Hackers Reveal Fully Operational Zero-Day Vulnerabilities
There is very little that can be considered more frustrating than realizing all your hard work has been made useless because of a silly mistake. This is probably what a group of hackers must be feeling at the moment. In this instance, the hackers appeared to have accidentally exposed two fully-working zero-days when they uploaded a weaponized PDF file to a public malware scanning engine. Unfortunately for the hackers, but fortunately for almost everyone else, security researchers at ESET discovered the potentially damaging zero-days and reported them. The first vulnerability affected Adobe’s PDF viewer and has been assigned the following Common Vulnerability and Exposure (CVE) number CVE-2018-4990 and has been patched. The second vulnerability, CVE-2018-8120, which if exploited targeted the Win32k component of Windows and was also recently patched.
The Planned Exploit Chain
In a report published by Anton Cherepanov, the ESET researcher who spotted the zero-days amongst the numerous other pieces of malware, the exploit chain the hackers were going to use was revealed. By using the two above mentioned the hackers created what is commonly called an “exploit chain”. An exploit chain, or sometimes referred to as chained exploits, can simply be seen as when hackers use a number of exploits that are chained together to form an attack. According to Cherepanov, the Adobe zero-day is intended to provide the ability to run custom code inside Adobe Acrobat/Reader, while the Windows zero-day allows attackers to escape Adobe's sandbox protection and execute additional code on the underlying OS.
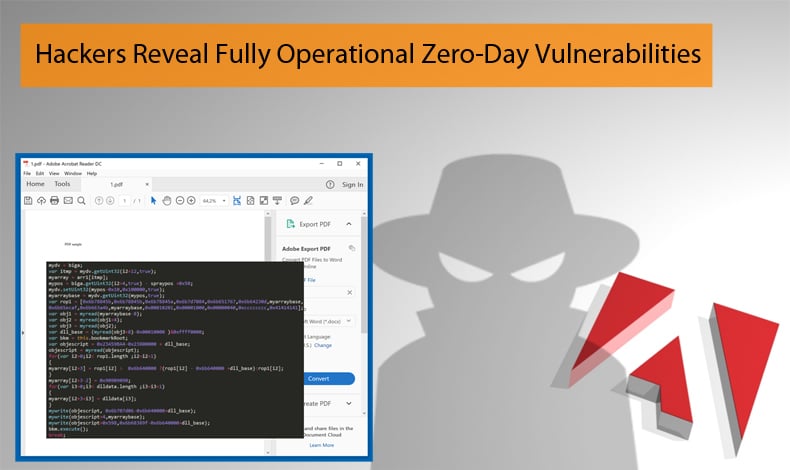
The malicious PDF file is central to the entire exploit chain. The PDF embeds JavaScript code that controls the whole exploitation process. This occurs as soon as the PDF is opened by the potential victim. Fortunately, the sample contained no final payload leading researchers to believe that the hackers were found out while in the process of fine-tuning the malware. Based on ESET’s report the exploit chain can be summarised as follows:
- The user receives and opens the boobytrapped PDF file
- Malicious JavaScript code executes when the user opens PDF
- JavaScript code manipulates a button object
- Button object, consisting of a specially-crafted JPEG2000 image, triggers a double-free vulnerability in Adobe Acrobat/Reader
- JavaScript code uses heap-spray techniques to obtain read and write memory access
- JavaScript code then attacks Adobe Reader's JavaScript engine
- The attacker uses the engine's native assembly instructions to execute its own native shellcode
- Shellcode initializes a PE file embedded in the PDF
- The part of the Microsoft Win32k zero-day kicks and lets the attacker elevate the privilege of the PE file to run, which is run in kernel mode, breaking out of the Adobe Acrobat/Reader sandbox to system-level access.
While it appears that a crisis has been averted due to a possible mistake on the side of the hackers, the exploit chain can still be regarded as a professional piece of offensive hacking. The one mistake the hackers made was to upload the malware to a known virus scanning engine in the hopes of testing its detection level. This alerted the researchers at ESET, who quickly discovered that the malware planned to exploit two previously unknown exploits. Cherepanov discovered not one but two samples, which can be viewed here and here, in March of this year. Both Adobe and Microsoft were quick to patch the vulnerabilities, with Microsoft releasing the patch as part of patch Tuesday.
Another Zero-Day Patched
As part of the latest patch Tuesday, which happened on May, 15, not one but two zero-day events were patched. The first being the one discussed above affecting the Win32k component, the second being one that affects Internet Explorer given the designation CVE-2018-8174. Like with the Win32k the one affecting Internet Explorer has also be seen in the wild. According to researchers at Qihoo 360's Core security unit, an advanced persistent threat (APT) group is using the IE vulnerability on a global scale in a cyber-espionage campaign. The campaign includes sending the malware to select targets in the form of a malicious Office document that is loaded with what it calls a "double-kill" vulnerability.
According to the firm, the vulnerability affects the latest versions of IE and other applications that use the browser. In order to be infected the victim is required to open the Office document, which launches a malicious webpage in the background to deliver malware from a remote server. The vulnerability was duly reported to Microsoft by the security firm. When pressed for comment when the story broke in late April Microsoft responded with:
“Windows has a customer commitment to investigate reported security issues, and proactively update impacted devices as soon as possible. We recommend customers use Windows 10 and the Microsoft Edge browser for the best protection. Our standard policy is to provide remediation via our current Update Tuesday schedule.”
Fortunately, the tech giant took the threat seriously and did indeed provide “remediation via our current Update Tuesday schedule.”
Why all the fuss surrounding Zero Day Events?
The news of a Zero Day is often met with fear and trepidation by some and head scratching by others. By definition, a zero-day vulnerability, also known as a computer zero-day, is a flaw in the software, hardware or firmware that is unknown to the party or parties responsible for patching or otherwise fixing the flaw. As these vulnerabilities are not, and by definition, cannot be known in advance they pose a serious threat to users. They are difficult to detect and cannot be stopped by an anti-virus package till it is updated to be able to detect exploitation. Often the only way to prevent such attacks is by the software company in question patching the vulnerability before any real damage can occur. Unfortunately, the two Microsoft vulnerabilities covered above were indeed seen been exploited in the wild. Such occurrences should serve as a reminder as to the importance of keeping software and operating systems up to date even if it might be a minor inconvenience.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion