Whatsapp Encryption Explained
WhatsApp, like Facebook, uses OpenSignal opensource to encrypt messages. It encrypts all chat messages and does not need to be turned on.
Here we explain how that works. And we explain how it might be possible to compromise that security by copying a phone’s private key, although reasoning through that it does not seem likely.
WhatsApp Encryption
WhatsApp uses three keys to encrypt messages as they explain in their technical specs.
They say they do not keep a copy of the private keys on their servers. WhatsApp generates the private key on your phone and leaves it there. But they store the public keys on their server. There is no risk in that, as giving away your public keys is how encryption has always worked.
To understand what that means, imagine you are chatting with someone, say, Fred. You send Fred your public key when you start to chat with him. He uses that key to encrypt messages that only you can read with your private key. Since WhatsApp does not have your private key, they could not read those.
Here are the WhatsApp keys. The Public ones identify who you are. The Session keys are used to encrypt a single chat session.
Public Keys
Identity Key Pair - generated when you install WhatsApp.
Signed Pre Key - generated at install time and signed by the Identity Key Pair.
One-Time Pre Keys - a set of keys for one-time use. A new batch is generated as they are used up.
Session Keys
Root Key - used to generate the next key, the Chain Key. A root key (usually called root certificate) type proves that it came from a certified issuer, like Google or WhatsApp, and not a hacker.
Chain Key - used to generate the next key, the Message Key.
Message Key - used to encrypt messages.
WhatsApp uses these keys and the Curve25519 encryption and SHA256 hashing algorithms to create keys and encrypt messages. When you chat with someone it saves that key exchange so that it does not have to repeat that key exchange when you chat with them again. Reinstall WhatsApp and the chats are lost, as new keys are created and those, by definition, cannot read old messages.
How to Verify that Your WhatsApp Key is Not Compromised
For each WhatsApp chat, you can verify that the Identity Key used to encrypt that message has not be compromised, meaning replaced by one generated by a hacker.
To do this, open a chat and click the contact name at the top. Then click View Security Code. Then it shows the QR code and a series of numbers at the bottom. (See graphic below.) The 60 digit string is the concatenation of your identity code and the identity code of the contact. Click the Scan Code button to make sure that they match. It will say “You opened the ‘Verify Security Code’ for the wrong phone number.’ if they do not match.
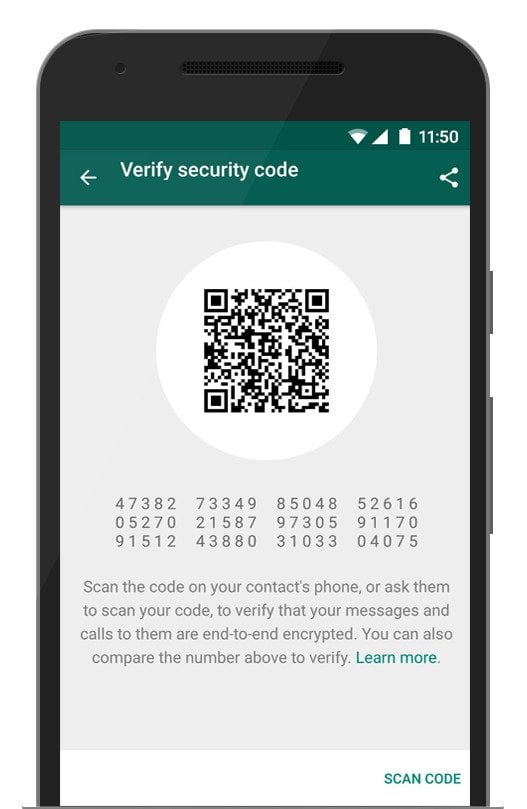
Copying the Private WhatsApp Key on an Android Device
There is a tool, located here, that says it can copy your private key from an Android device. Let’s take a quick look at that and then give an opinion as to whether it really works. Thinking through how all of this works casts doubt as to whether it actually could work.
Conceivably you should be able to copy a key, since a key by definition is not encrypted. One limiting factor that this tool might be able to overcome is that you cannot access all the folders on an Android device without root access. But this developer says that tool does not require root access. And then there is Android file-level encryption which could encrypt the file containing the clear-text key. But not every Android file is encrypted, even on a device that has turned on file encryption.
The author of the tool uses whatcrypt.com web site to download an old version of WhatsApp that the tool installs on your phone. That website lists various WhatsApp tools by which they say they can decrypt different kinds of Android databases.
The site asks for donations and not payment, which suggests it does not belong to any criminals trying to trick you into entering payment information. But if you do upload your data there you are obviously giving them that.
In order to run this procedure you have to enable USB debugging on your Android device which you do by tapping the Build Number under Settings 7 times.
The software and instructions are on this Git. On a Linux box you would need to install Git and then download the software like this:
Then on Linux you would run this script to run the utility.
- WhatsApp-Key-DB-Extractor/WhatsAppKeyDBExtract.sh
I ran through the procedure but I could not get my Android device to attach to my Windows 7 PC in USB debug mode. The phone driver installation failed on this very old version of Windows.
You might ask: “Why are you using a Windows 7 PC?” Because I am travelling in the USA and left my Ubuntu laptop at home. All I have with me is a Chromebook. And when I normally write on security I use Ubuntu or CentOs servers in the cloud. A server in the cloud has no USB port into which you can connect an Android device. And as for Windows 7, if you have to use Windows at all, my view is version 7 is the best, as it is small and simple.

Still I will explain what this program does.
You can read the script yourself right here. There’s nothing fancy there, meaning no code the developer wrote himself. It’s just a script that uses adb, push, backup, and other tools from the Android developer’s kit and Android OS to copy data and send commands to the Android device.
What the WhatsAppKeyDBExtract.sh program does is first copy the WhatsApp data to your local PC. Then it removes the current version of WhatsApp and then installs an old one (WhatsApp-2.11.431). That one perhaps exposes the private key in a way that it can be copied. What they are looking for are different files including this one: apps/com.whatsapp/f/key.
If copies that data to your PC and then reinstalls the current version of WhatsApp. It uses the Android backup programmed called backup to backup the data and then the Jar file abe.jar to extract the contents. When it runs backup it asks for your Android passcode if you have create a backup password, which most people have not. That is not the same as your screen lock password.
Now, if you have copied the private key to a PC, you could simply read it. It must be the file apps/com.whatsapp/f/key. A private key is by definition not encrypted. After all it is what you use to encrypt data so it cannot be encrypted itself.
But there is something that does not make sense. That makes me wonder whether this procedure works at all.
The program was written in May 2015, so presumably the author knows about newer versions of WhatsApp and how they stores keys. But what did installing the old version of the program onto the phone do if the key was backed up to the PC? I do not see it putting the old key back in place of the new one or visa versa or running any kind of decryption program. And reinstalling WhatsApp would have created a new, different private key which would render the one backed up useless if one wants to use it to read new messages.
But if someone could actually retrieve the old private key, they could conceivably decrypt WhatsApp messages. But if that was possible to do using this tool or any other technique then people would be doing that. I have not seen anything in the news about people doing that.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion