Microsoft warns of Sneaky Phishing Tactic
Microsoft security researchers have recently published an article detailing a widespread phishing campaign looking to steal credentials by abusing redirector links. At first, the potential victim is baited by impersonations of well-known productivity tools. They are then redirected to multiple sites which include a CAPTCHA verification page before taking the victim to a fake login page.
Using redirection links has long been a favored technique of hackers, but it is also used by legitimate businesses even if it irritates some customers. Often redirects are used in emails sent by sales and marketing teams to lead customers to a desired landing web page and track click rates and other metrics.
Hackers will use the tactic to link a trusted domain and embed the eventual final malicious URL as a parameter. This is done to prevent security solutions from quickly detecting if the redirect is malicious. Researchers provide the following real-world abuse of this tactic,
“For instance, users trained to hover on links and inspect for malicious artifacts in emails may still see a domain they trust and thus click it. Likewise, traditional email gateway solutions may inadvertently allow emails from this campaign to pass through because their settings have been trained to recognize the primary URL without necessarily checking the malicious parameters hiding in plain sight.”
The phishing campaign discovered by Microsoft researchers was also notable for another reason. That being that attackers made use of a wide array of domains for sending the emails that would eventually redirect users to the fake login page. Domains used in the campaign included free email domains from numerous country code top-level domains (ccTLDs), compromised legitimate domains, and attacker-owned domain generated algorithm (DGA) domains.
In total, the attackers made use of at least 350 unique domains. For those tasked with uncovering the details of the phishing campaign, it showed not only the scale of the attack but also the level the attackers had invested in the campaign. This possibly shows that the attackers were expecting a high return on their investment.
Phishing has proven time and time again that it is an effective means to gather credentials or act as the initial step of compromising a network. Researchers noted that a successful phishing campaign requires three things to be executed well.
These three requirements being: a convincing social engineering lure, a well-crafted detection evasion technique, and a durable infrastructure to carry out an attack. According to Microsoft, 91% of all cyberattacks begin with a malicious email emphasizing the need for enterprises to invest in effective measures to stop at attacks, including phishing emails, at the source.
Credential Phishing at the Redirector Pond
Recently, we have seen several novel techniques being used in phishing campaigns including the use of morse code and how even well-known threat groups, like FIN8 make use of phishing tactics to compromise enterprise networks. Microsoft’s recent revelation further shows how sneaky phishing campaigns can be.
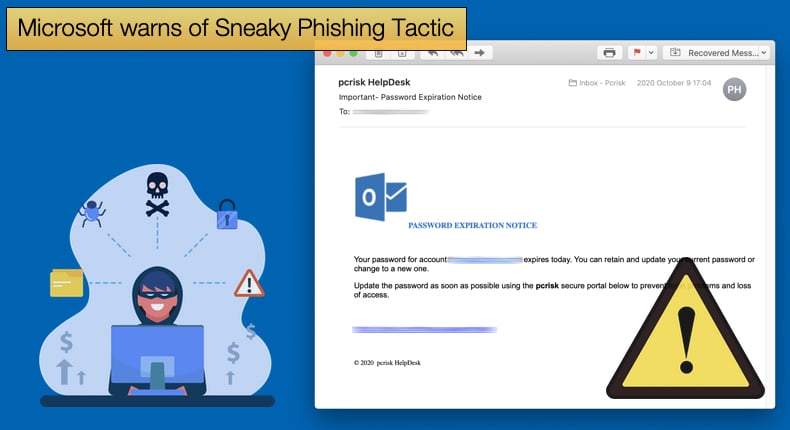
In this campaign, emails followed a general pattern which will hopefully make it easier to spot for admins. Emails sent displayed all the email content in a box with a large button that led to credential harvesting pages when clicked. The subject lines for the emails varied depending on the tool they impersonated. The following subject lines were used by attackers:
- Recipient username] 1 New Notification
- Report Status for [Recipient Domain Name] at [Date and Time]
- Zoom Meeting for [Recipient Domain Name] at [Date and Time]
- Status for [Recipient Domain Name] at [Date and Time]
- Password Notification for [Recipient Domain Name] at [Date and Time]
- [Recipient username] eNotification
If the recipient hovers their pointer over the link they are shown the full URL but importantly the actors set up open redirect links using a legitimate service, users see a legitimate domain name that is likely associated with a company they know and trust. If they looked a little closer they would find that the end of the domains uses .xyz, .club, .shop, and .online suffixes.
Given that the suffice is at the end or towards the end of a relatively long link it is perceivable that recipients will ignore the tiny detail and click through. Researchers noted,
“These crafted URLs are made possible by open redirection services currently in use by legitimate organizations. Such redirection services typically allow organizations to send out campaign emails with links that redirect to secondary domains from their own domains. For example, a hotel might use open redirects to take email recipients to a third-party booking website, while still using their primary domain in links embedded in their campaign emails…Attackers abuse this functionality by redirecting to their own malicious infrastructure, while still maintaining the legitimate domain in the full URL. The organizations whose open redirects are being abused are possibly unaware that this is even occurring.”
CAPTCHA Abuse
As mentioned previously if the recipient clicks the link they are redirected through several web pages, including a CAPTCHA page. Typically, these pages are used by website owners that those looking to access the website are human and not programmed bots. In this case, the use of a CAPTCHA verification is done to add legitimacy to the phishing email and helps prevent detection by security solutions.
Once the victim “proves they are human” they are then redirected to a legitimate-looking but ultimately fake login site. Once the user enters in credentials for popular software applications like Office 365, of which a fake login page was discovered, the credentials are harvested and sent to a server under the attacker's control.
The attackers have added another nasty trick to the operation by displaying an error message when the victim clicks the login button. They are then prompted to enter their credentials again.
Researchers believe this is done to make sure they get the correct username password combination as the victim will be forced to enter the correct details the second time. Once the user enters their password a second time, the page directs to a legitimate Sophos website that claims the email message has been released. This adds another layer of false legitimacy to the phishing campaign.
This attack campaign and others seen recently show how well-crafted phishing campaigns have become. Attackers will purposefully mimic legitimate operations like linking appear legitimate when hovering over it, only to have one of the parameters appear illegitimate to only the most well-trained eye.
The potential victim is then taken to what they deem legitimate verification services and login pages. It is little wonder that phishing is still a very effective means to initially compromise a network, even before any malware has been added to the equation.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion