MacOS Bundlore Virus (Mac)
![]() Written by Tomas Meskauskas on (updated)
Written by Tomas Meskauskas on (updated)
What is MacOS Bundlore?
MacOS Bundlore (also known as Crossrider) or is a family of deceptive software installers that allow criminals to proliferate ("bundle") adware-type applications (such as CinemaPlusPro, FlashMall, MyShopcoupon, etc.) together with regular apps. Adware-type apps typically offer 'useful features' and most may seem legitimate.
After infiltration, however, these programs deliver intrusive advertisements and gather sensitive information.
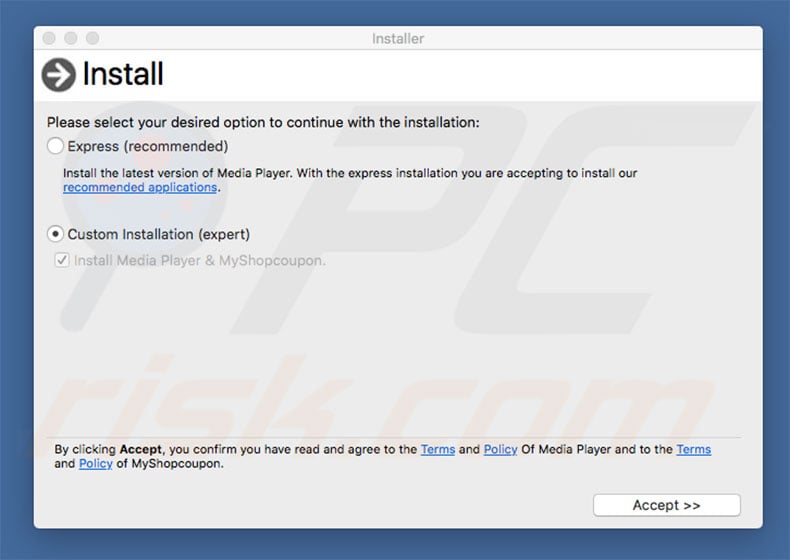
MacOS Bundlore overview
Adware-type apps deliver intrusive advertisements using tools that enable placement of third party graphical content on any site. Therefore, coupons, banners, pop-ups, and other ads that often conceal underlying content, thereby significantly diminishing the browsing experience.
Furthermore, they can lead to malicious websites and execute scripts that download and install malware. Even a single click can result in high-risk computer infections. As mentioned, adware-type apps also collect user-system information.
Internet Protocol (IP) addresses, queries entered into search engines, URLs of visited pages and other information that may include personal details. It is common that those details are shared with third parties (potentially, cyber criminals). Third parties misuse shared information to generate revenue.
Research shows that apps from Bundlore family target details such as a unique identifier for the computer, user name, macOS version, Safari and Chrome version, list of entries in the Applications folder, list of installed agents and daemons, list of installed system configuration profiles and/or version of the installed antivirus software or other security software that is designed to remove malware.
Also, apps from this family often get installed as browser extensions and collect data that is displayed on websites or is entered into forms on a websites. It is possible that those apps may be capable of accessing sensitive data, such as usernames, passwords, and credit card numbers.
Therefore, having data-tracking apps installed on your computer can lead to serious privacy issues or even identity theft. We strongly recommend that you uninstall all adware-type applications immediately.
| Name | MacOS Bundlore (Crossrider) adware |
| Threat Type | Mac malware, Mac virus |
| Detection Names | Avast (MacOS:Bundlore-CJ [Adw]), DrWeb (Adware.Mac.Bundlore.227), Kaspersky (Not-a-virus:HEUR:AdWare.OSX.Bnodlero.x), NANO-Antivirus (Riskware.Script.Adware.fvryso), Full List (VirusTotal) |
| Symptoms | Your Mac became slower than normal, you see unwanted pop-up ads, you get redirected to shady websites. |
| Distribution methods | Deceptive pop-up ads, free software installers (bundling), fake flash player installers, torrent file downloads. |
| Damage | Internet browsing tracking (potential privacy issues), displaying of unwanted ads, redirects to shady websites, loss of private information. |
| Malware Removal (Mac) | To eliminate possible malware infections, scan your Mac with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. |
There are hundreds of adware-type applications, all of which are very similar. As mentioned, these programs typically offer "useful features".
In doing so, potentially unwanted applications (PUAs) attempt to give the impression of legitimacy, however, their only purpose is to generate revenue for the developers. Rather than giving any real value for regular users, PUAs deliver intrusive advertisements and gather sensitive information, thereby posing a direct threat to your privacy and Internet browsing safety.
How did potentially unwanted programs install on my computer?
As mentioned, MacOS Bundlore's installers "bundle" adware. Therefore, due to the lack of knowledge and careless behavior of many users, potentially unwanted applications often infiltrate systems without consent. Developers do not disclose PUA installations properly. Therefore, adware-type apps are often concealed within various sections (e.g., "Custom/Advanced" settings) of the download or installation processes. Furthermore, many users are likely to rush these procedures and skip steps, thereby exposing systems to risk of various infections and putting users' privacy at risk.
How to avoid installation of potentially unwanted applications?
The key to computer safety is caution. Therefore, to prevent system infiltration by potentially unwanted applications, be very cautious when downloading/installing software and browsing the Internet. Select "Custom/Advanced" settings and carefully analyze each window of the download/installation dialogs.
Opt-out of all additionally-included programs and decline offers to download/install them. We advise you to download software from official sources only, using direct download links. Unofficial downloaders/installers should never be used, since developers monetize them by promoting ("bundling") PUAs.
As well as using the "bundling" method, adware developers often proliferate these programs using intrusive advertisements. Developers invest many resources into intrusive ad design, thereby making them seem legitimate, however, the ads often lead to dubious websites (gambling, adult dating, pornography, and so on).
If you encounter these ads, immediately eliminate all dubious applications and browser plug-ins. If your computer is already infected with PUPs, we recommend running a scan with Combo Cleaner Antivirus for macOS to automatically eliminate them.
Most commonly adware from "Bundlore" family install via fake Adobe Flash Player updaters:

List of .plist files modified by MacOS Bundlore virus:
- ~/Library/Containers/com.apple.Safari/Data/Library/Preferences/com.apple.Safari.Extensions.plist
- ~/Library/Containers/com.apple.Safari/Data/Library/Preferences/com.apple.Safari.plist
- ~/Library/Preferences/com.apple.Safari.SandboxBroker.plist
- ~/Library/Preferences/com.google.Chrome.plist
- ~/Library/Safari/Bookmarks.plist
- ~/Library/Safari/Extensions/Extensions.plist
List of domains related to MacOS Bundlore virus:
- auctioneer.50million[.]club
- cdn.macmymacupdater[.]com
- cdn.mycouponsmartmac[.]com
- cdn.myshopcouponmac[.]com
- events.blitzbarbara[.]win
- events.macinstallerinfo[.]com
- events.mycouponsmartmac[.]com
- events.ponystudent[.]com
- otcct.beforeoctavia[.]site
- secure.mycouponsmartmac[.]com
- service.ezsoftwareupdater[.]com
- service.macinstallerinfo[.]com
- software.macsoftwareserver05[.]com
List of adware-type applications relating to MacOS Bundlore virus:
| BestSmart Shoppers | BestWebShoppers |
| CoolShopper | Couponizer |
| Easy-Shopper | EasyShopper |
| FlashMall | HotShoppy |
| LiveShoppers | MyCouponize |
| MyShopBot | MyShopcoupon |
| MyShopMate | ShopTool |
| Shopperify | Shoppinizer |
| Smart-Shoppy | SmartShoppy |
| SurfBuyer | SurfMate |
| WebShoppers | WebShoppy |
Update September 13, 2019 - Cyber criminals have updated MacOS Bundlore a number of times since it first release and, thus, its behavior has changed.
First of all, MacOS Bundlore uses a different technique to manipulate web browsers' search settings. In the past, MacOS Bundlore was using malicious browser extensions. Since MacOS 10.13 release, however, MacOS Bundlore achieves this by creating new device profiles, because the previous method is no longer working due to newly-added MacOS security features.
Now it is worth mentioning that MacOS Bundlore performs a chain of actions to inject rogue applications into the system. Initially, a bash script ("Install.sh") connects to a remote server and downloads an archive containing an app named "mm-install-macOS".
Once executed, this app connects to a remote server and downloads/executes scripts necessary to install unwanted applications. Now it is worth mentioning that password of the user is necessary for MacOS Bundlore to communicate with the system.
In order to extract the password, MacOS Bundlore prompts a pop-up window pretending to be MacOS and asks user to enter the password. Once entered, the password is saved and used for further actions. MacOS Bundlore consists of three main components:
1) MyMacUpdater (responsible for communication with Command & Control (C&C) server in order to keep the infection up-to-date); 2) WebTools (responsible for bypassing MacOS security, changes of browsers' behavior, persistence achievement, and installation of ad-delivering tools), and; 3) ad-delivering tool which injects JavaScript into browsers by using AppleScript.
Update June 29, 2020 - MacOS Bundlore has been updated in order to target the newest version of the Safari browser. Since Safari 13 is longer compatible with the old Safari Extension format (.safariextz), developers of both legitimate and questionable software have been pushed to update their products in accordance. These changes in formatting have not escaped the notice of MacOS Bundlore developers. Several new installers have been released containing payloads compatible with the new Safari App Extension format (.appex).
IMPORTANT NOTE! As mentioned above, MacOS Bundlore uses device profiles to alter web browsers' behavior. Therefore, before taking any further removal steps, perform these actions:
1) Click the "Preferences" icon in the menu bar and select "Profiles"

2) Select the "AdminPrefs" profile and delete it.
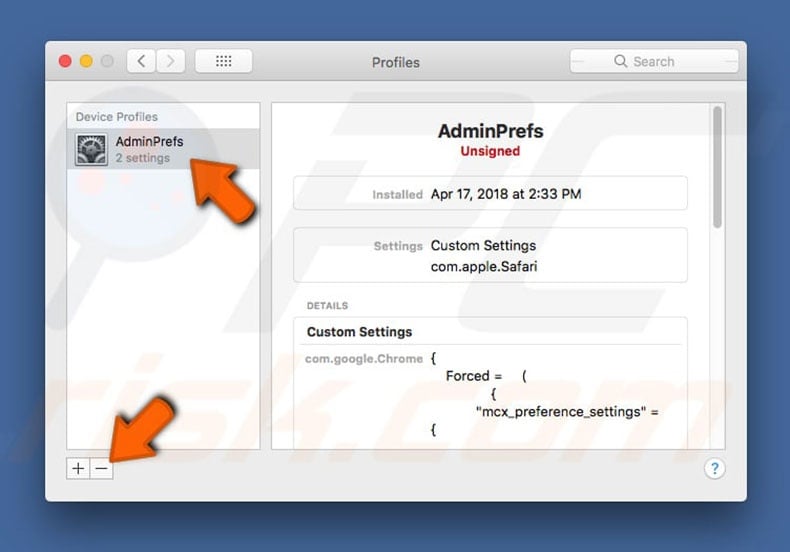
3) Perform a full system scan with Combo Cleaner anti-virus suite.
After performing these actions, you can proceed with further removal steps for this browser hijacker.
Instant automatic Mac malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of Mac malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner for Mac
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. Limited seven days free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Quick menu:
- What is MacOS Bundlore?
- STEP 1. Remove PUP related files and folders from OSX.
- STEP 2. Remove rogue extensions from Safari.
- STEP 3. Remove rogue add-ons from Google Chrome.
- STEP 4. Remove potentially unwanted plug-ins from Mozilla Firefox.
Video showing how to remove adware and browser hijackers from a Mac computer:
Potentially unwanted programs removal:
Remove PUP-related potentially unwanted applications from your "Applications" folder:
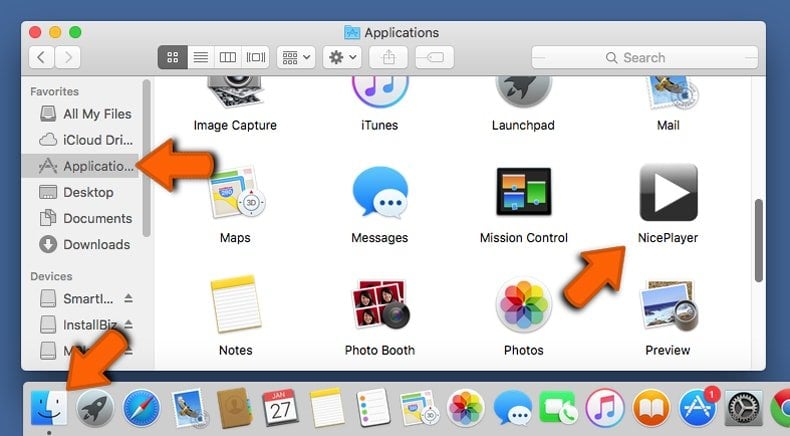
Click the Finder icon. In the Finder window, select “Applications”. In the applications folder, look for “MPlayerX”,“NicePlayer”, or other suspicious applications and drag them to the Trash. After removing the potentially unwanted application(s) that cause online ads, scan your Mac for any remaining unwanted components.
Remove adware-related files and folders
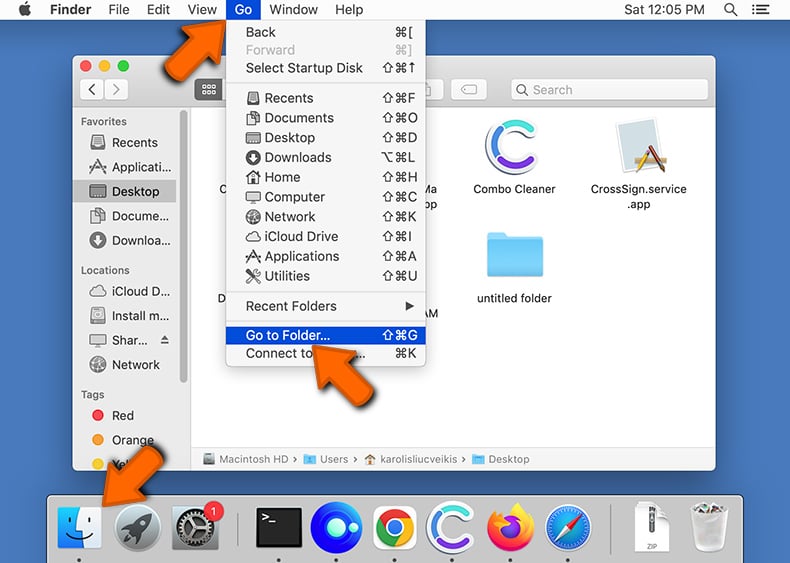
Click the Finder icon, from the menu bar. Choose Go, and click Go to Folder...
 Check for adware generated files in the /Library/LaunchAgents/ folder:
Check for adware generated files in the /Library/LaunchAgents/ folder:
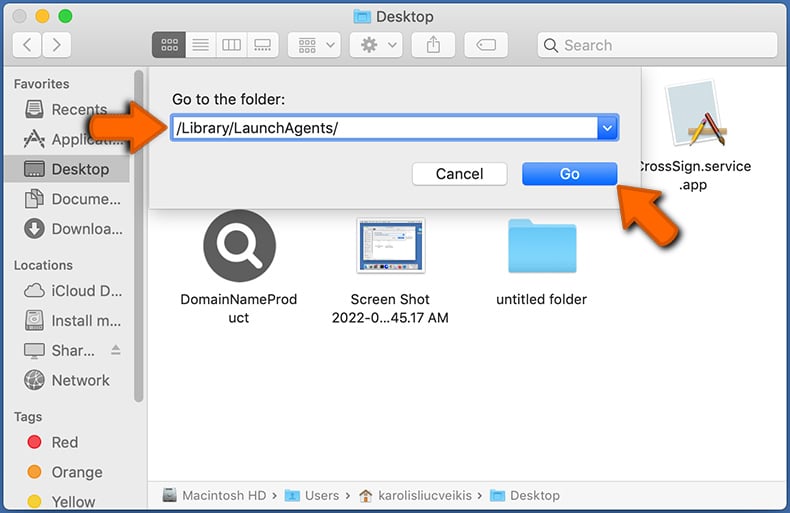
In the Go to Folder... bar, type: /Library/LaunchAgents/
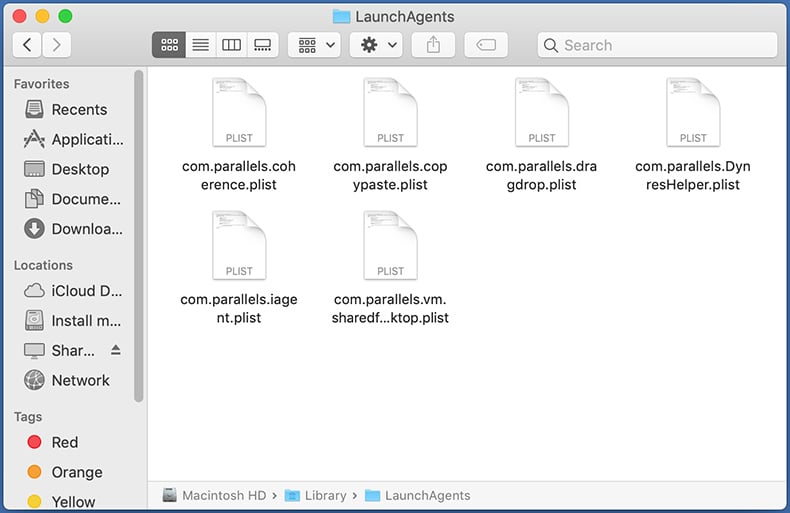
In the "LaunchAgents" folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - "installmac.AppRemoval.plist", "myppes.download.plist", "mykotlerino.ltvbit.plist", "kuklorest.update.plist", etc. Adware commonly installs several files with the exact same string.
 Check for adware generated files in the ~/Library/Application Support/ folder:
Check for adware generated files in the ~/Library/Application Support/ folder:
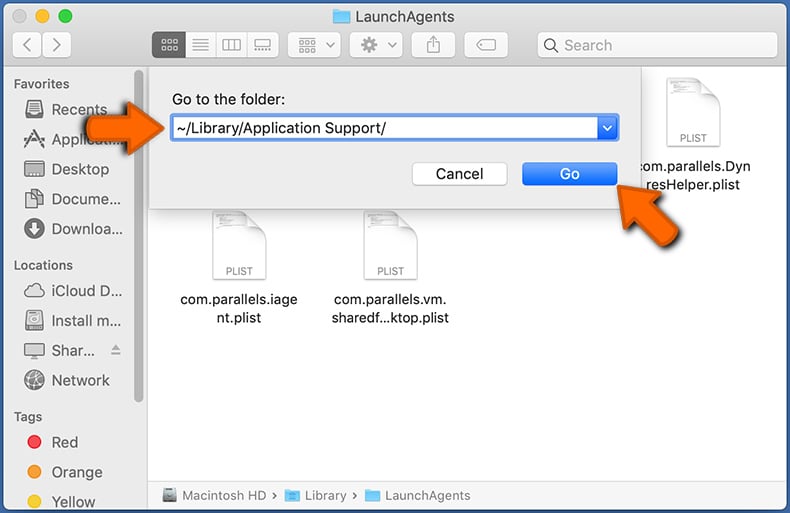
In the Go to Folder... bar, type: ~/Library/Application Support/
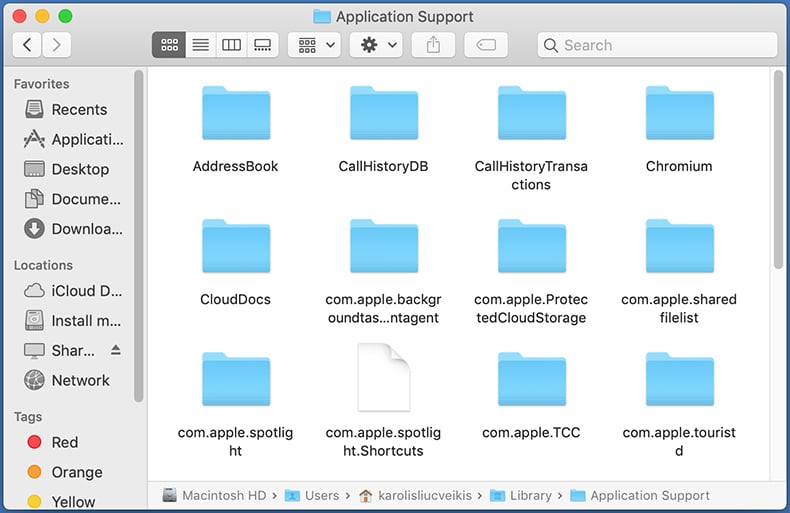
In the "Application Support" folder, look for any recently-added suspicious folders. For example, "MplayerX" or "NicePlayer", and move these folders to the Trash.
 Check for adware generated files in the ~/Library/LaunchAgents/ folder:
Check for adware generated files in the ~/Library/LaunchAgents/ folder:
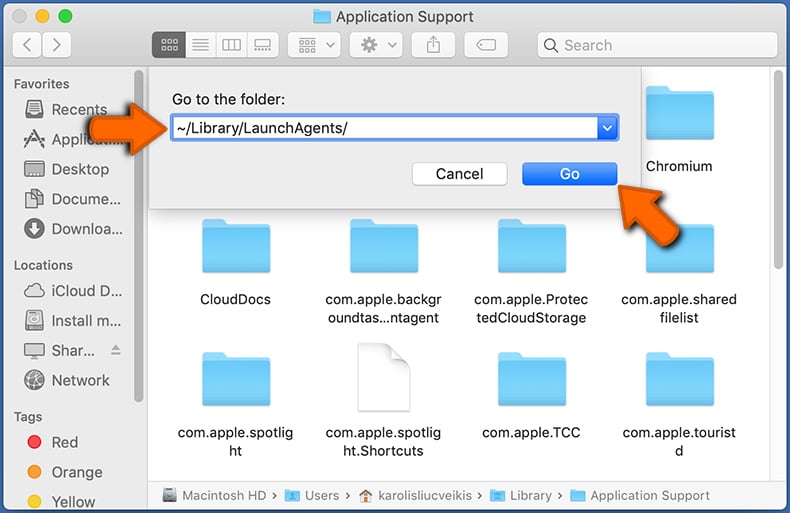
In the Go to Folder... bar, type: ~/Library/LaunchAgents/
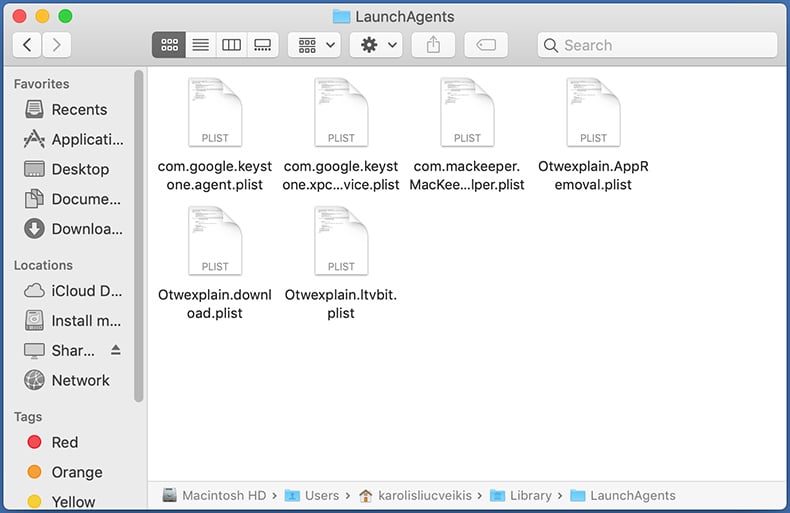
In the "LaunchAgents" folder, look for any recently-added suspicious files and move them to the Trash. Examples of files generated by adware - "installmac.AppRemoval.plist", "myppes.download.plist", "mykotlerino.ltvbit.plist", "kuklorest.update.plist", etc. Adware commonly installs several files with the exact same string.
 Check for adware generated files in the /Library/LaunchDaemons/ folder:
Check for adware generated files in the /Library/LaunchDaemons/ folder:
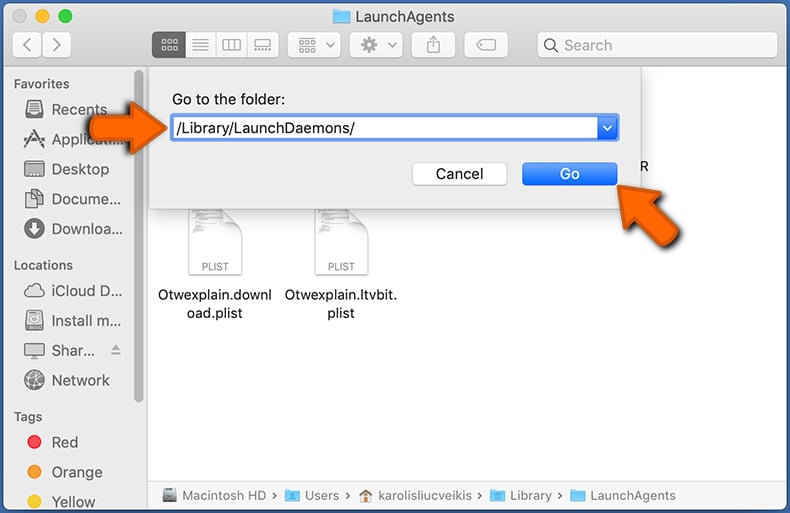
In the "Go to Folder..." bar, type: /Library/LaunchDaemons/
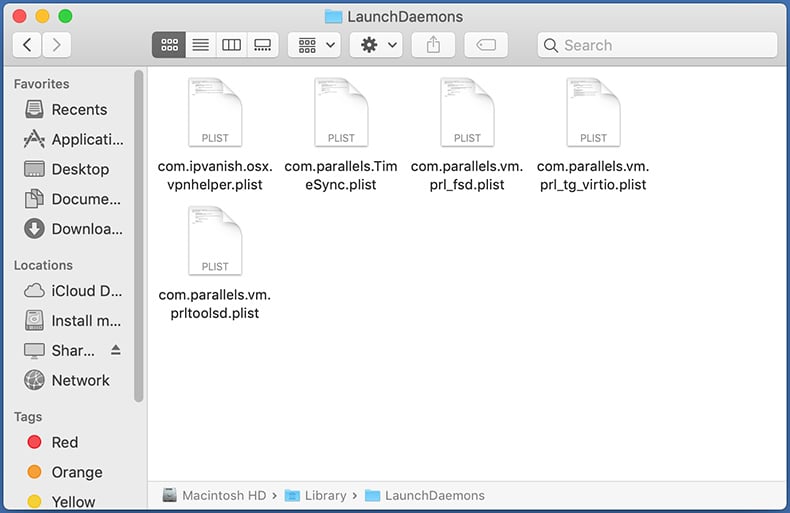
In the "LaunchDaemons" folder, look for recently-added suspicious files. For example "com.aoudad.net-preferences.plist", "com.myppes.net-preferences.plist", "com.kuklorest.net-preferences.plist", "com.avickUpd.plist", etc., and move them to the Trash.
 Scan your Mac with Combo Cleaner:
Scan your Mac with Combo Cleaner:
If you have followed all the steps correctly, your Mac should be clean of infections. To ensure your system is not infected, run a scan with Combo Cleaner Antivirus. Download it HERE. After downloading the file, double click combocleaner.dmg installer. In the opened window, drag and drop the Combo Cleaner icon on top of the Applications icon. Now open your launchpad and click on the Combo Cleaner icon. Wait until Combo Cleaner updates its virus definition database and click the "Start Combo Scan" button.
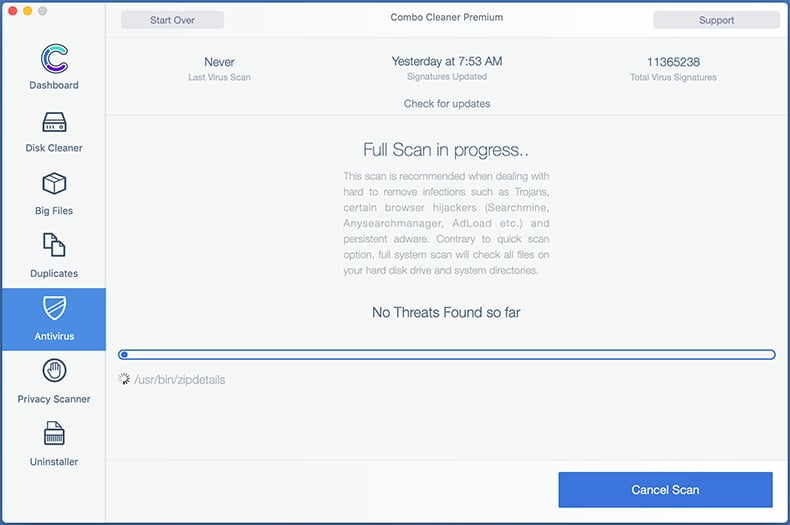
Combo Cleaner will scan your Mac for malware infections. If the antivirus scan displays "no threats found" - this means that you can continue with the removal guide; otherwise, it's recommended to remove any found infections before continuing.
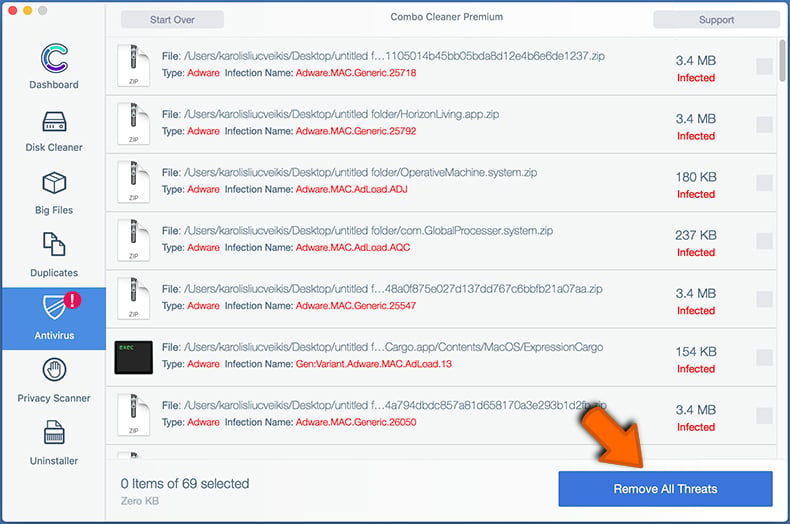
After removing files and folders generated by the adware, continue to remove rogue extensions from your Internet browsers.
Remove malicious extensions from Internet browsers
 Remove malicious Safari extensions:
Remove malicious Safari extensions:
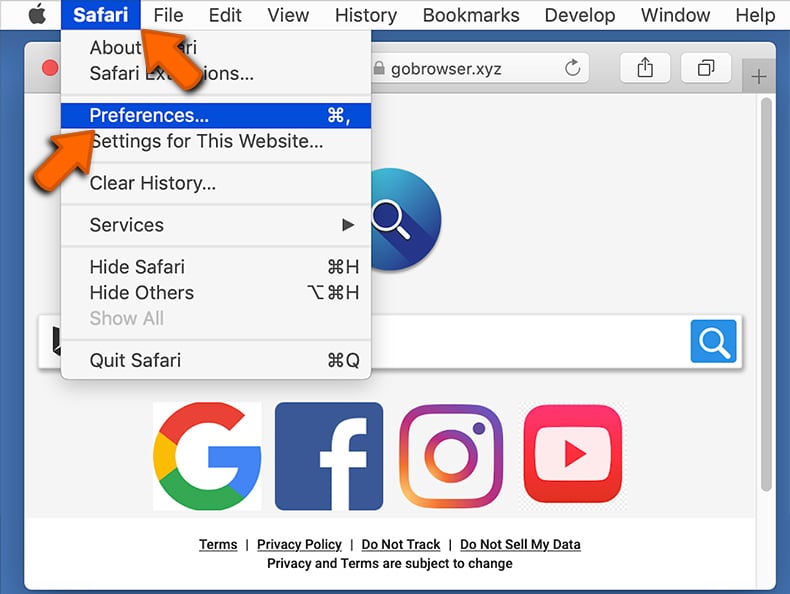
Open the Safari browser, from the menu bar, select "Safari" and click "Preferences...".
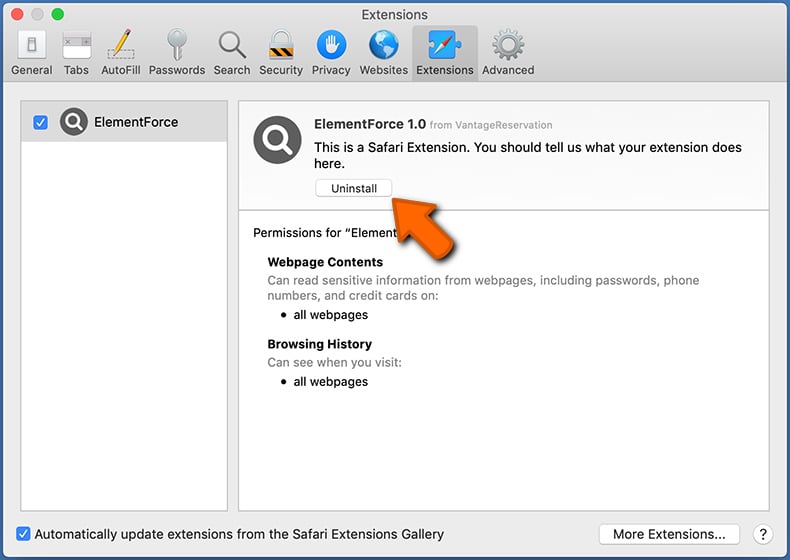
In the preferences window, select "Extensions" and look for any recently-installed suspicious extensions. When located, click the "Uninstall" button next to it/them. Note that you can safely uninstall all extensions from your Safari browser - none are crucial for regular browser operation.
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Safari.
 Remove malicious extensions from Google Chrome:
Remove malicious extensions from Google Chrome:
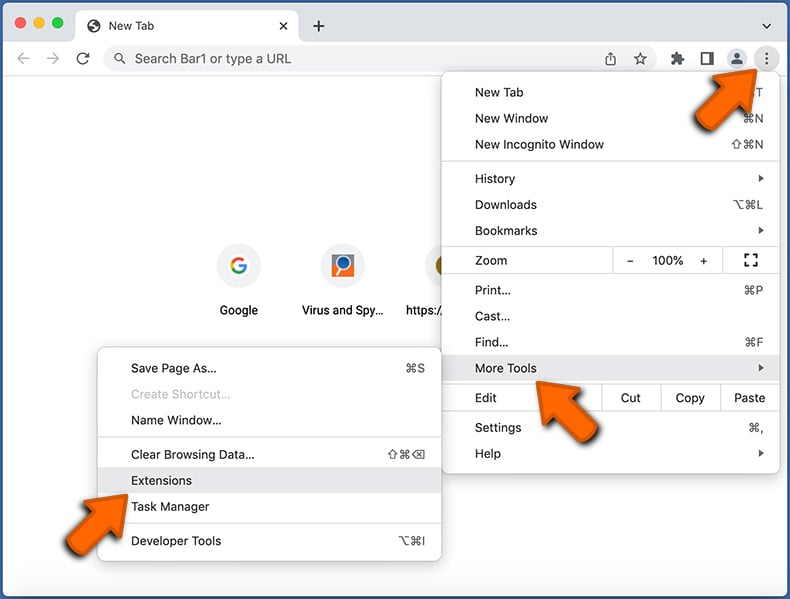
Click the Chrome menu icon ![]() (at the top right corner of Google Chrome), select "More Tools" and click "Extensions". Locate all recently-installed suspicious extensions, select these entries and click "Remove".
(at the top right corner of Google Chrome), select "More Tools" and click "Extensions". Locate all recently-installed suspicious extensions, select these entries and click "Remove".
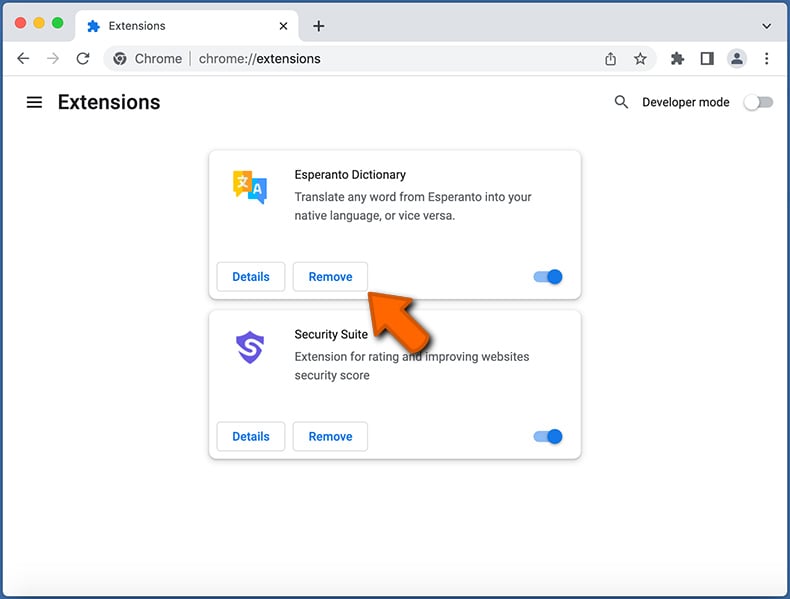
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Google Chrome.
 Remove malicious extensions from Mozilla Firefox:
Remove malicious extensions from Mozilla Firefox:
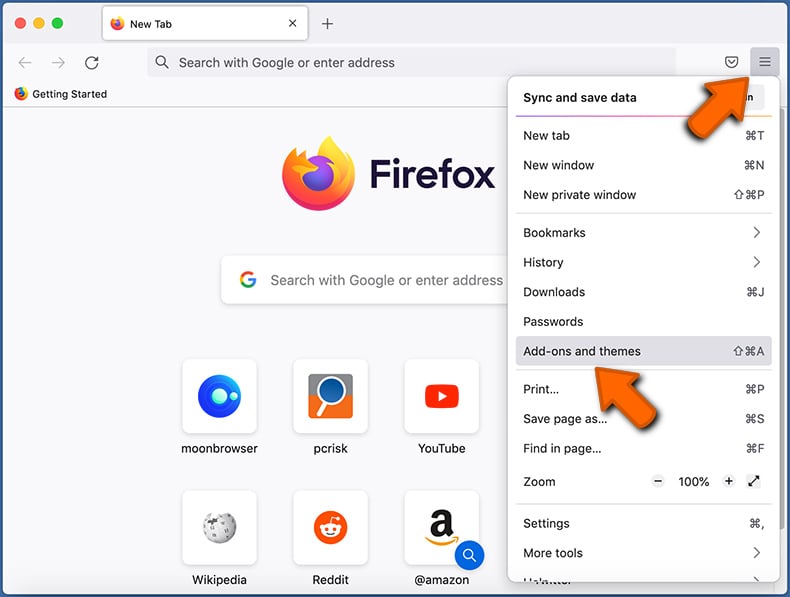
Click the Firefox menu ![]() (at the top right corner of the main window) and select "Add-ons and themes". Click "Extensions", in the opened window locate all recently-installed suspicious extensions, click on the three dots and then click "Remove".
(at the top right corner of the main window) and select "Add-ons and themes". Click "Extensions", in the opened window locate all recently-installed suspicious extensions, click on the three dots and then click "Remove".
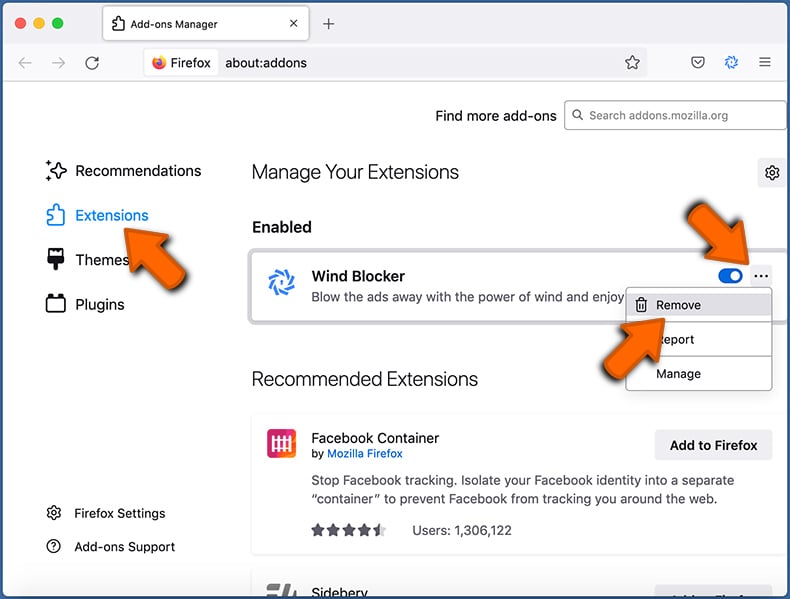
- If you continue to have problems with browser redirects and unwanted advertisements - Reset Mozilla Firefox.
Frequently Asked Questions (FAQ)
What harm can adware cause?
Adware can decrease browsing quality and system performance. Significant threats are posed by content endorsed through adware-delivered ads (e.g., system infections, privacy issues, financial losses, etc.). Additionally, advertising-supported software usually has data-tracking abilities – hence, it is considered a privacy threat.
What does adware do?
Adware is designed to run intrusive ad campaigns. The software's primary functions include displaying adverts on various interfaces, generating redirects, and collecting private data.
How do adware developers generate revenue?
Adware developers profit mainly via affiliate programs by endorsing various websites, apps, extensions, products, services, etc.
Will Combo Cleaner remove adware?
Yes, Combo Cleaner will scan your device and eliminate all adware-type applications that are installed. Keep in mind that manual removal (performed without security tools) might not be ideal. In some cases, after the advertising-supported software has been manually removed – various leftovers (files) stay hidden within the system. The remaining components can continue to run and cause issues. Therefore, it is paramount to eliminate adware and other unwanted software thoroughly.


▼ Show Discussion