BlackByte Ransomware Attacks the 49ers
Many, particularly in North America, are still dealing with the hangover from the Super Bowl. Some overindulged if they won, and others looked to drown their sorrows. For the San Francisco 49ers who did not even play in the Super Bowl, any disappointment in not playing was impacted by a cyberattack that occurred just before the Rams and Bengals were set to start.
According to a statement made by a 49ers spokesperson for the storied National Football League (NFL) team,
“Upon learning of the incident, we immediately initiated an investigation and took steps to contain the incident. Third-party cybersecurity firms were engaged to assist, and law enforcement was notified…While the investigation is ongoing, we believe the incident is limited to our corporate IT network; to date, we have no indication that this incident involves systems outside of our corporate network, such as those connected to Levi's Stadium operations or ticket holders. As the investigation continues, we are working diligently to restore involved systems as quickly and as safely as possible.”
Soon after the attack, an announcement was made on a ransomware gang's leak site that they had successfully compromised the football team's infrastructure.
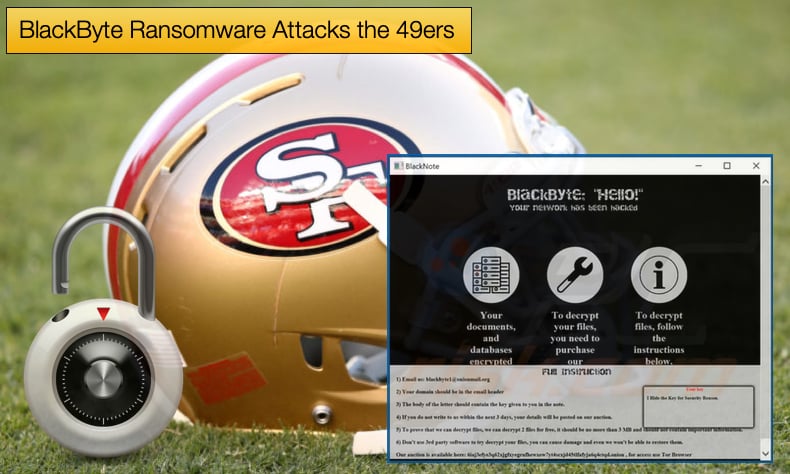
The gang responsible actively distributed BlackByte ransomware. The attack came a few days after the Federal Bureau of Investigation (FBI) warned the gang was targeting private and government organizations including critical infrastructure. The warning stated,
“This joint Cybersecurity Advisory was developed by the Federal Bureau of Investigation (FBI) and the U.S. Secret Service (USSS) to provide information on BlackByte ransomware. As of November 2021, BlackByte ransomware had compromised multiple US and foreign businesses, including entities in at least three US critical infrastructure sectors (government facilities, financial, and food & agriculture). BlackByte is a Ransomware as a Service (RaaS) group that encrypts files on compromised Windows host systems, including physical and virtual servers.”
Further, the FBI summarized the ransomware’s main tactics and techniques by stating,
“The BlackByte executable leaves a ransom note in all directories where encryption occurs. The ransom note includes the .onion site that contains instructions for paying the ransom and receiving a decryption key. Some victims reported the actors used a known Microsoft Exchange Server vulnerability as a means of gaining access to their networks. Once in, actors deploy tools to move laterally across the network and escalate privileges before exfiltrating and encrypting files.
BlackByte’s Beginnings
The first utterings and subsequent discovery of BlackByte occurred on July 19, 2021, when a user posted to Bleeping Computer’s forum looking for more information regarding the ransomware strain as it appeared that a network associated with the user was hit. Information regarding the ransomware began to trickle in incredibly slowly.
This was until October 2021, when the gang which operates under the ransomware-as-a-service (RaaS) umbrella where the malware is developed then handed over to affiliates to carry out distribution, infection, and encryption, struck a farming cooperative in Iowa.
A local newspaper reporting on the matter noted that along with another attack on a separate farming cooperative conducted by those behind BlackMatter, Farmers Cooperative Elevator Co., based in Arcadia, Iowa, was hit by BlackByte.
The ransomware gang announced that they had struck the cooperative via their leak site and would be releasing gigabytes worth of data if the collective failed to meet the ransom demands.
While this attack affected a much smaller company than the BlackMatter attack its timing helped bring the spotlight on BlackByte allowing more security researchers to start uncovering the more technical aspects of the ransomware.
Following this attack, Trustwave soon released not one but two in-depth articles analyzing the ransomware. The articles go into amazing depth and can be considered top-notch threat intelligence for those tasked with defending IT infrastructure. For readers not to be fussed with the technical aspects Trustwave researchers summarized some of their findings, noting:
Same as other notorious ransomware variants like REvil, BlackByte also avoids systems with Russian and ex-USSR languages.
- It has a worm functionality similar to RYUK ransomware.
- It creates a wake-on-LAN magic packet and sends it to the target host - making sure they are alive when infecting them.
- The author hosted the encryption key in a remote HTTP server and a hidden file with .PNG extension.
- The author lets the program crash if it fails to download the encryption key.
- The RSA public key embedded in the body is only used once, to encrypt the raw key to display in the ransom note – that’s it.
- The ransomware uses only one symmetric key to encrypt the files.
Trustwave has also managed to develop a decryptor that can be downloaded from their Github repository. The fast turnaround time in developing a decryptor came as a result of how the ransomware is coded. Other ransomware strains create a unique key in each session.
BlackByte differs in that it uses the same raw key that it has to download during infection to encrypt files and it uses a symmetric-key algorithm – AES. To decrypt a file, one only needs the raw key to be downloaded from the host.
As long as the .PNG file it downloaded remains the same, we can use the same key to decrypt the encrypted files. The .PNG file, often labeled “forest.png” has been seen by researchers to contain the raw key.
Red Canary’s Discovery
In November 2021, another security firm, Red Canary, made an important discovery as to how BlackByte achieves initial access and spreads laterally. According to researchers in a campaign, they witnessed, BlackByte achieved initial access by exploiting ProxyShell vulnerabilities in Microsoft’s exchange server.
The vulnerabilities have been well documented by Microsoft with the Redmond tech giant advising users to install the subsequent patches. The vulnerabilities, CVE-2021-34473, CVE-2021-34523, CVE-2021-31207, if correctly exploited do allow for remote code execution.
In the instance of the observed attack, researchers discovered that an adversary remotely created a draft email with an attachment saved in the user’s Drafts folder. The attachment contained the encoded web shell. Subsequent exploitation resulted in the adversary being able to export the entire mailbox to a PST file.
Once initial access is gained and a machine compromised, BlackByte relies on everyone’s favorite penetration testing tool Cobalt Strike by dropping a beacon. This technique has been seen used with several other ransomware strains.
Cobalt Strike is then used to dump credentials for a service account on the compromised network. In this instance, the attackers installed a compromised version of ANyDesk to further assist in lateral movement.
Given BlackByte’s recent attack on the San Francisco 49ers and recently released FBI warning, activity by the gang is clearly on the rise and attempting to fill the vacuum left by several defunct ransomware gangs who either retired or were successfully shut down by law enforcement operations.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion