New JavaScript Threats Discovered in the Wild, Threaten to Take Control of PCs
JavaScript is still heavily used as a scripting language for interactive website effects. In fact, JavaScript is still number 8 on the Top 10 coding languages this year despite the fact that both JavaScript and Java, its proverbial big brother, are heavily leveraged by hackers to distribute malicious software and as Trojan attack vectors. It’s no secret that any active content solution can leave your PC vulnerable to attack and the two JavaScript-based exploits described below are no exception. Despite the potentially tragic consequences of infection by either of these malware campaigns, it’s worth pointing out that both are easily blocked with basic PC maintenance such as automatic updates and a current antivirus software solution. Recently, Threatpost reported that a flood of spam emails have been detected that contain a .JS attachment filled with obfuscated JavaScript code.
Within this obfuscated code is a downloader that contacts multiple domains as a way to install Kovter or Miuref, both notorious click-fraud malware variants. To make these spam emails look legitimate and to propagate a feeling of urgency, most of these messages are about bogus court appearances, toll charges, and delivery notices. Kovter is a Trojan specifically designed to exploit advertising campaigns.
Often referred to as click or advertising fraud, the Trojan is used to hijack Web browser sessions in order to simulate a victim’s machine clicking on advertisements to generate advertising revenue for the hackers behind the malware campaign.
Miuref is similar to Kovter in that it is also specifically designed to create advertising revenue for the hackers behind the campaign by creating fake ad clicks that are generated from the victim’s PC. Once installed via a spam email attachment, Miuref downloads and installs additional components including the encrypted payload of the Trojan. This file can be identified because it has a specific file extension ending in one of the following: “.dat”, “.lck”, “.idx”, and “.txt”. Miuref modifies the Windows registry to ensure that the Trojan runs every time the victim logs onto the infected PC. If either Firefox or Chrome are installed on the machine, Miuref also covertly installs an extension to one or both of the browsers.
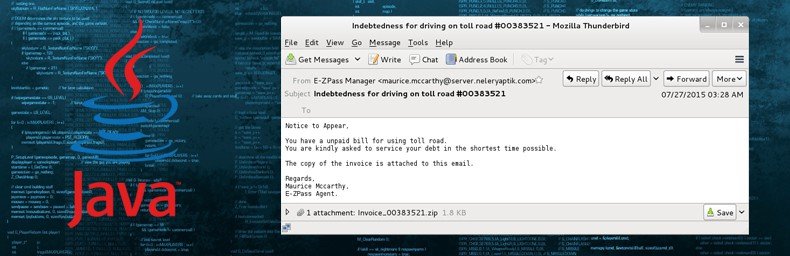
Although this campaign may work occasionally, it is relatively easy for antispam programs to detect and block attachments containing JavaScript, just as these same programs block messages that contain .exe attachments. In other words, although this spam campaign is a threat, it is a threat that is easily mitigated and shouldn’t be a concern for any PC user with updated antivirus software installed. Once installed in Internet Explorer, Firefox, and/or Chrome, Miuref injects itself into hidden browser processes to perform hidden clicks that lead to online advertisements. In some cases, these hidden clicks also lead to compromised websites that serve additional malware via drive-by download attacks that target known vulnerabilities in popular Web browser plug-ins including Java, Adobe Flash Player, and Microsoft Silverlight. Miuref is also capable of hijacking and replacing search engine results. In Internet Explorer, Miuref directly connects to a remote server to retrieve the redirection URLs. In Firefox and Chrome, the extensions that have already been installed by Miuref are used to redirect any search to a website of the hackers’ choosing. Windows Registry entries that indicate a Miuref infection are typically found in subkey HKCU\Software\Microsoft\Windows\CurrentVersion\Run and sets values. A typical Miuref registry entry might look like: “Regsvr32.exe %LOCALAPPDATA%\Arltworks\MozSvcs64.dll”. Another, more dangerous, JavaScript exploit has also been discovered.
The Rowhammer vulnerability is a serious malware threat that can be used to gain kernel privileges on multiple systems. This exploit relies on the physical property of specific dynamic random access memory (DRAM) chips.
Basically, when these DRAM chips are placed in close proximity in an attempt to increase capacity while decreasing size, hackers can force electrical interactions between cells and cause unwanted bit flips. This vulnerability gets its name because when the same memory location is accessed repeatedly (known as hammering a row of chips), targeted privilege escalation can be obtained. Rowhammer was first discovered in March by a team of Google researchers but at the time the attack was considered a minor threat because it required native code, physical access to the target, and special instructions – all requirements that even the most adept hackers would have a hard time securing to execute this attack.
Recently, however, researchers from France and Austria successfully packaged Rowhammer into a .JS file that bypasses the aforementioned requirements meaning that, at least in theory, the Rowhammer attack could be launched against multiple targets from a single compromised website. In a research paper recently published by the team responsible for packaging Rowhammer into a JavaScript delivery package, it is made apparent that this version of Rowhammer has only been tested in sandboxes that defend against the retrieval of virtual addresses. That said, it is still possible to determine portions of the physical address and force bit flips.
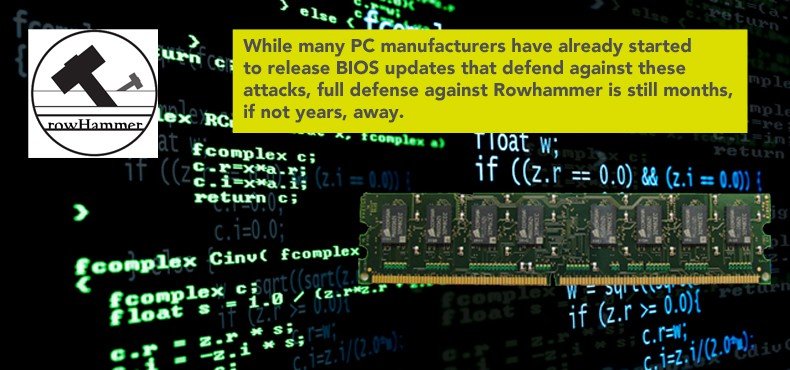
While many PC manufacturers have already started to release BIOS updates that defend against these attacks, full defense against Rowhammer is still months, if not years, away and that doesn’t even take into consideration the fact that this exploit can also be used against victims via common Web browsers such as Google Chrome, Mozilla Firefox, and Microsoft Internet Explorer.
These threats, especially Rowhammer, are nothing to scoff at although protecting your PC from either of these threats is relatively simple. First, never open emails or attachments from unsolicited sources even if the emails seem legitimate at first glance. As always, ensure the OS and all third party applications are regularly updated. Disable any Web browser plug-ins that are not absolutely necessary and keep antivirus software updated with the latest virus definitions. Both of these attacks rely on known exploits within the Windows OS and Web browser plug-ins making them easy to defend against with basic PC maintenance and security.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion