Duqu 2.0: A Powerful Worm Targeting Internet Security Companies, Iran Nuclear Talks
A powerful computer worm known as Duqu 2.0 has been recently discovered in the networks of three hotels used to host the P5+1 negotiations. These negotiations included representatives from the US, UK, France, Germany, China, and Russia and were created to discuss Iranian nuclear capabilities over the last year and a half. Although the official Kaspersky report does not name the hotels in question, it is believed that this worm was deployed by a state-sponsored Israeli campaign in an attempt to gather sensitive intelligence as it relates to the nuclear talks and anything else of relevance that the worm was able to gather in the process. Although a direct link to an Israeli sponsored campaign cannot be proven at the time of this writing, it’s worth pointing out that just this past March, the US Government accused Israel of spying on the negotiations and using the intelligence gathered to persuade Congress to undermine the talks.
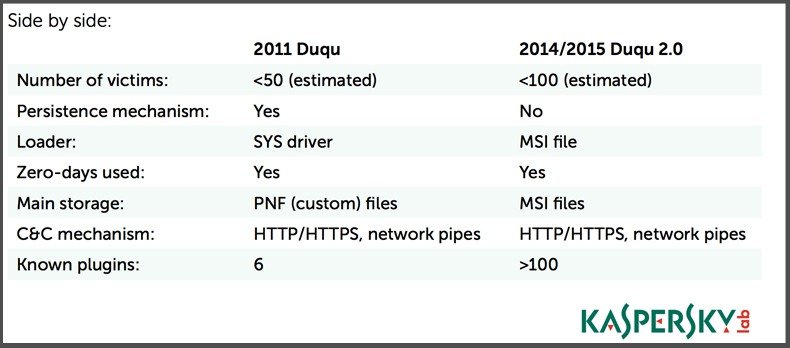
Another sign that Israel was involved with the deployment of Duqu 2.0 is that Duqu is an evolved version of Stuxnet, a powerful worm that was deployed as part of a joint intelligence gathering mission between the US and Israel. Duqu was first discovered by CrySyS Lab in 2011 when it was used to create a backdoor into systems in Hungary, Indonesia, Austria, Sudan, Iran, and the UK. Even then, evidence suggests that the deployment was meant to gather intelligence about the Iran nuclear program.
Even in 2011, Duqu was ahead of its time as it was one of the first malware variants capable of hijacking digital certificates to evade security solutions by signing malicious files using trusted credentials. That said, the latest version of Duqu is even more advanced than its predecessor.
The group behind this attack did everything possible to avoid detection including many unique and never-before-seen evasion technique. Duqu 2.0 also leaves practically no trace of its presence on a system–often making it difficult for security analysts to pinpoint exactly what information was compromised on an infected system. Duqu 2.0 leverages three zero-day exploits (an impressive feat that indicates a large development budget). Once the system has been exploited, Duqu 2.0 elevates its privileges to domain administrator before spreading throughout the network using MSI files (commonly used by system admins when deploying software to remote Windows computers within the network). Since Duqu doesn’t create or modify any disk files–staying hidden within system memory instead–detecting Duqu 2.0 is nearly impossible (until it’s too late).
According to Costin Raiu of the Kaspersky Global Research and Analysis Team, “The people behind Duqu are one of the most skilled and powerful advanced persistent threat groups and they did everything possible to try to stay under the radar.” Interestingly enough, Duqu 2.0 was first discovered on Kaspersky’s own systems. As of this writing, the company reports that no key systems were compromised, although it’s worth pointing out that Duqu is so evasive that more Kaspersky systems could have been infected that the cybersecurity company is simply not aware of at this time. What Kaspersky does know, however, is that the hackers behind this attack installed Duqu 2 on Kaspersky’s systems in an attempt to spy on Kaspersky Lab technology, internal processes, and ongoing research projects. Essentially, the hackers wanted to learn about the cybersecurity company’s proprietary technology as it relates to discovering and analyzing advanced persistent threats (APTs) as well as any information pertaining to ongoing investigations into advanced targeted attacks. Likewise, it isn’t clear what Duqu was used for at the hotels in question.
Some security researchers think that the infected computers were used to control cameras, phone systems, and microphones within the hotels as a way to spy on the negotiations.
What is clear is that the attack on Kaspersky Lab (known within the cybersecurity community as one of the leaders in APT detection and prevention) represents a frightening milestone in the cyber-arms race. Attacks against cybersecurity companies are historically rare due to the high risks assumed by the hacking group behind the attack. The fact that this malware campaign directly targeted Kaspersky Lab in addition to the hotels used for the P5+1 talks indicates a sophisticated cybercriminal group that isn’t afraid to take international cybersecurity companies head-on in its attempt to extract critical information. Trend Micro has already confirmed that the latest version of Duqu exhibits all the signs of a nation sponsored attack; summed up by Head of Security Research Rik Ferguson when he stated “It certainly has all the hallmarks of a nation-state attack and reuses much from its ancestor the original Duqu, but in new and improved ways.”
Furthermore, Kaspersky estimates that the costs associated with developing Duqu 2.0 come in at around $50 million. Cybercriminals after financial gains do not usually have access to enough funds to support the development of such a complicated malicious framework. While the average consumer isn’t likely to be directly impacted by Duqu 2.0, the research and development behind the creation of Duqu 2.0 invariably filters down to more common and widely spread cybercrime campaigns.
The creators of Duqu 2.0 meant for the malware to gather sensitive intelligence data but criminals cold just as easily use the same techniques to steal financial information from consumers (much as hackers used lessons learned from Stuxnet to create malware strains designed to steal banking information from victims).
To protect your PC from Duqu 2.0, make sure a reputable antivirus product is installed, ensure Windows is updated regularly (including the Patch Tuesday update from June 9), and always reboot all networks computers at the same time to prevent the malware from surviving on one machine and re-infecting the others. Remember that Duqu 2.0 relies completely on zero-day exploits to access the kernel meaning that your PC is only at risk if you fail to update the OS on a regular basis.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion