News Archive September 2013
Monthly Cyber Security News Archive: September 2013 Summary
Table of contents:
- School Districts Spying on Students?
- OS X Bug Gives Hackers Access to Root without Password
- A Look Inside the Nigerian Email Scam
- Phishing Scams Are Becoming More Difficult to Detect
- Fake Email Plays on Syria Situation
- Facebook Password Hacking Scam
- Retirement Funds Stolen via SSA Website
- iOS 7 Already a Hacker’s Paradise
- The Long Arm of Identity Theft
- Fake DivX Plug-in Malware Threat
School Districts Spying on Students?
02.09.13
The US government, especially the NSA, has had trouble keeping itself out of the limelight lately as more information continues to be leaked that points to widespread clandestine intelligence operations being conducted on American soil. Although that may be hard for some citizens to grasp or even care about, actions taken by the Glendale Unified School District in Southern California have many people concerned that government espionage may still be in its infancy when it relates to its own citizens.
The Glendale Unified School District has decided to keep tabs on its students both on and off campus by hiring an outside company to monitor social media posts from students. The district chose Geo Listening to follow the activities of students while they are online.
This company specializes in following the Facebook, Twitter, Instagram, and YouTube feeds of children. The district’s superintendent, Richard Sheehan, reported to CBS that the whole purpose of this new program is to keep students safe from themselves and others. This stance does make sense from the perspective that the prepubescent Internet community can be a hostile one. Most school districts around the country have instituted anti-bullying policies that extend online as well as onto the school campus. Incidences of online bullying are occurring more frequently as teens turn to the Internet to express themselves. The system works by watching for certain keywords. This technique is similar to techniques purportedly used by the NSA to monitor for terrorist activity both foreign and domestic. The district cites examples of how potentially suicidal children have been the subject of interventions thanks to this system.
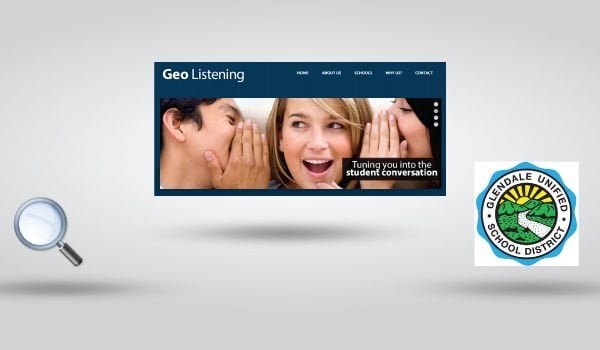
What is concerning for parents is that Geo Listening monitors traffic both on and off campus. Even though most people will argue that the school district is well within its right to monitor Internet traffic within its own network, where does the district’s legal obligation end and individual privacy begin? The district currently has approximately 13,000 students and every single public posting is currently being monitored. Geo Listening insists that it does not look at private pages, SMS, MMS, email, phone calls, or voicemails. Rather, it states its role as providing “timely” information to the district so that it can act accordingly to prevent bullying, self-harm, vandalism, substance abuse, and truancy.
What the company has not stated is what happens to information once it has been analyzed.
Is private student information being held in a database somewhere? Could it be used to negatively impact employment opportunities for these students in the future (especially those who had behavioral issues in school) as potential employers reach out to school districts in search of this type of information? Multiple studies have proven that employers are looking at social media behavioral before making hiring decisions. Does the Glendale Unified School District decision to monitor and record student web traffic have impacts that stretch further than the immediate need to thwart misbehavior in schools? Unfortunately, there are more questions than answers about the long-term effects that these monitoring programs may have. What is known is that web traffic within homes of the school district can no longer ensure the privacy of their information and this leaves many people wondering – what’s next?
OS X Bug Gives Hackers Access to Root without Password
05.09.13
Apple’s OS X has long been revered as a more secure operating system than its competition; namely Windows computers. Although Apple would have you believe that this additional security is simply part of their innovative strategy, it’s actually a result of using a UNIX based system that requires a password before making any administrative changes to the OS. A flaw in OS X revolves around the use of the “sudo” UNIX command. Typically, this command is used before other commands in UNIX-based systems to grant administrative privileges to a particular function. For instance, the sudo command must preface any request to install or modify software on the machine or before deleting files from the hard drive. This flaw allows hackers to bypass access permissions and obtain superuser access to the entire filesystem; including system files.
Normally "sudo" command is off-limits to everyone except administrators. Even administrators have to enter their password to use the command. However, the flaw in OS X allows sudo to be used without a password simply by setting the computer’s system clock back to January 1, 1970. Considered the “beginning of time” for UNIX systems, this date allows sudo to be accessed without authentication. Although this seems like a powerful vulnerability, it does require that the current user is an administrator and has authenticated the sudo command during the current login session. What that means is a user could perform an administrative action, step away from their computer, and someone else could access root privileges without a password.

During normal operation, an OS X user needs to authenticate the sudo command once and the system uses these credentials for 10 minutes before requiring that the password be entered again. By setting the system clock back to 1970, this 10 minute “rule” is voided and allows a hacker to access administrator credentials as long as the password has been entered during the current session. This vulnerability also affects many UNIX and Linux systems; however, these systems require authentication to change the system date. Since OS X does not require authentication to change the system date, it is very easy to exploit this vulnerability via a remote session or physical access to the machine.
The fix is very simple – add authentication requirements to the system time/date functionality.
However, it is still unclear how long it could take Apple to address this simple patch. This bug is known to affect OS X versions 10.7 through 10.8.4. It has already been the designation CVE-2013-1775 in the hopes of addressing the vulnerability as quickly as possible. Until this vulnerability has been patched by Apple, the only way to ensure your credentials are not being used without your permission is to log off your current session whenever the computer is not in use. Although OS X-based machines are still less prone to virus infection when compared to Windows machines, this vulnerability is potentially more damaging than any virus as it would allow the installation of any type of software without knowledge or consent of a legitimate user.
A Look Inside the Nigerian Email Scam
06.09.13
Most people have seen the Nigerian email scams that bombard inboxes across the country and around the world. Specifically, the Nigerian 419 scams (named after Section 419 of the Nigerian criminal code) ask for money from unsuspecting Internet users using a variety of media outlets. Although email is still the primary way this scam operates, these Nigerian criminals have also started using Facebook and online dating sites to woo potential victims before clearing out their bank accounts. Recently, security experts used a simple exploit to uncover the user information of almost 3,000 scammers using a particular service known as BestRecovery. This service offers hackers an easy to implement key logging program that can be disguised in a variety of ways including screensavers and photos.
What makes this particularly concerning is that even if a victim realizes they are being scammed, the key logging software may mean that their bank accounts get cleaned out by Nigerian criminals anyway. Online dating sites are apparently very effective when using this technique. Photos that are supposedly of the scammer are embedded with key logging software that monitors every keystroke made by the victim’s computer once downloaded locally. This makes it extremely easy to gain access to online banking accounts and other sensitive financial information which the hackers can then use to extract money to banks in Nigeria and other parts of the world that may be sympathetic to their cause.
You may find these hoaxes laughable, but the FBI warns that millions of dollars are lost each year using 419 scams alone.
Most of this money is voluntarily sent over by victims who are unaware that they are being scammed.
However, as people are becoming more aware of the existence of these criminal acts, key logging software and other malware is often more effective at extracting money involuntarily than voluntary “donations” once were. Staying safe from these scams is simply a matter of common sense. Although it may be nice to think about extracting millions of dollars from a foreign bank account, it is not going to happen. Do not fall victim to the stories (which can often be very convincing) of these scammers and their plight in a foreign country. Security experts were able to identify thousands of Facebook accounts linked to email addresses uncovered by the vulnerability in the service’s website. Again, this shows that these Nigerian 419 scammers have branched out and no longer rely only on email to lure in victims. A Facebook profile or an attractive online dating profile can often leave people with their guard down and susceptible to this type of Internet fraud.
To make matters worse, the Nigerian government does not have sympathy for those who participate in these actions meaning that there is likely no legal recourse once money has been lost to one of these criminals.
Although these scams are not new, tactics have certainly improved over the years and new victims are uncovered almost every day. The addition of a malware component to these scams makes them even more dangerous and capable of continuing to take millions of dollars for years to come.
Phishing Scams Are Becoming More Difficult to Detect
08.09.13
Phishing attacks are nothing new. In many cases, they are comically easy to spot for most computer users. However, it seems that criminals relying on phishing as a source of income have started to use automated scripts to “target” their attacks more accurately. A recent phishing scam that targeted WordPress administrators is a perfect example of how these attacks can offer much higher rates of return to the criminals behind them. This particular scam works by scraping the Internet for WordPress sites that have a link back to the website designer in the footer. The website designer is targeted as a possible administrator of the site who commonly received emails from WordPress anyway.
The rogue backend server used by these phishing criminals is very simply a compromised Web server with some rudimentary PHP scripts that simulate a WordPress administrative login page. The fake WordPress login even includes the URL of the site where the information was originally gathered. This adds to the “legitimacy” of the page and could easily fool even an experienced administrator if they are not looking carefully. As is the case with every phishing scam that leads to a spoofed website, the URL in the address bar is the key giveaway that the site is malicious.
Although most administrators are used to checking the URL as they log into secure sites, it isn’t hard to imagine a WordPress admin getting tricked into entering their credentials.
The phishing scam starts with an email pretending to be a WordPress notification about a pending comment that needs approval. At the time of this writing, the spoof has a fatal spelling error that would probably tip off most users that this email is probably malicious.

The “sign in” button with the link to the malicious phishing site is incorrectly labeled “sing in.” It appears that the criminals behind this scam need to run a spell check before sending out mass targeted emails. However, the spoofed WordPress login page look so good that if a user happens to overlook this misspelling, they could very well be tricked into providing administrative login credentials. And by being just a little bit more careful next time, the criminals could fool an even larger audience. Targeted phishing scams aren’t exactly new. The difference here is that criminals have obviously found new ways to associate email addresses with specific phishing scams. The more believable and timely a phishing scheme is, the more likely it is to work on a larger group of people. As previously stated, the single best way to avoid a phishing scam is to get into the habit of constantly checking the URL of the site you are supposedly logging into.
If the URL does not match the standard domain you should be visiting, do not enter any login information as this site is probably spoofed and malicious.
Another way to combat scams like this (especially WordPress specific ones) is to always log into WordPress directly from a web browser. Any time you rely on an email link to access a secure page, you run the risk of falling victim to a phishing scam yourself.
Fake Email Plays on Syria Situation
12.09.13
It’s no secret that the potential for war in Syria has taken control of local news outlets. Never to be outdone and always looking for a new angle, hackers have started using this conflict as a way to lure unsuspecting people to malicious websites. Most recently, a spam email is being sent out that is designed to look like a CNN report about the conflict in Syria. The catchy title of the spam email states “The United States began bombing!” This title is sure to grab the attention of many email users who may not be aware that the US has started “bombing” in Syria (as of this writing the US has not started bombing Syria).
The email looks like this:
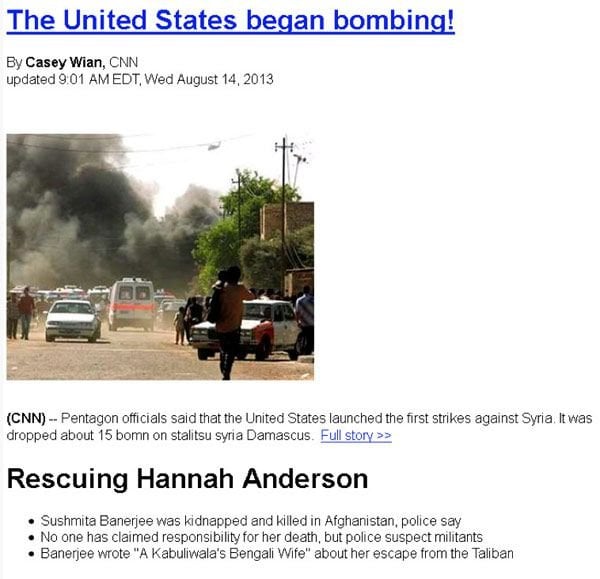
From: {spoofed CNN email address}
To: {random}
Subject: CNN: “The United States began bombing”
Message body:
The Unites States began bombing!
by Casey Wian, CNN
updated 9:01AM EDT, Wed August 14, 2013
(CNN)—Pentagon officials said that the United States launched the first strikes against Syria. It was dropped about 15 bomn on stalitsu syria Damascus. Full story >>
When a user clicks on “Full Story” they are brought to a compromised website that redirects (using JavaScript) to a URL set up for drive-by download attacks. Among others, users may inadvertently download variants of Medfos, Fareit, or Zbot malware.
All of these malicious programs are considered information stealers that open up backdoors into user computers for hackers to gain access remotely. If you are reasonably diligent, you should have no problem spotting this fake email if it comes to your inbox. As you can see from the text contained within the email, there are numerous spelling errors that should tip off most users that there is a problem. There is a similar email also circulating that has a few variations. Although it uses the same CNN byline, the altered headline reads “United States made ? the first surgical skes on Syria.” The contents of the email are:
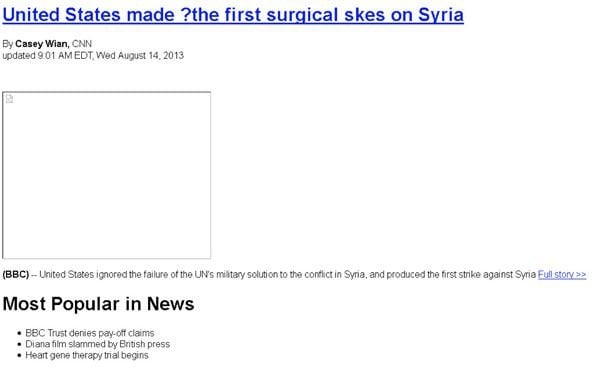
From: {spoofed BBC email address}
To: {random}
Message body:
(BBC)—United States ignored the failure of the UN’s military solution to the conflict in Syria, and produced the first strike against Syria…{ other news }
Once again, there are numerous spelling errors in the email title and the body of the email that should tip off most users that this email is not actually from CNN or BBC.
The best way to protect yourself from being redirected to malicious links like those found in these emails is to delete the emails from your inbox once you realize they are not legitimate. Furthermore, properly updated antivirus and web browsers will often block these downloads from automatically infecting your computer.
Facebook Password Hacking Scam
14.09.13
Although it may be tempting to retaliate against an ex-significant other, former boss, or other “arch enemy,” there is no such thing as a Facebook Password Hacker. Recently, a number of sites claiming to offer up Facebook hacking/password recovery tools have been found on the Internet that are aimed at tricking users into downloading malicious software or providing payment information. The sites seem relatively legitimate and provide a testimonial section where individuals claim that the software works within seconds. There are phone numbers provided as well as links to live chat and other information.
All of these things combine to make this scam seem relatively legitimate to users who may be unfamiliar with how difficult obtaining Facebook passwords illegally actually is. The tool claims to retrieve Facebook passwords and also mentions the installation of some sort of search bar.
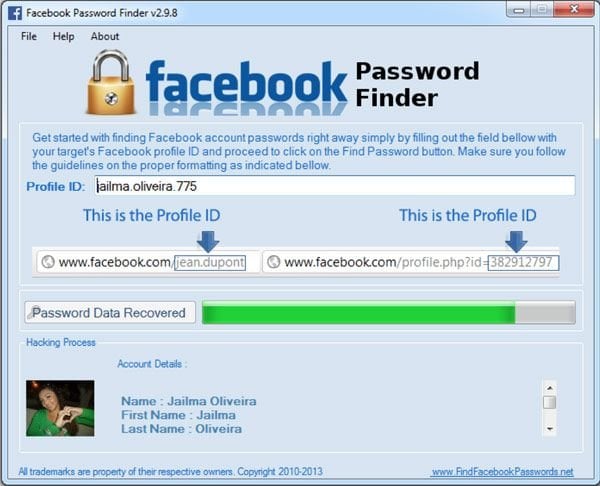
Security expert testing did not find the installation of the search bar; rather, the only software installed was the fake Facebook hacking program. No matter what Facebook user ID is entered into the program, after a few seconds of a “looking up the profile” prompt, a message appears saying that the password has been successfully cracked. Users are then instructed to obtain a product key in order to view passwords. In order to receive a product key, users are required to pay $29.99.
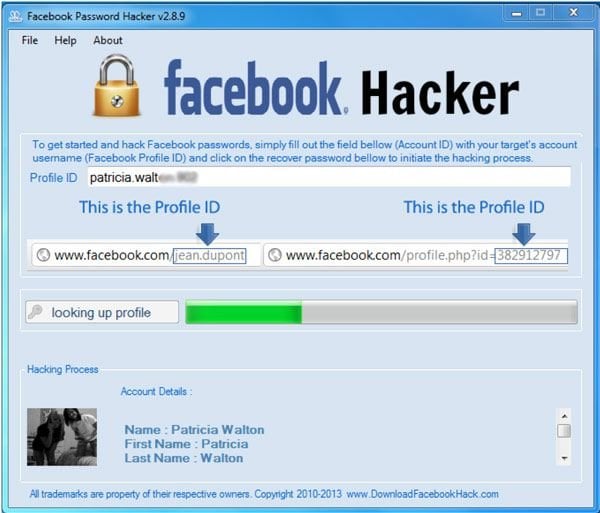
This allows them to view the password recovery and management guide. This website has an about page which gives a rundown of every team member along with their headshot. Interestingly enough, these images appear as other individuals in Google image search results. Basically, these hackers have ripped random head shots from around the Internet and put together as a “team” of Facebook hacking professionals. At this time, the fake program does not introduce any detected malware to a user’s computer. However, as you may have already guessed, if someone actually pays the $29.99 for a product key, their payment information is compromised and opens the door for credit card fraud and possibly identity theft.
The only real way to stay safe from this threat is to not participate in it.
There are literally hundreds of URLs offering this “service,” but three of the most popular include:
hxxp://Findfacebookpasswords.net
hxxp://Downloadfacebookhack.com
hxxp://Freefacebookhacking.com
Not only is it unethical, but Facebook password hacking is nearly impossible, especially from a locally run program. Even if someone were able to access Facebook passwords, they would quickly be caught and criminal charges would certainly be filed. Also keep in mind that although this program does not have malware currently embedded within its installation program, this could change relatively quickly if the pay for product key model fails to work as well as the hackers hope. Key logging programs and banking Trojans could easily be installed along with the spoofed Facebook hacking program – leaving your machine susceptible to easy exploitation and attack.
Retirement Funds Stolen via SSA Website
15.09.13
The Social Security Administration has always been a target for fraud. Currently, approximately 62 million Americans receive a benefit check each month from the SSA and these people (many of them elderly or disabled) are prime targets for identity thieves around the world. Historically, the agency has received about 50 fraud allegations each day. The government thought that the problem was going away as those numbers started to decline, but in fact, the criminals simply changed their tactics. Earlier this year, the SSA started mandating that most beneficiaries sign up for direct deposit through the SSA website. Under limited circumstances, paper checks are still available but for the most part, every American is required to set up direct deposit.
This can be accomplished using an 800 number or more commonly, through the SSA website. It seems that this latest string of fraud is a result of identity thieves creating fraudulent SSA accounts for real beneficiaries that have not already done so.
Once the account has been created, the thieves are able to change direct deposit information and redirect deposits to prepaid debit cards that are basically untraceable.
The government thought they had a foolproof setup because the website only allows one account to be created per Social Security number on file. However, many current beneficiaries have still not created accounts on the SSA website which leaves an opening for these identity thieves. Since this scam has been uncovered, the SSA has increased security by requiring beneficiaries signing up to input the date and amount of their last deposit. In most cases, identity thieves do not have access to this information and will be unable to complete the sign-up process. 
Despite these security improvements, representatives from the SSA are urging current beneficiaries to immediately create their web accounts if they have not done so already. As already mentioned, only one account can be tied to a Social Security number and creating an account effectively blocks identity thieves from taking advantage of this vulnerability. If you are a current Social Security beneficiary and you notice any changes in your payment status or do not receive a payment at all, contact the SSA immediately so that the issue can be tracked down and identified as fraud quickly. For those who are not computer savvy, you can still go to your local Social Security Administration office to make any changes as necessary. Employees will also help beneficiaries create their online account to avoid fraudulent activities. Of course, vulnerabilities still exist for computer users with key logging software installed on their computers.
A hacker could easily record the login information for the SSA account, login, and still defer the payments to a prepaid debit card.
The unfortunate aspect of this scam is that it targets the elderly, people who typically are not technology inclined and may not understand the importance of creating a web account safely with the SSA. If you are the loved one of a beneficiary, reach out to them and make sure they have taken the necessary precautions to protect their identity and their Social Security benefits from fraudsters.
iOS 7 Already a Hacker’s Paradise
20.09.13
Most people are aware that Apple recently released its newest iPhone and its new operating system, iOS 7. As usual, Apple has spent millions of dollars to market this new operating system on its flagship devices as “revolutionary” technology. Unfortunately, it seems that the only thing revolutionary about the new iPhone is how easy it is to break into. One of the biggest features that the new iPhone 5S brings to the table is a Touch ID fingerprint scanner that is supposed to replace the conventional lock screen. Once it is set up for a specific user, the phone will only unlock when that person’s fingerprint is read by the sensor. Seems pretty high tech, right?
Less than a week after the iPhone 5S’s release, this new technology has already been hacked by German researchers known as the Chaos Computer Club. This attack has also been confirmed independently across the Internet as a working hack that can be replicated relatively easily. The hack works by transposing the actual fingerprint of the registered owner to a thin piece of latex. This is enough to fool the Touch ID Sensor into unlocking the phone for anybody who has the latex strip. The fingerprint could be lifted from a coffee cup, a table, or pretty much anything else the victim touches. Although this may seem rather complex, the person who originally discovered the hack only gave vague instructions about how to accomplish this feat and yet hundreds of people around the world have already posted YouTube videos demonstrating how to do the same thing. Some of these people are security experts; others are just iPhone users who were able to bypass this security measure quickly and easily.

If you have the new iPhone and rely on the Touch ID Sensor, experts are recommending that you use the ring or pinky finger as these are more difficult to lift a print from. If that’s not enough, there are also two lock screen vulnerabilities that are very alarming. Last week, someone uncovered a lock screen vulnerability that allowed anyone with direct access to the iPhone the ability to access personal information including Facebook and email accounts. Apple has acknowledged this issue but has yet to fix it meaning that the lock screen is no more secure than Touch ID at this point. Another concerning vulnerability discovered a few days later is that intruders are able to make calls from a locked iPhone. Due to a glitch in the emergency calling feature of the new iPhone equipped with iOS 7, anyone can make calls including to international and premium numbers. It seems that Apple has its work cut out for it to address these serious security issues quickly.
As people continue to use their mobile phones for daily tasks including online banking, vulnerabilities like this are simply unacceptable.
Especially when you factor in the $700 retail price tag of the iPhone 5S, is it really that difficult to make a lock screen that is secure? Apple has not issued a statement regarding when these issues will be fixed as of this writing.
The Long Arm of Identity Theft
25.09.13
Identity theft is often associated with malware installed on a victim’s personal computer or a phishing scam that originates from a rogue email. What many people do not realize is that there are identity theft services around the world that profit from selling information about millions of Americans for as little as $.50 per record. Recently, one of these identity theft services known as SSNDOB was compromised and gave security experts a look into the scary truth about how far-reaching identity theft has become in United States. This website has been advertising for months on underground hacking forums that it sells Social Security numbers, birth records, credit and background reports, and other personal information on millions of Americans by infiltrating some of America’s largest data aggregators. Some of the resources this service has been relying on include the LEXIS-NEXIS database and Dun & Bradstreet.
LEXIS-NEXIS maintains the world’s largest electronic database for legal and public record related information. Dun & Bradstreet licenses information about the creditworthiness of businesses and corporations. A couple of other large background check companies were also involved. Basically, the identity theft service was operating a massive botnet that included public facing Web servers at these companies.
Using malware that is undetectable by any current antivirus software, the hackers were able to access internal databases and funnel out information on over 4 million Americans which has been sold on the black market for at least a few months.
At this point, LEXIS-NEXIS has confirmed that the compromises did in fact occur, but has not yet divulged whether or not sensitive information was actually retrieved. Based on the databases retrieved from SSNDOB, however, is clear that millions of confidential records were in fact compromised during this five-month breach.

In addition to the actual information that was compromised, the other problem is that many of these companies store massive amounts of what is known as “knowledge-based authentication” questions. If you ever applied for credit online, you may have been asked questions about your previous address or who services your mortgage. These knowledge-based authentication questions are stored by companies like LEXIS-NEXIS to aid in positively identifying an individual. If this information has been compromised (the answer is still unclear), then identity thieves could “legitimately” apply for credit in these people’s names by answering the authentication questions correctly. These types of authentication methods are what companies throughout the United States have been relying on to detect fraud. If this information has been compromised, how will that affect fraud detection methods in 2014 and beyond?
Regardless of the potential long-term effects, it is clear that SSNDOB sold over 1 million unique Social Security numbers to customers and nearly 3.1 million birth records in just the last year.
It goes without saying that this is not the only company using the sale of these documents as their business model. This begs the question – how many other data aggregators have been compromised in the US (let alone the rest of the world)?
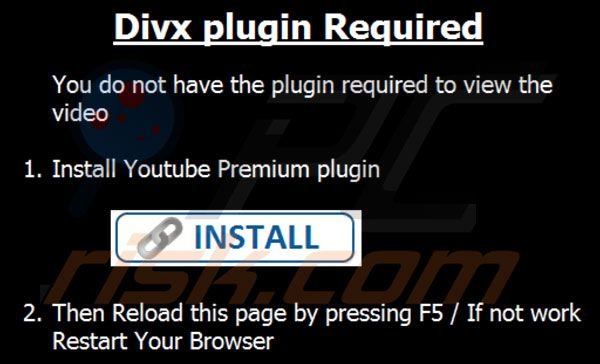
Fake DivX Plug-in Malware Threat
27.09.13
Funny Internet videos are passed around between friends and colleagues faster than practically any other commodity. Although sometimes inappropriate, these videos are usually harmless. Hackers know this and have been using fake videos embedded with malware for years. In many ways, their tactics haven’t changed and yet they are still able to fool many unsuspecting users on a daily basis. A new batch of malware is making its rounds disguised as a DivX plug-in. Right away, those of you are familiar with video formats realize that this really doesn’t make much sense, but unfortunately most users are unaware that they cannot “watch” a DivX plug-in.
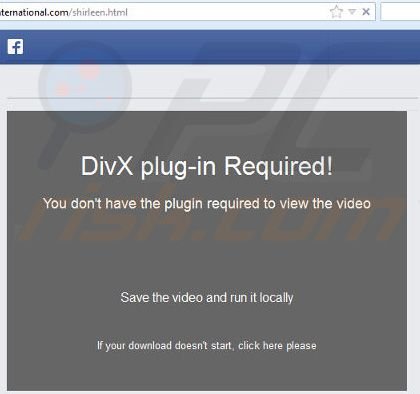
The malicious sites that are pushing these files claim that users have the wrong type of DivX plug-in installed with a link to download the proper plug-in to view the content.
The page displays the following prompt to site visitors:
“DivX plug-in required!
You don’t have the plugin required to view the video
Save the video and run it locally”
The rogue file that it is actually downloaded appears to be of Russian origin and is made up of various filenames that suggest lewd pictures and/or videos. Even though there are approximately 10 different filenames currently used on this site, all of them share the same MD5 checksum.
Most of these files have GIF, JPEG or TIF file name extensions; at least that’s what they want users to believe. This is another technique that has been used for years and still manages to fool Internet users all the time.
Another page on the same domain tells users “You need to download and execute the Facebook app to see it! It’s amazing!” and offers another malicious file to unsuspecting visitors.
Once installation has been initiated on a local machine, the file performs many functions such as deleting original sample, making network connections, creating registry entries to execute on system start-up, etc.
Both websites have been receiving a significant amount of traffic recently. Antivirus typically detects the install file as either Trojan.Win32.Generic!BT or Virtuemonde (the “Facebook app”). The latter file has been around for quite some time but has been frequently modified by hackers to avoid detection and cause additional havoc on computer systems. The key to avoiding this thread is to not download any “plug-ins” or Facebook apps from unknown sources.
Even if you receive an email from a friend or acquaintance, assume that their email account has been hijacked and do not navigate to links embedded within an email message.
As always, make sure your antivirus software is up-to-date and you have installed any OS patches that are available to mitigate damage caused by these and similar malware attacks.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion