New Tool Bypasses 2FA
It is the best practice to enable two-factor authentication, often simply referred to as 2FA, when one can. Beyond best practice, it is recommended by experts to enable 2FA to prevent becoming a victim of the numerous phishing campaigns that stalk the Internet on a daily basis. Two events that have recently arisen that may be the beginning of the end for 2FA, or at the very least far more secure versions of it. The first of these events being a penetration testing tool released by a Polish security researcher capable of bypassing 2FA in a phishing attack. The second being a research report released by Amnesty International which details how APT groups are able to bypass 2FA using phishing tactics. While developed by different interested parties these developments may signal a significant eroding of trust in the widely trusted 2FA protocols.
Modliska, the Polish for Mantis, is the name given to the new tool created by Piotr Duszyński which can bypass 2FA in a far easier way than previously thought possible. The tool can be best described as a reverse proxy, which acts like a type of proxy server that retrieves resources on behalf of a client from one or more servers. Importantly, these resources are returned to the client, appearing as if they originated from the proxy server itself. In practice, these proxies can be used to shield the functionality of an application from weak HTTP capabilities. In Modlishka’s case, the reverse proxy is used to modify traffic meant for login pages and phishing operations.
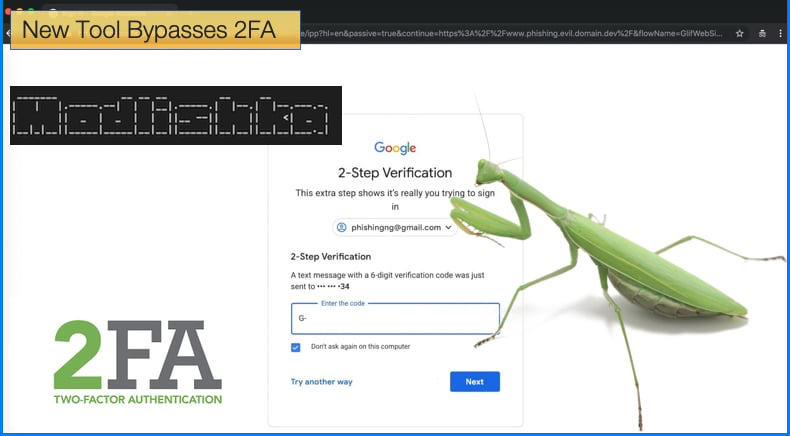
In a blog post published by Piotr Duszyński, the researcher goes into great detail on how the tool works and if more technical information is needed than provided below it is advised to read the blog. In summary, the tool is designed to sit between the secure email platform, like Gmail or ProtonMail and the victim. When the victim wishes to visit what they believe to be the secure mail website it is the reverse proxy sitting in the middle which makes the request. Then the victim receives authentic content from the legitimate site but importantly all the traffic including all the victim's interactions with the legitimate site pass through the Modlishka server. It is then recorded by the server to be used as deemed fit by the attacker.
The tool will then automatically log any password entered by the victim. Then the tool will prompt users for 2FA tokens if they have enabled 2FA. If the potential attacker is online they can then collect the tokens in real time and log into the victim's email account. A major advantage to using the tool is that unlike other phishing scams the tool is not reliant on using templates a term used by phishers to describe accurate clones of legitimate sites to trick users into handing over login information. As all the content is retrieved from the legitimate site in real time, attackers don't need to spend much time updating templates to look almost exactly like the real thing. Rather, all the potential hacker requires is a phishing domain name, to host on the Modlishka server, and a valid TLS certificate to avoid alerting users of the lack of an HTTPS connection.
Amnesty International’s Report
On December 18, 2018, Amnesty International published a report detailing how advanced state-sponsored actors have already started using phishing systems that can bypass 2FA. The tactics employed may not be as simple in practice as using the tool detailed above but shows that a potential attacker now has two options available when looking to steal passwords and other important information. The report was quick to point out that users should not abandon 2FA and use it wherever possible as requiring a secondary form of authentication prevents some scenarios in which an attacker might have obtained access to your credentials. This is a secondary form of authentication has proven more than adequate when stopping unsophisticated forms of phishing.
While it is still important to have 2FA enabled, researchers pointed out that if a victim has been tricked into providing a username and password they are also likely they may provide other information including 6-digit two-factor tokens, mobile phone numbers, or any other relevant information. How then in this instance can the attacker bypass 2FA? Essentially researchers stumbled onto servers hosting phishing sites targeting Google and Yahoo users. These servers were mistakenly exposed allowing researchers a unique insight into the attacker’s operations.
Researchers discovered a number of files showing how the attacker managed to steal and store credentials. Another file contained a version of Selenium, which is a set of tools used to test web applications. The software can be used nefariously to automate login attempts and streamlining phishing attacks. Further investigation revealed that the attack used Selenium to spawn instances of Google Chrome in order to further automate the stealing of credentials. Once the credentials had been stolen the attacker was able to perform an “account migration”, giving the attacker the ability to clone emails and contacts and send them to an account under the attacker’s control.
Is 2FA dead?
When both events are taken into consideration many might assume that 2FA is dead and we are doomed to a future of Internet insecurity. The wiser amongst us will see it as an opportunity to further increase the security protocols behind 2FA to prevent such attacks. Internet Security is a game of cat and mouse at the best of times and such events when taken seriously enough can amount to a more secure Internet experience for all. While questions will be asked as to the value of whether such information should be made public, user education will, for the most part, be a sufficient counter-argument.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion