News Archive October 2013
Monthly Cyber Security News Archive: October 2013 Summary
Table of contents:
- The Silk Road is Gone – What Will Take Its Place?
- Adobe Systems Breached
- Cash Skimming Devices Rising in Popularity
- Criminal Hackers Could Be Targeting Animals
- Simple Backdoor to Many Popular D-Link Routers
- Snapchat Openly Working with the Government
- Even the Credit Bureaus are Working with Identity Thieves
- Spyware Comes Standard with Some Computer Systems
The Silk Road is Gone – What Will Take Its Place?
04.10.13
Federal agents have finally seized and shut down the Silk Road. This site has been mentioned briefly on this blog in the past due to its ties with a host of criminals and hackers. Often referred to as the “eBay of drugs,” the Silk Road is an online black-market that even as late as last month was hosting nearly 13,000 sales listings for controlled substances including marijuana, LSD, heroin, cocaine, and ecstasy. Similar to the popular auction platform, merchants on the Silk Road mail their customers the illicit merchandise and receive feedback from these customers about the quality of the products and service. In addition to a large drug market, the Silk Road also offered visitors digital goods including banking Trojans, pirated content, and hacked Netflix accounts to name a few.
The “Forgeries” section of the Silk Road offered fake driver’s licenses, Social Security cards, and other documents typically associated with identity theft. Hacking services, firearms, and even hit men were able to advertise their goods and services under the cloak of this “hidden” website. The Silk Road could only be accessed via the Tor network; an anonymity network that bounces its user’s communications across a distributed network of relays run by volunteers around the world.
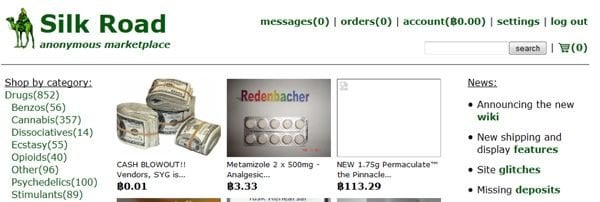
It turns out that the owner and operator of the Silk Road is a 29-year-old San Francisco resident named Ross William Ulbricht. He has since been arrested and is being held on a number of charges including conspiracy to commit drug trafficking and money laundering. Why is this important from a security standpoint?
It demonstrates that underground sites like this can provide illegal services for years before being shut down.
The Silk Road was in operation for over three years before finally being seized earlier this week. The question now becomes – who or what will take the Silk Road’s place in the Internet underworld? Although this particular site is relatively well known, how many other sites provide similar services but maintain a low profile and slip under the radar?
How many of these sites are based outside of the US where they may not be subject to the strict regulations of this country?
Obviously, there are many other sites similar to the Silk Road offering every imaginable illegal service all in one place. Identity theft is a big one. It’s no secret that stolen identities are bought and sold daily through various channels.
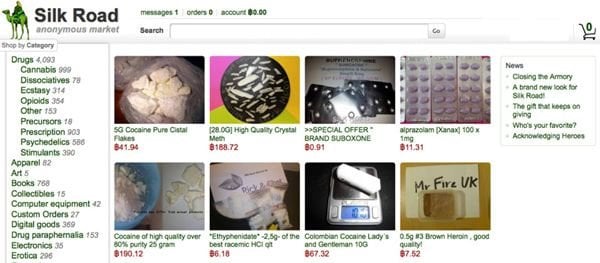
Often, these websites also rely on the Tor network for anonymity. With 2014 quickly approaching, it’s anyone’s guess as to what the next major black-market Internet retailer will look like. It’s inevitable that it will occur; in fact, it may already be happening at the time of this writing.
It goes to show that the Internet is not a safe place and will most likely become more dangerous in the months and years to come.
As always, a degree of vigilance is required every time your computer is connected to the Internet and websites like the Silk Road are a perfect example of why computer security is of the utmost importance.
Adobe Systems Breached
07.10.13
Adobe Systems is one of the largest and most successful software companies in the entire world. The company is responsible for creating the Adobe Creative Suite which includes programs such as Photoshop, Dreamweaver, Flash, and many others. Hackers have broken into major servers at the Adobe headquarters and stolen source code for an undetermined number of software titles including the ColdFusion web application platform and the Acrobat family of products. In addition, the company has reported that hackers also accessed almost 3 million customer credit card records and stole login information for an undetermined number of Adobe users.
The customers affected include customers of the increasingly popular Creative Cloud; a cloud-based version of the Creative Suite that offers users a monthly fee instead of the notoriously expensive price tag attached to the Creative Suite.
Adobe is advising all customers to immediately change their passwords and keep an eye on credit card statements.
The company states that all of the credit card information that was stolen was encrypted; however, Visa has already issued a warning to its customers about the potential fraud possibilities associated with this security breach. It appears that the hackers responsible for this attack are also responsible for hacking into large data aggregators such as LEXIS-NEXIS and Dun & Bradstreet.

That story was reported on this blog last month and remains a serious security concern for millions of people potentially affected by the security breach. These hackers were also responsible for breaching the secured networks at the National White Collar Crime Center; a congressionally funded nonprofit organization that provides training and investigative support to agencies involved in the prevention of cybercrime.
By Adobe’s own admission, the security breach occurred in mid-August 2013 and was not discovered as a potential threat by the company until the middle of September.
Adobe has not yet pinpointed exactly how significant the security breach was. Source code for additional software products was likely stolen as well. More information should be available within a few days about the extent of the attack. At this time, it appears that the breach was made possible by known security vulnerabilities in the ColdFusion platform. What’s ironic about this is that ColdFusion is an Adobe product and at first glance, it appears that Adobe’s own systems were not properly updated with patches released over the summer. Adobe is taking full responsibility for the cleanup effort and is in the process of notifying customers who may have been affected by this breach.
If you use any Adobe products currently, be sure to change all of your passwords immediately and keep an eye on your credit card statements for potentially fraudulent charges.
Once again, Adobe insists that all of the credit card information that was obtained is encrypted and useless to the hackers, but due diligence and time are the only ways to know for sure. Adobe already has critical security updates planned for Tuesday for both Adobe Acrobat and Adobe Reader, both of which were compromised during this attack.
Cash Skimming Devices Rising in Popularity
11.10.13
In terms of the risks faced by Internet users every day regarding around identity theft, most of the focus is on phishing sites and malware designed to log keystrokes from unsuspecting users. Powerful malware such as the Citadel banking Trojan have made headlines time and again as various hacking groups deploy the software and ultimately funnel millions of dollars away from bank accounts in the United States and around the world. There have always been other threats such as scam artists who deploy credit and debit card skimmers at ATM machines, but these events have never been as prominent as they are today. And it’s not just ATMs that are affected anymore either. Last weekend, the popular retail department store Nordstrom reported that it had found six inexpensive skimmer devices that had been discreetly affixed to cash registers at a store in Adventura, Florida.
The devices that were discovered can be purchased for approximately $30 apiece from a variety of online retailers.
Unlike traditional credit card skimmers that sit inside the magnetic card readers used in ATMs and department stores, these devices are hardware keyloggers designed to connect to PS/2 connectors typically reserved for wired keyboard and mouse peripheral hardware.
Although Nordstrom was quick to report the breach once it was discovered, the company has not yet released any information about how many customers might have been affected by this new scam. The local authorities reviewed closed-circuit camera footage and found three men who walked into the store. Two of the men worked to distract sales staff while the third took pictures of the register and even removed the rear access panel. Several hours later, three different men were also caught on closed-circuit cameras returning to the store.

Once again, two men distracted sales staff while the third person installed the hardware keylogger devices. The devices are designed to store all of the data collected until the criminals come back and physically retrieve the devices. In this case, it is possible that no credit card information was compromised; however, this scam has a very professional feel to it meaning that this is probably not the first time that such an event has been perpetrated by these individuals.
It’s worth noting that other devices can be purchased that perform the same tasks but offer criminals wireless access to the data for only a few dollars more per unit.
It seems that no matter how careful you are with your personal and financial information while shopping online there are some serious risks inherent to shopping in traditional brick-and-mortar stores as well. It can only be assumed that scams like this will continue to increase as the holiday season quickly approaches and criminals look for easy targets. Especially when most cashiers are not particularly computer savvy, the risk of this scam becoming a widespread success for criminals is extremely real.
The only way to combat this type of activity is to regularly monitor credit and debit card statements for any activity that appears fraudulent.
If any such activity is notice, contact your credit card company immediately to notify them of the problem.
Criminal Hackers Could Be Targeting Animals
12.10.13
Apparently people are not the only targets when it comes to hacking information for profit. The Internet has facilitated explosive growth in the wildlife trafficking niche and one of the latest exploits is targeting endangered tigers which can fetch as much as $50,000 a piece on the black market. Especially in many Asian countries, tiger parts are valued for their alleged medicinal value and criminals are quick to cash in. In fact, the World Wildlife Fund (WWF) estimates that the wildlife trafficking industry is worth approximately $10 billion per year. Officially known as cyber poaching, this latest attack occurred when a professional email account at the Panna Tiger Reserve in central India was hacked. This account contains the encrypted geographic location of a GPS collar Bengal tiger.
The collar is currently fitted to a 2 ½-year-old male Bengal tiger and includes both satellite and ground tracking capabilities. The collar is designed to provide GPS data every hour so researchers can track the exact movements and behavior patterns of the endangered species. With the price that this tiger would fetch on the black market, it’s no wonder hackers are attempting to breach these systems as well as many other systems around the world that specialize in endangered wildlife.
Although it is unclear whether this attack was directly aimed at obtaining the GPS details of the tiger’s whereabouts, with only 2,500 tigers left in the entire world, researchers do not want to take any chances.
As a result of this event, a team of researchers now stays within 1,600 feet of the tiger at all times in order to deter poachers. Early next year, conservationists at the reserve will also deploy surveillance drones and wireless sensors designed to detect human intrusions in the forest.

Researchers at the facility claim that the encrypted GPS data would be of no use to the hackers responsible, but encryptions are broken all the time and $50,000 is a good motivator for most criminals. This incident brings to light the fact that hackers will do almost anything to profit from technology.
As if stealing banking and credit card information from Internet users wasn’t enough, the fact that society relies so heavily on technology for practically everything means that it is easy for hackers to partake in potentially massive cyber poaching campaigns.
Let alone the money that can be earned by selling the animal once it has been successfully poached, just the information about where the animal can be found would be extremely valuable to poachers and is more likely to be the avenue taken by many hackers.
Either way, it appears that even endangered species are no longer safe from the prying eyes of hackers. In recent years, is been proven that many GPS systems are easily hacked.
Examples abound where students were able to “hijack” a million-dollar yacht by spoofing GPS signals or take over control of a GPS controlled drone using similar techniques. How long will it be before animals with GPS collars are prime targets for criminals who care more about earning money than the health and existence of an entire species? Hopefully, this event serves as a lesson to conservationists about the importance of proper IT security at their research facilities to protect these precious animals from extinction.
Simple Backdoor to Many Popular D-Link Routers
14.10.13
The hackers responsible for breaking into large computer networks usually get all the notoriety in the computer security world; however, there are quite a few hackers who spend their time working with embedded systems. Although it may not seem as glamorous on the surface, these individuals try to tweak wireless routers, set-top boxes, and other proprietary hardware/firmware combinations for fun, profit, and sometimes malicious activity. There have been many discussions about recent flaws discovered within embedded devices. Just last month, serious flaws in many popular consumer grade wireless routers allow hackers to access a root command line and make administrative changes from outside the LAN. There have been many other serious flaws as of late including a botnet that unlawfully mapped the entire Internet by jumping from router to router and taking measurements and a flaw that allows hackers to open up the administrative interface of the router to the Internet.
Other router flaws include vulnerabilities in Universal Plug and Play (UPnP) that could leave your router susceptible to attacks from the Internet. The latest threat to hit embedded devices is targeted at D-Link routers. Specifically, model numbers that are known to be affected include: DIR-100; DI-524; DI-524UP; DI-604S; DI-604UP; DI-604+; TM-G5240 It is likely that other modern D-Link routers are also affected by this vulnerability.

This vulnerability is so simple that it is almost comical that a relatively large router manufacturer would miss this grave security mistake.
Basically, if you browse to any page on the administration interface with your browser’s User Agent (UA) string set to a specific value, the router does not ask for a password. The string is:
xmlset_roodkcableoj28840ybtide
And spelled backwards this User Agent string is:
Edit by 04882 Joel: Backdoor
For those of you unfamiliar with User Agent strings, every HTTP request sent from your browser includes a text string that tells the Web server what type of device and web browser you are currently using. This allows the web server to serve content suitable for your device.
So by simply setting the User Agent string to the above line of text, the affected D-Link routers do not ask for an administrative password and the entire administrative interface is vulnerable.
It is worth noting that this flaw does not work from outside the LAN unless remote administration has been enabled in the settings. On all of the affected routers, this setting is turned off by default – meaning that the criminal would have to already be connected to the wireless network for this hack to work. Of course, if they do gain access from within the network, it is very easy to enable remote administration using this technique and gain access remotely in the future. The most unfortunate part about this flaw and the many other router flaws mentioned is that router manufacturers are not quick to fix these changes (if they do it at all).
The nature of embedded devices means that new firmware has to be flashed into the internal memory of the device – something that is often outside the comprehension and skill level of the average Internet user.
Furthermore, these changes would have to be made from within the administrative panel and many users are unlikely to check for available updates if they were offered anyway. As of this writing, D-Link has not stated whether they intend to fix this glaring hole or when a patch will be released if they do choose to correct the flaw.
Snapchat Openly Working with the Government
19.10.13
Snapchat has become a very popular photo sharing application with Android and iOS users. Basically, Snapchat works by sending recipients images from other users that can only be viewed for up to 10 seconds before they are “permanently” deleted from the device on which they were received. Snapchat has been relied on for many uses and has become especially known for sending lewd pictures to significant others because they are less likely to be saved and possibly shared via social media at a later date. Snapchat is also popular with criminals who wish to share information about illegal activities without the risk of photographs falling into the hands of law enforcement.
However, Snapchat admitted in its own blog on Monday that it has and will continue to hand over photos to US law enforcement agencies as requested.
This is yet another example of how unsafe your information can be once it leaves your house and travels the airways of the Internet.
Micah Shaffer, Snapchat’s Head of Trust and Safety, explained that there actually multiple ways to gain access to photos that supposedly disappear after only a few seconds. In addition to forensic examination of the handset that has received a snap, Snapchat also possesses an in-house tool that allows them to grab photographs as they pass through Snapchat servers.

These photographs can then be handed over to law enforcement officials very easily. The blog posting also made it very clear that Snapchat reserves the right to hold onto some photographs for longer periods of time in cases where law enforcement has shown interest in a particular target but has not formally filed a request for information. Many users of Snapchat realized months ago that the photographs do not really disappear forever. There are multiple ways to record the images including taking a screenshot and digging through the file system of the mobile device.
However, this blatant admission from Snapchat means that the government is not only monitoring your email and phone accounts, but your photographs as well.
In Snapchat’s defense, the company is very open about their policies and cites the Electronic Communications Privacy Act as the reason for divulging information to authorities. Internally, Snapchat claims that only two people have access to the in-house tool capable of retrieving old snaps.
The point here is to realize that nothing sent electronically is safe from prying eyes.
Whether it’s the government, local law enforcement, or an ex with a chip on their shoulder, Snapchat is no safer than sending the same picture via normal text message. Remember not to share anything that you would not want others to see beside your intended recipient. Snapchat’s frankness about policies relating to collaboration with law enforcement almost begs the question about how much information is really being shared. In the wake of ongoing disputes between the government and search engine giant Google about similar privacy issues, it seems odd that a popular social media platform such as Snapchat would be so willing to cooperate when so many other companies are not. The moral of the story – be careful what you send via Snapchat because it is not nearly as secure as the company would like you to think.
Even the Credit Bureaus are Working with Identity Thieves
24.10.13
For those who are not familiar with credit reporting in the United States, the task is handled primarily by three agencies: Experian, Trans Union, and Equifax. In a recent investigation, it was reported that Experian sold sensitive personal information about millions of consumers to an identity theft service based in Vietnam. The illicit site, known as hxxp://Superget.info, is an underground service marketing the ability to look up full Social Security numbers, birthdays, driver’s license information, and financial records on millions of Americans. Registration for this service is free and searches are funded using virtual currencies including Bitcoin and WebMoney; currency that is notoriously used for cybercrime. In Experian’s defense, the data was actually sold to the identity theft website via Court Ventures, a third-party company that was acquired by Experian in March 2012. This company had full access to all of Experian’s records and sold them to other information companies including US Search Info.
A few months ago, the US Secret Service began investigating Experian and obtained a grand jury subpoena against the company. When it was first discovered that the fraudulent information was being obtained via Court Ventures, the Secret Service contacted this company as well.
The reason Experian is held liable in this case is that even after exercising due diligence prior to purchasing Court Ventures, the company made the acquisition anyway.
On a monthly basis, Court Ventures was receiving wire transfers from a bank in Singapore that were supposedly from a US-based private investigator acquiring these records on behalf of customers. The criminal is in fact a Vietnamese national known as Hieu Minh Ngo. This individual is an active Vietnamese hacker who has openly advertised his site via underground hacking forums and has gained notoriety in the past for defacing websites including that of the University of New Zealand.
Just last week, the US District Court indicted Ngo for these electronic crimes. The indictment specifies that the hxxp://superget.info service sold “fulls.” This is a slang term used by cyber criminals to describe an entire identity theft package typically including an individual’s name, address, Social Security number, date of birth, place of work, duration of work, state driver’s license number, mother’s maiden name, bank account numbers, bank routing numbers, email accounts, and other account passwords.
This is widely considered to be the “holy grail” for identity thieves as it includes practically all of the information needed to completely hijack an individual’s identity and open new lines of credit in that victim’s name.
According to the indictment, the website was responsible for selling over 500,000 unique records to customers around the world. In an official statement, Experian denied any prior knowledge of the breach and has reportedly worked closely with law enforcement since this scam has been uncovered. However, for a company charged with collecting (and protecting) the most personal details of every US consumer, it seems that security efforts fell far short in this instance. Only time will tell exactly how many of the identity theft related scams discussed on this website have been directly related to Ngo and the hxxp://superget.info scam that is just now being uncovered after years of clandestine operation.
As always, remaining vigilant about your identity and financial information is the only real way to protect against these scams.
Victims affected by this scam did nothing wrong other than have their information collected by one of the major credit reporting agencies – only to have their identity compromised for profit.
Spyware Comes Standard with Some Computer Systems
26.10.13
As the economy continues to rumble at a rough idle without moving much since 2008, many people have turned to alternative financing for many large purchases. Computers are at the top of this list and are big business for rent-to-own companies throughout the country. The two largest names in rent-to-own nationwide are Aaron’s and Rent-A-Center; however, there are also many online-only companies that sell computers using a rent to own payment model (sometimes referred to as a lease). Aaron’s recently settled with the Federal Trade Commission after coming under fire from consumers about software being installed on new machines before being rented to customers. This spyware was knowingly installed at the corporate level and used in franchises nationwide to track customer location, take photos with the computer webcam, and activate keyloggers that were able to capture login credentials for everything from email to social media to banking sites.
Some of the images caught by the remotely activated webcams included “adults engaging in intimate activities,” according to the official FTC report. Under the terms of the FTC settlement agreement, Aaron’s is prohibited from using any monitoring software that captures keystrokes, takes photos, or records sound. The company must also get customer consent before using location tracking software on rented computers.
Unfortunately, this rent-to-own company is only one of eight large franchises that have been accused of using a program called “Detective Mode.”
In addition to the spyware features mentioned above, this software also prompts users to enter personal information via fake software registration screens.
This information is collected to locate a computer in the event that a customer does not pay on the agreed-upon schedule. The bigger concern here is that even legitimate companies are now resorting to spyware tactics against consumers. The average consumer is completely unaware of this type of spyware or its widespread use throughout corporate America. As if the threats from unscrupulous hackers aren’t enough, it seems like Americans also need to be concerned with the companies they do business with. News of this story comes on the heels of recent reports of the FBI using spyware for monitoring Internet traffic in a similar manner to that performed by Aaron’s.
In addition to the FTC settlement, Aaron’s is also in the process of settling a lawsuit filed by consumers affected by this blatant privacy violation.
Obviously, computers are especially vulnerable to this type of spyware compared to other high-end electronic items.
However, as more TVs emerge on the marketplace with integrated webcams and Internet connectivity, it seems that these are also a likely source of future spyware campaigns.
If you or anyone you know has used Aaron’s, Rent-A-Center, or any other rent-to-own company for a recent computer purchase, it is advisable to completely reinstall Windows and erase any traces of Detective Mode or similar spyware programs as soon as possible (the software remains even after the purchase has been paid off).
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion