News Archive December 2013
Monthly Cyber Security News Archive: December 2013 Summary
Table of contents:
- Bitcoin Malware - Capitalizing on the Boom
- Think Your Computer is Safe?
- Password Security Still a Big Problem
- Target Customers at Risk for Fraud
- Botnet Uses Firefox to Hack Websites
- The NSA is Still Spying on Citizens
Bitcoin Malware - Capitalizing on the Boom
11.12.13
Bitcoins have become an extremely hot topic. Financial news channels can’t stop talking about the rise of value in Bitcoins. Just last week, Bitcoins went over $1,000 USD each (although it has dropped since then). This blog has been discussing the rise of Bitcoins for even longer. For a couple of years, Bitcoins have been the preferred currency of international criminals around the world. The Silk Road, a notorious drug trafficking website that was shut down by the FBI recently, relied heavily on the exchange of Bitcoins for transactions ranging from drugs to prostitution to murder-for-hire. Many Russian crime syndicates also rely on the anonymity provided by this digital currency. So, it should come as no surprise that criminals are beginning to capitalize on the Bitcoin craze.
Since Bitcoins are a digital currency that has to be generated by calculating complex mathematical equations, some people have started wondering if they to can join the highly competitive (but extremely lucrative) Bitcoin generation business. There are quite a few websites, YouTube videos and other online resources offering “free” Bitcoin generation programs. Some of them require downloading a specific file that is pumped full of malware while others force would-be Bitcoin miners to complete countless surveys in the hopes of downloading a file that never arrives.
Another popular tactic is to offer visitors a download link to a program that earns them Bitcoins by filling in CAPTCHA codes on various websites.
The program, is in fact, another version of this malware in disguise. Still others force users to purchase a premium download license from multiple file-sharing sites. The end result is an expensive download designed to takeover your computer. Researchers have proven that the application creates connections with servers in China, the United States and Vietnam.
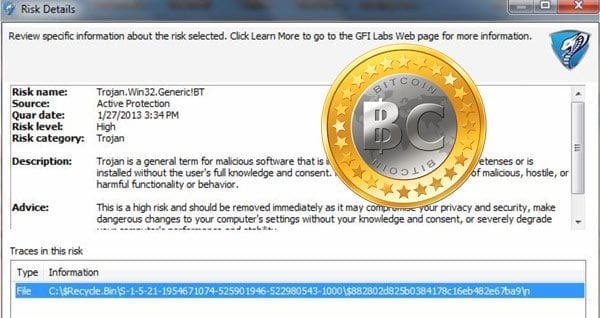
The program also includes a registry entry that allows it to start with the computer as well as multiple other behaviors commonly associated with malware. The malware has been identified as Trojan.Win32.Generic!BT. Currently, researchers are unsure of the purpose of the malware as many of its features seem to be deactivated. There is no doubt, however, that the hackers behind this malware deployment have financial gain on their minds - it is only a matter of time before the infrastructure is available to create a massive botnet using this increasingly popular malware attack.
The fact that Bitcoins are receiving mainstream media attention across multiple platforms has certainly added to the awareness of the Bitcoin as a virtual currency alternative.
Many people are trying to break into this market. As a result, this latest malware variant is likely to become a more prominent player in the global underworld as 2014 quickly approaches.
As usual, protection from this attack comes from not downloading software from unknown sources and vigilantly monitoring your computer for suspicious activity.
Remember that although Bitcoin mining seems lucrative, the equipment required to generate Bitcoins successfully (i.e. large, powerful servers) are outside the reach of most aspiring entrepreneurs.
Think Your Computer is Safe?
14.12.13
You may think your computer is safe because you have the latest antivirus software, all required operating system patches and a relatively strong understanding of Internet best practices. Until recently, this would probably be enough to protect your computer from most threats; however, a new threat has been successfully created that could change the rules completely. A lab-created proof of concept was recently documented in the Journal of Communications that proves computers can communicate without wires or wireless networks. In fact, this software makes it possible for hackers to control a computer that is not connected to the network at all. Using a pair of Lenovo speakers with built-in microphones, researchers discovered a way to transmit data up to 65 feet to other computers. The technology relies on sound waves and software that was originally created for underwater communications systems. High frequency signals are transmitted from the host computer.
These signals are received via the microphone of another machine which can carry out the instructions, pass them onto yet another machine...or both. This threat could reach even the most secure networks components - including servers traditionally hidden behind complex security protocols and hardware firewalls. The implications of a product like this include powerful hacking communities developing a similar threat. There would be very little, if anything, capable of stopping these criminals from accessing the most critical government and business information in the world.
The range of the threat can be extended indefinitely by connecting a relay system of infected computers - the reach of this threat seems to be limitless.
Currently, the technology is only capable of transmitting data at 20bps (extremely slow), but researchers say this is enough bandwidth to enable keyloggers or other forms of malware to be controlled without a physical network connection.

What’s especially disturbing about this new threat is that current antivirus technology isn’t equipped to deal with threats that originate this way.
Without warning, your computer could literally be controlled remotely by an infected computer next door or by a hacker sitting in a parked car in front of your house.
There is simply not a security infrastructure in place that can deal with acoustic threats - which is what makes this new threat so concerning. As of this writing, there is no known way to block this threat. Researchers are discussing ways to protect against potential variants of this malware threat, including a host-based intrusion detection system capable of analyzing audio signals.
The reality of this new security technology becoming a mainstream product any time in the next few years is unlikely, but eventually, antivirus manufacturers will be forced to address this new threat and its widespread implications.
Until that time, there is little you can do to protect yourself from this threat. Although widespread deployment is certainly a possibility, the expensive of implementing this technology makes high-profile, valuable targets much more likely. At some point, however, the source code to this threat could be leaked as Citadel and Zeus before it. That’s when you really need to wonder if your computer is actually safe after all.
Password Security Still a Big Problem
17.12.13
As often as most people hear about the importance of secure passwords, it appears that weak passwords are still predominant in most of corporate America. This is evidenced by a new threat that has been identified as a marketplace for stolen Remote Desktop Protocol (RDP) credentials. For those unfamiliar, RDP is a tool built into Windows machines that allows for remote access of the entire desktop and any attached hardware. This software is used extensively by large corporations and by businesses that outsource some or all of their IT needs. RDP allow technicians to troubleshoot a system remotely simply by entering the proper username and password combination. RDP is also used increasingly by employees participating in Bring Your Own Device (BYOD) programs. A secure RDP connection allows employees to access work programs and resources using another computer or even a tablet.
Unfortunately, a website has been identified that sells secure RDP login credentials to the highest bidder. The underground site known as hxxt://makost.net currently has over 6,000 secure RDP credentials for sale. The price varies based on the perceived value of the username and password combination being sold. For instance, an administrative account at a large company is worth a lot more than a basic user account at a small company.
Some of the industries affected by this breach include large educational and healthcare providers, government agencies and multiple technology firms.
Preliminary reports suggest that the hackers responsible for the theft and subsequent sale of this information simply scan large blocks of Internet IP addresses looking for computers that respond to requests on common RDP ports (such as 3389). Once target IPs have been located, the hackers only need to figure out the username and password combination to gain full access to the remote machine. This is probably the easiest part for these criminals because people use such poor passwords.
In many cases, the password is the same as the username - sometimes even for administrative accounts.
All the hackers needed to do was identify valid usernames and use the same text value for the password. This is bad password management at its worst and it has been responsible for countless instances of fraud.
Security experts have identified multiple clients of hxxp://makost.net who were spending thousands of dollars purchasing these hijacked RDP accounts. One customer of the service has purchased over 400 unique RDP accounts in just the last six months.
In the wrong hands, a hijacked RDP connection is extremely dangerous because the user has complete control of the computer as if they were sitting in front of it.
Although RDP is included in almost every Windows release, it is usually turned off by default on home computers. This eliminates your PC as a potential target, but if you use a computer at work, it could be susceptible to this scam. The moral of the story is password security.
Please make sure you use secure passwords that are at least 8 characters in length.
Use special characters whenever possible and make the password something that is not easily guessed. This will keep hxxp://makost.net and other hacker sites from hijacking your information and selling it to the highest-bidding criminal.
Target Customers at Risk for Fraud
18.12.13
If you shopped in a Target store in the United States between November 27th and December 15th of this year, your credit card information has probably been compromised. The large retailer just announced that its database was hacked and the criminals made off with personal financial information for over 40 million customers. In a public statement, Target acknowledged the security threat and stated that the names, credit card numbers, expiration dates and three digit security codes were stolen from a database that stored this payment information. This breach affects all customers who shopped in a physical Target location in the United States during the aforementioned time frame. The data stolen included all payments received during the Black Friday shopping period; one of the busiest times of the year for Target.
Customers in Canada and those who made purchases online are not affected by this breach. At this time, Target has not stated how the hackers were able to gain access to the system, but it seems reminiscent of the CardSystems and TJX breaches perpetrated by Albert Gonzalez. Collectively, these two breaches were responsible for compromising well over 100 million credit and debit card numbers and resulted in millions of dollars in fraudulent charges.
Although Target does not know who is responsible for this attack, they have hired a private forensics firm to track the criminals.
Law enforcement officials are actively tracking these criminals as well. The tactics appear to be similar to that used of Gonzalez and his fellow hackers known as Shadowcrew.

Even though Gonzalez is in prison, could Shadowcrew have new leadership and be responsible for this costly attack as well? At this point it is unclear, but the stolen information was not encrypted and could be used for illegal purposes almost immediately.
Target is advising Redcard (an in-store credit card) card holders to contact Target Customer Service directly if they notice any unusual charges. All other customers should contact their credit or debit card issuer with any unusual charges or suspicious activity.
Target has publicly declared its network safe following the attack. Whatever exploit was used to access the database has apparently been patched and Target urges customers to continue shopping with confidence at Target stores. This, of course, comes at the most critical time of the year for the retail giant. If you have shopped at any Target store within the last month, keep an eye on your financial statements and remember that debit cards often do not have the same protections afforded to credit card customers.
At the first sign of any suspicious activity, notify your card issuer or bank immediately.
Law enforcement officials are expected to work with credit card issuers to flag accounts that may have been compromised in an effort to mitigate the potential expense of this incident.
Botnet Uses Firefox to Hack Websites
20.12.13
If you use Mozilla Firefox as your web browser of choice, your computer could be helping to perform SQL injection attacks on websites around the world. An unusual botnet has been discovered that has infected at least 12,500 computers running the popular web browser. Known as Advanced Power, this botnet is disguised to look like a Microsoft .NET Framework Assistant update for the Firefox browser. This Firefox plugin looks completely legitimate and until recently was available through the Firefox plug-in repository. Antivirus software is unable to the detect this threat because it installs without any of the typical behaviors associated with most malware. Although the threat was only discovered recently, it is estimated that the attack began in May of this year and has quietly been helping hackers discover vulnerable websites while infected computers are browsing the Internet.
For those unfamiliar, a SQL injection attack is a method hackers use to access the contents of databases held by web servers.
By adding certain characters to the end of a web page URL using the PHP programming language, hackers can locate websites not protected from these dangerous SQL attacks.
A successful SQL injection attack can provide hackers with personal customer information or even be used as a way to establish a drive-by download malware attack (infecting vulnerable computers as they visit the compromised site).
The process of locating vulnerable sites can be time-consuming, but the release of Advanced Power makes the task much easier for potential criminals. As infected computers browse the web, each visited web page is discreetly tested for a variety of SQL vulnerabilities without the knowledge of the user. This type of attack is unique because it does not adversely affect the performance of the machine; making it nearly impossible to detect and providing hackers with information that would normally take months or even years to discover using traditional methods to uncover vulnerable web servers. SQL injection attacks are big business for hackers around the world.
A recent study reported that most web sites are attacked by various SQL injection techniques at least four times each month. Some web sites (especially Web retailers) are constantly under attack as the databases held by these retailers often contain customer payment information with a high resale value in the hacking underground.
At this point, it is unclear whether the information gained from this malware release has been used to exploit any specific websites; however, the increased popularity of SQL injection attacks makes it very probable that the hackers responsible for Advanced Power have had some success using this discreet but dangerous malware variant.
Firefox recently announced that the fake Firefox add-on has been removed from its repository and blocked. Users of the Firefox browser shouldn’t need to do anything as the browser checks in for security updates every day automatically. Unfortunately, there could be many similar versions of this software circulating under various names. This attack is likely only the “tip of the iceberg” as hackers continue to look for discreet ways to mine data autonomously. As usual, do not download anything you are unfamiliar with including updates that seem suspicious or unnecessary.
The NSA is Still Spying on Citizens
23.12.13
As if the NSA hasn’t received enough heat for allegedly spying on American citizens, new evidence has been revealed that shows just how far the US Government is willing to go in its effort to spy on the public. RSA is a leading security and encryption company responsible for developing many important security algorithms for use in residential and commercial settings. One of these products, known as Bsafe, is used to enhance the security of PCs and many other electronic products. In yet another report released by NSA whistleblower Edward Snowden, it is apparent that the NSA secretly paid RSA $10 million to intentionally leave a couple of backdoors in the Bsafe security algorithm. This would allow the NSA to access encrypted files quickly without a court-order or specialized code-breaking hardware.
Not only did RSA accept the $10 million payment, but the company ultimately became one of the biggest distributors of the product over a period of several years. RSA is now owned by EMC Corp, a computer storage company.
Spokespeople from both companies have advised customers to stop using Bsafe in light of this leak and claims that RSA had no knowledge that the algorithm provided by the NSA could be used to spy on American citizens.
Instead, RSA claims that they were paid by the NSA simply to use an encryption algorithm designed by the NSA. The NSA declined to comment on this latest leak. Regardless of where the truth lies, this information points to an alarming trend that has been going on for years. The NSA has been focusing on systematic erosion of security protocols for years and most likely continues to operate along a similar plan. Even encryption software designed to protect the privacy of communications has been tainted by the NSA in its quest for information obtained both legally and illegally. Leaked NSA documents confirm that the government agency has conspired to use “commercial relationships” as a way to further its reach.

Although RSA was not specifically mentioned in these leaked documents, RSA has already publicly admitted to its involvement and to receiving payment directly from the NSA for the addition of intentional security loopholes. This information comes at a time when privacy has never been more important to consumers and businesses alike.
Some of the products in your home probably use RSA public key encryption technology; software that has been licensed to major electronics manufacturers around the world.
Unfortunately, there is not enough information available at this time to confirm the extent of this NSA activity, but it is sure to be significant once all the information becomes available (if it ever does). It is unfortunate to see large businesses working with the NSA in this capacity. The government constantly submits information requests to major Internet companies like Google, Yahoo! and Facebook - hopefully these companies do not comply with the NSA’s far-reaching policies as RSA did or there will be nothing safe from the prying eyes of government in the near future. No matter how or why you use the Internet, assume your communications are being intercepted and read by the United States Government in the name of “national security.”
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion