The Dawn of DoubleLocker
Researchers at Slovakia based security firm ESET have discovered a new ransomware variant that targets Android users. The researchers believe this to be the first instance on ransomware which abuses Android Accessibility. A feature that provides users alternative ways to interact with their smartphone devices, and mainly abused in the past by Android banking Trojans to steal banking credentials. Discovered by ESET products as Android/DoubleLocker.A, this ransomware strain is based on the foundations of a particular banking Trojan, known for misusing accessibility services of the Android operating system.
Lukáš Štefanko, the ESET malware researcher who discovered DoubleLocker believes that based on the ransomware’s banking Trojan roots DoubleLocker has the possibility of being converted into a ransombanker malware. This would be a two-stage malware that first tries to wipe your bank or PayPal account and subsequently locks your device and data to request a ransom. While this is currently speculation, ESET researchers have seen similar malware in the wild already dating back to May of this year.
DoubleLocker encrypts data and changes PIN
DoubleLocker is a particularly nasty piece of ransomware, the modern favorite malware of cybercriminals everywhere, as it not only encrypts data but also changes the device's PIN. This combination of both encryption and changing the device's PIN has not been previously seen in the Android ecosystem.
DoubleLocker is distributed in the same way its banking parent does, that being through fake Adobe Flash Player downloads via compromised websites. Once launched, the app requests activation of the malware’s accessibility service, named “Google Play Service”. After the malware obtains the accessibility permissions, it uses them to activate device administrator rights and set itself as the default Home application, in both cases without the user’s consent. By setting itself as the default home app the malware increases its persistence as whenever the user clicks on the home button, the ransomware gets activated and the device gets locked again. This problem is further worsened thanks to it using the accessibility service, making it very difficult for the user to know whether they have launched the malware or not.
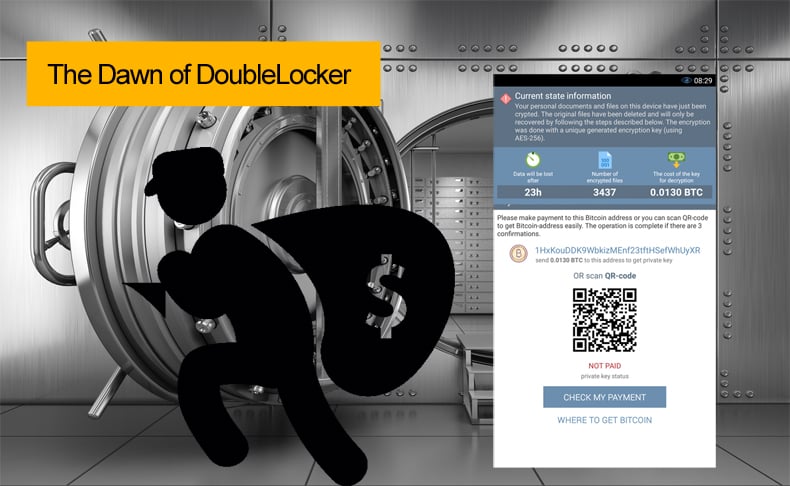
Once DoubleLocker is executed, as previously mentioned, it changes the device’s PIN, effectively blocking the victim from using it. This new PIN is randomly determined and attackers do not need to have a code stored or sent anywhere. This makes it impossible for the user or a security expert to recover it. Once the ransom is paid the attacker can remotely reset the PIN and unlock the device.
The second stage occurs when the user’s data is encrypted. DoubleLocker encrypts all files from the device’s primary storage directory and uses the AES encryption algorithm, appending the extension “.cryeye”. This extension could be inspired by a ransomware caller WannaCry which targeted Windows computers this year. The encryption is implemented thoroughly meaning the only way to gain access to the data would be to pay the ransom and receive the encryption key.
As it stands the ransom has been set to 0.0130 BTC (which is 72.95 USD at the time of writing) and the victim has 24 hours to pay. In what some may see as an act of kindness but in reality may be a way to insist on the ransom being paid the DoubleLocker malware does not delete the data if the ransom is not paid in the 24 hours limit, it rather remains encrypted.
How to remove DoubleLocker
Štefanko explained that if your device already has a quality antivirus solution installed on it your device will be safe from a DoubleLocker infection. In an effort to circumnavigate this the cybercriminals advise falsely that the user should disable their antivirus to prevent unwanted removal of the “software”. However, if you do find that your device has been infected the only way to remove DoubleLocker is via a factory reset.
If your device is rooted, however, there is a method to get past the PIN lock without a factory reset. For the method to work, the device needed to be in the debugging mode before the ransomware got activated. In order to do this, the user can connect to the device by ADB and remove the system file where the PIN is stored by Android. This will unlock the screen and allow the user to access their device. In safe mode, the user can deactivate device administrator rights for the malware and uninstall it. In some cases, a device reboot is needed. The bad news, however, is that the data encrypted cannot be recovered.
DoubleLocker’s older brother
As was mentioned above DoubleLocker uses as its foundation Android.BankBot.211.origin, a banking Trojan distributed in exactly the same way and abuses the Accessibility Service. After a successful infection, the Trojan connects to its command and control service, registers the mobile device there, and awaits further commands. The Trojan can execute multiple actions including tracking all incoming SMS and sends them to cybercriminals. It not only performs monitoring functions but can receive special commands from the attacker designed to steal login credentials for banking associated apps. It does this by displaying fake login forms for banks. Initially, the attackers sought to target users who had Turkish banks but later was expanded to include residents of other countries, including Germany, Australia, Poland, France, the United Kingdom, and the USA. In July shortly after the banking Trojan’s discovery, it was found to contain more than 50 applications designed to operate with payment systems, remote banking services (RBS), and other software.
Flash Player’s troubling past
Adobe’s Flash Player was critically in creating interactive websites during the 90s and early 2000s but it has continually be used by cybercriminals in spreading and deploying numerous different malware types over the years. With the advent of HTML 5, which is faster and more secure, Flash Player has become increasingly irrelevant in the mobile ecosystem. This has not stopper cybercriminals from abusing the product as it seems to manifest endless security exploits.
In order to help prevent DoubleLocker and Android.BankBot.211.origin infections users are advised not to download Flash from SMS and Email links sent to users and only download apps from trusted sources, like Google Play Store, and stick to verified developers.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion