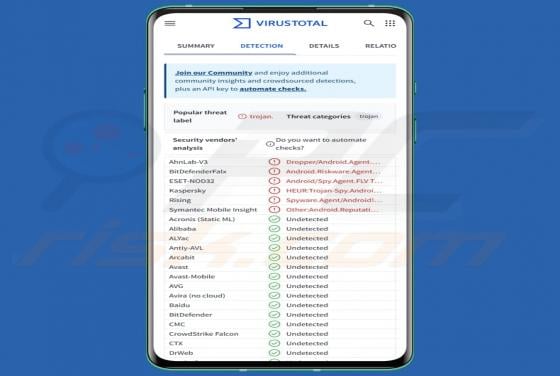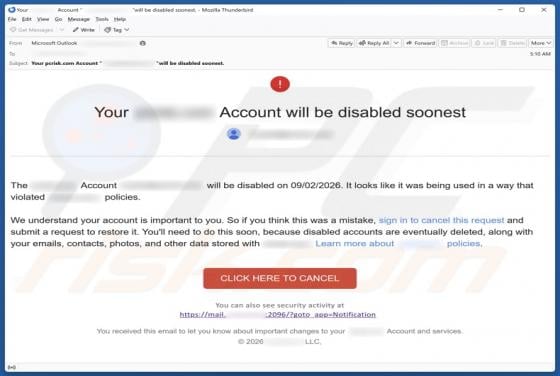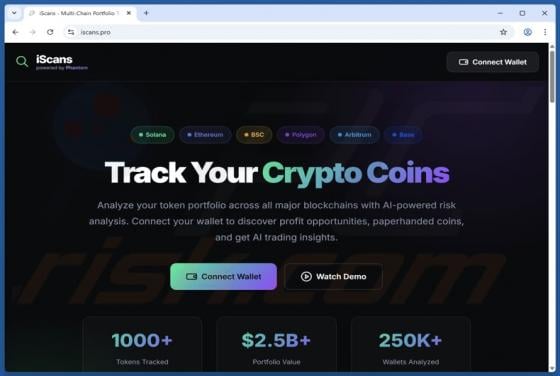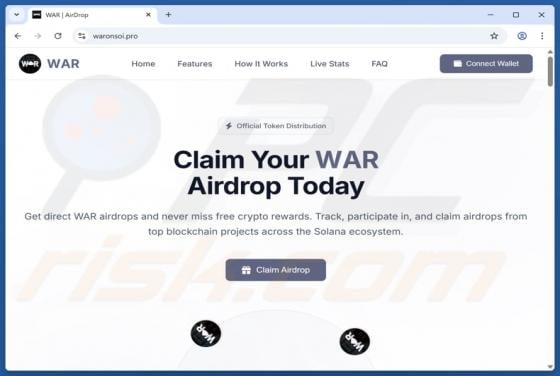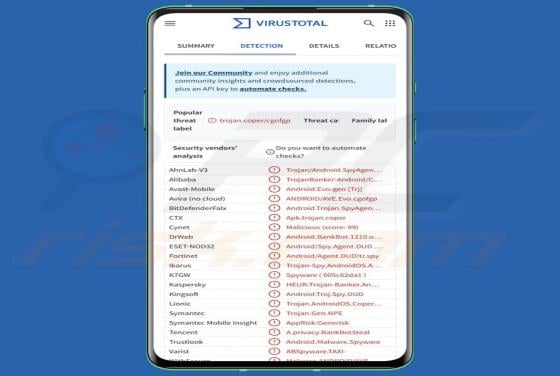
Massiv Banking Trojan (Android)
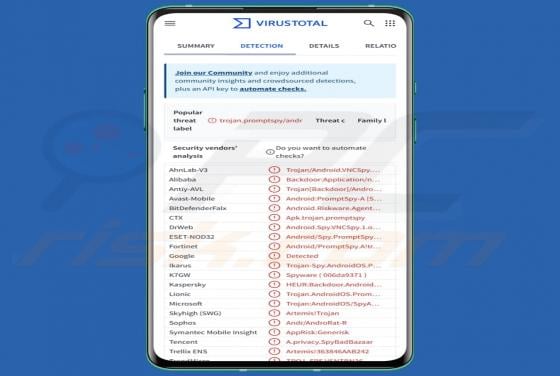
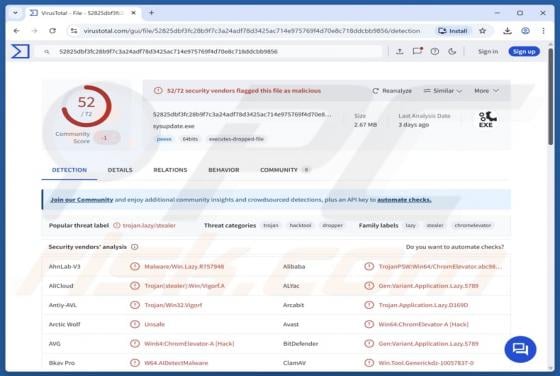
Massiv is a banking Trojan aimed at Android devices. It allows threat actors to take control of infected phones and carry out fraudulent transactions from the victim's bank accounts. Cybercriminals disguise Massiv as IPTV apps to trick users searching for online TV services. If detected on a devic