Security Hazards for Manufacturers using ICS Protocols
The massive DDOS attack on the Akamai CDN (content distribution network) that last year took down Netflix, Amazon, and others because of compromised IP cameras that were using a default password shined the spotlight on IoT security. In particular, there is the concern about attacks on heavy industrial machinery, valves, gas pipelines, turbines, electric grids, etc. and other equipment. Many if not most of these use the ModBus protocol to communicate between PLC and SCADA devices, which control this equipment. ModBus has no authentic at all and transmits its data in clear text.
Most industrial machines do not have a public IP address. Ethernet does not even work throughout all of the plant as part of the industrial network is serial and other protocols that a hacker could not attack using tools written for Linux or Windows.
But there are many devices exposed to the internet. Here is via a Shodan query a list of wind turbines on the internet, for example. And here are devices that have “ics” somewhere in their name.
The most famous of all industrial ICS hacking was the Stuxnet worm launched by the USA and Israel against Iran’s nuclear fuel enrichment program. By hacking PLC controllers the spies were able to cause expensive centrifuges used to separate fuel to rotate at such high speed that they broke.
Some other notable attacks include:
- 1982 Trans-Siberian pipeline section destroyed by Trojan in SCADA system. This caused an explosion.
- Venezuela refinery attacked.
- 2003 US hydroelectric decoy (honeypot?) system lost power after hack by APT1 (Chinese military espionage).
- 2003 power outage in 7 states.
- 2013 two security researchers took over an oil rig.
A report says that in 2013 there were 200 attacks in the USA. 59% of attacks were against the energy sector. And 79% worked of those worked. Not sure how they calculated that as any device attached to the internet is attacked all the time, like your home or office router and website.
ICS Industrial Control Systems
There are many ICS protocols. One reason is there are many is certain manufacturers have their own. The shortened list includes MTConnect, OPC, PPC UA, Profinet (industrial ethernet), BACnet (building automation), ModBus (SCADA, PLC, read meters), ZigBee (home automation mesh network), INSTEON, Z-Wave (home automation), LonTalk, KNX (building control), EnOcean (low power wireless), CC-Link Industrial Networks (Mitsubishi Electric), and DNP3 (power systems automation).
Here is a graphic of an Industrial Control Network. You can see that Ethernet extends through the network to the devices. But there are lots of industrial protocols so there are network gateways to translate traffic from those to Ethernet and back.
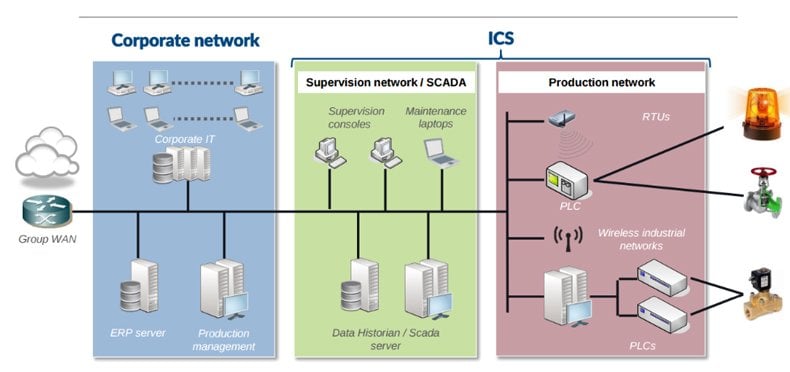
Graphic Source Blackhat
With PLCs (programmable logical controllers) we are talking about sending very small amounts of data to specific memory address to turn on and off valves, lathes, and other physical devices. So there is no way to run, for example, Windows or Linux malware on that link.
PLC commands are very short bytes of data. This is decades old technology still in wide use. The memory address in PLC controllers are called nodes. To program those engineers use what is called ladder logic. The devices sends and receives some short field like (field length)(data bytes) to a specific node. That translates into a signal, like on or off, depending on the manufacturer of the device and their instruction set. The devices talk to the control SCADA system and other PLC devices as well via network gateways and protocol convertors.
SCADA
SCADA (supervisory control and data acquisition) is a master-slave designed system that connects terminal screens, supervisor systems, and PLC controllers together. The main network protocol for that is ModBus, which has no authentication and is in clear text. We discuss that below.
Here is another view of SCADA:
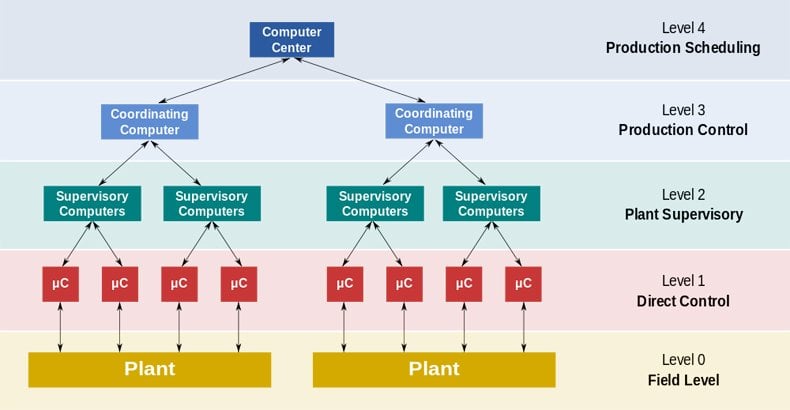
Graphic Source WikiPedia
Level 0 are sensors. Level 1 is PLC. The others you can simply read off the graphic.
ModBus Protocol
This is used with some (many) PLC devices used to connect monitors (RTU or remote terminal unit), HMI (human machine interface), to SCADA systems. The network data is sent in clear text. There is no authentication. This is probably because this was created in the 1970s from a serial protocol, before IP networks emerged as the dominate networking standard.
John Rinaldi of RTA Automation, manufacturer of serial to ethernet and other industrial network gateways says, “If you are new to Modbus, or new to security, you already know everything there is to know about Modbus security: NOTHING. There is no security in Modbus, Modbus RTU, or Modbus TCP. It doesn’t exist.”
Since the protocol does not verify (authenticate) the device, a hacker could insert their own network router in between two points and take over equipment if they knew what kind of device was located there and had the Siemens of other PLC manual to know how to program the device. There would be no IP address. So they would need someway to know what is plugged into which RS232 or other port.
There have been attacks on the Ethernet part of the network too. For example, the CVE-2014-2250 vulnerability in the Siemens SIMATIC S7-1200 was found because there was not enough randomness in generating keys. If a hacker can find the keys used to encrypt traffic then they can spoof that device, if they are not using SSL, thus taking it over and hijack the session.
How to Reduce the Risk of Hacking in an Industrial Control System
Obviously the best way to reduce the risk to ICS systems is to not have public IP address for these and put authentication in front. But some devices by nature need to be on the internet so that technicians and automation systems can work with them from the distance.
Most devices have a web server somewhere in the attached devices. So the manufacturer can create a login screen here. If not, they can install another nginx or Apache web server running as a reverse proxy server in front of that to have a place to make a login screen. And there are special industrial firewalls like the Tofino Modbus TCP Enforcer that whitelists commands.
Warning to Metasploit Users
Someone looking into this would be wise not to try to use Shodan to find and then Metasploit, Nmap, or PLCScan to try to hack into ICS devices. Such experimentation can cause genuine physical damage to equipment and people. Plus it is against the law.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion