WannaCry: Thoroughly Preventable
The Wake-up Call
Microsoft has labeled the cyber wildfire called WannaCry a massive wake up call. By Saturday, May 13, it was reported that over 200,000 computers from over 100 countries had been infected with the ransomware in question. The speed at which WannaCry propagated was extraordinary, which leveraged a Windows SMB Exploit which had already had a patch released, by targeting computers and systems without the patch installed. It has been reported that the SMB exploit is the recently dumped EternalBlue, a collection of hacking tools allegedly developed by the NSA and dumped by the hacking group “The Shadow Brokers”.
The ransomware affected the British National Health Service, Nissan manufacturing plants, as well as numerous telecoms and well-developed organizations which one would assume, would do their utmost to protect against ransomware and similar attacks. The version which caused all the fuss had a killswitch which was exploited by the security analyst who goes by the name of MalwareTech to greatly reduce the spread and infection rate of the malware. As to whether the killswitch was a feature included by the ransomware’s creators or was merely an oversight is not apparent yet. Regardless, Europol, cyber security companies, software manufacturers, and other service providers are sending out multiple warnings to help mitigate the damage done. By the end of the weekend, it was estimated that the creators of WannaCry had received over a hundred payments totally over 25,000 USD.
Unsophisticated Code
Security analysts who began investigating the code on Friday concluded that this is neither new nor sophisticated ransomware. As early as February 10, a researcher from MalwareBytes confirmed the discovery of the WCry family of ransomware which was involved in a brief campaign in March. The attacks of WCry was so unspectacular that it barely blipped on the cyber threat radar and was easily dealt with by Trend Micro. WCry relied on the tried and tested boring methods of scam emails and traditional malware droppers to spread the malicious code. As was mentioned above was how the gang leveraged EternalBlue to distribute the code at a truly phenomenal rate. Despite using EternalBlue, the code and methods of receiving payment for WannaCry are relatively primitive. For example, in sophisticated attacks will have a Bitcoin address for each infection, WannaCry had a total of three. This would make it determining you had indeed paid the ransom and who had not difficult, to say the least. It is thus advised not to pay as with most ransomware attacks there is no guarantee that once paid files will be unencrypted, the more so with WannaCry.
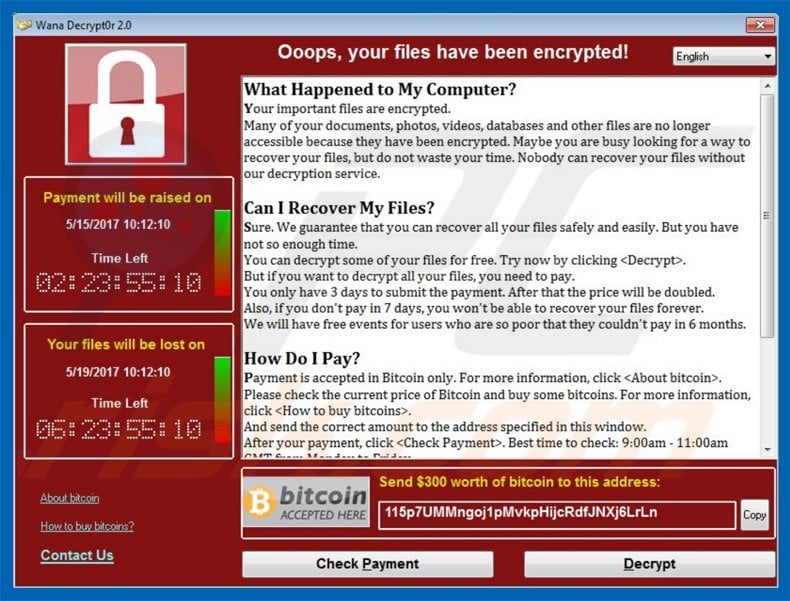
Another example of the unsophisticated nature of this attack despite its virulence is the discovery of the killswitch by MalwareTech. It was found that the ransomware keeps pinging the following domain, iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com. The executable malicious code would only deploy if the domain was unregistered. MalwareTech registered the domain, and rather humorously due to its simplicity, prevented further infections. Despite the unsophisticated nature of the attack a flaw is yet to be found in the encryption of files to restore the encrypted files.
Version 2.0
No second version of WannCry has been detected but that doesn’t mean that one will not rise its ugly head. Given the media coverage that this attack has already received, there will probably be a string of copycat hacks. There have been some claims of a second version which lacks the previously flawed killswitch exists, however experts contacted by Bleeding Computer have yet to detect the second version. That been said researchers at Kaspersky have said that they have detected a second version lacking a killswitch equipped with the same SMB exploit, potentially created by someone else. Apparently, this version detected by researchers at Kaspersky is corrupted. However, a working version can be made. It can be safely assumed that there will be future attacks using WannaCry or a newer version. The only thing that would prevent further attacks is if all the vulnerable systems are patched. It can be safely assumed that despite the media attention thousands of computers will remain vulnerable.
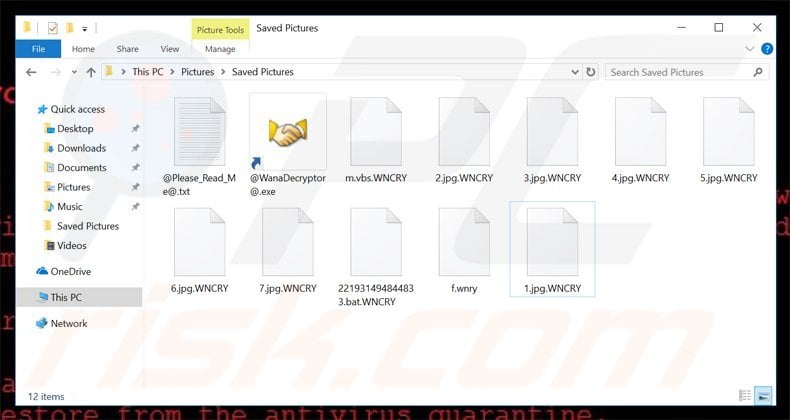
The Same Old Story
I imagine that security experts are getting fairly tired of saying the same thing over and over again to try help protect the public from further attacks. Backups, patches, and up to date updates are going to be given as advice as many times as systems infected. To that effect, this attack is sad and frustrating in the sense that it infected so many systems even though a patch had been released in March by Microsoft to correct the SMB exploit. Microsoft has since released patches for Windows XP, a product it stopped supporting in 2014, to help prevent further attacks. Additionally, CERT has released a tool to prevent WannaCry from running.
As was mentioned previously it is not advised to pay, based on the unsophisticated nature of the attack and paying the ransom will not prevent attackers from attempting a similar attack again. If you have up to date patches and good backups you or your organization have very little to worry about. Hopefully, this attack serves to be a wake-up call to those infected or just those who believe updating systems can be a waste of time. Just by keeping up to date on released patches would have prevented this attack. Such a simple fix could have saved many the embarrassment and financial cost of buying bitcoins. One can hope that this event will serve to educate more of the public in taking cyber security seriously in order to prevent the thoroughly preventable.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion