Free Software Lets Anyone Create Ransomware in a Just Few Minutes
Ransomware was a big threat to PC users around the world in 2014 and although a few ransomware variants have made headlines this year, there could be a massive increase in the number of ransomware campaigns during the next several months thanks to a new, free tool available for anyone to download. This program, known as Tox, was created and released by a hacker who has yet to be identified. Essentially, Tox is a ransomware-as-a-service kit. While similar kits have been made available to wannabe hackers in the past, most of these kits cost money to get started. Tox, on the other hand, does not charge users for its service - at least not up front. Rather than charge an upfront fee for ransomware creation, the creator of Tox opted to offer the service for free; choosing instead to charge a 20% fee on any success ransom attempts created using Tox.
For those not familiar with the term, ransomware refers to malware that encrypts all files and folders on a computer. In most cases, these files (including pictures, music, documents, and third party applications) cannot be decrypted without the decryption key and this key is only made available to victims by paying the ransom. Although the amount of the ransom can vary, many popular strains of ransomware seen in the wild over the last few months demand upwards of $500. Some variants even penalize victims for not paying immediately by increasing the ransom amount if payment is not received within a day or two of infection. While many of the ransomware variants that have made headlines in recent months are easily detected by most modern antivirus solutions (with properly updated definitions), the new ransomware variant used in the Tox ransomware kit is previously undiscovered and its availability to the general public as a free service could signal the start of the largest global ransomware campaign in history.
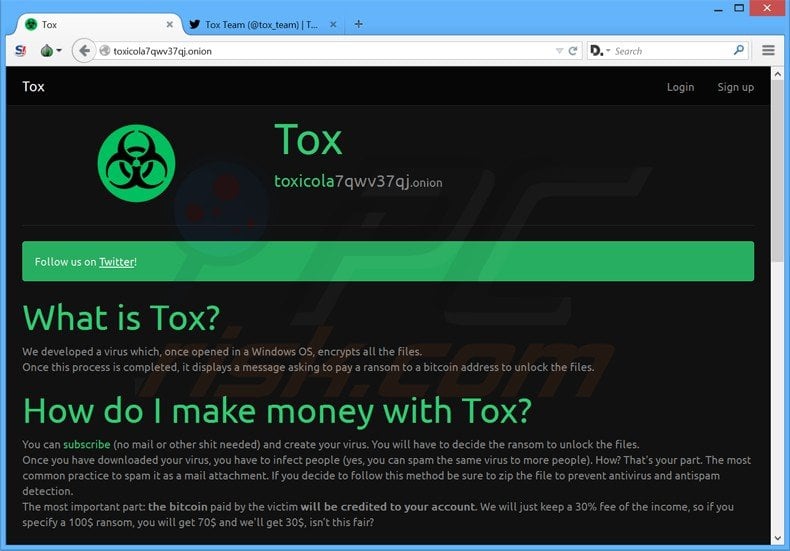
Between existing cybercriminals looking to expand illicit operations and novice script kiddies that want to try their hand at being a hacker without any programming or networking knowledge, there is no shortage of potential customers for the new malware kit. The malware kit runs on TOR and does not require any technical skill to use. In fact, security researchers from McAfee who discovered Tox, stated that the malware kit is designed in such a way that anyone can create and deploy ransomware in just three simple steps. Creating ransomware using Tox can be accomplished in just minutes by following a series of four simple steps.
1. Visit the Tox website and create a free account. The site does not require an email address or any other personal information that could tie the attack back to the user.
2. Once registered on the website, create ransomware by entering a desired ransom amount (must be at least $50).
3. Add a “Note” to the ransomware to let victims know they have been infected with ransomware and that personal files and folders will only be recoverable if the ransom amount is paid.
4. Finally, fill out a captcha and click on the “Create” button.
According to the report released by McAfee researchers, this easy-to-follow process creates an executable file (approximately 2MB in size) that is disguised as a .scr file. Users are able to distribute and install the ransomware as they want. The Tox site tracks installations and profits. All a Tox user needs to do is supply a Bitcoin address to receive payment (after Tox takes its 20% cut). Obviously, someone with little to no prior experience running a malware campaign will have difficulty infecting mass numbers of PCs unless they install it on a corporate network where they work, but the point is that a dangerous malware variant can be created in a matter of minutes without any prior programming experience and can be deployed around the world almost as fast. The most common way this ransomware can be distributed is via spam email attachments containing the .scr file. When a user clicks on the attachment, the ransomware is deployed and immediately goes to work encrypting all of the victim’s files and folders.
A more complex distribution system might include the use of drive-by download techniques. Even people without experience in this department can find a variety of exploit kits to bundle the ransomware in such as the Blackhole and Angler exploit kits. These exploits usually aren’t free, but just like Tox, little to no prior hacking knowledge is required to take advantage of these tools. So far, ransomware created using Tox has only been observed in the wild as a spam email attachment, but if Tox users really want to maximize the effectiveness of this attack, drive-by downloads and social engineering techniques could become more popular in the coming months as more people learn about this new malware creation tool. The fact that the malware creation tool is completely free to users – meaning no upfront financial risks are required to make ransomware – is likely to attract an entirely new customer base of people interested in making a few illicit dollars. To protect your PC from Tox ransomware, regularly backup important data, ensure you are running antivirus software that is regularly updated, refrain from opening any email or attachment from an unsolicited or unknown source, and follow safe Internet browsing practices. While some variations of ransomware can be decrypted without paying the ransom (Cryptolocker and CryptoWall for example), Tox ransomware appears to be impenetrable. In other words, if your PC is infected, you will be required to pay the ransom to recover your personal files and folders so the best course of action is to protect your PC from infection in the first place.
Update Jun 03 2015 - Developers of Tox ransomware decided to stop providing their rogue services and to sell their platform:
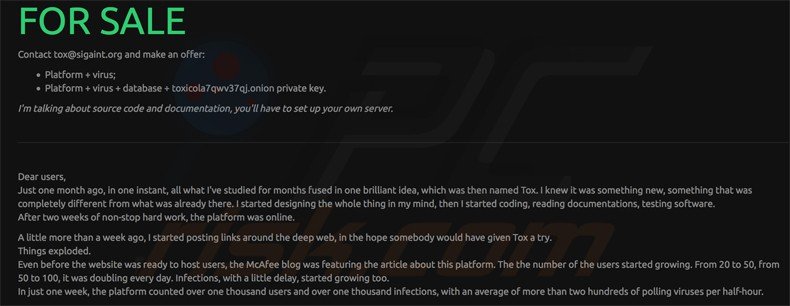
Dear users, Just one month ago, in one instant, all what I've studied for months fused in one brilliant idea, which was then named Tox. I knew it was something new, something that was completely different from what was already there. I started designing the whole thing in my mind, then I started coding, reading documentations, testing software. After two weeks of non-stop hard work, the platform was online. A little more than a week ago, I started posting links around the deep web, in the hope somebody would have given Tox a try. Things exploded. Even before the website was ready to host users, the McAfee blog was featuring the article about this platform. The the number of the users started growing. From 20 to 50, from 50 to 100, it was doubling every day. Infections, with a little delay, started growing too. In just one week, the platform counted over one thousand users and over one thousand infections, with an average of more than two hundreds of polling viruses per half-hour. Yesterday, 2nd June 2015, I decided to quit. Plan A was to stay quiet and hidden. Well, I think I screwed up. It's been funny, I felt alive, more than ever, but I don't want to be a criminal. The situation is also getting too hot for me to handle, and (sorry to ruin your expectations) I'm not a team of hard core hackers. I'm just a teenager student. Some have said I think out of the box, others said I'm a skid who just developed the worst ransomware ever. I think that both opinions may be true, but one thing is objectively true: with Tox, I opened a door for a whole new way of thinking. I'm sure that others will try to replicate what I did. Not just for bad reasons, maybe somebody (maybe myself?) will find out how to do something good based on all this. One last thing: if I really was a team of hard core hackers, with time and resources, this would have become one the greatest viruses ever. In these days, in the chat, people helped me testing and debugging the virus, but the most interesting part is that they suggested me how to improve it. I don't think that such a great brainstorming has ever happened in the process of designing a virus. Users were spurred to help me improving the platform, for their own good. What's next? I'm selling all this out because even if I didn't, somebody would have developed his own Tox-like version. I'm asking my users to be patient, I'm not going to scam you. In a few days I'll ask you a bitcoin address in the case somebody pays some of your ransoms. I'll forward you your part. If nobody's going to buy the database, in one month I'm releasing the keys, and victims will have their files automatically unlocked. My choices are not linked to the recent external events, I pondered all these choices on my own, for my own good.
Depending on the success of this model, it’s possible that many similar services will be made available in the second half of 2015.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion