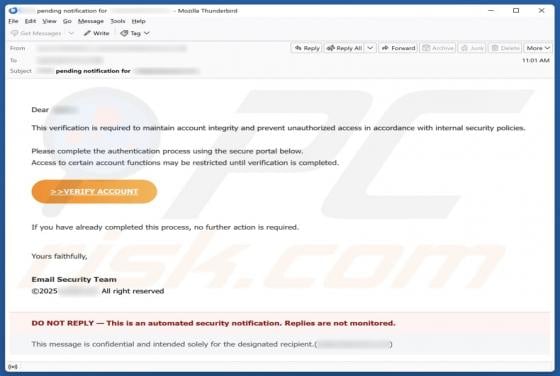
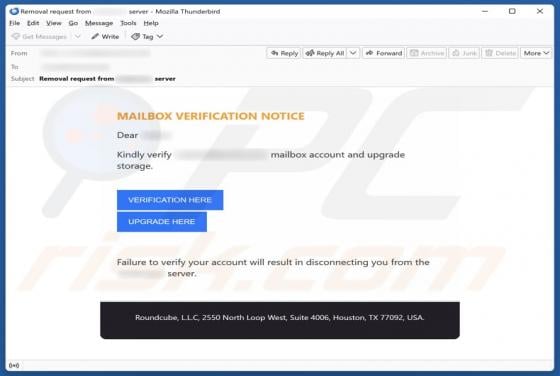
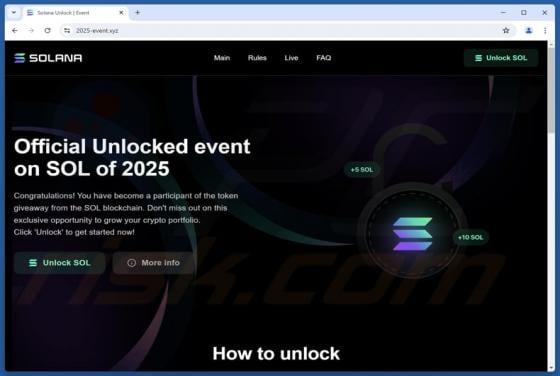
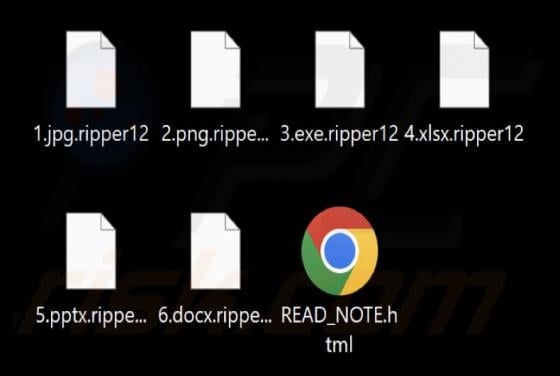
ProcessOffers Adware (Mac)
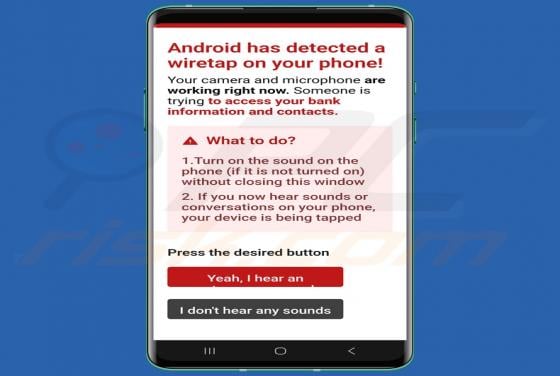
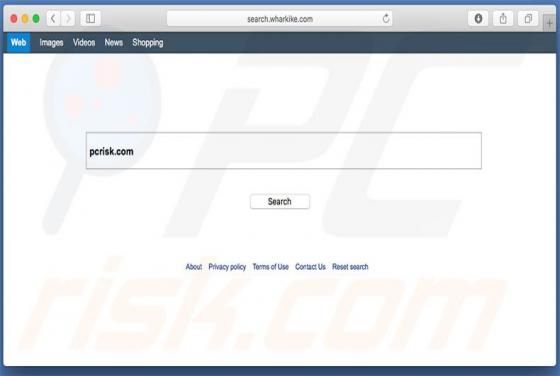
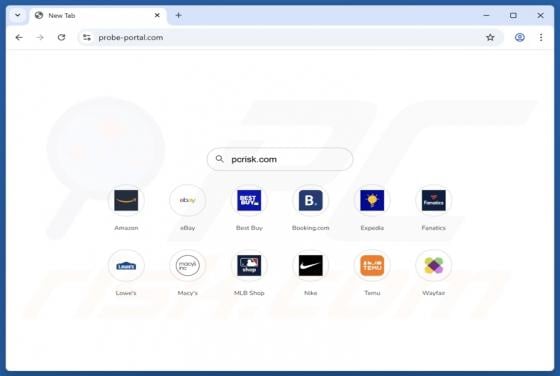
While testing ProcessOffers, we uncovered that this is an unwanted application designed to deliver unwanted and annoying advertisements. Apps of this type are classified as adware. Moreover, our analysis shows that multiple security vendors flag ProcessOffers as malicious. Thus, users should avo