Iceland hit by Biggest Cyber Attack on Record
The small island nation, known for its small population and giant-slaying football team, hardly ever makes the headlines in cybersecurity publications. That was until October 12, when cybersecurity news sites began publishing articles detailing how Iceland had just experienced its biggest attack yet. This is a stark contrast to reports from 2017 which stated that Iceland experienced no reported cases of the WannaCry attack in May of that year.
Fast forward to the present day where a phishing campaign took Iceland by surprise, sending out malicious emails to thousands of individuals, in an attempt to fool them into installing a powerful remote access tool. For many nations, a cyber attack affecting thousands can be seen a mere trifle. However, when you consider that the population of Iceland is approximately 350,000 people, thousands represent a significant percentage of the population.
Phishing Tactics
The attack appears to have started on the evening of Saturday, October 6, with messages that impersonated the Icelandic police. The emails asked the recipients to come in for questioning and warned them that non-compliance resulted in issuing an arrest warrant. That in itself would not be enough for those targeted to install malware on their PC. The email included a link which leads to a fake version of the Icelandic Police’s webpage. In an attempt to make the link appear as legitimate as possible the attacker registered a domain which would resemble the original, in this case, “logreglan.is.”
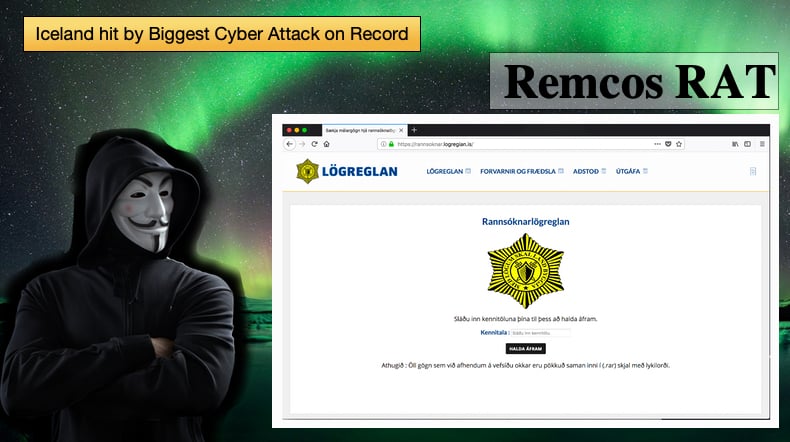
A team of security researchers based at Cyren have been working with the police during the investigation. In a blog article published by the researchers they explained that, “…the attacker registered a domain name of www.logregian.is--using a lower case ‘i' (which on first glance, may appear like a lower case “L” or “l”),” This tactic is often called an IDN homograph trick.
Such an attack involves the malicious exploitation of the internationalized domain name (IDN) register and exploiting the fact that many different characters look alike. The Unicode standard which was employed to help ensure consistent coding, has a number of similar looking characters. For example, characters such as Greek Ο, Latin O, and Cyrillic О were not assigned the same code but still look incredibly similar. Attackers use this often in an attempt to get users to click malicious links. In the above case the link in the message used “switched the lower case “i” for a capital “i” or “I”, so the “i” actually looks like a small “L”—making it indistinguishable from “logreglan” to almost any web user.”
Remcos’ RAT exploited
According to the researchers at Cyren the tool used by the attacker is Remcos, or Remote Control & Surveillance Software, which is a powerful tool available commercially as a legitimate solution for access to remote computers. Such tools are commonly referred to as remote access tools, or simply just RAT, and used to gain access and control of remote computers. While legitimate many threat actors use the tool for malicious and illegitimate reasons. In this case, the tool is used to collect sensitive information, such as passwords and usernames. This is done by also leveraging keylogging malware that record keystrokes which are then uploaded to the attacker's command and control server.
While Remcos is a powerful and useful tool, such malicious use is by no means new. Prior to this in August 2018, Cisco Talos reported another instance of abuse. In this instance, Cisco listed a number of instances where the software was maliciously used. These included campaigns targeting defense contractors, international news agencies, Diesel equipment manufacturers, and service providers in the energy and maritime industry. In one campaign which was seen in Turkey Remcos was delivered through carefully planned spear-phishing attacks that purported to be an official communication from the Turkish Revenue Administration, responsible for taxation in the country. Cisco Talos has called out the creators of Remcos for not doing enough to prevent its malicious use. This created a war of words between Cisco Talos and Breaking Security, the company behind Remcos, with the latter stating that malicious use is against the terms of service.
The developer of Remcos also told Bleeping Computer that they are aware of the malicious use and have implemented a mechanism to prevent abuse. The developer said,
“Apart from blocking the customer license (preventing him to use our software), we provide help into removing the software from the compromised system. This can be done very easily from us,”
Further, the developer stated that when Remcos was used maliciously, the attacker relied on other tools, too. In the Icelandic case, security researchers believe it was a VBS script that ran at startup to ensure the execution of Remcos.
Campaign directly targeted Iceland
Researchers and Cyren discovered that the attacker’s command and control servers were located in Germany and Holland respectively. It was also seen that the link directing to the spoof website imitates almost to perfection the official website of the Icelandic police, and asks users to enter their social security number (SSN). What is odd is that the attacker could check the validity of the SSN numbers, which should not be possible for a phishing site. One theory is that the attacker has access to a previously leaked database.
Once the user enters their SSN number on the spoof site, the user receives the alleged documents in a password-protected archive, with the key provided on the webpage, which in reality is the packed RAT. The campaign is cunning and would trick even the canniest user, this indicates a level of sophistication above that of the average hacker. Once the RAT is installed it is used to steal banking info, as it checks if the victim has access to the largest banks in Iceland. The attacker is unknown but police believe that the campaign is the work of someone familiar with the Icelandic administrative system. Fortunately, the reaction of the police was swift and the domain to the landing page was taken down a day after detection.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion