Exchange Server Vulnerabilities used to spread Ransomware
When news broke that the state-sponsored threat group Hafnium was actively exploiting four Microsoft Exchange zero-days the InfoSec community waited with bated breath to see when other groups would begin to target the same flaws. This would only take a few days till news that the fear of other threat actors exploiting the flaws arrived. This was then followed by the fear that ransomware may be dropped onto vulnerable machines accessed by attackers using the flaws. That day has seemingly arrived.
In summary, Microsoft disclosed that they and other security firms had discovered Hafnium exploiting four previously unknown vulnerabilities within Microsoft’s Exchange package. Patches have been released, and Microsoft even released patches for versions of Exchange that had reached end-of-life status. Hafnium is described as a Chines state-sponsored group that targets the US, and global, organizations via creating a web shell once access is granted.
The web shell can then be used to exfiltrate data and as Exchange is targeted, attackers can steal the contents of a user’s email inbox as an example.
The four vulnerabilities, and how Hafnium exploits them, are:
- CVE-2021-26855 is a server-side request forgery (SSRF) vulnerability in Exchange that allows the attacker to send arbitrary HTTP requests and authenticate as the Exchange server.
- CVE-2021-26857 is an insecure deserialization vulnerability in the Unified Messaging service. Insecure deserialization is where untrusted user-controllable data is deserialized by a program. Exploiting this vulnerability gave HAFNIUM the ability to run code as SYSTEM on the Exchange server. This requires administrator permission or another vulnerability to exploit.
- CVE-2021-26858 is a post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials.
- CVE-2021-27065 is a post-authentication arbitrary file write vulnerability in Exchange. If HAFNIUM could authenticate with the Exchange server then they could use this vulnerability to write a file to any path on the server. They could authenticate by exploiting the CVE-2021-26855 SSRF vulnerability or by compromising a legitimate admin’s credentials.
It bears repeating that the flaws have been patched by Microsoft and it is strongly recommended that organizations who make use of the popular communication tool ensure that all relevant patches have been installed. As other threat actors, and now those deploying ransomware, are also looking to exploit the above-mentioned vulnerabilities patching systems should be made a priority.
DearCry Ransomware
According to Bleeping Computer hackers are now installing a newly discovered ransomware, DearCry, onto unpatched machines running Exchange and making use of the above-mentioned flaws, which have become collectively known as the ProxyLogon vulnerabilities. The discovery was made by Michael Gillespie, the creator of the ransomware identification site ID-Ransomware. On March 9, several users began submitting a new ransom note, after a bit of digging it was discovered that almost all of the ransom notes were submitted via an Exchange server.
On the same day, a user of Bleeping Computer’s ransomware forum created a post stating that their Microsoft Exchange server was compromised using the ProxyLogon vulnerabilities, with the DearCry ransomware being the payload. This was then confirmed by Microsoft via Twitter, stating,
“Microsoft observed a new family of human operated ransomware attack customers – detected as Ransom:Win32/DoejoCrypt.A. Human operated ransomware attacks are utilizing the Microsoft Exchange vulnerabilities to exploit customers. #DearCry @MsftSecIntel”
The ransomware samples discovered by MalwareHunterTeam are MinGW-compiled executables. MinGW is a free open-source compiler used to create Windows applications, often used to compile scripts written in C, but supports C++, Objective-C, Objective-C++, Fortran, and Ada as well. When launched DearCry will attempt to shut down a Windows service named 'msupdate.' It is not known what this service is, but it does not appear to be a legitimate Windows service. Once complete the ransomware will begin to encrypt files using AES-256 and RSA-2048 algorithms.
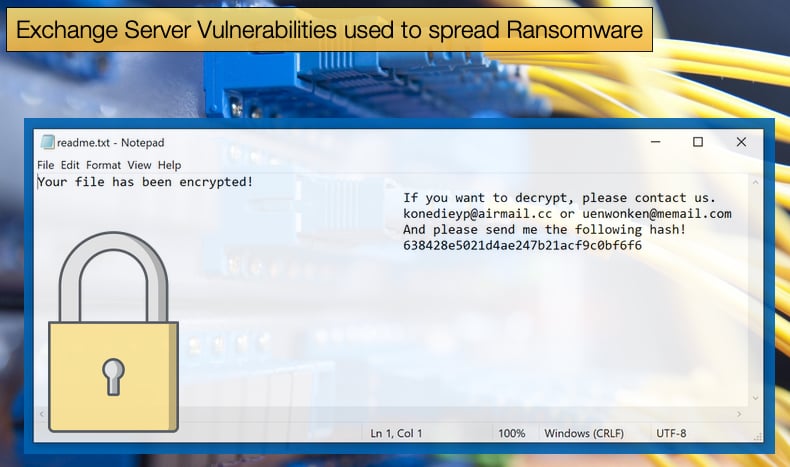
Unfortunately, there appears to be no weakness in the encryption process, making the creation of a free decryptor an impossibility for the near future. During encryption the ransomware appends .CRYPT to the end of encrypted files and is a key identifier for those who believe have been infected with the ransomware. Once encryption is done the ransomware will create a simple ransom note named 'readme.txt' on the Windows desktop. According to Bleeping Computer, one victim needed to pay 16,000 USD to have files decrypted. It is believed that DearCry is human-operated in the sense that the attackers will deploy the ransomware in a highly targeted manner and manually enable the encryption process when the hacker feels the victim is unable to respond quickly.
It is important to note that DearCry’s use of the ProxyLogon vulnerabilities is not 100% confirmed at this stage. However, there is strong evidence to suggest this is the case. Even though it might not be confirmed as the main delivery method of the DearCry payload, it does not detract from the importance of ensuring all relevant patches have been applied. Palo Alto Networks noted that 80,000 older servers cannot directly apply the patches. This leaves hackers with an opportunity many of them would not think twice about exploiting. Speaking to Bleeping Computer, Matt Kraning, Chief Technology Officer, Cortex at Palo Alto Networks, noted,
“I’ve never seen security patch rates this high for any system, much less one as widely deployed as Microsoft Exchange, Still, we urge organizations running all versions of Exchange to assume they were compromised before they patched their systems, because we know attackers were exploiting these zero-day vulnerabilities in the wild for at least two months before Microsoft released the patches on March 2."
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion