$10 to access Machine at an International Airport
Security firm McAfee recently discovered a hacker offering access to a machine at an international airport for the low price of only 10 USD. This was of course discovered on the Dark Web, that cesspit of immoral behavior. Access to the machine would be granted via Remote Desktop Protocol (RDP) which is fast becoming a favored method the popular delivery method for many malware types. RDP is a proprietary Microsoft protocol that provides access to remote machines through a graphical interface. It was initially designed for administration purposes, but cybercriminals are increasingly using it as part of their arsenal of attack tools. Cybercriminals are known to subvert legitimate tools for their own purposes and their use of RDP is no different.
McAfee’s Discovery
On July 11, 2018 researchers at the security firm published an article detailing the discovery. What has been revealed that it’s actually incredibly easy for cybercriminals to gain RDP access to high-value networks. All that is needed is to spend a relatively small amount of cash and work off the scans of an accessible system done by someone more enterprising. The researchers looked into several RDP shops. The shops were offering anywhere between 15 to 40,000 RDP connections and all of them for sale. The largest of these shops is the Ultimate Anonymity Service (UAS), a Russian business, followed by Blackpass, Flyded, and xDedic.
Many of those above-mentioned shops operate with a similar business model. RDP access is offered over a wide range of Windows operating systems, be it Windows XP to Windows 10 but by far the most popular offerings are for Windows 2008 and 2012 Server. Prices range from 3 USD, for a simple configuration, to 19 USD for a high-bandwidth system with admin rights. For more discerning cybercriminals access to systems running Windows Embedded Standard (or Windows IOT) is also available. This can include hundreds of similar configurations associated with municipalities, housing associations, and healthcare institutions. Multiple government systems worldwide were also being sold.
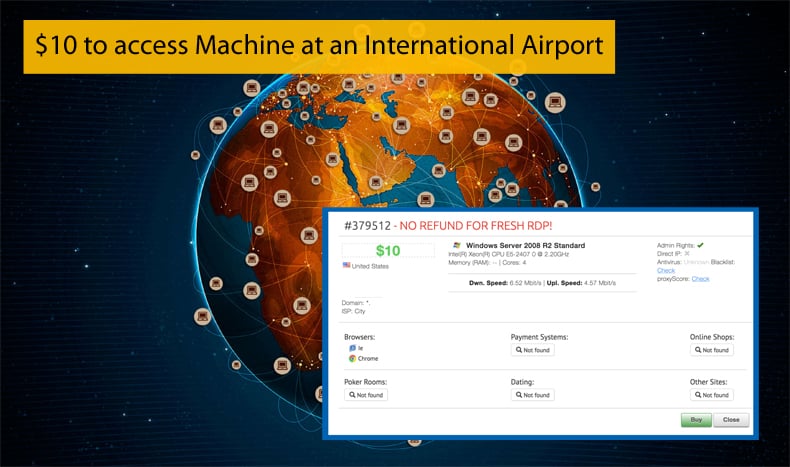
On the UAS shop, McAfee discovered a newly added Windows Server 2008 R2 Standard machine. This machine was later revealed to belong to a major international airport within the US. It was further revealed that the system had three user accounts available, one is an administrator account, while the other two were associated with a company specializing in airport security and building automation while the other a contractor specializing in camera surveillance and video analytics for airports.
xDedic not just a store for RDP Access
An investigation into xDedic was conducted in 2016 by Kaspersky Labs. It was shown at the time of the investigation that the Dark Web marketplace had more than 70,000 items offered for sale, including compromised servers on government networks, corporate servers, web servers, or databases. The marketplace could also boast 416 unique sellers had hacked servers in 173 affected countries. The marketplace came into being in 2014 offering only one server, by 2016 the number of servers offered had grown to 70,624 servers. Not only does the marketplace offer servers but it also provides a wealth of information on the servers which includes information pertaining price, location, speed, anti-virus installed, and more.
Since xDedic opened its digital doors it became a dream for hackers. For relatively low prices it effectively simplified access to victims. This would be appealing to low-level hackers as well as advanced threat actors. Researchers did notice that the hacker collective behind the marketplace did not sell anything themselves, rather they offered an environment for a network of affiliates to sell their wares as it were. In order to offer the best service to potential buyers, the creators offer live technical support available for the forum. Kaspersky researchers discovered that accounting, tax reporting, and point-of-sale (PoS) software on these servers are of high interest, as they open up many opportunities for fraudsters.
RDP Distribution becoming more popular than email
Researchers at Webroot noticed that in 2017 RDP distribution is becoming an ever-increasing popular distribution vector for ransomware in particular. A chart published by Webroot showed that RDP distribution is more widespread than email when it comes to ransomware. It was seen that 66% of detections were as a result of RDP versus 33% email. Historically, ransomware has been distributed via other methods as well, including exploit kits and mal-advertising, but the traffic associated with these vectors doesn’t appear to be as popular. Recent trends in ransomware show that those vectors will become far less popular.
With the lessons learned from operations on the Dark Web like the infamous Silk Road, a marketplace for illicit drugs, cybercriminals are adapting lessons learned. Marketplaces such as UAS and xDedic will continue to expand what services affiliates can offer. Researchers at McAfee noticed that
“In addition to selling RDP, some of these shops offer a lively trade in social security numbers, credit card data, and logins to online shops. […] BlackPass offered the widest variety of products. The most prolific of these brokers provide one-stop access to all the tools used to commit fraud: RDP access into computers, social security numbers and other integral data to set up loans or open bank accounts,”
Given the recent rise in popularity in malware associated cryptocurrencies and exchanges, it might only be a matter of time when such malware becomes the most bought and sold commodity on such marketplaces. To the best knowledge of the author, no coin miners of clipboard hijackers have been distributed via RDP. For the time being, it would appear that ransomware is been distributed and access to targeted systems granted via the RDP tool. Such tools are incredibly useful to administrators and can make their daily tasks much easier, however, these incidents should serve as a warning that they are a liability if not properly secured.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion