TrickBot Evolves…Again
Fast becoming the favored banking Trojan, TrickBot has been updated to steal funds from Coinbase accounts. Coinbase seems to be having a torrid time of late with a surge of complaints from its customer base for the year so far. The rise in complaints has been a reported staggering 4,700% when compared to last year. The total for 2016 is 6 complaints. The amount for 2017 so far is sitting at 442. Any real or perceived vulnerabilities to the platform offered by Coinbase may signal battle stations.
As for TrickBot, since June of this year, it has been updated every month to target more than just the traditional banking sector. Given that recently Bitcoin reached the $5,000 mark on Friday before initiated a mass selloff and returning to $4,500, been able to steal such a highly volatile commodity must be on many hackers Christmas lists. As a malware strain, it is relatively new, first surfacing in the wild in the autumn of 2016. It is believed to be created by some of the Russian hackers behind the Dyre banking Trojan, with some of the operators being arrested in 2015 in Russia. This sentiment is shared by many within the cyber security sector.
Another month, another update
In June of this year, TrickBot underwent one of its biggest updates. The update enabled the Trojan to target Customer Relationship (CRM) providers as well as PayPal users. Essentially this was done by adding even more fake online login screens used to steal credentials from multiple organizations based in a variety of countries. By April of 2017, TrickBot had already infected banking institutions in the UK, the US, Germany, Ireland, New Zealand, Canada, Switzerland, and France with Australia been first hit by the malware. Initial infection rested on a carefully crafted social engineering campaign which would need the victim to open a PDF attachment part of a spam email campaign, then the victim would be prompted to enable macros which would bypass any security alert. In the June campaign researchers discovered 35 PayPal login URLs added to CRMs and two high profile SaaS providers.

In July, those behind TrickBot added a self-spreading worm component. The worm utilized the same SMB vulnerability as WannaCry in an effort to increase the chances of infection. In this instance, researchers at Flashpoint determined that the newly added module would scan domains for lists of servers via the NetServerEnum Windows API, and enumerates other computers via Lightweight Directory Access Protocol (LDAP). After the discovery, it appeared that the module had not been fully activated. What this instance did show researchers was that the using of worms, which was thought to have died out, could again be a powerful tool in a malware’s code. When WannaCry and NotPetya began infecting thousands of systems many other hackers took notice of what made worms such a powerful tool in the first place.
August’s iteration
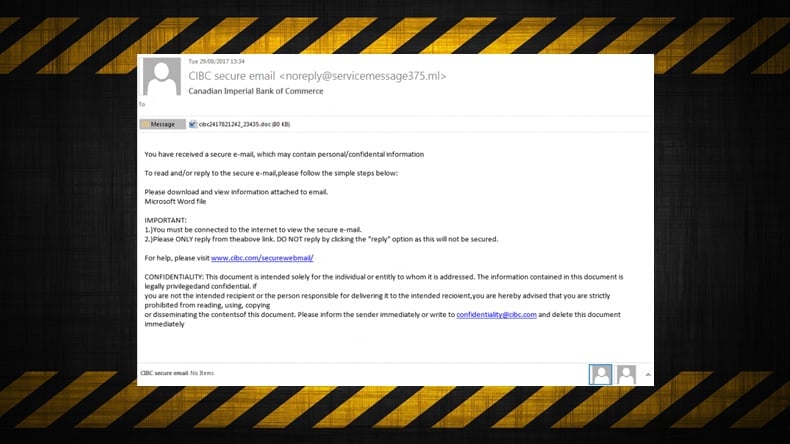
The latest update which was discovered by researchers at Forcepoint at the end of August. This campaign used a fake Canadian Imperial Bank of Commerce (CIBC) email as part of the phishing campaign. Like with the June campaign the fake spam email was part of an intricate and well thought out social engineering campaign. Within the attachment, a macros downloader was cleverly disguised which would ultimately download and execute TrickBot. At the time that Forcepoint published its findings, the company had already captured 8,600 spam emails the UK, Canada, and France as the top three targets, although the majority of recipients have the “.com” top-level domain (TLD).
Once Forcepoint decrypted the files which contained the list of targets all appeared as one would expect the target list to read based on previous TrickBot campaigns. However, one exception was found, Coinbase had been added to the list. By targeting Coinbase it means that those seeking to deploy TrickBot can now target non-traditional currencies as well non-traditional banking services. As with the June PayPal campaign TrickBot would trick victims into giving over their credentials by using fake login pages.
The best prevention of infection in this instance would not be to open any suspicious emails and not to enable macros on Word files.
Targeting Crypto-currencies is becoming increasingly popular
While it was thought that banking Trojans, like worms, were becoming increasingly unpopular given the rise in popularity in ransomware use, Trojans like TrickBot and Dridex were still actively being developed. While TrickBot used a carefully crafted social engineering campaign designed primarily to steal credentials, variants of Dridex took a different route. In the instance of Dridex, the update discovered in 2016 would dump data taken from installed Bitcoin wallet apps. Despite the slowdown in use of Dridex, this new feature was worrying. Dridex had a host of in built features that were created to avoid detection and analysis.
The September 2016 variant included to distinct lists for targeting software installed on the victim's system. The lists included ways to target back-end payment and point-of-sale software, online banking software, and a recently added list of crypto-currency wallet managers. Dridex also has keylogging capabilities assisting in stealing victims crypto-currency wallet credentials.
Often banks advertise many of their services safe and secure. This tag line is been used by emerging crypto-currency wallet providers such as Coinbase. It seems as advertising something as safe and secure is an open invitation to hackers to prove otherwise. Whether through a clever social engineering campaign or malware designed to dump data both TrickBot and Dridex are proving that industries who provide safe and secure banking may not be as safe as originally imagined or advertised. With the creators of TrickBot and Dridex showing that they are not run of the mill amateurs who have a fair amount of expertise, one can expect that their respective malware shall evolve rather than die out. Researchers believe Dridex, in particular, will become harder to detect and analyze as this is a recurring feature that continually improves. This can also be seen as a warning to newer technologies and crypto-currencies that security should always be a major concern.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion