Cambridge University Hacks iPhone 5c that FBI Says Could Not be Hacked
Cambridge University researcher Sergei Skorobogatov demonstrated that he can brute force attack the passcode screen lock feature on the iPhone 5c. He did this by physically opening up the iPhone and then making a copy of the memory chip which he then connected to the phone using wires. Then he said you could enter every 4 digit passcode from 0001 to 1111 manually until you unlocked the phone. He did not actually do that as it would take 20 hours. Instead he proved it would work. The goal was to use copies of the memory chip, because if the security feature is enabled the iPhone erases the memory after 6 failed attempts.
The paper he wrote explaining the process is here. And a YouTube video of him demonstrating the procedure is here.
The FBI wanted to try this type of attack against iPhone owned the San Bernardino terrorists. The FBI director said, “It did not work.” Then they paid a security firm $1.3 million for their secret technique.
Sergei wrote his paper after the FBI said that.
NAND mirroring
The technique Sergei used is called NAND (negative-AND) mirroring. The NAND is the flash memory chip used in the phone.
Sergei physically removed the flash memory chip of the phone. Then he plugged a logic analyzer and oscilloscope into it to reverse engineer the protocol used to send data from that to the iPhone CPU. Then he could write a C program to emulate those instructions.
Then he cloned the memory card, just the same way that thieves clone stolen ATM and credit cards. Except it was far more difficult that that. For example, he had to add capacitors and resistors to the wires connected to the memory card to change the voltage and keep making other adjustments that would not cause errors in the process. He also had to study and figure out how Apple writes data and error correction code and hands wear-leveling on the memory card so he could write a copy of the phone’s memory in a way the the Apple iOS would accept.

So the real difficulty here was cloning the card.
It takes 1.5 hours to clone a card because of slow transfer speed. He used iTunes to repair damaged NAND cards that he made.
Once he had a working card, he attached that to the iPhone using external wires. Then he powered it up and entered the passcode.
Brute Force Attack on the Passcode
Sergei was not able to automate the process of entering the passcode into the iPhone. He had to type those manually.
If you do that more than 5 failed times on the iPhone it will erase the phone if you turn on that security feature, which is what the FBI presumed the terrorist had done. And the iPhone slows down progressively slower each time you try that to defeat a brute force attack. So it takes 20 hours to try all 10,000 possible combinations for a 4 digit pass code. If the passcode is increased to 6 digits it takes 3 months.
So his procedure does not bypass any logic in the iPhone. Instead it just makes enough copies of the memory so that you can enter failed attempt 6 times over and over and replace the erased memory card with another copy. So his real success was making a bootable copy of memory card and attaching it externally to the iPhone.
He was able to do this using local parts he got from “a local electronics distributor.”
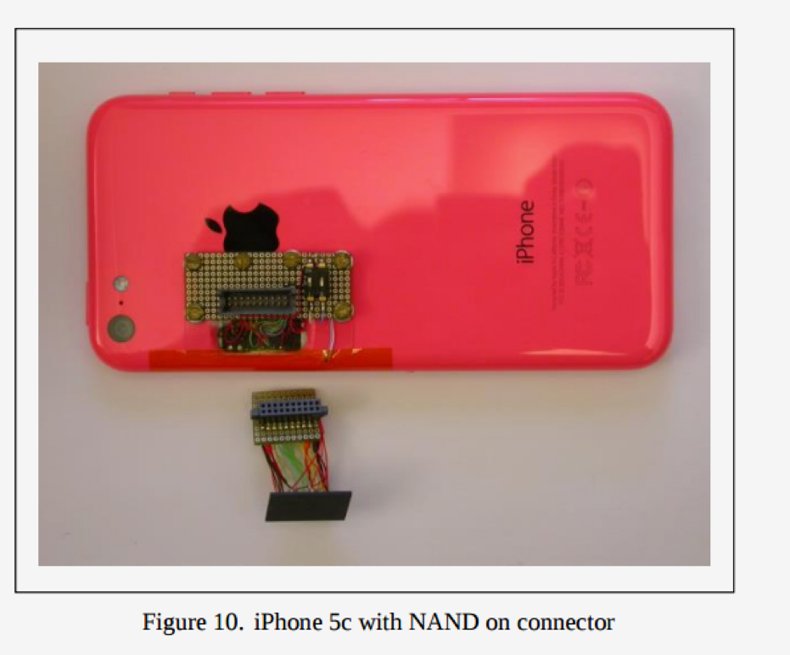
Graphic Source: Sergei Skorobogatov

Graphic Source: Sergei Skorobogatov
He bought a non-working iPhone 5C to make a backup of the memory so that he could restore it every time he messed it up. That memory was more reliable that the cloned memory card. It took him a lot of effort to clone the actual memory card onto blank ones that he said you could buy cheaply on eBay.
Another difficult was removing the memory from the iPhone without damaging it. He had to heat the chip to 300°C to make the glue holding it in place melt yet not overheat it as to damage the chip. Then he used a special thin knife to pry it loose.
Serei said wiring diagrams and instructions for opening the iPhone are supposed to be secret. But he said those are available on the internet.
This procedure will not work on the iPhone 6, although Sergei did not explain why. He did however suggest several security improvements that Apple could make to defeat this technique. Apple must have done some of those to make the iPhone 6 more secure.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion