Americans Release Technical Details of Russian Hacking
The Department of Homeland Security and FBI Have released technical details of the hacking of the Democrat Party and Clinton Campaign that they first described in this document in October. As President Obama promised, the government has released proof that this hacking came from Russian intelligence agencies. Now he has punished them by expelling 35 spies and putting banking and travel sanctions on certain Russians. Americans have a unique ability to effectively punish people around the world that way, since most international commerce uses American dollars and some part of the US banking infrastructure.
Obama also promised that any technical analysis would not reveal all the details of how they uncovered what the Russians did, saying that would give away secret techniques. Instead the document includes a list of malware, exploit kits, viruses, domains, techniques, and IP addresses used by the Russians. The document also gives advice how system administrators can help secure their network against these attacks.
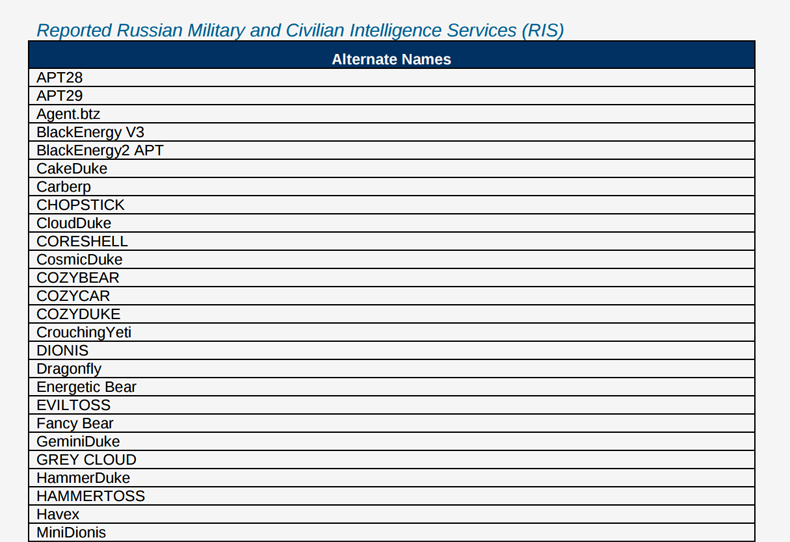
The government is calling this attack Grizzly Steppe and laying blame directly with the RIS (Russian civilians and military intelligence services). They divided these advanced persistent threats into two groups, by the dates of the attack: Summer 2015 (APT 28) and Spring 2016 (APT 29).
CSV and STIX Files
Here are the CSV and STIX files that go with the report. Those give details needed to identity these attacks.
STIX is an XML file format used to exchange virus information between different databases. CSV of course is just a list, with no format, except comma-delimiters.
The CSV Indicators are here and the STIX indicators here.
Here is a sample of the STIX. The top part is just the introduction.
At the top of the CSV file, it lists some of the Russian and other domains used by the attackers. They also list IP addresses. Those are not just in Russia. Many are in the USA.
ritsoperrol[.]ru
littjohnwilhap[.]ru
wilcarobbe[.]com
one2shoppee[.]com
insta[.]reduct[.]ru
editprod[.]waterfilter[.]in[.]ua
mymodule[.]waterfilter[.]in[.]ua
List of Viruses, Exploit Kits, and Malware
Here is part of the malware listed in the document. The list is not long. Many of the viruses are old. For example, here is a January 2015 technical analysis of one called Seadog.
It might be that the government is keeping secret some of the zero-day exploits.
Attack Vector
The government says that phishing was one of the main attack vectors (It always is.). The Russians sent emails to 1,000 individuals. To create the illusion that some of these came from US government and other legitimate organizations, like the Democrat Party, the emails were spoofed to look like they came from those domains. Then the recipients were tricked into logging into and entering their credentials into what looked like official US government or other websites.
Other attacks used SQL injection, Cross-site scripting (XSS), and known vulnerabilities of the devices they attacked.
Yara Signatures
The government doc shares one Yara signature. It is not clear why they only give one and not one for each virus.
Yara is not an anti-virus tool. Instead it is a way for security researchers to classify malware when they are doing forensics. The Yara file format looks for strings of text, measures file sizes, etc. to identify a virus.
For example, the sample given in the doc below is for a malware called the PAS_TOOL_PHP_WEB_KIT. The source code for it is on Github here. It is some kind of SQL injection or XSS attack using PHP.
To use this you would save the rule as a text file then run it using yara against a file that you believe might be malware. You can download Yara from here.
If you compare the rule below to the malware on Github you can see that all it basically does is look for certain strings to see if they match.
Yara Signature
rule PAS_TOOL_PHP_WEB_KIT
{
meta:
description = "PAS TOOL PHP WEB KIT FOUND"
strings:
$php = "$base64decode = /\='base'\.\(\d+\*\d+\)\.'_de'\.'code'/
$strreplace = "(str_replace("
$md5 = ".substr(md5(strrev("
$gzinflate = "gzinflate"
$cookie = "_COOKIE"
$isset = "isset"
condition:
(filesize > 20KB and filesize < 22KB) and
#cookie == 2 and
#isset == 3 and
all of them
}
Hardening Steps
The rest of the document gives advice on how to harden against these Russian attacks. There is nothing new here regarding hardening techniques. Instead they just say to enter those IP addresses and domains into your firewall. Of course antivirus software vendors will take the STIX file and add those rules to their databases and push those out to their customers.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion