Phishing Attack tied to DNS Record Update
It seems hackers also go after people who are supposed to be educated about the dangers of phishing: tech professionals.
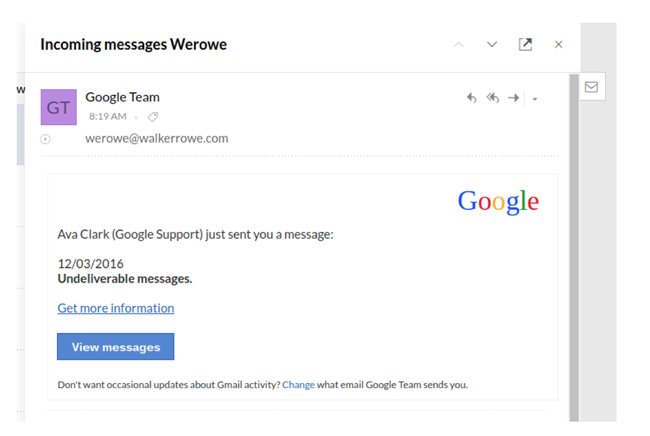
Last week I updated the DNS records for my personal email domain. So I was easily tricked when a few hours later I got this email that looks very much like it came from Google support. Luckily this was a harmless ad rotator and not malware. Or it could be that this switched to an ad rotator when it queried my browser and OS and found no match for whatever attack they had planned.

Logo - letsgophishing.com
Look at the email below. It looks very much like it came from Google, which is where I switched my domain. So hackers are monitoring DNS records to see which have been just now updated.
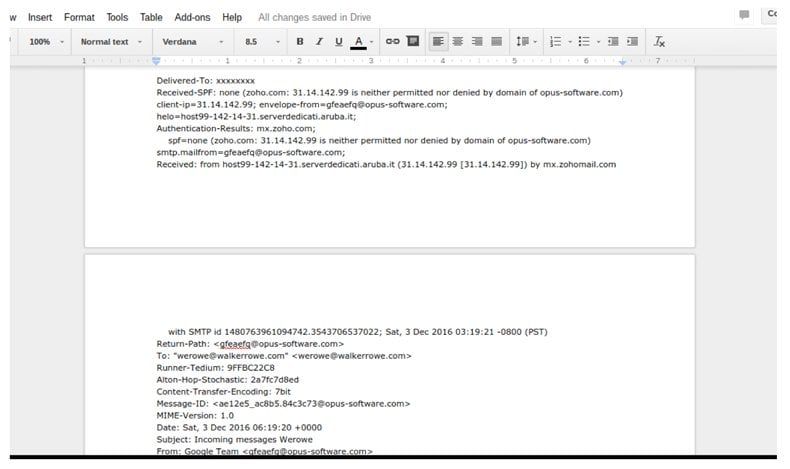
Here are the headers from that email. There is not much to be learned there except that this mail was sent by a server in Italy. Of course hackers would use a hacked device to do that and not their own. So it’s not obvious from where this mail came.
The mail looks like it came from “Google Team” but was actually sent from “opus - software . com”, or maybe. One of the security weaknesses with the SMTP (simple mail transfer protocol) is that you can spoof the sender address, in other words make it up.
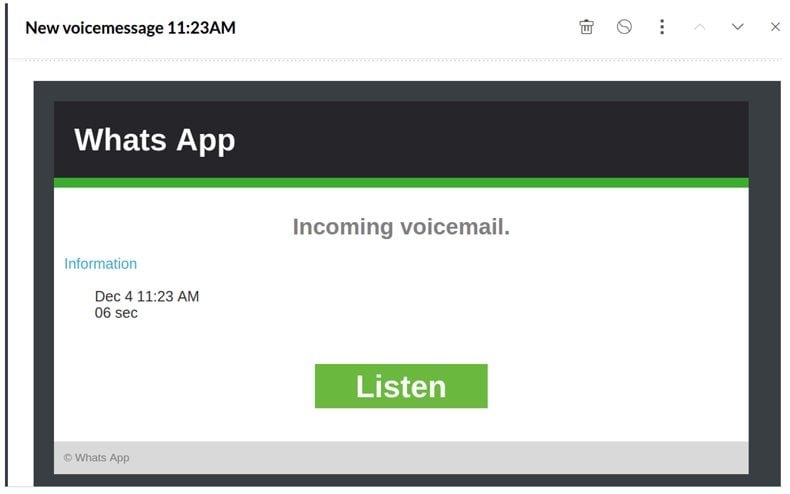
That image linked to this URL "luc.su /modules/ clucked.php". It put spaces in that so that you cannot click there. And at the time of writing this that file has been removed off that web server. But when it was up it presented this page which looks like it lets you retrieve WhatsApp voice mail online, which you cannot.
One of these links also sent me to this ad rotator, meaning a web page that does nothing but redirect to ads. You can tell by the wp-content folder that this is a WordPress site:
“stroiprestij.ru / wp-content/ uploads/ 2 015/ lambda.php”
And when I click on that now it takes me to an article on Forbes magazine. The only reason to do that is if the hacker was in some kind of affiliate relationship with Forbes. Affiliates are websites that get paid when someone lands on their page from the affiliate’s page. To be more accurate they are probably in an affiliate relationship with some kind of advertiser as Forbes probably does not have hackers as affiliates. Or they should be aware of this hack if they do.
So the takeaway message here is to beware that hackers are watching for changes to DNS records to send phishing attacks.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion