Action1 RMM Seen Abused In Ransomware Attacks
Following several reports from security firms, it appears that ransomware operators are abusing the remote monitoring and management (RMM) product Action1 RMM which is used by Managed Service Providers (MSPs) to manage endpoints on customer networks remotely.
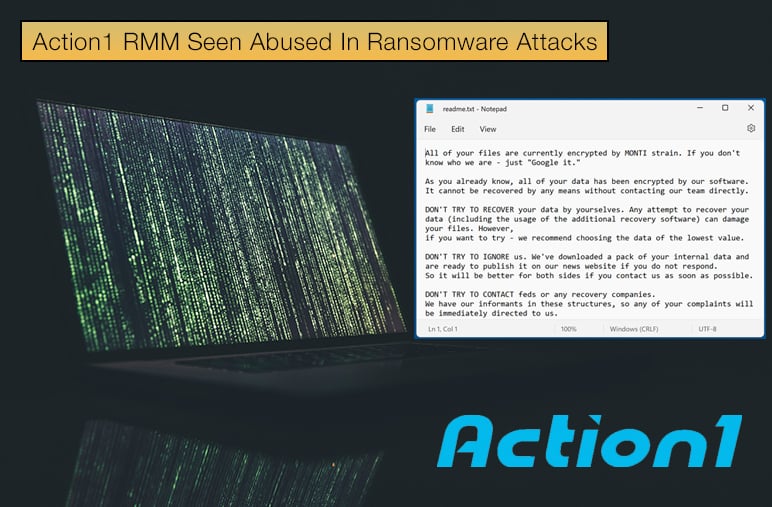
The software package allows patch management, installing security software, and troubleshooting to be done remotely, making it an appealing choice for MSPs and their customer base.
Unfortunately, such tools can also be used by threat actors to compromise and maintain persistence on corporate networks. Further, these tools can be used to drop malware strains on compromised machines.
On April 12, 2023, Kostas, a member of the volunteer analyst group The DFIR Report, tweeted the following,
Threat actors have started leveraging a new RMM platform called Action1…Using Action1, they are seen executing commands, scripts, and binaries. To do that, they must first create a "policy" or an "app". The name of those will show up in the command line during execution…Unfortunately, it is very easy and free for threat actors to use the Action1 RMM for up to 100 endpoints. I think we will see more TAs using this RMM in the feature. I will be creating a Threat Hunting Sigma rule soon to help with the initial search queries based on the above.
Not good news for anyone using the Action1 RMM; however, a tweet from a reputable researcher needs to be corroborated by other evidence.
Bleeping Computer contacted multiple sources who confirmed that attacks were observed from multiple ransomware threat actors where Action1 was abused, particularly in the initial stages of the attack chain.
Further, Bleeping Computer was told by sources that tactics, techniques, and procedures (TTPs) of specific attacks closely resemble an attack that the BlackBerry Incident Response team investigated last year. More on this to follow.
Action1 is aware that their product, while serving customers and making the task or remote management easier, is being used maliciously. To combat this, the company has employed several security upgrades, including AI filtering. Speaking to Bleeping Computer, the company’s Vice President Mike Waters said,
Last year we rolled out a threat actor filtering system that scans user activity for suspicious patterns of behavior, automatically suspends potentially malicious accounts, and alerts Action1’s dedicated security team to investigate the issue…At the same time, I would like to emphasize that these attacks do not target the Action1 users since our platform has not been compromised,
The Confusing Case of Monti
As mentioned above, the tactics seen by security researchers were similar to that of incidents involving the Monti ransomware strain. Monti is seen by experts as a newer variant of the Conti family, with Monti using many of the tactics that made its predecessor such a threat.
Conti was well-known for abusing remote management software to initiate ransomware attacks. However, these often involved AnyDesk, not Action1, it should be noted.
There are also cases where brokers sold initial access to organizations through ManageEngine Desktop Central software from Zoho, a product that allows admins to manage Windows, Linux, and Mac systems on the network.
Sadly, from a ransomware perspective, legitimate RMM software is versatile enough to fit their needs as it provides wide reach on the compromised network and ensures continued persistence because security agents in the environment do not usually flag the platforms as a threat. All of which are factors most desirable to ransomware operators.
In the incident investigated by BlackBerry, security researchers noted that,
The threat actor apparently intruded via an exploitation of the well-known “Log4Shell” vulnerability (a.k.a. CVE-2021-44228) in the client’s internet-facing VMware Horizon virtualization system. At the time the BlackBerry team was engaged, the operators had already initially encrypted 18 user desktops. They also encrypted a three-server ESXi cluster that resulted in 21 virtualized servers being impacted.
Of particular interest, especially in terms of this article, was the threat actor also downloading and installing two remote monitoring and maintenance (RMM) agents, namely AnyDesk and Action1.
Researchers believe the RMM software was used by these agents to establish persistence within the network and to facilitate additional remote access. This incident might have been the first to leverage Action1 in this way. Given how Conti has used this tactic in the past, this is not perhaps as surprising.
It should also be noted that Monti was also abusing other software packages, including the security software packages. This, in turn, was a popular tactic of Conti operators. The link between Conti, whose operations ended after a data leak occurred that could be used by other threat actors to dive into ransomware operations, and Monti is unclear.
However, regardless of the link, it is clear that those behind Monti have developed a ransomware strain in combination with successful tactics, which poses a threat to enterprises.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion