Multi-Platform Virus Spread Through Facebook Messenger
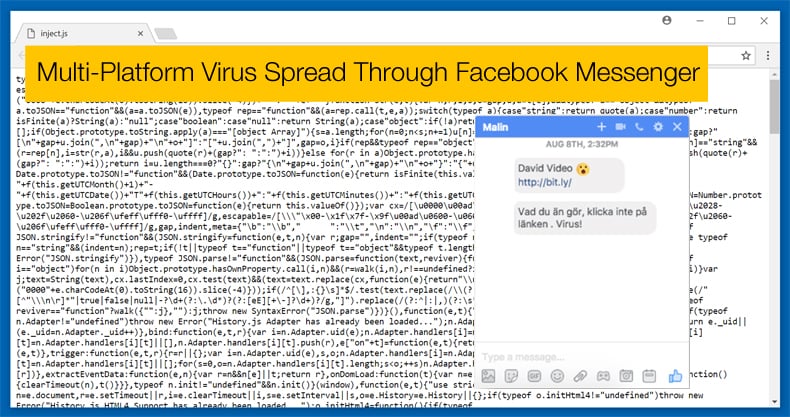
Security experts are warning against opening messages sent to Facebook users with a video link attached. Do not open the video even if sent by a friend. The video links to numerous fake websites, depending on the users OS and browser, in an attempt to install malicious software on their systems. The attackers make use of social engineering to lure the potential victim into clicking on the required links. On the initial message, it will read “{ your friend name } Video” followed by a bit.ly link. Researchers are yet to determine how the malware spreads, they assume spammers are using compromised accounts, hijacked browsers, or clickjacking techniques to spread the malicious link.
David Jacoby, the researcher at Kaspersky Labs who discovered the malware when he received a message from a friend on Facebook he hardly speaks to. He immediately knew the message was suspicious and began analysing the message. In a short space of time, he discovered that the message was indeed part of an advanced and carefully crafted adware campaign capable of infecting user’s systems across platforms be they Windows, MacOS, and Linux.
The initial spreading mechanism appears to be through Facebook Messenger, a method employed before to spread various types of malware. Other than how the message promulgates further is unknown. In the past compromised accounts, hijacked browsers, or clickjacking has been the favoured method employed by spammers when utilising social media platforms to spread adware, for example.
What is known is that the link once clicked redirects to a modified Google docs file which appears as if ready to stream the video. Once the victim clicks on the video in the hope that it will play, the malware redirects to a website which enumerates their browser, operating system and other vital information. Depending on which operating system the victim uses they will be directed to other websites. This method of attack is called domain chaining and uses language, geo location, browser information, operating system, installed plugins and cookies to redirect to multiple websites used by the spammers. By doing this the spammers have the ability to move the victim to websites of their choosing, often employing social engineering tactics to get victims to click on certain links.
Different browser information directs to different landing pages
One of the interesting things discovered by David Jacoby was that depending on which browser the victim used also directing them to specific landing pages only used in instances where that browser was used. For instance, when Firefox was used the victim would be provided with a fake Flash update needing installation. For those using Google Chrome, they would be redirected to a landing page resembling YouTube with a fake YouTube logo. The victim would then be notified with a fake error message which when clicked a malicious Chrome extension would be downloaded. The malicious Chrome extension in question is a downloader.
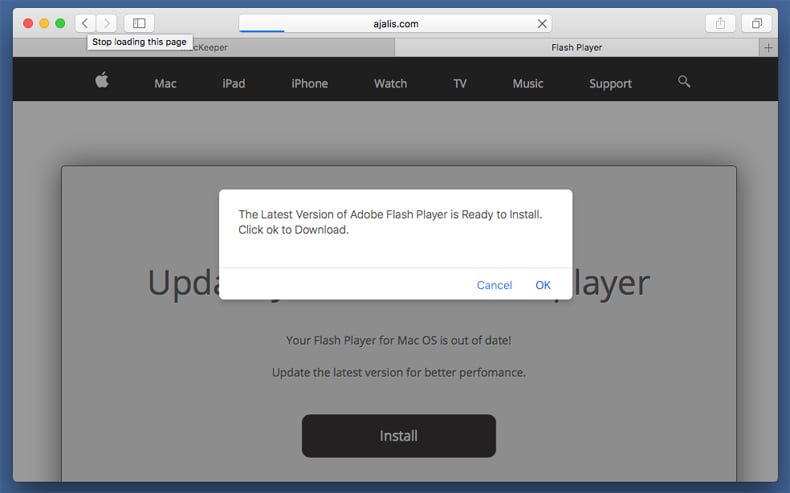
Victims using OSX Safari landed up on a similar website to the Firefox instance, the only difference being that it was modified to OSX users. Victims are presented with a fake Flash Media Player update. Once clicked then an OSX executable .dmg file is downloaded which is also adware. It has been a while since Facebook has been used to spread adware, what made this particular instance unique was the use of Google Docs to redirect to specific landing pages depending on what browser is used. There is currently no evidence that other malware, such as Trojans or exploits, are being in used in conjunction with the adware. For the moment it appears the spammers are content with generating money through ads and getting Facebook users’ information.
Previous instance where Facebook has been used to spread malware
Given the popularity of Facebook and other social media platforms, it is little wonder they would be exploited by hackers. Not only does social media platforms give hackers access to potentially millions of victims, platforms like Facebook contain a treasure trove of user information generally handed over willingly or often unknowingly by users. The above instance is just one more example of Facebook being used for nefarious ends.
Towards the end of 2016 Facebook users witnessed a spate of potential threats. Towards the end of November in that year Facebook users were warned not to open .jpg files sent via Messenger. The file was used as a delivery method to install the now infamous Locky ransomware. In an earlier instance it was reported that .svg files were used to deliver the ransomware, however, Facebook denied that it was the case. In the second instance, security researchers in Israel based at the firm Check Point discovered a vulnerability in both Facebook and LinkedIn that would forcibly download the maliciously coded image file onto a victim’s system. In some case, the image would need to be clicked by the potential victim in others clicking was not necessary. Once downloaded the malicious code would install a variant of Locky which would begin the process of encrypting files and demanding a ransom. Certain versions of Locky also had the ability to encrypt files on the user’s network, turning a bad day worse.
Facebook users cautioned
It is advised to anyone who uses a social media platform, whether that is Facebook, LinkedIn, or any other to not open any .jpg, .svg, or video files sent to you even if by a friend that appears suspicious. While the most recent example is an example of adware redirecting victims to websites in an attempt to get them to click on a variety of links, the research as to how the virus actually spreads is still been conducted and may still have a few other surprises in store.
It is further advised to keep any anti-virus software you may have up to date. Further to keep your operating system up to date can also go a long way in defending against malicious cyber-attacks. Given that most users of a computer or a smart phone has access and uses social media incorporating a little bit of scepticism in your daily routine may be beneficial.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion