How to Fix "The requested resource is in use" Error?
![]() Written by Rimvydas Iliavicius on
Written by Rimvydas Iliavicius on
How to Fix "The requested resource is in use" Error in Windows 10
If you're getting "The requested resource is in use" error when trying to open a particular program or copy/move files, then your system was likely infected by a Trojan called SmartService.
SmartScreen is a malicious rootkit. Rootkits are often more difficult to deal with since they are designed to be discreet and make changes to the system unnoticed. Furthermore, the SmartService rootkit prevents specific processes from being terminated that could otherwise stop malicious software from running. Simply put, this Trojan is designed to be as destructive as possible.
This Trojan can infiltrate your system through attachments sent to you via email, through malicious ads clicked on untrusted websites, downloaded and installed files, etc. Removing it from the system is difficult, and it is often hard to ascertain if the computer is actually infected.
Nevertheless, it is possible to remove SmartScreen, and you should do before it causes any damage (or any further damage). This guide shows how to remove this Trojan, ensure that your system is safe, and remove the "The requested resource is in use" error.
Video Showing How to Fix "The requested resource is in use" Error:
Table of Contents:
- Introduction
- Start Windows in Safe Mode
- Scan Your System Using Third-Party Antivirus Software
- Uninstall Malicious Software Using Windows Application Wizard
- Stop Malicious Software From Running on Startup
- Check for Malicious IP Addresses
- Remove Malicious Entries Using Registry Editor
- Video Showing How to Fix "The requested resource is in use" Error
Start Windows in Safe Mode
Safe Mode is a diagnostic start-up mode in Windows operating systems used to obtain limited access to Windows when the operating system does not start or function normally. It is the opposite of Normal Mode, which starts Windows in the usual manner.
One of the most common steps when troubleshooting a computer is to boot into Safe Mode. Safe Mode starts Windows in a basic state, using a limited set of files and drivers. It can help to troubleshoot problems on your computer. If, for example, the problem does not occur in Safe Mode, this will confirm that the default settings and basic device drivers are not causing the issue.
Safe Mode is also a good way to prevent Trojans from blocking your antivirus software. You can start Windows in Safe Mode using System Configuration tool or by applying one of the methods described in this guide.
To start Windows in Safe Mode using the System Configuration tool (which is used to configure how a computer starts and which programs and Windows services load), press the Windows (Win) key + R or type "run" in Search and click the "Run" result.
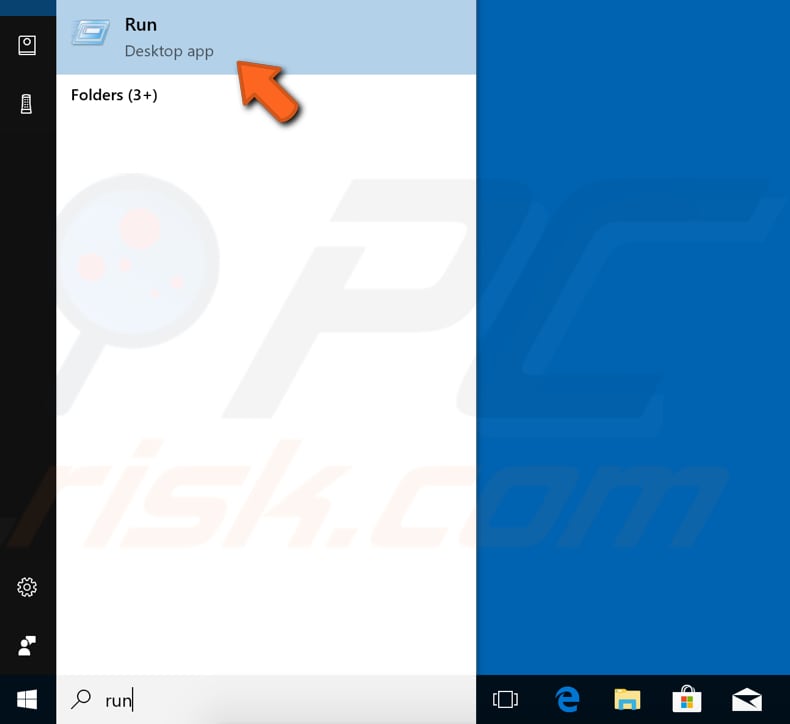
In the Run dialog box, type "msconfig" and click "OK". This will open the System Configuration tool. Another way to open the System Configuration tool is to type "system configuration" in Search and click the "System Configuration" result.
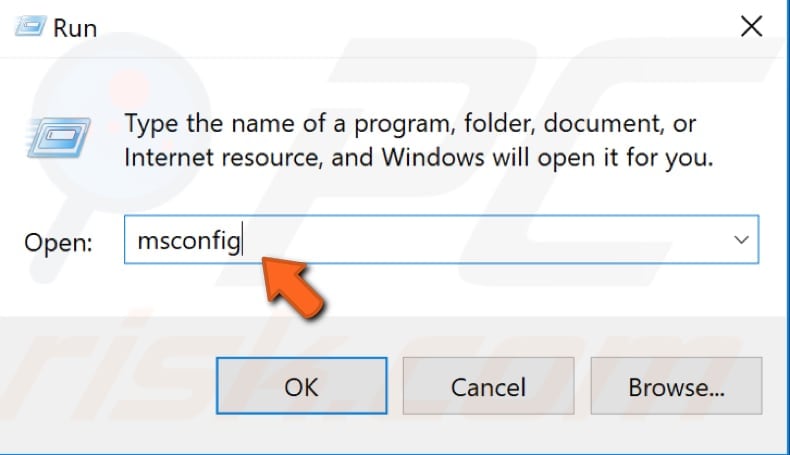
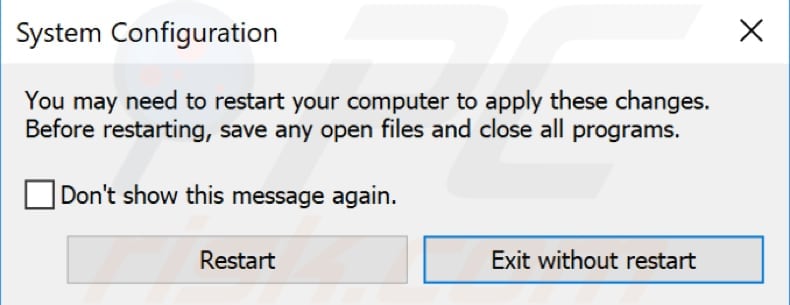
When the System Configuration window is open, click the "Boot" tab. Under Boot options, mark the "Safe boot" checkbox, select "Network" and click "OK". This will start Windows in Safe Mode with Networking.
Windows will inform you that you may need to restart your computer to apply these changes. Click "Restart" - Windows will restart the computer and start the operating system in Safe Mode.
This will allow you to remove malware without it continuing to harm your system. Proceed to the next step.
Scan Your System Using Third-Party Antivirus Software
Not all antivirus software is capable of detecting and removing the SmartScreen Trojan. Therefore, you must use advanced malware removal software. If you wish, choose a virus and malware scanner from our Top anti-malware list. The list comprises well-known top spyware removers and will help you choose the right software for your computer's protection. Go to the list by clicking this link.
The list includes antivirus software such as Malwarebytes, SpyHunter, etc. To use all available features, you will need to buy a license. There is, however, a free trial that allows you to scan your computer for infections.
If buying antivirus software is not an option, you might need to manually remove malware from your computer. This can be a long process, and for some users, quite tricky and possibly leading to even more damage. If you are still interested in methods that require manual work, read the solutions described below.
Uninstall Malicious Software Using Windows Application Wizard
Using the Windows Application Wizard, you can uninstall any software installed on your computer. In this case, we recommend that you use it when Windows has been started in Safe Mode. In any case, you must know which programs were installed by you and which might have been installed by SmartScreen Trojan malware.
To open the Windows Application Wizard, open the Run dialog box (by pressing Windows key + R or right-clicking the Start menu and selecting the Run result) and type "appwiz.cpl".
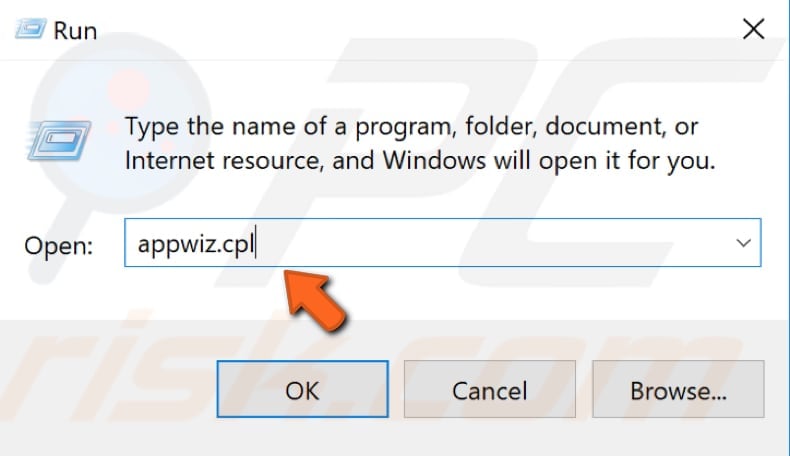
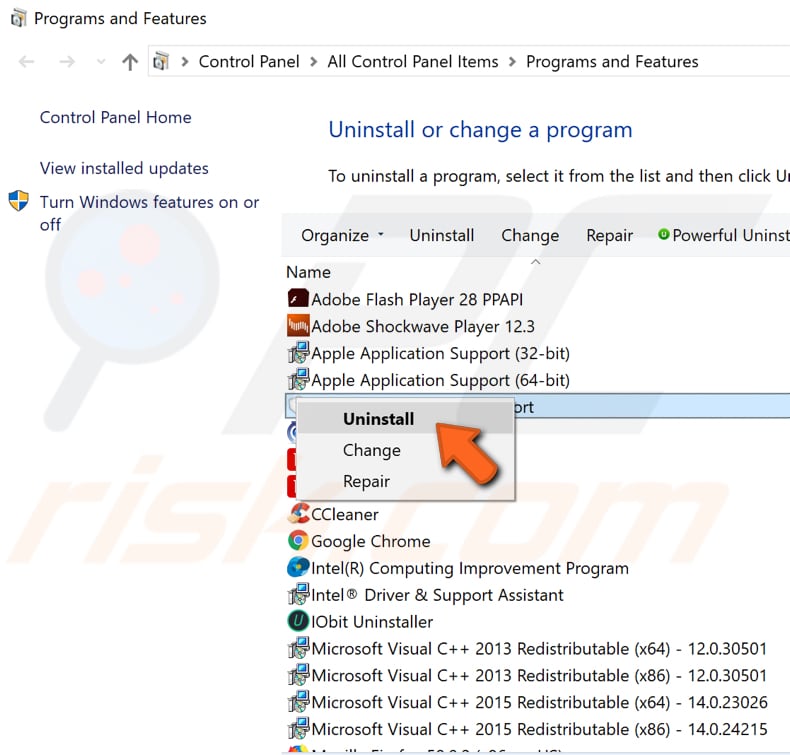
In the Programs and Features window, you will see a list of installed programs. Study the list and look for suspicious software that you do not recall installing.
Right-click the suspicious software and select "Uninstall" from the drop-down menu. Apply this step to all suspicious programs.
If you were unable to uninstall suspicious software, try using CCleaner. CCleaner, a small, effective utility for computers running Microsoft Windows. It cleans junk and issues that accumulate over time: temporary files, broken shortcuts, and other problems. It protects privacy, cleans browsing history and temporary Internet files, allowing you to be a more confident Internet user and less susceptible to identity theft.
CCleaner can clean redundant files from various programs, thus saving hard disk space, removing unneeded entries in Windows Registry, helping uninstall software, and selecting which programs start with Windows. You can download CCleaner from here.
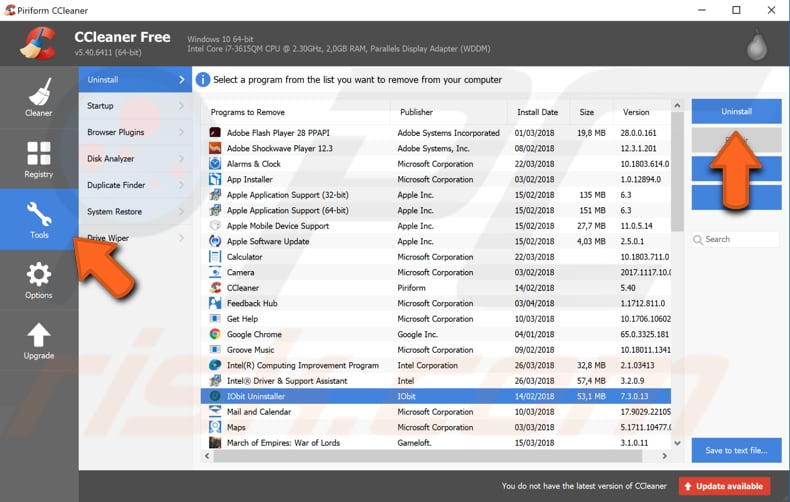
When downloaded, install CCleaner and open it. Find "Tools" on the left pane and click it. Now find and select the suspicious software from the list and click "Uninstall" on the right pane.
Stop Malicious Software From Running on Startup
Most malicious software starts when the Windows operating system starts (why it is hard to detect). This applies to the "The requested resource is in use" error Trojan.
To stop malicious software from running on Windows startup, start Windows in Safe Mode and use the System Configuration tool.
Type "msconfig" in the Run dialog box and click "OK". Once the System Configuration tool is open, select the "Startup" tab and click "Open Task Manager".
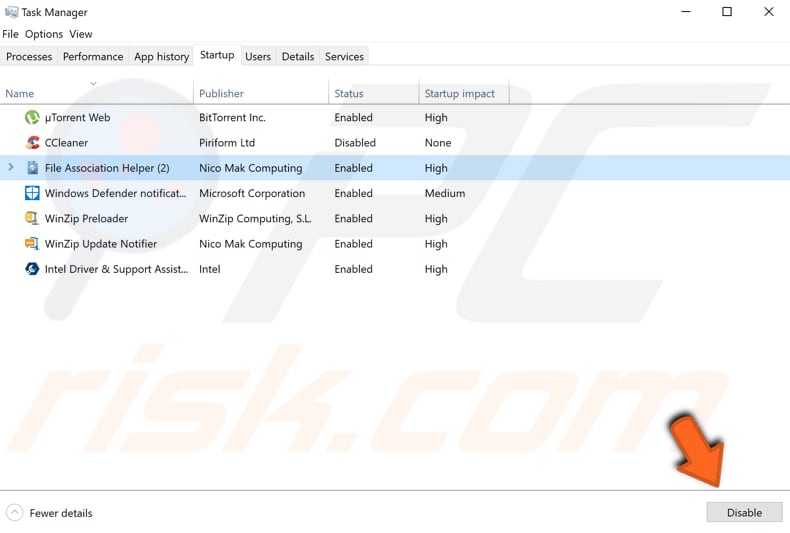
Under the Task Manager Startup tab, you will see a list of running programs once you start Windows. Look for suspicious programs - the malware publisher will probably be listed as 'Unknown'.
Look for unknown publishers (or suspicious) software, select them and click "Disable" in the bottom-right corner of the Task Manager window.
If you could not uninstall suspicious software using the Windows Application Wizard or CCleaner, remove it using Windows Registry Editor. First, we show how to check if malware is using any malicious IP addresses.
Check for Malicious IP Addresses
To check if there are any malicious IP addresses planted in your system files, open the Run dialog box and type this command (you can copy-and-paste it from this article): "notepad c:\windows\system32\drivers\etc\hosts", and then press Enter or click "OK".
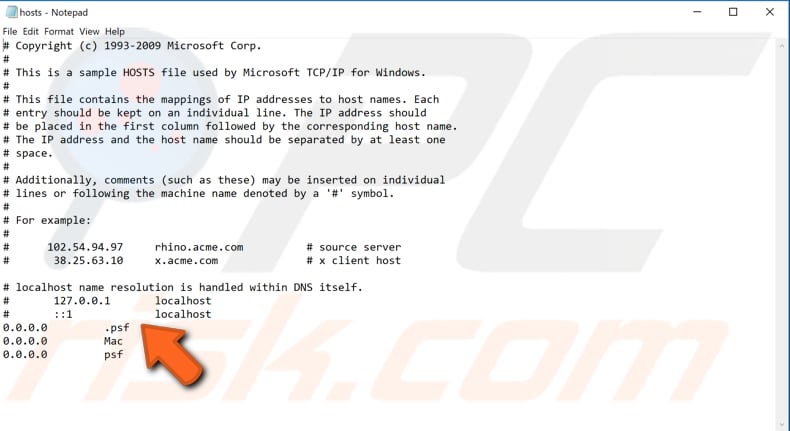
The two IP addresses at the bottom (as in our example) are the localhost's or your computer's addresses. If there are any other additional IP addresses under these two, you should contact a person who specializes in cyber security who will advise if your computer has been hacked and help you to remove the unwanted IP addresses.
Remove Malicious Entries Using Registry Editor
Windows Registry is a collection of databases of configuration settings in Microsoft Windows operating systems. It stores much of the information and settings for software programs, hardware devices, user preferences, operating system configurations, and much more.
Many of the options found in the registry are not accessible elsewhere in Windows. To edit your registry and remove malicious entries, you must use Windows Registry Editor.
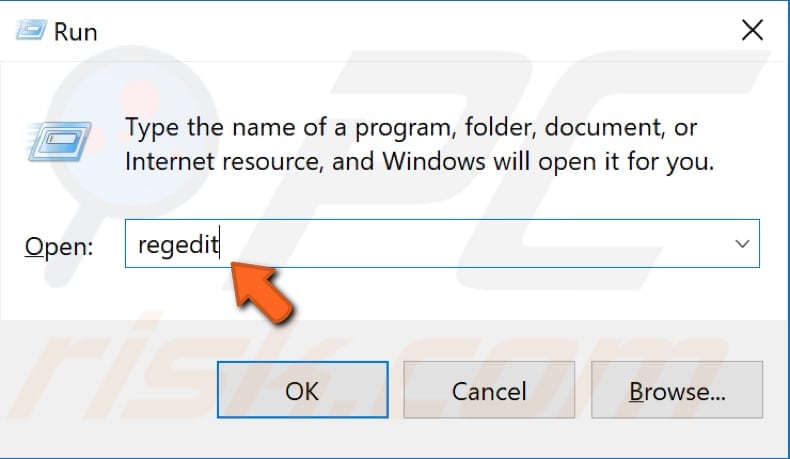
To open Registry Editor, open the Run dialog box (press Windows the Windows key + R or right-click Start and select "Run") and type "regedit". Press Enter or click "OK".
NOTE: Editing the registry can be risky - deleting the wrong entries can lead to serious problems such as computer malfunctions, etc.
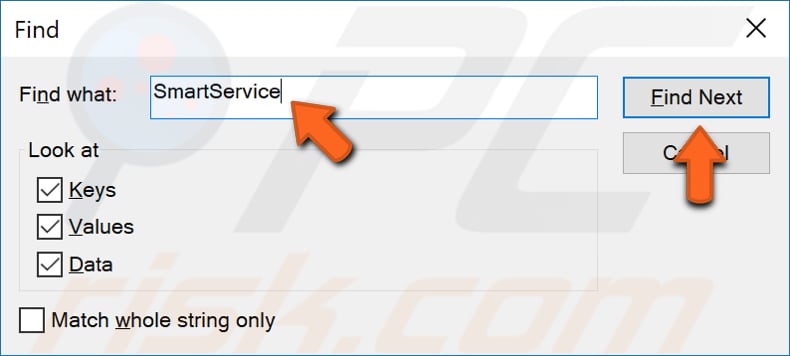
The easiest way to find malicious entries is to use Registry Editor's Find tool. Open it by clicking "Edit" and selecting "Find..." or by simply pressing the Ctrl (Control) + F keys on the keyboard.
Type "SmartService", click "Find Next" and see if it finds any suspicious registry entries related to it.
If it finds something suspicious and you are sure that is an entry planted by malware, right-click the entry and delete it. Note: you must be sure before deleting any registry entries.
If you know of other Trojan names, or you used third-party antivirus software to indicate malware infections, you can look for them using Registry Editor's Find tool.
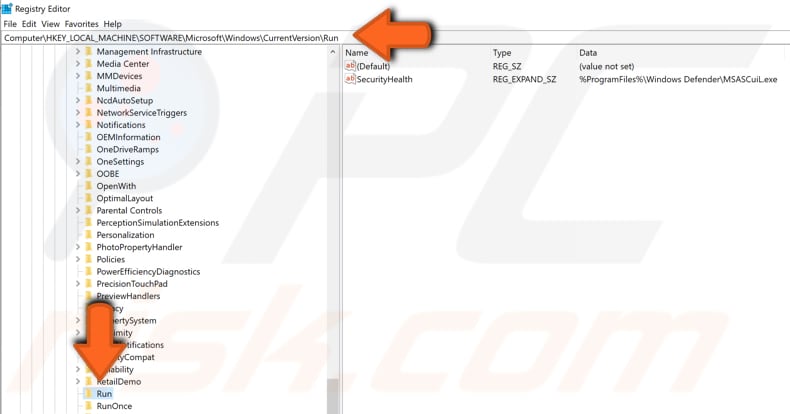
Another way to look for suspicious malware software entries is to follow this path, "HKEY_ LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion" and find "Run", "RunOnce" and other folders that have the word "Run" in the title.
Click each folder with "Run" in the title and see if it contains any suspicious entries. If you are not sure if it is malware, look up the names using Google and see if there is any information indicating malware.
We hope this guide was helpful and you were able to detect and remove malware causing the "The requested resource is in use" error.
If you know of other solutions to this problem that are not mentioned in our guide, please share them with us by leaving a comment in the section below.

▼ Show Discussion