Two Ransomware Gangs call it a Day
![]() Written by Karolis Liucveikis on
Written by Karolis Liucveikis on
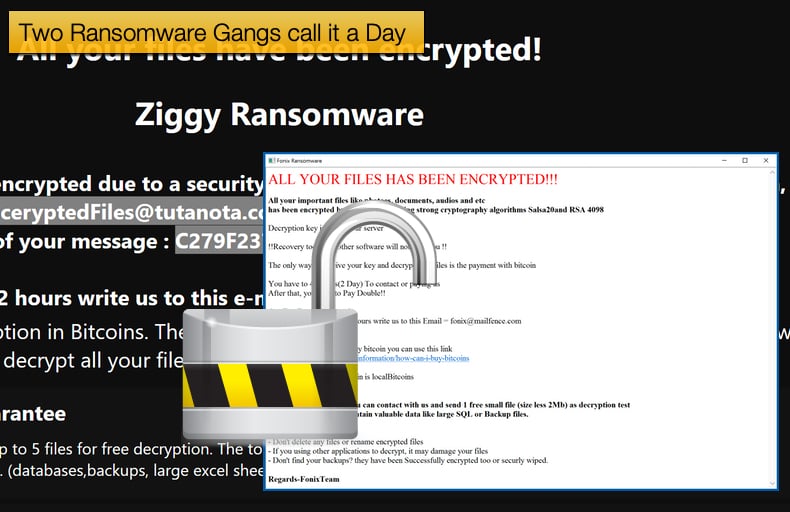
Recently, not one but two ransomware gangs have called it a day. For those who are victims of both the Ziggy and Fonix, ransomware strains will be pleased to know that both gangs have released decryption keys to help assist victims to recover their encrypted data. While the act may be viewed as a generous gesture to right wrongs committed in the past, not all may be as altruistic as it seems at first glance.
According to Bleeping Computer, security researcher M. Shahpasandi told the publication that the Ziggy Ransomware operators announced on Telegram that they were shutting down their operation and would be releasing all of the decryption keys. This was later confirmed by the publication when they reached out to the operators. Further, those behind the ransomware’s creation did so as they reside in a third-world country and needed to “generate money”. The reasons to stop operations boiled down to them feeling guilty about their actions and recent developments regarding law enforcement targeting cybercriminals. More on that to follow.
At the time of writing the operators had posted a SQL file containing 922 decryption keys for encrypted victims. For each victim, the SQL file lists three keys needed to decrypt their encrypted files along with a decryptor. The operators also shared with Bleeping Computer a decryptor for offline decryption keys. Ransomware will still look to encrypt data even if no online communication can be achieved between the victim’s machine and the attacker's command and control server.
To do this they enable the malware to decrypt offline using a specific set of encryption keys. Speaking to Bleeping Computer Emisoft’s Brett Callow noted,
“The release of the keys, whether voluntarily or involuntarily, is the best possible outcome. It means past victims can recover their data without needing to pay the ransom or use the dev’s decryptor, which could contain a backdoor and/or bugs. And, of course, it also means there’s one less ransomware group to worry about…The recent arrest of individuals associated with the Emotet and Netwalker operation could be causing some actors to get cold feet. If so, we could well see more groups ceasing operations and handing over their keys. Fingers crossed…”
Towards the end of January 2021, an individual claiming to be the admin behind the Fonix ransomware took to Twitter to announce that ransomware operations were shutting down. The post stated,
“I'm one fonix team admins.
you know about fonix team but we have come to the conclusion.
we should use our abilities in positive ways and help others.
Also rans0mware source is completely deleted, but some of team members are disagree with closure of the project, like telegram channel admin who trying to scam people in telegram channel by selling fake source and data.
Anyway now main admin has decided to put all previous work aside and decrypt all infected systems at no cost.
And the decryption key will be available to the public.
The final statement of the team will be announced soon.
Regards-FonixTeam”
Fonix, also called Xinof and FonixCrypter, began operating in June 2020 and has been steadily encrypting victims since. While not nearly as active as some other rival ransomware strains in November 2020 a significant rise in activity was detected by ID Ransomware. According to the announcement, the ransomware’s members, possibly a term used to describe affiliates, are not pleased with the admin shutting down operations, this may cause the affiliates to look for new fertile ransomware soil elsewhere. This has been seen in the past, notably when Maze ceased operations and Egregor activity saw a massive spike. This seems to have been confirmed by a recent analysis conducted by Chainalysis.
In a different Tweet the admin posted a link to a RAR archive named “Fonix_decrypter.rar” containing both a decryptor and the master private decryption key. While there is nothing wrong with the master key, the decryptor is woefully inadequate. According to Bleeping Computer, the decryptor is far from user friendly, meaning most victims will struggle to decrypt already encrypted files. It is more of an admin tool to be used by the ransomware’s operators and admin. Fortunately, Emisoft is currently working on a decryptor which should be available soon to victims.
Altruism only goes so far
Taking nothing away from the good intentions of those mentioned above and the guilt they may, or may not feel, recent developments involving law enforcement targeting cybercriminals may also be causing a fair amount of doubt amongst ransomware gangs. On January 27, 2021, Europol announced that in a collaborative effort between officials from the Netherlands, Germany, the United States, the United Kingdom, France, Lithuania, Canada, and Ukraine, with international activity coordinated by Europol and Eurojust the infrastructure of the Emotet botnet was severely crippled. Describing Emotet’s impact on the cyber threat landscape Europol stated,
“EMOTET has been one of the most professional and long lasting cybercrime services out there. First discovered as a banking Trojan in 2014, the malware evolved into the go-to solution for cybercriminals over the years. The EMOTET infrastructure essentially acted as a primary door opener for computer systems on a global scale. Once this unauthorised access was established, these were sold to other top-level criminal groups to deploy further illicit activities such data theft and extortion through ransomware.”
To cripple and take over the infrastructure used by Emotet a truly international effort was required as the infrastructure was spread across several hundreds of servers all over the globe. Added to this the servers all had specific purposes, whether to distribute the malware, infect new machines, or to serve the malware-as-a-service business model those behind Emotet had developed over the years. This ultimately made the entire networked infrastructure incredibly resilient to takedown attempts. Summarising how law enforcement managed to achieve this Europol stated,
“To severely disrupt the EMOTET infrastructure, law enforcement teamed up together to create an effective operational strategy. It resulted in this week’s action whereby law enforcement and judicial authorities gained control of the infrastructure and took it down from the inside. The infected machines of victims have been redirected towards this law enforcement-controlled infrastructure. This is a unique and new approach to effectively disrupt the activities of the facilitators of cybercrime.”
On the same day, US officials announced that a Netwalker affiliate had been charged and in a coordinated effort between US and Bulgarian officials the Netwalker website hosted on the Dark Web and used to leak data of victims for not paying the ransom was seized. Due to the prevalence of ransomware as a threat, it was predicted that governments would take steps to bolster law enforcement agencies' capabilities to combat the scourge. Events such as this seem to be that desire manifested. The affiliate of Netwalker charged by the US Department of Justice is a Canadian national.
Along with being charged, authorities seized nearly 500,000 USD in the form of Cryptocurrency believed to have been ransom payments. According to the unsealed indictment the charged individual was identified as Sebastien Vachon-Desjardins. Acting Assistant Attorney General Nicholas L. McQuaid of the Justice Department’s Criminal Division speaking about the case advised,
“We are striking back against the growing threat of ransomware by not only bringing criminal charges against the responsible actors, but also disrupting criminal online infrastructure and, wherever possible, recovering ransom payments extorted from victims…Ransomware victims should know that coming forward to law enforcement as soon as possible after an attack can lead to significant results like those achieved in today’s multi-faceted operation.”
It is hoped that more news that arises that details effective law enforcement operations slowly becomes the norm rather than articles and lists detailing new victims. Further, it is hoped that this signals a change in global policy towards how cybercrimes are dealt with by law enforcement and justice departments to make cybercriminals at least think twice about their actions.

▼ Show Discussion