Cobalt Quick to Exploit Windows Vulnerability
Hacking group Cobalt, who has developed a reputation for attacking banks, have been quick to exploit a Windows vulnerability that recently surfaced. Microsoft has patched the vulnerability found in Microsoft Office and it is strongly advised that all patches are downloaded as soon as possible. The vulnerability was discovered by the Embedi research team which affects the Microsoft Equation Editor (EQNEDT32.EXE), one of the executables that are installed on users' computers with the Office suite. This tool was designed to allow users to embed mathematical equations inside Office documents as dynamic OLE objects.
One of the major threats posed by the vulnerability, CVE-2017-11882, is that it can be exploited to run malicious code without user interaction and affects all Windows versions over the past 17 years. Having such a backdoor in your hacking arsenal is something hackers and criminal organizations dream of. Cobalt, believed to be behind an attack that targeted Russian speaking business earlier this year, has jumped on the opportunity to exploit the vulnerability detailed above.
Cobalt spreading malicious RTF documents
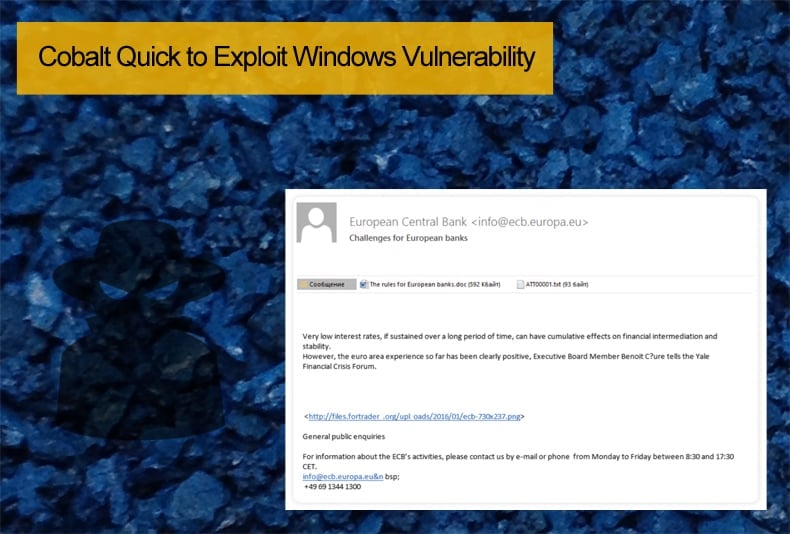
Reversing Labs, a UK based cybersecurity firm, has been tracking the groups most recent activity. They have seen an increase in the group spreading RTF documents laced with exploits that take advantage of CVE-2017-11882. These compromised documents are been sent to high-value targets such as banks and financial institutions. Reversing Labs have witnessed the group sending emails laced with the compromised RTF files. The infection chain seen by researchers appears to be long and complex but it ultimately ends with a download of a malicious DLL file.
Researchers at TrendMicro, have also been following this latest campaign and the group in general. While the methods employed and the campaign's targets suggest Cobalt is behind the campaign, it appears they have changed track slightly. Despite using the above-mentioned vulnerability, their latest spear phishing campaign differs to previous campaigns. Before the group would target the end users of the banks, this campaign targets the banks themselves. While they previously posed as sales and billing departments of legitimate companies, they’re now masquerading as the customers of their targets (banks), a state arbitration court, and ironically, an anti-fraud and online security company notifying the would-be victim that his “internet resource” has been blocked. Previously the group was using the vulnerability CVE-2017-8759 which was patched in September.
Cobalt’s infamous past
Researchers have been tracking the group since 2016, and one of their key operating methods appears to be using Microsoft vulnerabilities and weaponizing them for their campaign. Initially, the group began attacking ATMs across Europe. Then they moved to target the Americas and Russian banks, using the ex-Soviet space as a testing ground for new attacks, before it moved to more wealthy targets elsewhere. The group got its name from the malware family Cobalt Strike which is a multifunctional penetration testing tool similar to Metasploit. The group abused some of the components of the penetration testing tool to perpetrate ATM cyberheists and target financial institutions across Europe, and interestingly, Russia.
Often hacking groups will ignore targeting Russian institutions or interests in an attempt to avoid law enforcement. Cobalt rather uses Russia as its testing ground to test their malware variants. If these are successful in Russia they are then used in global campaigns. While the group may vary and change its attack methods it almost exclusively uses social engineered spear-phishing campaigns. Often the attachments contain a document file, which downloads a dropper from a remote server or contains the dropper in a password-protected archive. Small in size, a dropper is used to download and run other malicious software. A lot of time is spent crafting the emails so as to look legitimate and gain the user’s trust. In order to do this, it appears the group gets information stored on the servers and in the databases of the compromised partner organization. That information is then used in conjunction access gained to employee accounts on workstations and mail servers, giving phishing messages a high degree of trust and plausibility among potential recipients.
Banks globally have been quick to adapt spam filters to protect its employees from falling foul of such an intricately crafted campaign. Cobalt, on the other hand, have been quick to try and prevent such filters from stopping their spam emails. The group was finding that their emails containing forged sender information were been successfully blocked. The group altered their methods to now using Supply Chain Attacks to leverage the infrastructure and accounts of actual employees at one company, in order to forge convincing emails targeting a different partner organization. Other than what has been listed the group is also known to use the following methods:
- Active attacks on bank partners in order to use partner infrastructure for sending phishing messages to banks.
- Phishing messages disguised as mailings from financial regulators.
- Various types of malicious attachments: document with an exploit (.doc, .xls, .rtf), archive with an executable dropper file (.scr, .exe), and archive with LNK file (.lnk).
- Among the first groups to get access to the latest version of the Microsoft Word Intruder 8 exploit builder, which made it possible to create documents exploiting vulnerability CVE-2017-0199.
- Poorly protected public sites are used to upload files and then download them to victim computers.
- Phishing messages are sent both to corporate addresses and personal addresses of employees.
More groups will adopt similar methods
The entry point for would-be criminals to perpetrate cybercrime keeps dropping annually. Before hackers would need to hunt for zero-day vulnerabilities and expensive tools to perform attacks now all they require are basic programming skills, commercially available software, and instructions posted on the Internet. When this is combined with sophisticated groups looking to steal millions of dollars the effects can be felt by the average consumer. The costs associated with cybercrime result in increased fees or costs which ultimately the consumer pays for.
Information as to the extent of losses caused by the Cobalt group in 2017 is not yet available. Given the groups global reach multimillion-dollar losses by banks are a real possibility. With that in mind, users should apply Windows updates KB2553204, KB3162047, KB4011276, and KB4011262, included in the November 2017 Patch Tuesday, to guard against CVE-2017-11882 exploitation.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion