Virus and Spyware Removal Guides, uninstall instructions
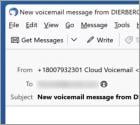
What kind of email is "Cloud Voicemail"?
After analyzing the "Cloud Voicemail" email, we determined that it is spam. The fake letter notifies the recipient of a voicemail that they have been sent. The voice message is supposedly in the attached file. The attachment is a phishing file that imitates the recipient's email sign-in page. Hence, by trusting this mail – recipients can have their mail accounts stolen.
What kind of malware is Deep (Phobos)?
While inspecting new submissions to the VirusTotal website, our researchers discovered the Deep ransomware-type program. It is part of the Phobos ransomware family. Deep (Phobos) operates by encrypting data to demand payment for its decryption.
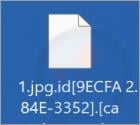
On our test machine, this ransomware encrypted files and renamed them. Original filenames were appended with a unique ID assigned to the victim, the cyber criminals' email address, and a ".deep" extension. For example, a file initially titled "1.jpg" appeared as "1.jpg.id[9ECFA84E-3352].[captain-america@tuta.io].deep".
After the encryption process was finished, ransom notes were created/displayed in a pop-up window ("info.hta") and text file ("info.txt").
What kind of application is Rocket App?
Following an evaluation of the Rocket App application, it has been determined that its primary purpose is to function as a browser hijacker with the objective of promoting r.bsc.sien.com, a fraudulent search engine. This extension alters the settings of a web browser with the intention of gaining control over it.
What kind of application is CanisLupusLupus?
During an examination of an unreliable installer downloaded from an unreliable website, we encountered the CanisLupusLupus browser extension. The investigation unveiled concerning characteristics associated with this extension, including its ability to activate the "Managed by your organization" feature in the Chrome browser, gather user data, and manipulate browser components.
What kind of malware is LuaDream?
In the dynamic field of cybersecurity, an interesting new development has surfaced. Sandman, a known advanced threat actor, has introduced an unusual and complex modular backdoor. What sets this apart is its use of the LuaJIT platform, which is not commonly seen in cyber threats. This innovative malware, named LuaDream, marks a noteworthy advancement in cybersecurity.

What kind of malware is Azop?
During our analysis of malware samples on the VirusTotal page, we came across the Azop ransomware, a member of the Djvu family. Upon infiltrating a computer, this ransomware encrypts data and appends the ".azop" extension to file names. For instance, it changes "1.jpg" to "1.jpg.azop" and "2.png" to "2.png.azop".
Azop ransomware also generates a ransom note in the form of a text document named "_readme.txt" Additionally, the distribution of Azop may involve other malware employed for information stealing, such as Vidar or RedLine.

What kind of malware is Azqt?
In the course of our examination of malware samples on the VirusTotal page, we encountered the Azqt ransomware, which belongs to the Djvu malware family. Upon infiltrating a computer, this ransomware encrypts files and adds the ".azqt" extension to their filenames. For example, it changes "1.jpg" to "1.jpg.azqt", "2.png" to "2.png.azqt", etc.
Azqt also generates a ransom note, which is a text document named "_readme.txt". Furthermore, the distribution of Azqt might encompass other forms of malware (information stealers), such as Vidar or RedLine.

What kind of malware is Azhi?
During our analysis of malware samples on the VirusTotal website, we came across the Azhi ransomware, a member of the Djvu malware family. Once it infiltrates a computer, this ransomware encrypts files and appends the ".azhi" extension to their names. For instance, it renames "1.jpg" to "1.jpg.azhi" and "2.png" to "2.png.azhi".
Azhi also produces a ransom note, which is a text document named "_readme.txt". Additionally, the distribution of Azhi may involve other types of malware specifically designed for data theft, such as Vidar or RedLine.
What kind of software is The Beach Tab?
The Beach Tab is a rogue extension that promises to display beach/seaside-themed browser wallpapers. Our examination revealed that this piece of software is a browser hijacker. It makes modifications to browser settings in order to promote (through redirects) the find.allsearchllc.com fake search engine. The Beach Tab also spies on users' browsing activity.
What kind of application is PracticeCycle?
Our research team discovered the PracticeCycle adware-type app while inspecting new file submissions to the VirusTotal platform. This advertising-supported software is part of the AdLoad malware family. PracticeCycle is designed to run intrusive advertisement campaigns.
More Articles...
Page 193 of 2139
<< Start < Prev 191 192 193 194 195 196 197 198 199 200 Next > End >>