How to identify scams like "You Are Now On The Radar Of An International Group Of Hackers"
![]() Written by Tomas Meskauskas on (updated)
Written by Tomas Meskauskas on (updated)
What is "You Are Now On The Radar Of An International Group Of Hackers"?
During our examination of the email, we found it to be a deceptive message impersonating a threat from a hacker. The scammer responsible for this email intends to trick recipients into thinking that compromising videos will be distributed to others unless they meet the specified demands. These types of emails are commonly referred to as sextortion scams.
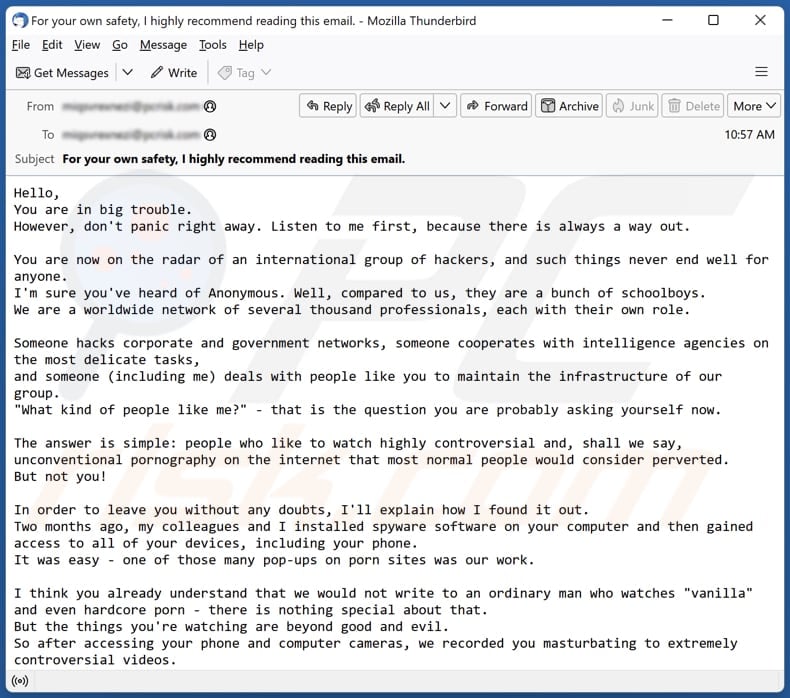
More about the "You Are Now On The Radar Of An International Group Of Hackers" scam email
The scammer begins the email by asserting that the recipient is in significant trouble but urges them not to panic immediately, stating that there is a potential way out. The email then claims that the recipient is under surveillance by an international group of hackers who surpass the notorious Anonymous group in terms of expertise and scale.
Also, the scammer alleges that the recipient has been caught watching highly controversial and unconventional adult videos, which the scammer finds reprehensible. Fraudster claims to have installed spyware on the recipient's devices two months prior and gained access to all their devices, including their phone, through a pop-up on an adult website.
The scammer then threatens to distribute compromising videos of the recipient to everyone in their contact list if they fail to transfer $1490 in Bitcoin to a specified cryptocurrency wallet within 48 hours.
Also, the recipient is warned against replying to the email, contacting law enforcement, or attempting to reset their devices, claiming that the scammer has access to all of their devices and can track their movements.
The purpose of this scam is to extort money from the recipient by leveraging fear and embarrassment. Recipients should not comply with the demands outlined in the scam email because the claims made by the sender are not true. The threat of having compromising videos and access to personal devices is fabricated to instill fear and coerce the recipient into making a payment.
| Name | You Are Now On The Radar Of An International Group Of Hackers Email Scam |
| Threat Type | Phishing, Scam, Social Engineering, Fraud |
| Fake Claim | The recipient is under surveillance by an international group of hackers |
| Cyber Criminal Cryptowallet Address | 13RuNi9xhDN5ngYy251h4WFDYoE3VA4kPJ, 19VQ4UwfrMskCbRLPrzsaL6TUCYomNdvKt, 17XansAD9geWqX31sP7a8A3DmoVseVikyt |
| Disguise | Letter from hackers |
| Symptoms | Unauthorized online purchases, changed online account passwords, identity theft, illegal access of the computer. |
| Distribution methods | Deceptive emails, rogue online pop-up ads, search engine poisoning techniques, misspelled domains. |
| Damage | Loss of sensitive private information, monetary loss, identity theft. |
| Malware Removal (Windows) | To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. |
Similar scam emails in general
Such emails, known as sextortion scams, rely on fear and deception to extort money from recipients. They typically claim to have compromising videos or information about the recipient and threaten to distribute it unless a payment is made. However, these claims are often baseless, and the scammers have no actual evidence.
Recipients should not engage with the scammer, refrain from making any payments, and report the scam to authorities. It is important to mention that emails of this kind can be used to trick recipients into activating malware on their computers.
Examples of similar scams are "Operating System Was Compromised Under My Direction", "Hello My Perverted Friend", "This Email Concerns Your Information Security".
How do spam campaigns infect computers?
Inadvertently, recipients can compromise their computers via email by interacting with malicious attachments or clicking links that redirect to malware-infested websites. For instance, an email attachment might pose as a harmless document like a Word or PDF file but actually harbors malware in the form of an executable file.
Also, fraudulent emails can lure recipients into clicking seemingly genuine links, which, in reality, lead to deceptive websites engineered to disseminate malware such as ransomware or keyloggers.
How to avoid installation of malware?
Refrain from opening attachments or clicking on links in emails from unfamiliar or dubious sources, particularly if they appear unexpected or unusual. Install reliable security software and keep it up to date to identify and eliminate threats effectively. Also, regularly update operating systems, web browsers, and other software.
Exercise caution when interacting with ads and pop-ups, especially those on shady pages that seem suspicious or offer unrealistic promises. Do not download pirated software or cracking tools. Obtain apps and files from official websites (or app stores).
If you have already opened malicious attachments, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate infiltrated malware.
Text presented in the "You Are Now On The Radar Of An International Group Of Hackers" email letter:
Subject: For your own safety, I highly recommend reading this email.
Hello,
You are in big trouble.
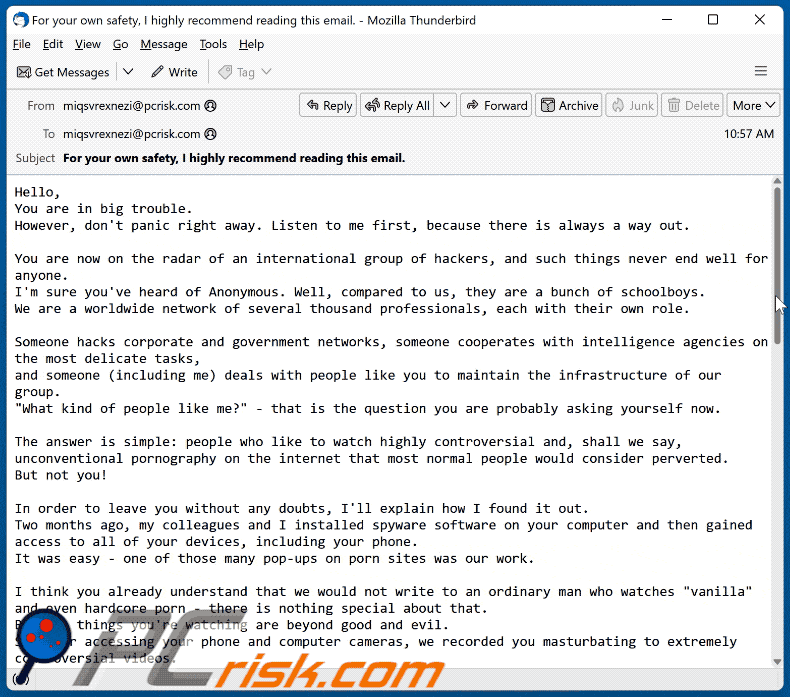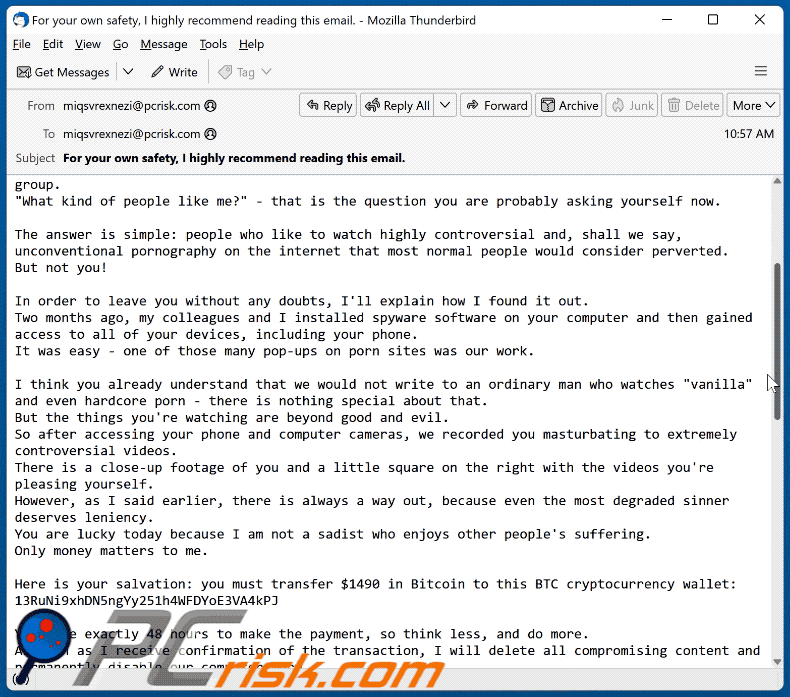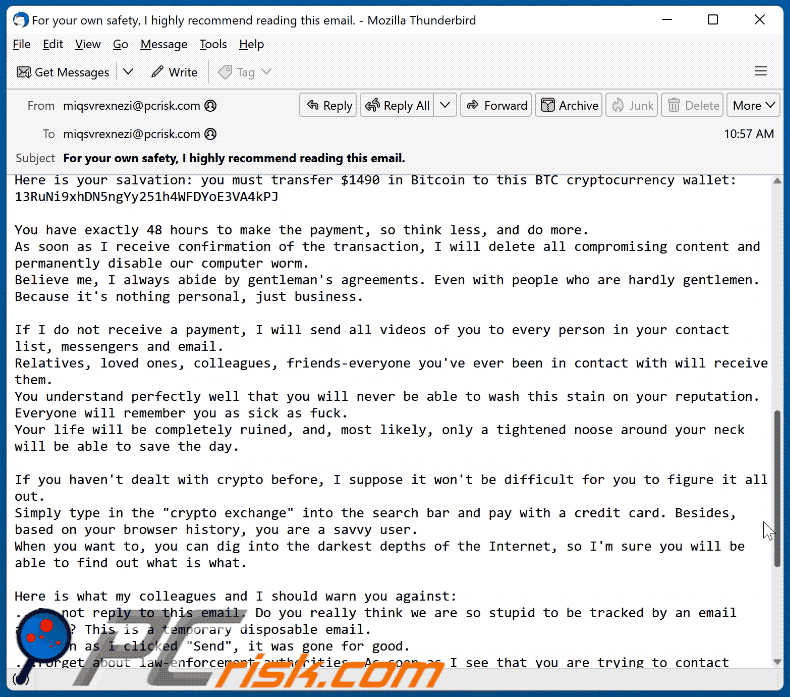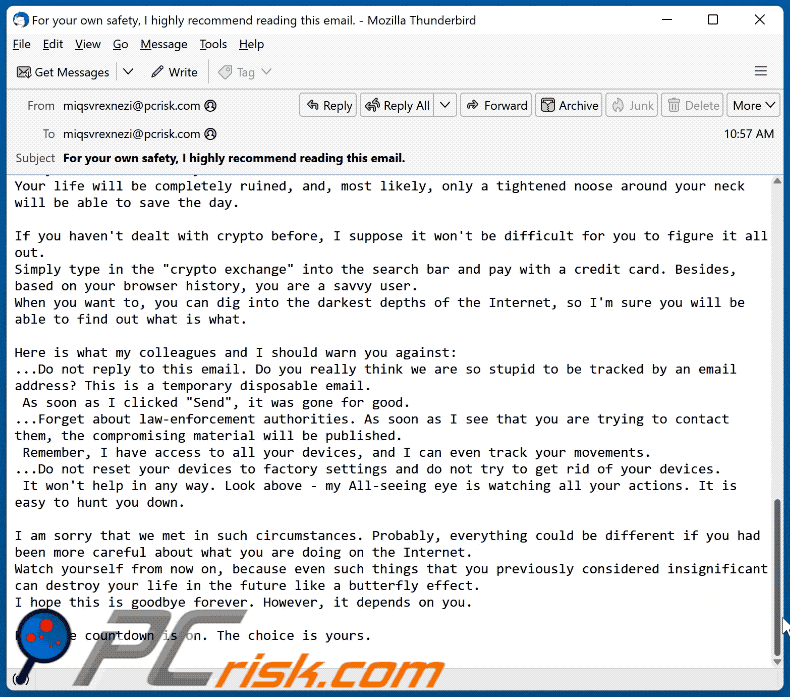
However, don't panic right away. Listen to me first, because there is always a way out.You are now on the radar of an international group of hackers, and such things never end well for anyone.
I'm sure you've heard of Anonymous. Well, compared to us, they are a bunch of schoolboys.
We are a worldwide network of several thousand professionals, each with their own role.Someone hacks corporate and government networks, someone cooperates with intelligence agencies on the most delicate tasks,
and someone (including me) deals with people like you to maintain the infrastructure of our group.
"What kind of people like me?" - that is the question you are probably asking yourself now.The answer is simple: people who like to watch highly controversial and, shall we say,
unconventional pornography on the internet that most normal people would consider perverted.
But not you!In order to leave you without any doubts, I'll explain how I found it out.
Two months ago, my colleagues and I installed spyware software on your computer and then gained access to all of your devices, including your phone.
It was easy - one of those many pop-ups on porn sites was our work.I think you already understand that we would not write to an ordinary man who watches "vanilla" and even hardcore porn - there is nothing special about that.
But the things you're watching are beyond good and evil.
So after accessing your phone and computer cameras, we recorded you masturbating to extremely controversial videos.
There is a close-up footage of you and a little square on the right with the videos you're pleasing yourself.
However, as I said earlier, there is always a way out, because even the most degraded sinner deserves leniency.
You are lucky today because I am not a sadist who enjoys other people's suffering.
Only money matters to me.Here is your salvation: you must transfer $1490 in Bitcoin to this BTC cryptocurrency wallet: 13RuNi9xhDN5ngYy251h4WFDYoE3VA4kPJ
You have exactly 48 hours to make the payment, so think less, and do more.
As soon as I receive confirmation of the transaction, I will delete all compromising content and permanently disable our computer worm.
Believe me, I always abide by gentleman's agreements. Even with people who are hardly gentlemen. Because it's nothing personal, just business.If I do not receive a payment, I will send all videos of you to every person in your contact list, messengers and email.
Relatives, loved ones, colleagues, friends-everyone you've ever been in contact with will receive them.
You understand perfectly well that you will never be able to wash this stain on your reputation.
Everyone will remember you as sick as fuck.
Your life will be completely ruined, and, most likely, only a tightened noose around your neck will be able to save the day.If you haven't dealt with crypto before, I suppose it won't be difficult for you to figure it all out.
Simply type in the "crypto exchange" into the search bar and pay with a credit card. Besides, based on your browser history, you are a savvy user.
When you want to, you can dig into the darkest depths of the Internet, so I'm sure you will be able to find out what is what.Here is what my colleagues and I should warn you against:
...Do not reply to this email. Do you really think we are so stupid to be tracked by an email address? This is a temporary disposable email.
As soon as I clicked "Send", it was gone for good.
...Forget about law-enforcement authorities. As soon as I see that you are trying to contact them, the compromising material will be published.
Remember, I have access to all your devices, and I can even track your movements.
...Do not reset your devices to factory settings and do not try to get rid of your devices.
It won't help in any way. Look above - my All-seeing eye is watching all your actions. It is easy to hunt you down.I am sorry that we met in such circumstances. Probably, everything could be different if you had been more careful about what you are doing on the Internet.
Watch yourself from now on, because even such things that you previously considered insignificant can destroy your life in the future like a butterfly effect.
I hope this is goodbye forever. However, it depends on you.P.S. The countdown is on. The choice is yours.
Full appearance of "You Are Now On The Radar Of An International Group Of Hackers" scam email:
Instant automatic malware removal:
Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
▼ DOWNLOAD Combo Cleaner
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Cleaner. 7 days free trial available. Combo Cleaner is owned and operated by Rcs Lt, the parent company of PCRisk.com read more.
Quick menu:
- What is You Are Now On The Radar Of An International Group Of Hackers sextortion scam?
- Types of malicious emails.
- How to spot a malicious email?
- What to do if you fell for an email scam?
Types of malicious emails:
![]() Phishing Emails
Phishing Emails
Most commonly, cybercriminals use deceptive emails to trick Internet users into giving away their sensitive private information, for example, login information for various online services, email accounts, or online banking information.
Such attacks are called phishing. In a phishing attack, cybercriminals usually send an email message with some popular service logo (for example, Microsoft, DHL, Amazon, Netflix), create urgency (wrong shipping address, expired password, etc.), and place a link which they hope their potential victims will click on.
After clicking the link presented in such email message, victims are redirected to a fake website that looks identical or extremely similar to the original one. Victims are then asked to enter their password, credit card details, or some other information that gets stolen by cybercriminals.
![]() Emails with Malicious Attachments
Emails with Malicious Attachments
Another popular attack vector is email spam with malicious attachments that infect users' computers with malware. Malicious attachments usually carry trojans that are capable of stealing passwords, banking information, and other sensitive information.
In such attacks, cybercriminals' main goal is to trick their potential victims into opening an infected email attachment. To achieve this goal, email messages usually talk about recently received invoices, faxes, or voice messages.
If a potential victim falls for the lure and opens the attachment, their computers get infected, and cybercriminals can collect a lot of sensitive information.
While it's a more complicated method to steal personal information (spam filters and antivirus programs usually detect such attempts), if successful, cybercriminals can get a much wider array of data and can collect information for a long period of time.
![]() Sextortion Emails
Sextortion Emails
This is a type of phishing. In this case, users receive an email claiming that a cybercriminal could access the webcam of the potential victim and has a video recording of one's masturbation.
To get rid of the video, victims are asked to pay a ransom (usually using Bitcoin or another cryptocurrency). Nevertheless, all of these claims are false - users who receive such emails should ignore and delete them.
How to spot a malicious email?
While cyber criminals try to make their lure emails look trustworthy, here are some things that you should look for when trying to spot a phishing email:
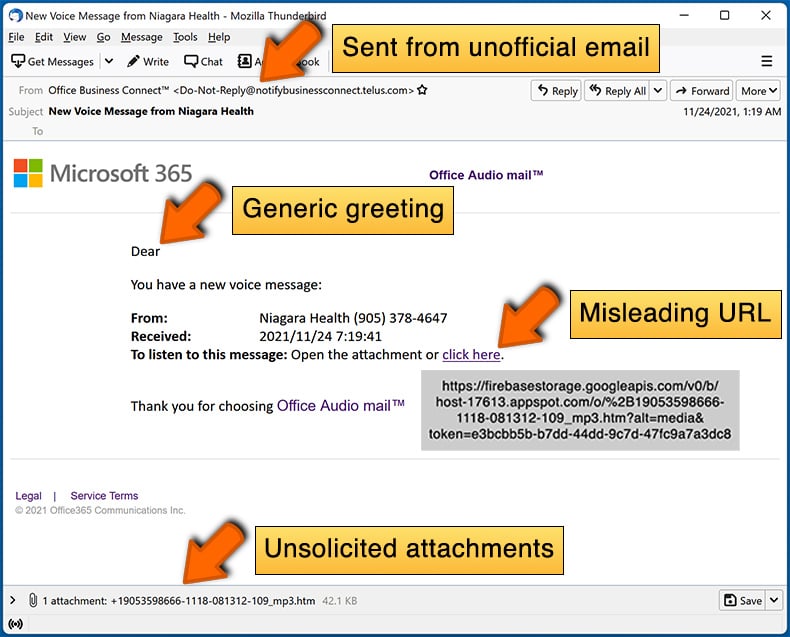
- Check the sender's ("from") email address: Hover your mouse over the "from" address and check if it's legitimate. For example, if you received an email from Microsoft, be sure to check if the email address is @microsoft.com and not something suspicious like @m1crosoft.com, @microsfot.com, @account-security-noreply.com, etc.
- Check for generic greetings: If the greeting in the email is "Dear user", "Dear @youremail.com", "Dear valued customer", this should raise suspiciousness. Most commonly, companies call you by your name. Lack of this information could signal a phishing attempt.
- Check the links in the email: Hover your mouse over the link presented in the email, if the link that appears seems suspicious, don't click it. For example, if you received an email from Microsoft and the link in the email shows that it will go to firebasestorage.googleapis.com/v0... you shouldn't trust it. It's best not to click any links in the emails but to visit the company website that sent you the email in the first place.
- Don't blindly trust email attachments: Most commonly, legitimate companies will ask you to log in to their website and to view any documents there; if you received an email with an attachment, it's a good idea to scan it with an antivirus application. Infected email attachments are a common attack vector used by cybercriminals.
To minimise the risk of opening phishing and malicious emails we recommend using Combo Cleaner Antivirus for Windows.
Example of a spam email:
What to do if you fell for an email scam?
- If you clicked on a link in a phishing email and entered your password - be sure to change your password as soon as possible. Usually, cybercriminals collect stolen credentials and then sell them to other groups that use them for malicious purposes. If you change your password in a timely manner, there's a chance that criminals won't have enough time to do any damage.
- If you entered your credit card information - contact your bank as soon as possible and explain the situation. There's a good chance that you will need to cancel your compromised credit card and get a new one.
- If you see any signs of identity theft - you should immediately contact the Federal Trade Commission. This institution will collect information about your situation and create a personal recovery plan.
- If you opened a malicious attachment - your computer is probably infected, you should scan it with a reputable antivirus application. For this purpose, we recommend using Combo Cleaner Antivirus for Windows.
- Help other Internet users - report phishing emails to Anti-Phishing Working Group, FBI’s Internet Crime Complaint Center, National Fraud Information Center and U.S. Department of Justice.
Frequently Asked Questions (FAQ)
Why did I receive this email?
The email you received is likely part of a widespread scam campaign targeting unsuspecting individuals. These scams are often sent out en masse to numerous email addresses in the hope that some recipients will fall victim to the deception.
I have provided my personal information when tricked by this email, what should I do?
Report the scam to the appropriate authorities, such as your local law enforcement agency, and change the passwords for any online accounts that may have been compromised.
Was my computer actually hacked and does the sender have any information?
It is unlikely that your computer is actually hacked, and the sender probably does not have any compromising information about you. Scammers often use scare tactics and fabricated claims to deceive individuals into believing that their devices have been compromised.
How did cyber criminals get my email password?
Cybercriminals may have obtained your password through a data breach, where information stolen from a website you have registered to could include your login credentials. Additionally, they may have acquired your password from a phishing website or another type of fraudulent webpage where it was provided.
I have sent cryptocurrency to the address presented in such email, can I get my money back?
Unfortunately, retrieving cryptocurrency sent to a fraudulent address presented in a scam email is extremely difficult. Cryptocurrency transactions are typically irreversible, meaning that once the funds have been sent to an address, they cannot be retrieved or refunded.
Will Combo Cleaner remove malware infections that were present in email attachment?
Certainly, Combo Cleaner has the capability to detect and remove nearly all recognized malware infections. It is important to note that sophisticated malware can conceal itself deeply within the system. Consequently, conducting a comprehensive full system scan is imperative to ensure thorough detection and removal.


▼ Show Discussion