Steam Accounts Stolen Using Browser-in-the-Browser Attack
Steam and its vast array of gaming enthusiasts who use the platform have long been a target for cybercriminals, either to frustrate users or make significant amounts of money hijacking accounts and selling them off. Now attacks are using a newly discovered phishing method, known as a Browser-in-Browser attack to go after the Steam accounts of well-known professional gamers. This is according to a new report by Group-IB.
Briefly, a Browser-in-the-Browser attack allows the attacker to create fake login screens as a pop-up for the targeted organization.
This attack method was discovered by security researcher mr.d0x who describes why the attack can be incredibly successful and damaging to the victim as follows,
“With this technique we are now able to up our phishing game. The target user would still need to land on your website for the pop-up window to be displayed. But once landed on the attacker-owned website, the user will be at ease as they type their credentials away on what appears to be the legitimate website (because the trustworthy URL says so).”
Since the new phishing method was discovered in March 2022, security firms have seen fake login pop-ups created for Steam, Windows, and Google.
As to why an attacker would want to gain access to and effectively steal a Steam account, a platform for downloading and playing computer games, Group-IB reports that selling access to a prominent account can net the attacker anywhere between 100,000 and 300,000 USD.
All successful phishing attacks require some kind of bait to lure their victim into handing over login credentials.
Campaigns using this attack method have used a variety of enticing lures for a wide variety of the gaming community and include offers to join a popular eSports team or discount tickets for popular eSport leagues including the ESL.
In other instances, ads for free gameplay skins were used as a lure that redirected to phishing operations of the attackers. As to who exactly the attackers are is a vast unknown. What is known, however, is the attackers are not a phishing-as-a-service operation.
Rather, they are more closely knit, possibly using Discord or Telegram to coordinate attacks privately.
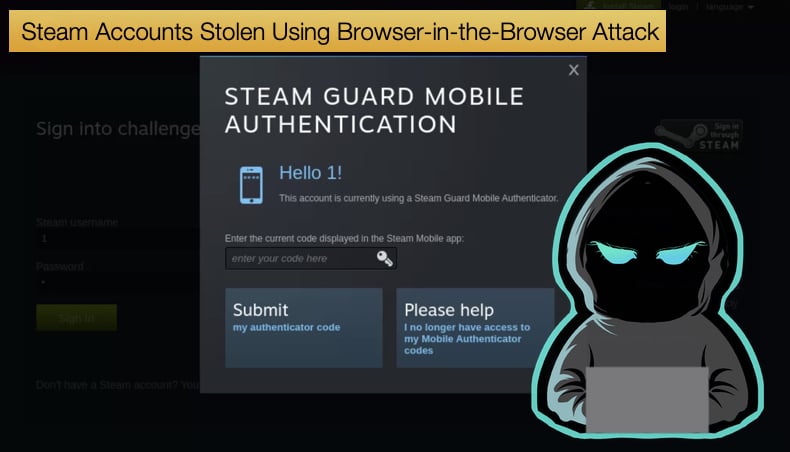
For those who click through to the pop-up login page, it can be very difficult to detect that this is a phishing attempt. The fake Steam login page includes a fake green lock sign, a fake URL field that can be copied, and even an additional Steam Guard window for two-factor authentication.
The HTTPS URL copy with the lock icon is particularly troublesome as the attacker can simply copy legitimate URL addresses. One of the things users are told to prevent phishing is to double check the URL, now a legitimate URL just copied prevents users from applying this mitigation tactic.
To add even more of a veneer of legitimacy users can be selected between 27 different language options on the fake login page.
This is done with a few JavaScript scripts rather than PHP scripts typically used in phishing campaigns. In the above campaign, the attackers even circumvented multifactor authentication, with researchers stating,
“If the victim has enabled two-factor authentication, the resource returns a code request. The code is created using a separate application, which sends a push notification to the user’s device.”
Browser-in-the-Browser versus Traditionally Phishing
To understand why the Browser-in-the-Browser, or simply just BitB, tactic can be so effective it helps to compare it to traditional phishing methods.
In traditional phishing attacks, the data entry form is displayed on a fake webpage, often with a URL created to mimic as best as the attackers can the actual legitimate page, alternatively, users are redirected to the attacker-controlled page.
As mentioned above in a Browser-in-Browser attack the data entry form is presented as a pop-up, much like Steam does in reality.
As it's a pop-up the legitimate web URL can be copied and the icon for an SSL certificate, the lock, can be displayed with relative ease. Traditionally, phishing pages cannot display the lock icon as they are unable to get an SSL certificate.
This begs the question, how does one defend against such an attack given that almost the whole campaign is manipulated to trick users by using security tactics they already apply.
The nuclear option is to block your browser from activating javascript scripts. As the attack is reliant on JavaScript to both render the pop-up and send the stolen credentials to a command-and-control server controlled by the attacker.
This will not be a popular choice as much of the majority of websites are reliant on JavaScript to provide the functionality and user experience the webpages needs to be considered useful.
The security researcher, mr.d0x, told Bleeping Computer that one of the ways to detect a BitB attack is to try to move the pop-up beyond the original browser window.
If the pop-up goes under the browser's borders it can then be assumed it's a BitB attack. Group-IB researchers also provided the following mitigation tactics:
- Check if a new window is opened in the taskbar, assuming you ungroup programs in the Windows 10 taskbar. If no new taskbar window exists, then this is not a real window. Unfortunately, Windows 11 does not support ungrouping at this time.
- Try to resize the window. If you are unable to, it is likely a fake browser window.
- Fake BiTB browser windows will close if you minimize them.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion