POS Malware Seen Targeting SMBs
Waking up to a notification from your bank saying that you spent a lot of money on some online purchase from a company in a country you’ve never thought of visiting is a horrible way to wake up. Cybercriminals have a unique ability to ruin days, even those of people careful with their credit cards. You make sure when you swipe your bank cards you are present or even swipe yourself to combat card skimming fraud and protect your details. What then if the POS (point of sale) device has been compromised with malware designed to steal your credit card details unbeknownst to you and the retailer?
In research published by Flashpoint, this is a reality facing both customers and small to medium businesses (SMBs). Malware called DMSniff is actively been used to target restaurants, cinemas, and other retailers in the entertainment and hospitality industries. The malware is believed to be active since 2016 has managed to fly under the radar until now, having been uncovered with the key targets of campaigns been small and medium-sized companies which rely heavily on card transactions, such as the food, hospitality and entertainment industries. This is not the first malware researchers have seen targeting POS machines bur DMSniff includes a unique feature designed to continually send stolen details even if the command and control (C&C) server operated by the cybercriminals has been shut down.
The feature that makes DMSniff unique is how it uses a domain generation algorithm (DGA) to create command-and-control domains on the fly, helping it to resist takedowns and bypass simple blocking mechanisms. These algorithms are seen in various families of malware that are used to periodically generate a large number of domain names. These can then be used as points with their command and control servers. A large number of potential rendezvous points makes it difficult for law enforcement to effectively shut down botnets since infected computers will attempt to contact some of these domain names every day to receive updates or commands. With DMSniff the attackers using DGA enables them to evade law enforcement and the malware can still communicate with the compromised POS device. Meaning that they can still continue to transfer stolen data.
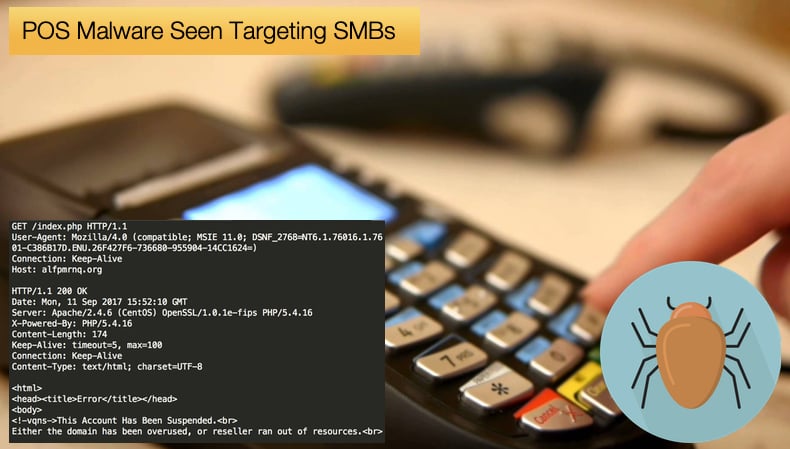
According to the researchers at Flashpoint, they have uncovered eleven separate variants of DGA be used in conjunction with DMSniff. What struck researchers is that such tactics have not been used in previously seen POS malware. This has led researchers to believe that DMSniff is been operated by a well-resourced cybercriminal gang. Such gangs adopt measures that big business would increase profit while eliminating the competition. Researchers believe that DMSniff is finding its way onto POS machines via brute force attacks on the networks such machines are connected to. These attacks intend to bypass poor passwords and by scanning for vulnerabilities which can easily be exploited if POS machines are unintentionally left exposed to the open internet. It's also possible that attackers could compromise the device by physically tampering with it.
Regardless of how it lands on the machine the malware works by scraping the credit card data from the magnetic strip when swiped. The malware incepts this information before it is encrypted and sent to the corresponding bank. Since the advent of Chip and Pin technology the use of magnetic strips in decreasing to the extent that they are rare in Europe but more common in the US. The information stolen can be sold on the Dar Web or used by the gang to make online purchases. DMSniff employs a string encoding routine to hide – and in the case of being discovered, to attempt to hide how the malware works. This appears to have worked based on how researchers do not know exactly how the malware lands on machines. String encoding techniques are often used by hackers to prevent analysis of malware with the techniques used simple but still effective.
Retail under Attack
As mentioned before this is not the first case of malware targeting POS machines. Security firm Morphisec published details on another malware targeting POS points. In an ongoing campaign hackers are using a legitimate penetration testing tool, Cobalt Strike, to attack VMWare Horizon Point-of-Sale (POS) thin clients. The tool is being used maliciously with other malware payloads to hijack systems, execute code, harvest credentials, and is also able to circumvent EDR scanning. The penetration testing tool is used to infiltrate the POS system then FrameworkPOS, a scraping malware, is deployed to scrape details from cards. All the scraped data is then compressed and sent to the attacker’s command and control server.
According to Morphisec, many of the tactics used by the attackers may indicate that this new campaign is being operated by FIN6. The group is infamously known for operating using stealth rather than sophisticated tools like in the above example. IBM researchers connected FIN6 to a POS attack campaign against retailers in the US and Europe in 2018, and the theft of millions of credit card numbers in 2016 has also been attributed to the same group. While attacks against retailers are certainly in the purview of FIN6, the researchers are not entirely confident of attribution as there are also indicators which suggest links to EmpireMonkey, another financially-motivated threat group which was recently linked to a cyber attack against the Bank of Valletta.
These discoveries are in line with what Akamai stated in their 2019 State of the Internet report which suggested that retailers have become the top target for cybercriminals utilizing credential stuffing attacks. The dumping of stolen credentials available for sale has proved incredibly lucrative for certain cybercriminals.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion