Ransomware Scam or Not, don’t Pay
The world is often a funny place at the best of times. The recent Twitter rant, that did not involve President Trump for a change but rather this platform and service it provides, proves this planet is a tad absurd. Notwithstanding the Twitter rant by a malware developer stating that this platform falsely accused the developer of being a scammer, the incident does raise a very important question. That being, should you ever pay the ransom if you’ve become a victim of ransomware?
Before that question is answered the details of the aforementioned rant should be discussed. King Ouroboros, the developer or group of developers behind the King Ouroboros Ransomware, went to Twitter in an attempt to right a much perceived wrong. In the Twitter post, King Ouroboros attempts to set the record straight by stating that individual or group are not scammers. This appears to be in response to a ransomware removal guide published on this platform. The intention of the published piece is to assist those infected with the ransomware by removing it from the infected system. In the guide victims are advised, “Research shows that ransomware developers are likely to ignore victims, once payments are submitted. Therefore, paying typically gives no positive result and users are scammed.”
It is this the group took obvious offense to. This is sound advice as will be shown later. In the Twitter rant, the group goes on to state that, “From the beginning, we’ve already helped loads of people solving any of their issues regarding the decryption of their files, as well as spending the time to code a standalone decryption tool for those who have deleted the original one. We do also provide discounts to those who are able to prove any kind of financial problems they may have. This is all we’re going to say, to believe it or not is up to you, prove us wrong and we’ll shut down the entire operation.”
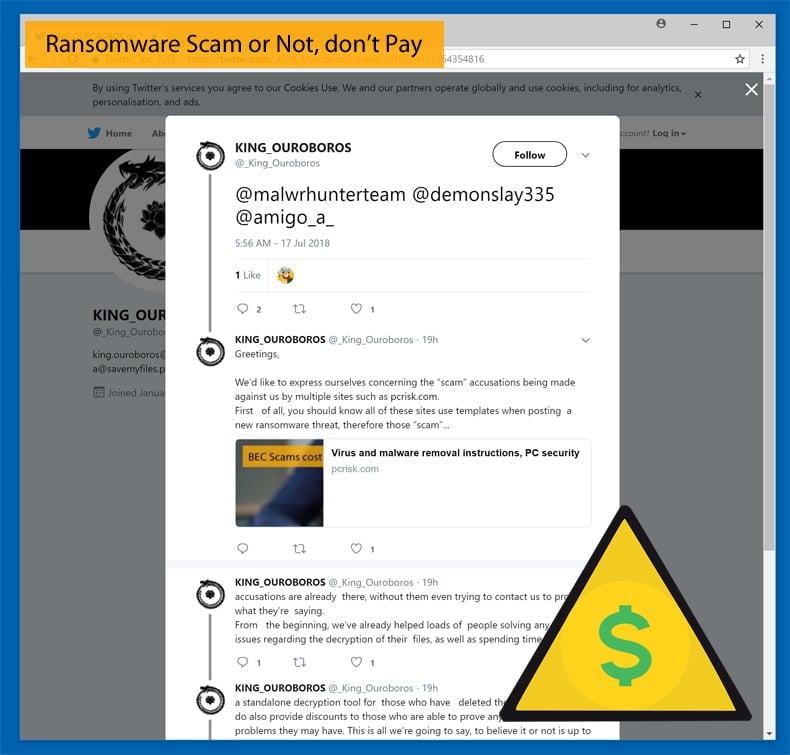
One vital bit of information left out of their attempted rebuttal is that it is the group that purposefully encrypts user’s data without their consent. This in itself is illegal and more importantly immoral. The decryption is done for financial gain rather than out of the goodness of their hearts, despite them providing “discounts” to those who cannot afford the initial ransom. Tagged to the rant were well-known malware researchers including MalwareHunterTeam, Michael Gillespie, and Amigo-A. This garnered the attention of Lawrence Abrams at Bleeping Computer who summarised the whole saga as such, “After reading this, I could only think WTH!?!?! Here is a ransomware developer screwing people over and now we are supposed to feel bad that some site called his software a scam?”
Why should you not pay?
Despite those behind King Ouroboros being such “nice guys” by offering discounts and assuring the public that they are not a scam, scam or not there are some very important reasons why you should not pay a ransom not matter how small. To that effect, a good article on the subject was published by SolarWinds, a managed service provider for companies. The first reason they give for not paying the ransom is that it is unreliable, meaning that once the payment has been made there is no guarantee that the encrypted files will be decrypted. It is important to remember that you are not dealing with legitimate businesses with a code of ethics. Rather you are dealing with individuals who illegally encrypted your data so you cannot access it and who are now extorting money from you. No matter how nice they may be they and, dare I say it, their scam is not to be trusted to fulfill their end of the bargain.
In another article research by Citrix was quoted that revealed that in a study 200 companies in the UK were infected with fake ransomware 63% of them paid. Fake ransomware can be seen ransomware that can encrypt data but the attackers have no way of decrypting the data. Those companies would have paid the ransom and then still pay more on top of that for data to be recovered. Another article published by CSO Online comes to the same conclusion while asking numerous security experts on whether payment should be made or not.
Much of that article dealt with attackers targeting hospitals with ransomware. The hope here of the attacker is that the hospital will pay the ransom as patients’ lives may be at stake and the information of patients is incredibly sensitive. That an individual or group of individuals are willing to attack institutions were lives may be at risk in order to extort a quick payday says much. This is not to say those behind the King Ouroboros have actively targeted hospitals but others have and users do not know who else has been targeted for possible infection.
It is also important to remember that even if you have paid the ransom and the files have indeed been decrypted there is no guarantee that they are out of your system or network. If you have paid once those attacking you may be emboldened to attack again. A lot of malware is persistent and incredibly hard to remove or the backdoor they used to break into your system may still be vulnerable. This potentially leaves victims open to further attacks by the same individual or group.
Lastly, ransoms paid are the proceeds of crime. In a legitimate business, proceeds go to paying expenses, salaries, and utilities. If the business turns a profit that could be used for expansion or numerous other things. The same cannot be said for the proceeds of crime. They are not taxed and portions of what is earned go back into creating new malware in order to make more money illegally. Some may find the rant funny and entertaining, others may be stunned or perplexed. It may also indicate that those behind PCRisk are providing a service which truly helps victims of ransomware rather than pretending to of assistance.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion