Virus and malware infections. researches and warnings

"Your device has been blocked" - How to Remove Ransomware Infections From an Android Device?
Cybercriminals have been spreading ransomware viruses on Windows-based computers for some time. These infections became popular in mid-2006 and continue to infect personal computers and extort money from their victims.
Recently, security research began showing a rise in Android-based mobile ransomware infections. Usually, ransomware viruses exploit the names of authorities, including the FBI, USA Cyber Crime Investigations, and The ICE Cyber Crime Center - making fake claims that users must pay an amount of money (for supposed law violations such as watching pornography, using copyrighted files, etc.) to unblock their devices.
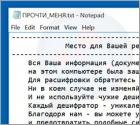
What is AMBA?
AMBA is ransomware-type virus that targets Russian websites. After infiltrating the server, AMBA encrypts most files on the system and adds the .AMBA or .RROD extension to the name of each encrypted file. A text file ("ПРОЧТИ_МЕНЯ.txt") is then created that contains a message (in Russian) encouraging server owners to contact cyber criminals via the email address provided.
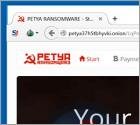
What is Petya?
Petya is ransomware distributed via malicious e-mails containing Dropbox download links to applications which, when executed, will install Petya on victims' computers. Research shows that these e-mails mainly target human resources (HR) departments of various German companies. After system infiltration, Petya encrypts portions of hard drives and makes ransom demands.

What is KimcilWare Ransomware?
KimcilWare ransomware targets websites using the Magento e-commerce platform (currently, it is not confirmed whether KimcilWare infects other platforms). During encryption, this ransomware adds a .kimcilware to each file stored on the server. Furthermore, it creates an index.html file containing a ransom-demanding message.
COMPUTER HEALTH IS CRITICAL removal instructions
What is COMPUTER HEALTH IS CRITICAL message?
This false error message pops-up when the system is infected with adware-type applications such as Games Desktop, MovieDea, and Desktop-play. All claim to provide various useful features that supposedly improve the Internet browsing experience, however, fake promises delivered by adware-type apps are simply attempts to trick users to install. Rather than providing the functionality promised, these applications gather personal data, deliver intrusive online advertisements, and generate this fake error message.
More Articles...
Page 1 of 3
<< Start < Prev 1 2 3 Next > End >>