Locker Virus
![]() Written by Tomas Meskauskas on (updated)
Written by Tomas Meskauskas on (updated)
What is Locker?
Locker is a ransomware infection that infiltrates computers through various files downloaded from the Internet (relating to fake Flash players and cracked versions of computer games including TeamExtreme Minecraft). After successful infiltration, this malware encrypts user files and demands a ransom payment of 0.1 BTC (bitcoins) within 72 hours to decrypt the compromised files.
The ransom is raised to 1.0 BTC if victims fail to pay within the given time. Locker ransomware encrypts document files (for example .doc, .ppt, and .docx) and image files (.psd, raw, and .jpg) Although crypto ransomware is not a new phenomenon (previous file encrypting ransomware programs were named cryptowall, ctb-locker, cryptolocker, etc.), this variant is unique, since cyber criminals set it to activate at 00:00 25.05.2015 (local time).
Prior to this time, victims are unware that Locker ransomware is present on their computers. This tactic allows cyber criminals to conceal their malicious program from antivirus vendors and malware researchers until the last minute when the malware activates simultaneously on many victims' computers.
This distribution method postpones malware research and antivirus definition updates until a point at which victims have already paid the ransom to regain control of their files. To make matters worse, some variants of Locker ransomware delete the Shadow Volume Copies of victims' files, thus making restoring the files an impossible task.
The name of Locker ransomware varies by version. At time of research, cyber criminals released Locker v1.7, Locker V2.16, Locker v2.60, Locker v3.5.3, Locker v.3.49, and Locker V5.52. The version numbers seem to be random - currently, it is not clear why cyber criminals assign these numbers.
At time of writing, there were no tools available to decrypt the compromised files. Using this removal guide, you will be able to eliminate the Locker ransomware, however, the affected files will remain encrypted.
Before removing the Locker ransomware you are advised to make a backup of the encrypted files and the contents of %PROGRAMDATA%\Digger, %PROGRAMDATA%\rkcl, %PROGRAMDATA%\tor, and %PROGRAMDATA%\steg folders. You should also write down/copy the unique bitcoin wallet address from the Locker ransomware Payment tab.
This information could be useful if malware researchers are able to develop a tool capable of decrypting the files affected by Locker malware in the future. Ransomware infections such as Locker present a strong case to maintain regular backups of your stored data.
Note that paying the ransom as demanded by this ransomware is equivalent to sending your money to cyber criminals - you will support their malicious business model and there is no guarantee that your files will ever be decrypted.
To avoid computer infection with ransomware infections such as this, express caution when opening email messages, downloading files from P2P networks, etc. Always use legitimate antivirus and anti-malware programs.
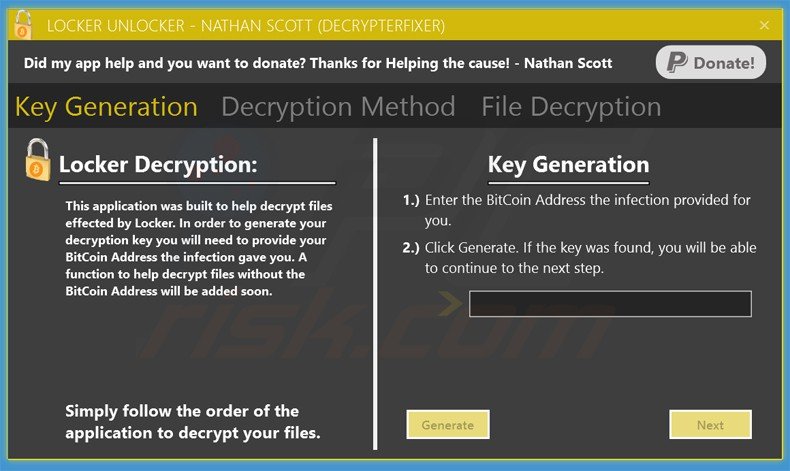
Update June 1, 2015 - The creator of this ransomware has released a database containing all private keys that can be used to decrypt all victims files (Locker Unlocker tool created by Nathan Scott) - download the Locker decrypt tool here.
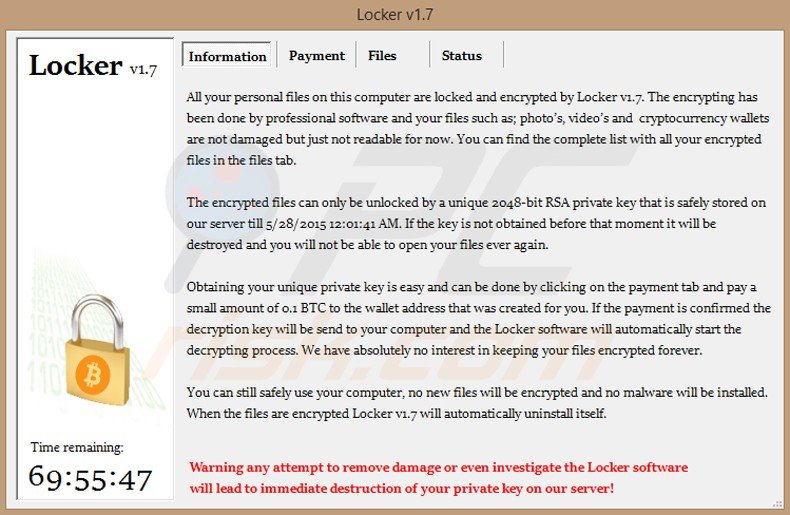
Locker ‘Information’ tab:
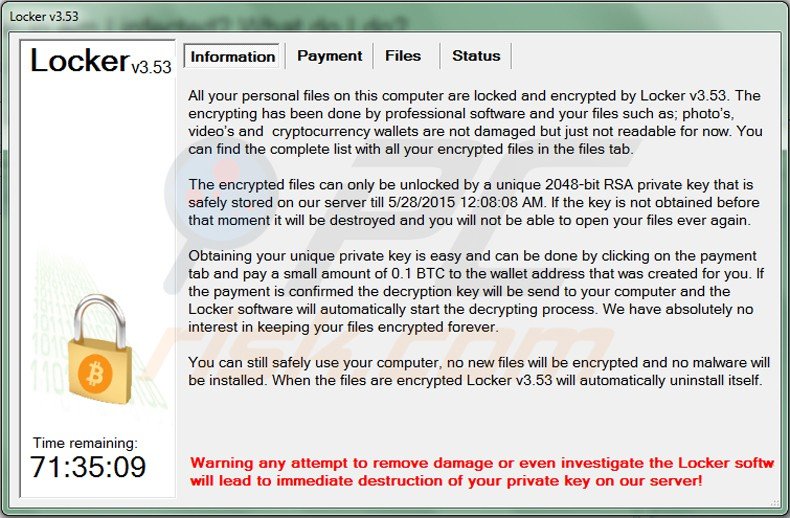
Text presented in the Information tab:
All your personal files on this computer are locked and encrypted by Locker. The encrypting has been done by professional software and your files such as: photos, videos, and crypto currency wallets are not damaged but just not readable for now. You can find the complete list with all your encrypted files in the files tab. The encrypted files can only be unlocked by a unique 2048-bit RSA private key that is safely stored on our server till [DATE]. If the key is not obtained before that moment it will be destroyed and you will not be able to open your files ever again. Obtaining your private unique key is easy and can be done clicking on the payment tab and pay a small amount of 0.1 BTC to the wallet address that was created for you. If the payment is confirmed the decryption key will be sent to your computer and the Locker software will automatically start the decrypting process. We have absolutely not interest in keeping your files encrypted forever. You can still safely use your computer, no new files will be encrypted and no malware will be installed. When the files are encrypted Locker will automatically uninstall itself.
Locker ‘Payment’ tab:
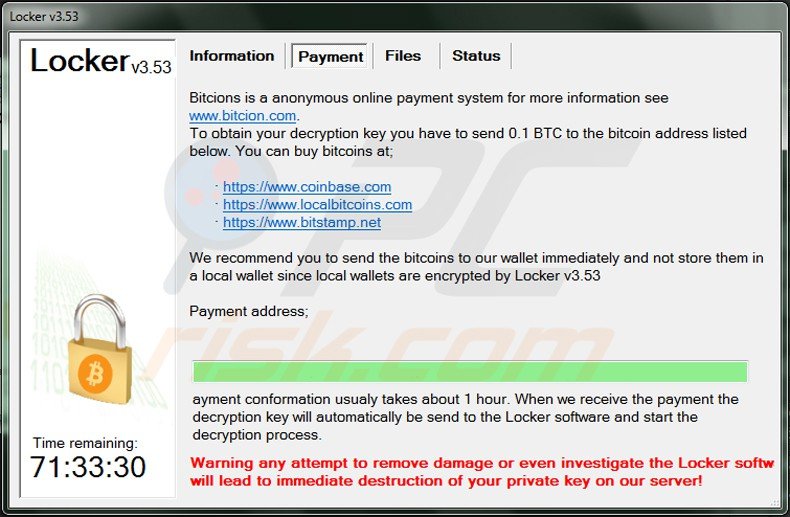
Text presented in the Payment tab:
Bitcoins is a anonymous online payment system for more information see bitcoin.com. To obtain your decryption key you have to send 0.1 BTC to the bitcoin address listed below. We recommend you to send the bitcoins to our wallet immediately and not store them in a local wallet since local wallets are encrypted by Locker. Payment confirmation usually takes about 1 hour. When we receive the payment the decryption key will automatically be send to the Locker software and start the decryption process. Warning any attempt to remove damage or even investigate the Locker software will lead to immediate destrution of your private key on our server!
Update June 1, 2015 - The creator of this ransomware has released a database containing all private keys that can be used to decrypt all victims files - download the Locker decrypt tool here.
Locker ransomware removal:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Quick menu:
- What is Locker?
- STEP 1. Locker ransomware removal using safe mode with networking.
- STEP 2. Locker ransomware removal using System Restore.
Step 1
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, then select Safe Mode with Networking from the list.
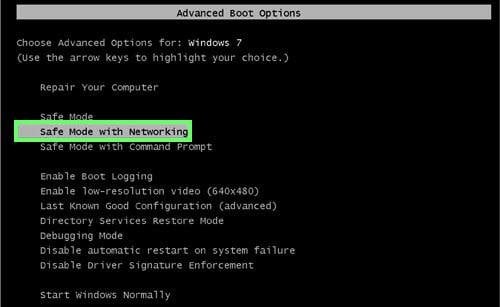
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Go to the Windows 8 Start Screen, type Advanced, in the search results select Settings. Click on Advanced Startup options, in the opened "General PC Settings" window select Advanced Startup. Click on the "Restart now" button. Your computer will now restart into "Advanced Startup options menu".
Click on the "Troubleshoot" button, then click on "Advanced options" button. In the advanced option screen click on "Startup settings". Click on the "Restart" button. Your PC will restart into the Startup Settings screen. Press "5" to boot in Safe Mode with Networking.
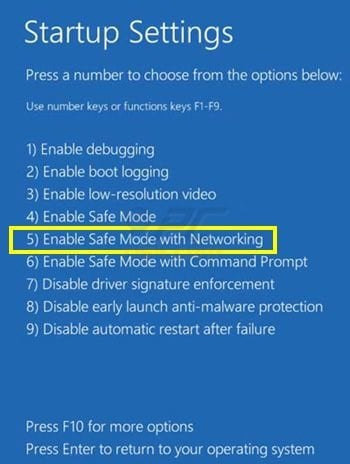
Video showing how to start Windows 8 in "Safe Mode with Networking":
Step 2
Login to the account infected with the Locker. Start your Internet browser and download a legitimate anti-spyware program. Update the anti-spyware software and start a full system scan. Remove all entries detected.
If you cannot start your computer in Safe Mode with Networking, try performing a System Restore.
Video showing how to remove ransomware virus using "Safe Mode with Command Prompt" and "System Restore":
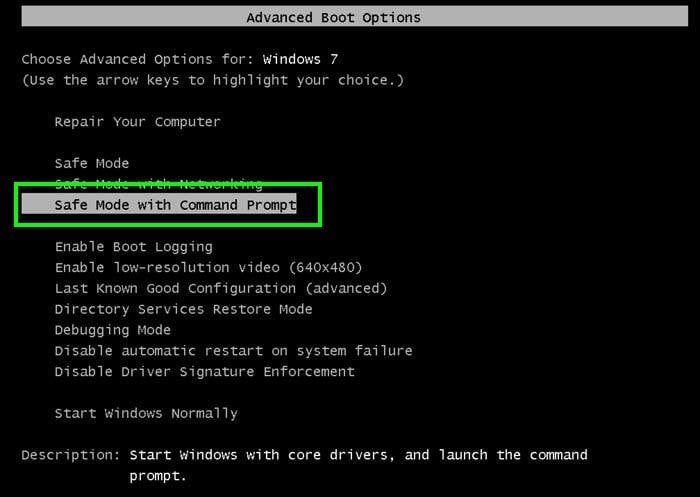
1. During your computer start process, press the F8 key on your keyboard multiple times until the Windows Advanced Options menu appears, and then select Safe Mode with Command Prompt from the list and press ENTER.
2. When Command Prompt mode loads, enter the following line: cd restore and press ENTER.
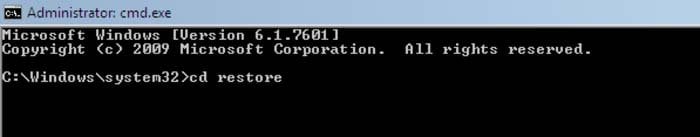
3. Next, type this line: rstrui.exe and press ENTER.
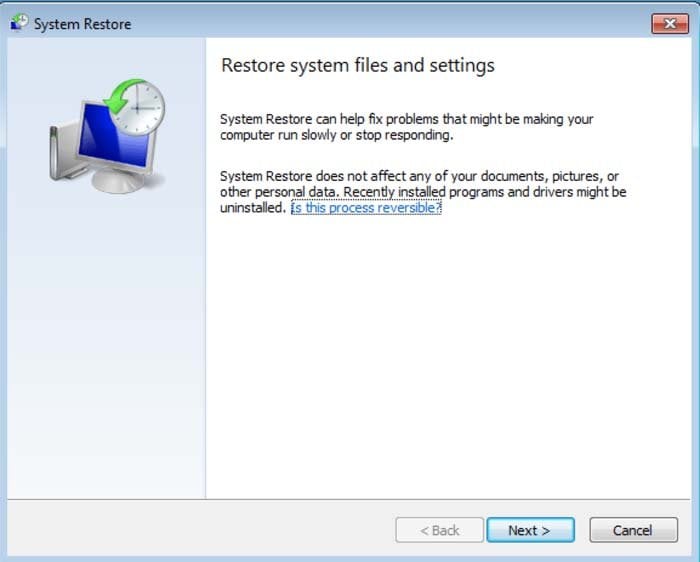
4. In the opened window, click "Next".
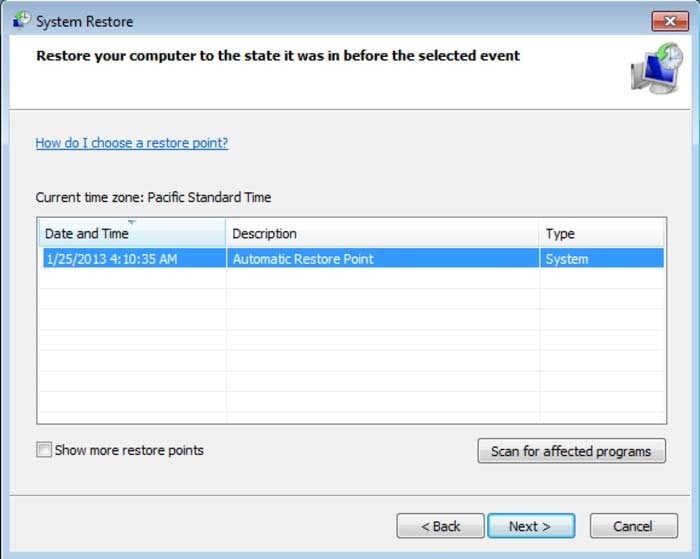
5. Select one of the available Restore Points and click "Next" (this will restore your computer system to an earlier time and date, prior to the Locker ransomware virus infiltrating your PC).
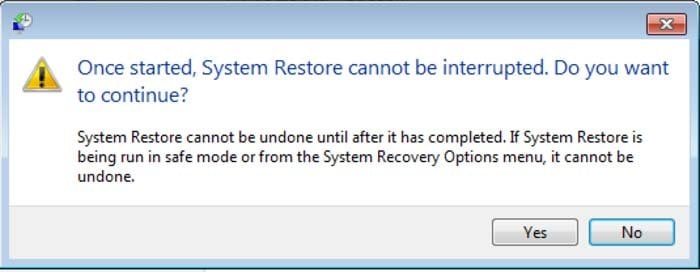
6. In the opened window, click "Yes".
7. After restoring your computer to a previous date, download and scan your PC with recommended malware removal software to eliminate any remaining Locker files.
To restore individual files encrypted by this ransomware, try using the Windows Previous Versions feature. This method is only effective if the System Restore function was enabled on an infected operating system. Note that some variants of Locker are known to remove Shadow Volume Copies of the files, so this method may not work on all computers.
To restore a file, right-click on it, go into Properties, and select the Previous Versions tab. If the relevant file has a Restore Point, select it and click the "Restore" button.
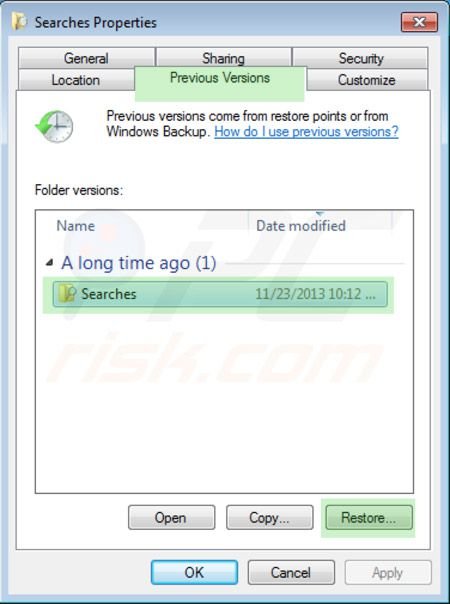
If you cannot start your computer in Safe Mode with Networking (or with Command Prompt), boot your computer using a rescue disk. Some variants of ransomware disable Safe Mode making its removal complicated. For this step, you require access to another computer.
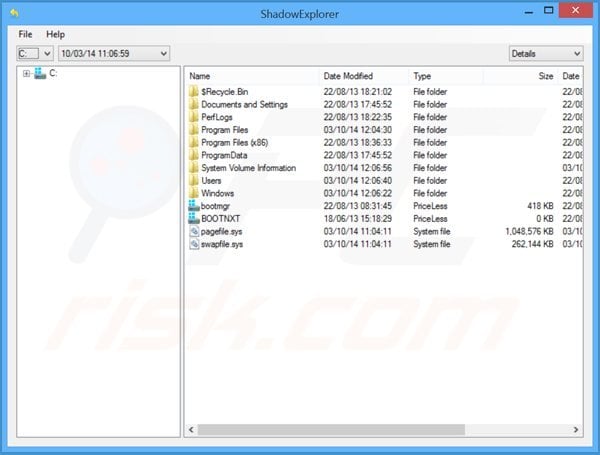
To regain control of the files encrypted by Locker you can also try using a program called Shadow Explorer. More information on how to use this program is available here.
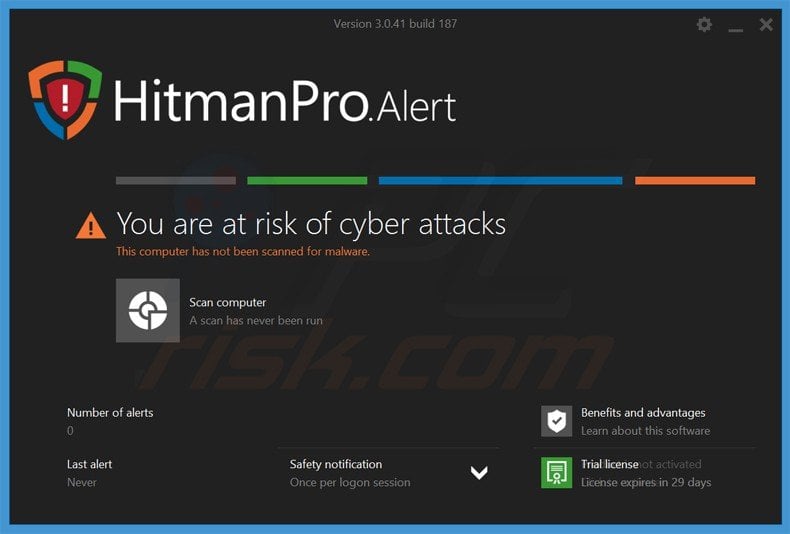
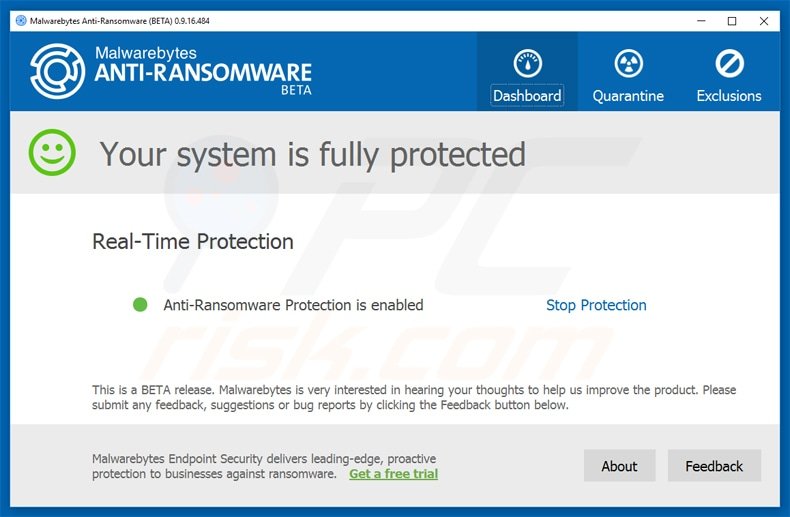
To protect your computer from file encrypting ransomware such as this, use reputable antivirus and anti-spyware programs. As an extra protection method, you can use programs called HitmanPro.Alert and Malwarebytes Anti-Ransomware, which artificially implant group policy objects into the registry to block rogue programs such as Locker.)
Update June 1, 2015 - The creator of this ransomware has released a database containing all private keys that can be used to decrypt all victims files - download the Locker decrypt tool here.
HitmanPro.Alert CryptoGuard - detects encryption of files and neutralises such attempts without need for user intervention:
Malwarebytes Anti-Ransomware Beta uses advanced proactive technology that monitors ransomware activity and terminates it immediately - before reaching users' files:
- The best way to avoid damage from ransomware infections is to maintain regular up-to-date backups. More information on online backup solutions and data recovery software Here.
Other tools known to remove Locker ransomware:


▼ Show Discussion