Qatar’s State News Agency Hacked
Fake News Hack
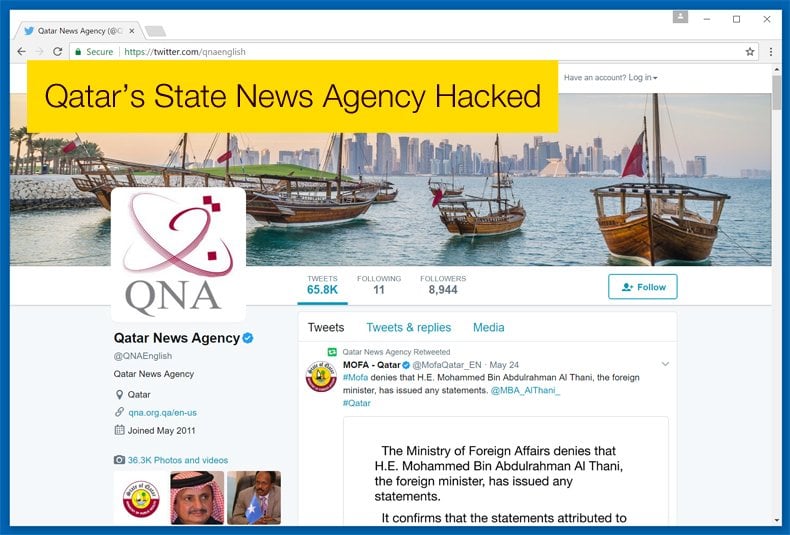
On May 23 reports surfaced that Qatar’s state news agency was hacked. Their website was hacked and allegedly uploaded fake news story pertaining to statements made by Emir Sheikh Tamim bin Hamad Al-Thani, Qatar’s current leader, supposedly made as to the small oil-rich nation’s political relations. The fake news stories included calling Hamas "the legitimate representative of the Palestinian people," comments as to the strong relations with Iran, and supposed tensions between Qatar and the US President Donald Trump. Qatari government officials and the news agency in question were quick to say that the news agency was indeed hacked and there is no substance to the stories.
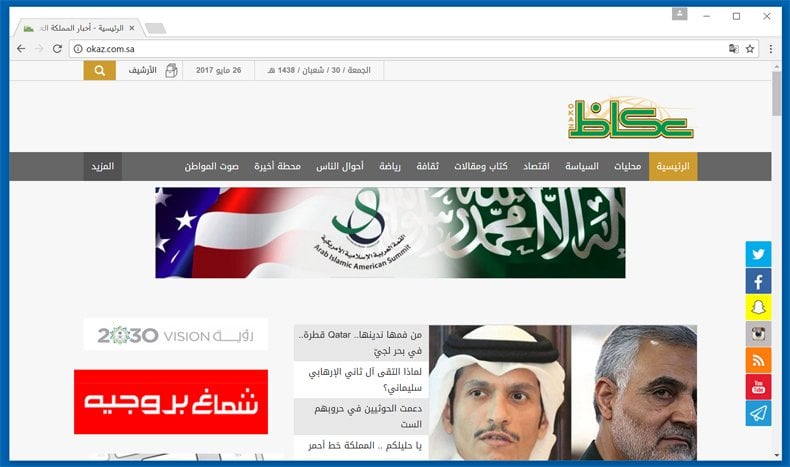
Despite the broad denials and the admission of being hacked, many of Qatar’s allies in the region were quick to condemn the nation. The Saudi Arabian news agency Okaz was most vociferous in its coverage. Comments such as "Qatar splits the rank, sides with the enemies of the nation." Illustrate that the denial was not accepted by Saudi Arabia and other Gulf nations. As if in retaliation Al Jazeera’s website, with its head office based in Doha, was blocked in Saudi Arabia and the United Arab Emirates.
As of yet, the identity of the hackers is unknown. It is also unknown as to whether this is state sponsored cyber espionage or the work of a private hacking group looking to stir trouble in an already unstable region. This would not be the first time the agency has been hacked, with an alleged hack occurring in April 2016 which also targeted Al Jazeera. Government Officials in Qatar have denounced the act and have stated that they intend to punish those responsible. Such statements may just be hot air given the extreme difficulty experienced by law enforcement agencies globally in convicting either group acting to further state goals through espionage or cyber criminals looking to defraud, embezzle, and steal money from unsuspecting institutions and individuals.
State-sponsored actors?
While the identity of the attacker is unknown it has led some to believe that whoever was involved may be state sponsored. The nature of the attack in spreading fake news has become a tell-tale calling card for past state-sponsored attacks. The recent accusations as to Russia’s involvement in the US Presidential Elections and possibly the more recent French Elections have got many in the cybersecurity industry wishing to open the debate on cyber espionage and what, if anything, amounts to cyber warfare. While answers to this debate will potentially reveal what many states spend a lot of time and resources secret they may in future assist in preventing hacking tool dumps as the one the NSA just witnessed which allowed a variety of ransomware and malware to spread like wildfire.
With the hack into Qatar, all experts not involved in the investigation can do is speculate as to the authors of the attack. Until concrete evidence is provided by Qatari officials this attack like so many others may be swept under carpet. This is due in part to the difficulty of identifying attackers as well as the lack of an independent press in the small Gulf nation as well as in many other nations in the immediate area. This lack of information can be particularly frustrating for those wishing to analyze the attack with the intention of preventing further similar attacks.
The assumption can be made that the attackers are probably not linked to organized crime in any way as there was no real financial loss or fraud. It is unclear if there was any significant data breach as none was admitted. This would perhaps mean that the attack may have been state-sponsored or done by hacktivists with the goal of embarrassing the news agency. If state sponsored the aims may be far harder to discern but considering the reaction of Saudi Arabia and the United Arab Emirates the goal may be part of a far wider campaign to destabilize the region with any number of parties benefitting from this.
The Rise of Cyber Espionage
Since the advent of the Stuxnet worm, probably created by the US in conjunction with Israeli secret services, many nations have seen the advantages of deploying techniques used by hackers and organized criminal enterprises as means to spy on one another. Since 2010 there has been a marked rise year on year of cyber espionage attacks. Unlike malware and ransomware attacks which happen fairly quickly and are easily detectable, state-sponsored attacks are often far harder to detect and are only often detected years after they were deployed. If the Qatar hack was state-sponsored it is was far blunter than the usual attack which generally looks to gather information. State-sponsored attacks are becoming an increasingly desirable method of gathering information and achieving other goals intelligence agencies require. Such means offer a low-cost and low-risk method of achieving goals. Been able to attribute attacks to the relevant agency is incredibly low with success rates been exceptionally high. Often such attacks do not require the development of malware or zero-day exploits. If they do need such tools they can be created in house with budgets criminal organizations can only dream of.
Whether or not the Qatar hack was state sponsored should not detract from opening the debate further around cyber espionage and cyber war. Given that, via the use of technology, intelligence agencies are less reliant on dangerous and costly missions to achieve their goals and can now employ low cost and low risk hacking methods open discussions are needed to prevent abuses of human rights such as privacy, security, and free association.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion