Pysa Ransomware Ramps Up Attacks
In the NCC Groups monthly threat pulse article it was discovered that the Pysa ransomware strain took the dubious honor of becoming one of the most prolific ransomware strains for the month of November. Attacking businesses has always been on the agenda for those behind Pysa, in the past the publication covered how the gang was targeting organizations within the education sector.
NCC’s latest findings show that Pysa attacks are up 50% with a 400% increase in attacks on organizations within the government sector.
The report notes,
“NCC Group’s Strategic Threat Intelligence team has identified PYSA and Lockbit as the threat actors dominating the ransomware landscape in November. Since August this year, Conti and Lockbit have been the top threat groups, but in November, PYSA, also known as Mespinoza, overtook Conti with an increase of 50%. Meanwhile, the prevalence of Conti decreased by 9.1%. PYSA is a malware capable of exfiltrating data and encrypting users’ critical files and data, which typically targets large or high-value finance, government and healthcare organizations.”
The majority of Pysa’s targets are based in either North America or Europe and in total the regions saw 154 and 96 victims respectively, for all ransomware variants including Pysa.
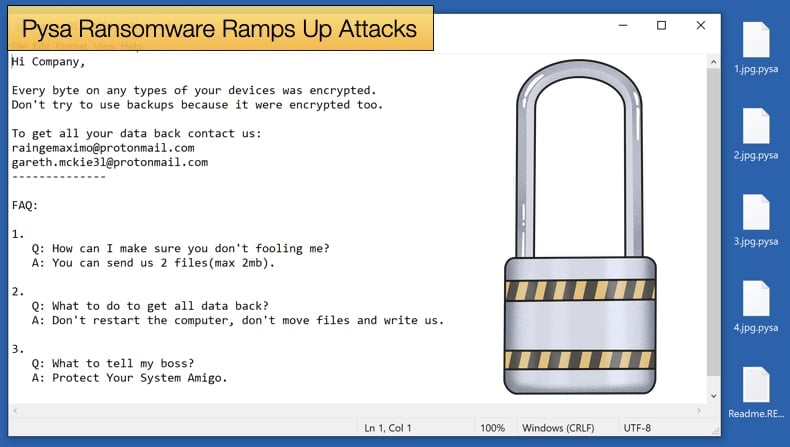
The ransomware was first seen in October 2019 and it was quickly determined that the ransomware was a new variant of Mespinoza. Researchers at Cyber Reason determined that the Pysa ransomware had three key characteristics. They are:
- Human-Operated: PYSA is a human-operated ransomware that does not have self-propagation capabilities. Threat actors manually deploy the PYSA ransomware as part of full attack operations. The PYSA ransomware operators typically gain initial access to target systems by compromising credentials or through phishing emails. Before the deployment of the ransomware, the malicious actors use publicly available and/or open-source tools for credential theft, stealthiness, privilege escalation, lateral movement, and more.
- Hybrid Encryption Approach: The PYSA ransomware is implemented in the C++ programming language and uses the open-source CryptoPP C++ library for data encryption. The ransomware encrypts data by combining the use of the Advanced Encryption Standard-Cipher Block Chaining (AES-CBC) and the Rivest, Shamir, Adleman (RSA) encryption algorithms. This is to maximize both encryption performance and security.
- Double Extortion: The PYSA ransomware operators use a double extortion tactic - if the victim refuses to pay for data decryption, the malicious actor threatens to leak the data or sell it for profit.
Pysa’s More Interesting Traits
Since Pysa’s discovery, those behind the ransomware’s distribution have adopted several interesting traits that separate the ransomware gang from its rivals. One such tactic involves ransomware operators searching for evidence of a crime being committed by the targeted organization this information is then used to apply more pressure to pay the ransom.
Initial access to the network is often gained by abusing Remote Desktop Protocol (RDP) connections. Credentials to access an RDP connection can be stolen in several ways but phishing is still one of the more popular methods.
Pysa operators can either gain credentials via phishing or by using brute force attacks where thousands of username-password combinations are used to try and guess the login credentials. This type of attack relies on the victim using weak passwords that they feel are easy to remember.
In the past Pysa infections have also relied on backdoors installed on compromised networks by other types of malware. Initial access, once gained, is then used to allow the operator to search and analyze the entire network a device is connected to.
The ransomware’s operators appear to be highly disciplined and patient, spending extended periods undetected while they perform high levels of reconnaissance.
It is in this phase of the attack that the ransomware operator will search for evidence that may suggest the organization committed a crime or is linked to criminal activity.
If such evidence or activity is found it will allow the attackers to apply a massive amount of pressure on business leaders to pay. This is due in part to the fact that Pysa operators will release information to the broader public.
To suggest that this would be a PR nightmare for the company would be an understatement as the evidence may be used to advance criminal cases by local law enforcement agencies. This also means that Pysa operators are often emboldened to demand ransoms in excess of 1.5 million USD.
This begs the question if the ransom is paid are there any assurances such sensitive information will not be leaked? The simple answer is no. Pysa in the past has been known to leak data even if the victim has paid the ransom. This has happened, in some instances, six months after the ransom was paid and decryption keys handed over. The FBI noted that,
“In previous incidents, cyber actors exfiltrated employment records that contained personally identifiable information (PII), payroll tax information, and other data that could be used to extort victims to pay a ransom. The cyber actors have uploaded stolen data to MEGA.NZ, a cloud storage and file sharing service, by uploading the data through the MEGA website or by installing the MEGA client application directly on a victim's computer. However, in the past, actors have used other methods of exfiltrating data that leaves less evidence of what was stolen.”
Given that Pysa activity rose steeply in November, there is nothing to suggest that this trend will decrease in the holiday season.
As many staff take leave over the holiday period businesses and other organizations may be understaffed in critical cyber security positions making such organizations a priority target, not just of Pysa operators by ransomware gangs in general.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion