Virus and Spyware Removal Guides, uninstall instructions
What kind of malware is DeepInDeep?
Our research team found the DeepInDeep ransomware while reviewing new malware submissions to VirusTotal. This program is part of the Phobos ransomware family. Ransomware is designed to encrypt files and demand ransoms for its decryption, and DeepInDeep is not an exception.
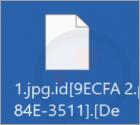
This malware alters the names of the locked files by appending them with a unique ID assigned to the victim, the cyber criminals' email address, and a ".deepindeep" extension. For example, a file originally named "1.jpg" appeared as "1.jpg.id[9ECFA84E-3511].[Deep_in_Deep@tutanota.com].deepindeep" on our testing system.
After the encryption process was finished, two ransom notes were created – one was displayed in a pop-up window ("info.hta"), and the other was dropped as a text file ("info.txt"). Based on the messages therein, it is evident that DeepInDeep targets large entities (such as companies) rather than home users.
What kind of software is TOPAPP?
Our researchers found the TOPAPP browser extension while investigating suspicious sites. The webpage endorsed TOPAPP as a tool for quick access to popular online platforms.
However, our analysis revealed that this extension operates as browser-hijacking software. It modifies browser settings in order to generate redirects to the rsrcfornow.com illegitimate search engine.

What kind of malware is Ran?
Our researchers discovered the Ran ransomware during a routine inspection of new submissions to the VirusTotal site. Designed to encrypt data to demand payment, the Ran malware also alters the titles of affected files.
On our test machine, this ransomware added the ".Ran" extension to filenames, e.g., a file titled "1.jpg" appeared as "1.jpg.Ran", "2.png" as "2.png.Ran", and so on for all of the encrypted files. After this process was completed, a ransom note – "Payment.txt" – was dropped.

What kind of malware is Yzaq?
While examining malware samples submitted to VirusTotal, we came across a ransomware variant referred to as Yzaq. This ransomware has been designed to encrypt files and change their filenames by appending the ".yzaq" extension. Moreover, Yzaq generates a ransom note, typically found in a file named "_readme.txt".
An illustration of how Yzaq modifies filenames is as follows: it transforms a file named "1.jpg" into "1.jpg.yzaq", "2.png" into "2.png.yzaq", and so forth. It is crucial to emphasize that Yzaq is part of the Djvu ransomware family. Frequently, cybercriminals distribute Djvu ransomware in conjunction with data-stealing malware, such as RedLine or Vidar.
What kind of software is Qwik Biz Tools?
Qwik Biz Tools is a rogue browser extension promising quick access to various tools commonly used in business. Our research team discovered this software's "official" promotional webpage during a routine investigation of deceptive sites.
After analyzing this extension, we determined that it is a browser hijacker. Qwik Biz Tools makes alterations to browser settings in order to promote (via redirects) the search.qwikbiztools.com fake search engine.

What kind of scam is "Bitcoin Mining"?
While inspecting spam emails, we discovered the "Bitcoin Mining" scam. This scheme is promoted on the Web. It claims that the user has been inactive on this automatic Bitcoin cloud mining platform for a long time – however, the amount of cryptocurrency mined can be retrieved.
It must be stressed that all these claims are false; they are used to deceive victims into disclosing their personal and financial data. Although, scams of this ilk may also target cryptowallet log-in credentials.

What kind of malware is Whole?
While investigating new malware submissions to the VirusTotal platform, our researchers found a ransomware-type program titled Whole. We determined that it is based on the Keylock ransomware. This malicious program encrypts data to demand ransoms for its decryption.
On our test machine, Whole encrypted files and appended their filenames with a ".whole" extension. To elaborate, a file originally named "1.jpg" appeared as "1.jpg.whole", "2.png" as "2.png.whole", etc.
Once the encryption process was completed, the desktop wallpaper was changed, and a ransom note titled – "README-ID-[victim's_ID].txt" was created. Based on the message therein, it is clear that this ransomware targets companies rather than home users.
What kind of software is KittyTab?
Our research team discovered the KittyTab browser extension during a routine inspection of dubious websites. This piece of software is endorsed as a tool that displays feline-themed browser wallpapers.
However, our analysis revealed that this extension is a browser hijacker. KittyTab changes browser settings to promote (through redirects) the kittytab.com fake search engine.
What kind of application is Search Soar USA?
Upon investigating the Search Soar USA browser extension, it became evident that this application functions as a browser hijacker. This conclusion was reached when we observed its modification of certain web browser settings. Notably, users often add such browser extensions without the awareness that they will lead to browser hijacking.
What kind of scam is "Funds For Transfer"?
Upon reviewing this deceptive email, it has become evident that it intends to deceive unsuspecting recipients into divulging personal information or sending money to scammers. It is disguised as a message concerning the release of an inheritance. Recipients should not respond to this fraudulent email.
More Articles...
Page 161 of 2139
<< Start < Prev 161 162 163 164 165 166 167 168 169 170 Next > End >>