Ransomware Gangs using Virtual Machines to Hide Activity
For any scholar of cybersecurity trends, ransomware provides a unique study. The threat has seen several key evolutions since it first emerged in 2010. The latest evolution seen and documented by two separate security firms involves how ransomware operators are using virtual machines (VMs) to hide activity.
VMs are often used for the emulation or virtualization of traditional hardware. A virtual machine can be defined as,
“A Virtual Machine (VM) is a compute resource that uses software instead of a physical computer to run programs and deploy apps. One or more virtual “guest” machines run on a physical “host” machine. Each virtual machine runs its own operating system and functions separately from the other VMs, even when they are all running on the same host. This means that, for example, a virtual MacOS virtual machine can run on a physical PC.”
In May 2021, researchers based at Sophos Labs discovered an instance of RagnarLocker in an Oracle VirtualBox Windows XP virtual machine. The discovery was detailed in a report published by the firm and it was discovered that the attack payload was a 122 MB installer with a 282 MB virtual image.
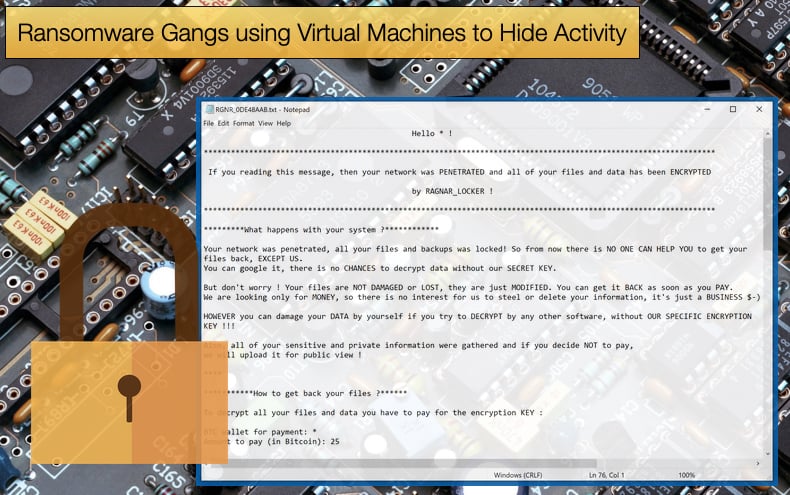
It is assumed that this was done to further hide the 48 KB ransomware executable responsible for encrypting selected files and folders. This marks a distinct change in tactics for the gang who relied on targeting managed service providers then gaining access to other networks via RDP connections.
Then attackers would move to gain administrator access to exfiltrate sensitive data to be used in extortion attempts. This would then be followed by encryption and threats to release the stolen data if the ransom is not paid.
These tactics were seen in April 2021, when the gang attacked the network of Energias de Portugal (EDP) and claimed to have stolen 10 terabytes of sensitive company data, demanding a payment of 1,580 Bitcoin (approximately 54 million USD at the time of writing) and threatening to release the data if the ransom was not paid.
In the past, the gang was also seen to abuse PowerShell and Windows Group Policy Objects to move laterally across a victim’s network to target a wider array of resources and files. In the attack detected by Sophos Labs, the attackers again abused Windows Group Policy Objects to install a package from a web server containing a working version, although an older version, of Oracle VirtualBox hypervisor and a virtual disk image file.
The image file contained a stripped-down version of the Windows XP SP3 operating system, called MicroXP v0.82, and the Ragnar Locker ransomware executable. This is then copied to the machines Program Files followed by the installation of the virtual machine. Commenting on the next steps in the infection chain, researchers noted,
“Now the virtual environment is prepared, the install.bat command goes through a list of process names and terminates these processes so any files they have open are unlocked and become accessible for encryption. This list of 50 entries consists of mainly line-of-business applications, database, remote management and backup applications and is stored in a text file. Another text file contains services names. These are tailored to the victim organization’s network environment, including process and service names belonging to endpoint protection software.”
Symantec’s Discovery
The second security firm to discover ransomware gangs abusing VMs was Symantec. In a recent blog article it was discovered that another threat actor was looking to execute ransomware via VirtualBox. This time running instances of Windows 7. It is believed by researchers that this is done to reduce the chances of the ransomware being discovered before it is too late.
In practice the VM allows the ransomware to “hide” within it until the attacker executes the encryption routine. This is made possible as the VM has access to the host machine’s files and directories. This access allows for later encryption as well as the attacker being able to steal and exfiltrate data if they so wish.
Unlike in the attack discovered by Sophos Labs, the researchers at Symantec have not definitely attributed the attack to one gang in particular. However, there is a belief that the gang behind the Conti ransomware strain may have been responsible. To complicate attributing the attack properly, evidence to suggest those behind the Mount Locker ransomware strain may have also been involved.
Researchers suggest that the attacker attempted to run Conti via the virtual machine but, when that didn't work, they switched to using Mount Locker instead. Commenting on the evidence found by researchers it was stated,
“While the payload running in the VM was not identified, there were reasonably strong indicators that it was Conti. A username and password combination (nuuser/7HeC00l3stP@ssw0rd) used in these attacks was previously associated with older Conti activity, dating from April 2021…
However, on the same computer that the VM was deployed on, Symantec also observed Mount Locker being deployed, raising the question as to whether the payload was actually Mount Locker. Since the main purpose of running a payload on a VM is to avoid detection, it doesn’t make much sense for the attacker to also deploy the payload on the host computer.”
Another Evolution in Tactics
Worryingly, the use of VMs to hide activity is not the only recent evolution in ransomware tactics enterprises and the general public need to be aware of. Microsoft now warns that call centers are now being used to guide victims into installing ransomware. The scam is a hybrid of popular call center support scams and ransomware distribution.
In summary, the call center is used to guide victims into installing the infamous malware BazarLoader that can then be used by the attackers to install ransomware.
The attack begins with phishing emails advising the victim that a trial subscription has expired and that they will be automatically charged a monthly fee unless they call a number to cancel the trial.
Microsoft’s Security Intelligence Team discovered that Office 365 users were targeted in a recent campaign and the phishing email is sent from a fake tech firm claiming that the victim has downloaded a demo version that will expire in 24 hours, at which point they will be charged for the software.
It was further discovered that the group is also using the Cobalt Strike penetration testing kit to steal credentials, including the Active Directory (AD) database. Cobalt Strike is frequently used for lateral movement on a network after an initial compromise. The AD theft is a big deal for the enterprise since it contains an organization's identity and credential information.
Given that the emails targeted Office 365 users, an application used in a majority of enterprises globally, it is safe to assume AD theft would be high on the agenda before ransomware is executed. Commenting further on the attack campaigns tactics researchers noted,
“When recipients call the number, a fraudulent call center operated by the attackers instruct them to visit a website and download an Excel file in order to cancel the service. The Excel file contains a malicious macro that downloads the payload,”
The above article shows two new methods ransomware can spoil your day. While some publications are asking whether ransomware has hit its peak one thing is clear and those ransomware operators will still be causing financial heartache in the short to medium term. One shouldn’t be surprised if the pain is still being caused in the long term.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion