35% of Websites Could Stop Working in January 2017 unless their Owners Update their Encryption
SHA-1 (Secure Hashing Algorithm 1) is an encryption algorithm used to encrypt traffic to and from SSL/HTTPS websites. It has some known security weaknesses. So it is being phased out and replaced with SHA-2 and SHA-3. Certificate authorities will quit issuing SHA-1 certificates in January 2017. Microsoft, Google, and Mozilla web browsers will quit supporting those then. That is all good, but the problem is 35% of websites still use these older certificates says research firm Venafi. Web browsers tell you exactly how strong the encryption in a website is when you go there by color coding the address bar. Green is good. Red is bad.
Lock means the site is safely encrypted and you can feel safe entering data there. Info means the site does not use encryption at all or in all places. And the red warning means the SSL certificate is expired, the site has been flagged by the Safe Browsing organization, or there is what Google calls “a weak security setup,” meaning SHA-1.
Should you panic? Is the internet going to stop working on January 2017? Doubtful.
First of all, the security weakness of SHA-1 is probably exaggerated where you consider practical details.
Encryption algorithms are designed to keep data safe by using such giant numbers that it would take computers so many years to brute force attack the encryption key (meaning guess until they get the correct answer) that it is fruitless to try.
Researchers at Princeton estimated that 10 years from now computers might be able to decrypt 2048-bit SSL encryption keys. They demonstrated that that can be done with keys half as large by wiring together thousands of computers and running them for 2 years straight. But a hacker going after your small business’s web site is not likely to devote such enormous resources to this problem.
Here is a nice graphic from Digicert, a certificate vendor showing what “good” looks like in each browser.
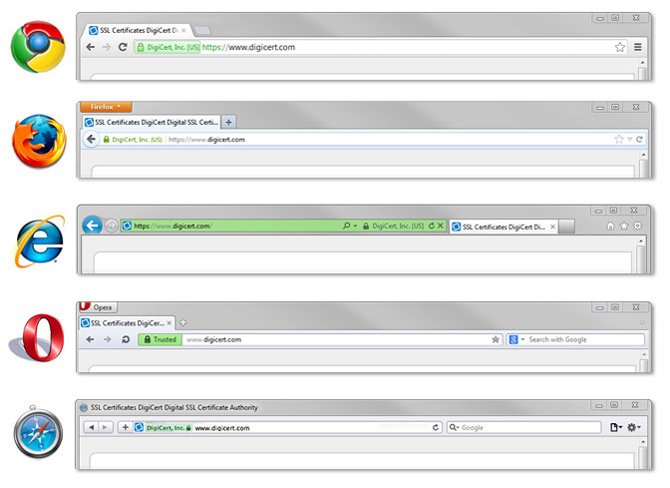
And here is how Google explains that in in another graphic:
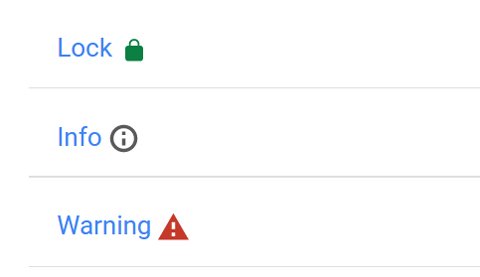
But doing that brute force attack against SHA-1 is moving closer to becoming a reality because of an weakness that lets hackers take a short cut. Plus computing power is said to double every year, according the the principle known as Moore’s law.
Bruce Schneider, writing on his security blog, put this effort in terms of dollars and cents to help people understand. It takes 2 raised to the 74th power (2**74) computing cycles to brute force attack the SHA-1 algorithm using the best available hacking algorithm. That can be translated into minutes, hour, and year. Given what it costs to rent CPU time on Amazon’s EC2 massive computing cloud, today it would cost $2.77 million to brute force attack SHA-1. If we assume that computing costs stay the same and computing power doubles every year then that cost could fall to $43,000 by 2021 and take 7 years to run.
Now, 7 years is a long time and Amazon is not likely to rent their cloud to hackers. But the point is that SHA-2, SHA-3, AES256, and other encryption and hashing algorithms take hundreds or thousands of years to brute force attack. So if there is some weakness such that a hacker can do this in 7 years instead of 1,000 years then presumably someone could wire together enough computers to get that number down to something reasonable, like a few weeks, if they were willing to throw enough money at the problem.
That is precisely what the American NSA, the British GCHQ, and the Chinese military are doing now. Hence there is some risk.
Finally, there are reasons to believe that Google, Apple, Mozilla, and Microsoft are not going to simply block 35% of the world’s internet traffic in just a few months when SHA-1 is set to expire. After all Microsoft still lets people use Windows XP and 7, which they no longer support, and which has known security problems.
Perhaps browsers might just step up their education campaign and make that icon bigger or flash a larger message. Concern over SHA-1 is what lead browser vendors to put the color there in the first place, some two years ago.
But if you have a website then you need to check with whoever maintains that and make sure you have a modern certificate. Of course not all websites even use encryption. It is not necessary to encrypt, for example, the newspaper. But if your site supports HTTPS then check the strength of your certificate.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion