web page used to lure computer users into paying for a non-existent full version of zorton win 8 protection 2014 scam and other rogue antivirus programs:
To protect your computer from zorton win 8 protection 2014 scam and other rogue antivirus programs users should:
- Keep their operating system and all of the installed programs up-to-date.
- Use legitimate antivirus and anti-spyware programs.
- Use caution when clicking on links in social networking websites and email messages.
- Don't trust online pop-up messages which state that your computer is infected and offers you to download security software.
Symptoms indicating that your operating system is infected with a fake antivirus program:
- Intrusive security warning pop-up messages.
- Alerts asking to upgrade to a paid version of a program to remove the supposedly detected malware.
- Slow computer performance.
- Disabled Windows updates.
- Blocked Task Manager.
- Blocked Internet browsers or inability to visit legitimate antivirus vendor websites.
If you have additional information on zorton win 8 protection 2014 scam or it's removal please share your knowledge in the comments section below.


▼ Show Discussion