Iran and Russia Hit by Hacktivist Group
Late on April 7, reports began emerging that a significant number of Cisco switches located in Iran and Russia were being hijacked. The attack appears to have been done by a hacktivist group calling themselves “JHT” and may be in response to and in protest to election-related hacking. Cisco switches are network switches sold by the company. A network switch connects computers, printers, phones, cameras, lights, and servers in an office building or campus for example. A switch serves as a controller, enabling networked devices to talk to each other efficiently as opposed to a router which allows for connection to a particular network. The attack targeted internet service providers, data centers, and in turn some websites within Iran and Russia. It is yet unclear on how exactly the attack was carried out but it is believed the attacks involve a recently disclosed vulnerability (CVE-2018-0171).
JHT
Tech news website Motherboard managed to make contact with the hacker group in order to find out hopefully why they attacked infrastructure in both Iran and Russia. The group told Motherboard that they wanted to send a message to government-backed hackers targeting “the United States and other countries.” They claim to have only caused damage to devices in Iran and Russia, while allegedly patching most devices found in countries such as the U.S. and U.K.
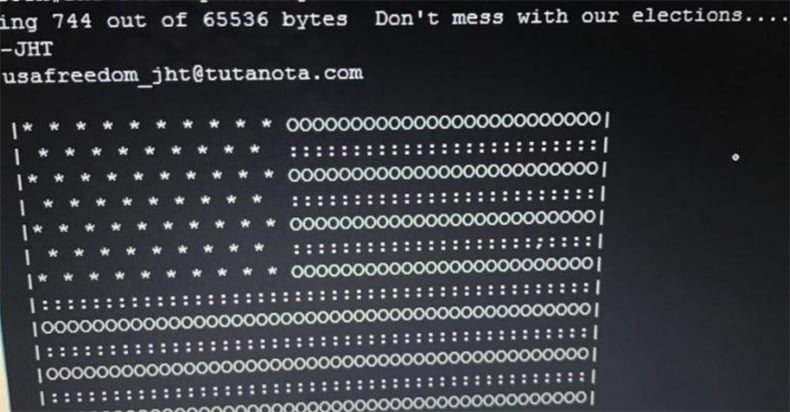
In order to hijack the switches, the group changed the compromised switches’ IOS (Interwork Operating System) image. Cisco IOS is software used on most Cisco Systems routers and current Cisco network switches that allows for the routing, switching, internetworking and telecommunications functions integrated through an operating system. Further, the hackers changed the switches configuration to display a U.S. flag using ASCII art and the message “Don’t mess with our elections…”

Was CVE-2018-0171 exploited or not?
Iran’s Communication and Information Technology Ministry confirmed that the attack had impacted roughly 3,500 switches in the country, but said a vast majority were quickly restored. While Kaspersky Labs reported that the attack appeared to mostly target the “Russian-speaking segment of the Internet.” The report went further to state how the attack was potentially carried out. The Kaspersky report published before the Motherboard article so within the security firm’s report they refer to the attackers as “an unknown threat actor”. Researchers at Kaspersky believe that the hackers exploited a vulnerability in a piece of software called Cisco Smart Install Client, which allows them to run arbitrary code on the vulnerable switches. The attackers then proceeded to change the ISO image in the manner stated above.
Kaspersky researchers believe they discovered a bot that is searching for vulnerable Cisco switches via the IoT search engine Shodan and exploiting the vulnerability in them. Once it finds a vulnerable switch, it exploits the Smart Install Client, rewrites the configuration, and thus takes another segment of the Internet down. As to the scale of the attack, little is yet known. According to Cisco Talos, there are more than 168,000 devices found on Shodan that have this vulnerability.
While there are some reports that the attack involves a recently patched remote code execution vulnerability in Cisco’s IOS operating system (CVE-2018-0171), that might not necessarily be the case. CVE-2018-0171 could allow an unauthenticated attacker can send specially crafted Smart Install messages to an affected device on TCP port 4786 and cause it to enter a denial-of-service (DoS) condition or execute arbitrary code. However, others believe, like the researchers at Kaspersky, that the Smart Install Client is the chosen attack vector. The Cisco Smart Install Client is a legacy utility, a program that is obsolete, allows no-touch installation of new Cisco switches. Roughly one year ago, the company warned customers about the misuse of the Smart Install protocol following a spike in Internet scans attempting to detect unprotected devices that had this feature enabled.
Cisco then issued another warning recently concerning the disclosure of CVE-2018-0171. The warning stated that CVE-2018-0171 increases the risk of attacks, but the networking giant said it had not actually seen any attempts to exploit this vulnerability in the wild. Cisco’s advisory for this flaw still says there is no evidence of malicious exploitation. To further prove that the recently disclosed vulnerability may not be the one used by the hackers, Chines security firm Qihoo 360 says their shows that the attacks have “nothing to do with CVE-2018-0171” and instead rely on a publicly available Smart Install exploitation tool released several months ago.
Is Hacktivism the answer?
If the group calling themselves JHT are indeed hacktivists, determining the truth of this in the cyber age is difficult at best, are there current actions effective? What are their aims and goals? Despite the statements made to Motherboard, these are murky at best. They oppose government-backed hacking groups in Iran and Russia but what about the numerous others around the globe that may even be supported by the US or UK? Due to the anonymous and untraceable nature of what hacktivists claim to do it becomes much harder for large numbers of the public to agree with their actions. All too often such activities regardless of the ethical point they wish to make are regarded as cowardly.
Often when it comes to protest that involves civil disobedience it is the protester’s strength of purpose that wins over the like-minded. They need to be seen and heard. Unfortunately, hacktivism is to easily forgotten by the masses as they have nothing to which they can relate. In the above article, much of the world’s attention is given to how it was done rather than why it was done. As there is no human face behind the actions it is too easy to discount such actions as a minor annoyance rather than politically motivated action. There are numerous methods of protest that are effective and given the right circumstances they can topple empires and regimes. As to whether a few individuals can something similar and retain the approval of large sections of the populace is doubtful.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion