News Archive November 2014
Monthly Cyber Security News Archive: November 2014 Summary
Table of contents:
- Is Rogue Antivirus Malware Making a Comeback?
- BlackEnergy Plugins Target Assorted Devices including PCs
- Dridex Malware Using a Decade Old Trick to Infect PCs
- Silk Road 2.0 Taken Down by FBI Almost Exactly One Year After the Original Silk Road Was Dismantled
- CoinVault Ransomware Offers Interesting Feature
- Darkhotel Malware Targets Corporate Executives Using Hotel WiFi
Is Rogue Antivirus Malware Making a Comeback?
02.11.14
As crypto-malware continues to be the preferred attack method for many cyber criminal organizations as of late, it begs the question of “What happened to malware variants that were prevalent just a few months ago?” One of the malware techniques thought to have fallen by the wayside is rogue antivirus malware. Just a few months ago, these scams were very popular among hacking groups large and small because they represented a relatively easy way to extort money from victims. In case you are unfamiliar with these types of scams, rogue antivirus software is a form of malware whereby the victim is constantly bombarded with warnings about viruses that have been detected on the machine.
In many instances, the infected machine becomes practically unusable as the rogue antivirus software is designed to block most programs from opening under the guise that the files have been infected with some unknown threat. The point is that rogue antivirus scams haven’t disappeared at all. In fact, a fake antivirus program, known as Rango, was recently observed in the wild. Why would hackers continue to rely on what many security experts believe is an antiquated malware technique? Simple. It still works.
Recently, security experts have observed the Asprox botnet spreading via spam email campaigns. These emails often appear to be a WhatsApp (a popular instant messaging service) voicemail notification. Included in these spam emails are multiple attachments that contain Kuluoz - a known downloader for Asprox.
Asprox is a malware payload dropper and, in this case, the payload is Rango - a rogue antivirus malware variant previously identified as part of the Fakerean family of rogue AV malware. Once Rango has been installed, the malware purports to be an authorized Windows application that even includes the current OS to make it seem more legitimate. The idea behind Rango - and most other rogue AV malware variants for that matter - is to coerce victims into paying for an unnecessary antivirus solution.
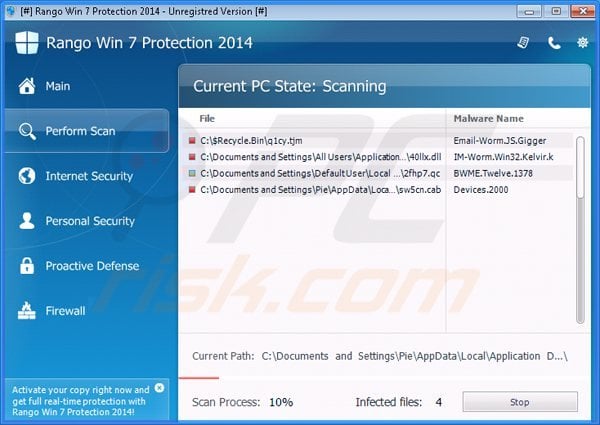
Although providing payment information will cause Rango to become dormant, most victims soon fall victim to credit card fraud as their personal financial information is sent directly to the cyber criminal organization responsible for disseminating the attack in the first place. Rango is so sophisticated that it even replicates a Windows Action Screen to further the illusion that this malware is a legitimate program. To the average PC user, the warnings seem real enough that many victims are entering credit card information as a way to “clear” the PC of infection.
It does appear that Rango becomes inactive after the victim makes payment, but once the cybercriminals behind the attack receive the payment information, it becomes anyone’s guess as to what is done with that information.
Protecting yourself from this threat is as simple as keeping real antivirus software properly updated as most modern solutions detect Rango and the droppers used to spread the malware. If your PC does become infected with Rango, do not enter payment information. Although payment will keep Rango at bay, your payment information will most likely be compromised as a result of this attack.
BlackEnergy Plugins Target Assorted Devices including PCs
12.11.14
A cyberespionage group was recently discovered that has been deploying a version of the notorious BlackEnergy cybercrime tool. The group behind this campaign — which has still not been identified — is currently targeting routers and Linux systems based on the ARM and MIPS architecture. Windows machines are also being targeted by the group using a variety of readily-available plugins designed to make BlackEnergy even more powerful.
BlackEnergy was originally created and used by cybercriminals as a way to launch distributed denial of service (DDoS) attacks. Variants of commonly available plugins used to increase the functionality of BlackEnergy were discovered that specifically target both Windows and Linux systems. These plugins add functionality including port scanning, password stealing, digital certificate theft, hard drive wiping, remote desktop connectivity and general system information gathering.
In one recent attack, a BlackEnergy plugin known as dstr destroyed the data on hundreds of Windows computers at a compromised organization. It appears the hackers intentionally activated this plugin once they had been discovered as a way to hide the true purpose of the network breach.
Similarly, another company discovered that data had been corrupted on multiple PCs and the organization could no longer access its Cisco routers using telnet. Eventually, IT experts were able to access the routers and found multiple scripts left by BlackEnergy. These scripts were apparently left over has the hackers tried to remove all traces of what they were actually doing within the network, but researchers were able to find one script called “Cisc0 API Tcl extension for B1ack En3rgy b0t.”

So far, this group seems to be targeting organizations that operate industrial control systems — especially organizations within the energy sector. Targets that have already been compromised include power facilities, construction companies, energy sector investors and power generation operators. The exact plugins used are customized via commands sent from a remote command and control server. This allows the hackers behind this attack to change the plugins used depending on the victim’s system.
Although the connection has not been confirmed yet, many experts believe the group responsible for this attack are the same people responsible for another recently discovered cyber espionage campaign that has been dubbed Sandworm.
Whether or not these attacks are connected is unclear, but what is known is that both attacks originated in Russia like so many other cybercrime campaigns as of late. While this string of attacks mostly targets large organizations for unknown information gathering purposes, the fact that these newly released BlackEnergy plugins are capable of targeting Windows machines as well as many popular wireless routers, it’s not really a stretch to think of BlackEnergy being used to target individuals in the future. Many of the attacks thus far have relied on zero-day exploits to inject malware into the system. The best way to protect yourself from this threat is to ensure all OS updates are installed immediately. You should also check the firmware version of your router and install any security updates as they become available.
Dridex Malware Using a Decade Old Trick to Infect PCs
14.11.14
Many of the recent threats reported by this blog target the banking information of unsuspecting victims once a Trojan specifically designed to steal the login credentials of these victims has been installed on the PC. Most of these attacks use modern techniques such as drive-by downloads and other exploits that capitalize on known vulnerabilities in Windows as well as popular browser plugins including Flash, Java and Microsoft Silverlight. Now, rewind about 10 years. At that time, the most common way for a hacker to install malicious code on a system was by using macros embedded within Microsoft Office documents.
This technique stopped being an effective way to distribute malware primarily because Microsoft increased OS security as it pertains to dealing with macros. In fact, macros are turned off by default in most current Windows installations. That said, there are legitimate uses for macros in some cases and many times, these machines have macros turned on by default. This circumvents any security measures designed to protect the machine from running arbitrary code hidden within a macro. This is why Dridex has been rather successful — especially considering the age of the exploitation technique being leveraged in this malware campaign.
Dridex works by embedding itself within a Microsoft Word document. If macros are already enabled in the target system, Dridex immediately installs itself without notifying the victim.
If macros are not enabled by default, the Word document prompts the victim to enable macros before continuing. In both cases, Dridex is installed and begins monitoring Internet traffic as it waits for the victim to navigate to any one of numerous bank URLs hardcoded into the malware. Although many of the financial institutions hardcoded into Dridex are European Union specific, some American banks are also on the list.
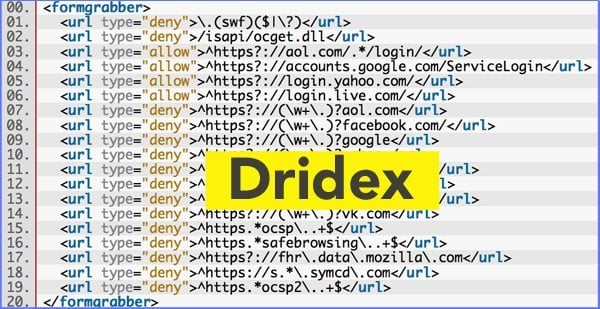
Once the malware has detected one of these sites, Dridex jumps into action. Essentially, the program is designed to inject additional HTML fields into legitimate online banking transactions. These extra fields ask victims to input additional personal information — information including social security numbers — which the legitimate financial institution already has and would never ask via an HTML form in the first place. Unfortunately, many people are unaware of the security risks associated with Dridex (or its predecessor, Cridex) and input the additional information without realizing the consequences in doing so.
It’s worth noting that although most of the financial institutions targeted by Dridex are hard coded; however, security experts have discovered a large network of command and control servers that could send additional instructions to infected machines at any time.
This means the probability of a large-scale attack focusing on US-based banks could happen any day if the hackers responsible for this campaign were so inclined. Dridex is spread almost exclusively via spam email at this time. The best way to defend your PC from this threat is to avoid opening any unsolicited email attachments. If you do not use macros for anything, take a moment to ensure macros are disabled by default and as always, keep Windows and your antivirus solution of choice updated at all times.
Silk Road 2.0 Taken Down by FBI Almost Exactly One Year After the Original Silk Road Was Dismantled
19.11.14
A San Francisco man was arrested earlier this week after it was discovered that he was responsible for operating the second iteration of the notorious Silk Road. For those readers unfamiliar with the Silk Road, it was an underground website only accessible via the supposedly anonymous Tor network. Originally run by Ross William Ulbricht (aka Dread Pirate Roberts), the Silk Road became synonymous with online black market dealings including the sale of illicit drugs, stolen credit card numbers and a host of other nefarious activities.
The original site was taken by through a joint effort between the FBI, Interpol and a few other organizations and Ulbricht is currently facing serious charges including conspiracy to commit computer hacking, money laundering and drug trafficking among others. Approximately one month after the original Silk Road was disbanded, a new version entitled Silk Road 2.0 went live.
Run by Blake Benthall (aka Defcon), Silk Road 2.0 was making as much as $8 million USD per month and had as many as 150,000 active users at any given time.
According to the official indictment, Benthall has been operating Silk Road 2.0 since December of 2013 and has made an estimated $400,000 per month since as a middle-man between cybercriminals and potential customers. Although Benthall’s history before becoming the new owner of the Silk Road is still unclear, social media profiles for Benthall indicate that he may have been employed by numerous technology companies in various roles before turning to the Silk Road as a sole source of income. As of October 17, 2014, the Silk Road 2.0 contained over 13,000 listings for controlled substances. The site also openly advertised fraudulent documents and computer hacking services.

Like the original Silk Road, the site was only accessible via the Tor network — although this takedown seems to point to a serious privacy breach within the Tor network that allows the government to monitor traffic despite Tor’s claims to the contrary. While the exact circumstances of the bust are still under investigation, the takedown of Silk Road 2.0 carries a striking resemblance to the “shady” circumstances under which Ulbricht was arrested last year. In other words, it isn’t entirely clear if the government was within their legal rights to take down the site in the manner in which it did.
According to the indictment, Silk Road 2.0 was traced back to the San Francisco resident (Benthall) because he used a personal email address when registering one of the servers used to host his version of the site.
While the takedown of Silk Road 2.0 certainly makes it harder for hackers to sell stolen information, this incident should serve as a reminder that there really is no such thing as Internet privacy anymore. Many people even think the Tor network has been infiltrated by US government agencies looking for exactly this type of activity — and perhaps more importantly, anything else you do online too.
CoinVault Ransomware Offers Interesting Feature
26.11.14
A new form of ransomware apparently from the same family as the notorious Cryptographic Locker has recently been discovered. Known as CoinVault, this malware works in a fashion similar to ransomware this blog has covered in the past. Specifically, the hackers demand payment in Bitcoins, the ransom goes up at set intervals (usually every 24 hours) and the GUI is almost identical. Once infected with CoinVault, the malware creates a system registry value called Vault which is set to run on startup. Once active, the malware scans all drives looking for and encrypting all data files it finds.
The path to each file is has encrypted is stored in a separate file called %Temp%\CoinVaultFileList.txt. This file is later called upon when the victim clicks on a link with the GUI that shows a list of all files that have been encrypted as a result of this infection.
The file types targeted by CoinVault include:
.odt, .ods, .odp, .odm, .odc, .odb, .doc, .docx, .docm, .wps, .xls, .xlsx, .xlsm, .xlsb, .xlk, .ppt, .pptx, .pptm, .mdb, .accdb, .pst, .dwg, .dxf, .dxg, .wpd, .rtf, .wb2, .mdf, .dbf, .psd, .pdd, .pdf, .eps, .ai, .indd, .cdr, .dng,3fr, .arw, .srf, .sr2, .mp3, .bay, .crw, .cr2,.dcr, .kdc, .erf, .mef, .mrw, .nef, .nrw, .orf, .raf, .raw, .rwl, .rw2, .r3d, .ptx, .pef, .srw, .x3f, .lnk, .der, .cer, .crt, .pem, .pfx,.p12, .p7b, .p7c, .jpg, .png, .jfif, .jpeg, .gif, .bmp, .exif, .txt, .zip, .rar, .mp4, .iso
Once all data files have been encrypted, the malware displays a GUI that explains in detail how the victim can get access to their files once again. Typically, this involves paying a ransom in Bitcoins which starts at 0.7 Bitcoins the first day and increases each day the victim does not pay.
Unlike other ransomware programs, CoinVault does not rely on a separate decryption site. All decryption and payment processing duties are handled within the program itself.
Perhaps the most interesting part of CoinVault which sets it apart from many other ransomware variations is that the GUI actually allows the victim to decrypt one file for free.

Almost like a gesture of goodwill, this simple addition has made CoinVault much more successful than some other ransomware variants. CoinVault is extremely difficult to remove once installed because it is designed to kill almost every executable file a victim may attempt to run against the malware. Although it may be difficult to remove, it is not impossible and most modern antivirus solutions will recognize CoinVault heuristically before it can even install itself.
There is some good news if your machine becomes infected with CoinVault. This malware does not encrypt data securely and it does not wipe Shadow Volumes. This means that a standard file recovery tool can be used to undelete files.
Files can also be restored using a program such as Shadow Explorer. In other words, if you fall victim to CoinVault, do not pay the ransom. There are other ways to save your data and remove the malware without paying criminals using Bitcoins. Computer users who are dealing with this ransomware virus should use the CoinVault removal guide to eliminate it and restore their encrypted files.
Darkhotel Malware Targets Corporate Executives Using Hotel WiFi
29.11.14
A new malware campaign was recently discovered that has been targeting corporate executives using hotel WiFi in Asian hotels. According to security experts, this campaign — dubbed Darkhotel — has been ongoing for at least four years meaning the number of potential victims or the sensitive information that has been stolen from their computers is difficult, if not impossible, to estimate at this time. It appears that most Darkhotel attacks are occurring in Japan, Taiwan, China, Russia and South Korea with United States and Asian top executives the primary targets in most cases.
Darkhotel works when the intended victim checks into his or her hotel room and signs into the complimentary WiFi service (usually using a combination of last name and room number). It’s important to realize that the hotel’s network has already been compromised by hackers at this time. When the target logs into the WiFi network, hackers are quickly able to locate the user. At this time, hackers attempt to trick the victim into downloading and installing a backdoor which purports to be an update for legitimate software. Examples seen in the wild include Google Toolbar, Windows Messenger and Adobe Flash.
Once this “hotel welcome package” has been downloaded, the real payload - Darkhotel’s back door - is installed and the hackers have complete control of the infected machine. Once Darkhotel has been successfully installed, the hackers have free reign to install an assortment of malware tools from keyloggers to Trojans to password crackers.
Since Darkhotel only targets high-level executives, it’s purpose appears to be gaining access to corporate networks and/or stealing sensitive corporate information stored locally on the infected computer. What makes Darkhotel especially dangerous is that once the attack is completed all traces of malware are removed from the system.

This is why Darkhotel was able to stay under the radar for so long without detection. Furthermore, it appears that recently the hackers behind this campaign have been installing Darkhotel on non-executive targets as well. Security experts surmise that this move is a way to make the true targets of the attack less noticeable and these compromised computers can also be used for other tasks such as DDoS attacks and similar botnet-like activities. The report released by Kaspersky Labs about Darkhotel did not specify which companies have been targeted by this campaign but it is clear that the victims come from a wide range of industries including electronics manufacturers, pharmaceutical companies and large non-governmental organizations.
Even though approximately 90% of all discovered infections occurred in the countries previously listed, Darkhotel has also been spotted in the United States, Singapore, the United Arab Emirates, the Philippines, India, Germany, Ireland, Greece and Italy among others. The best way to protect yourself from Darkhotel is to refrain from downloading any “updates” on non-private networks.
This holds true for hotels as well as other public places such as libraries, coffee shops, etc. These updates are more often than not designed to install a malicious payload once clicked on. These payloads could include Darkhotel or any other backdoor program designed to take over the infected machine. Also, make sure your antivirus software is updated regularly as most modern antivirus solutions can catch Darkhotel before it causes too much damage on an infected machine.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion