Beneficial Malware? It’s a Thing…
Traditional malware is slowly becoming extinct as malware creators have realized that targeting routers and other Internet-connected devices (the Internet of Things) is more successful and in some cases, more financially lucrative as well. Routers and IoT devices are easy to infiltrate and because there is no antivirus solution available for these devices, detection by the average consumer is extremely unlikely. Once malicious actors have infected a router, the device can be used to launch DDoS attacks or to spoof legitimate websites as part of a phishing campaign. In fact, the highly publicized attacks of the Sony PlayStation and Xbox Live online gaming platforms were both carried out using a botnet created from routers that had been infected with a special malware package designed to leverage vulnerabilities in the embedded firmware of affected devices. Despite all the bad press that malware is subjected to on a daily basis, researchers from Symantec recently discovered a new strain of malware that targets routers as well as other embedded devices including many smart home automation products.
What makes this malware strain unique is that it was designed to protect these devices from traditional malware attacks. The vigilante code is installed without the knowledge or consent of the individual user, which is why the program is still considered malware, but the program is actually designed to harden routers and other vulnerable devices against malware attacks designed for nefarious purposes. This malware, which has been dubbed Linux.Wifatch by Symantec researchers, was first discovered last year when a security researcher noticed that his router was acting strangely. Like other forms of malware, Linux.Wifatch had turned his router into a zombie - part of a large P2P botnet.
At the time, the researcher was able to identify at least 13,000 other devices infected with the same malware strain. Since that time, the malware has become rather famous and is also referred to by names such as Zollard and Reincarna within the IT security community.
Upon closer inspection of this malware strain, it became apparent that this botnet, although extremely sophisticated, wasn’t like the botnets commonly written about on this blog. Rather than being used to conduct DDoS attacks or to distribute other malware variants, Linux.Wifatch is designed to pass malware threat updates between infected nodes as it relates to notorious malware families that specifically target embedded devices. Once this malware strain has been successfully installed on an embedded device, it immediately gets to work buy eradicating any malware infections found on the device before making changes to security settings to make the device less vulnerable to attack.
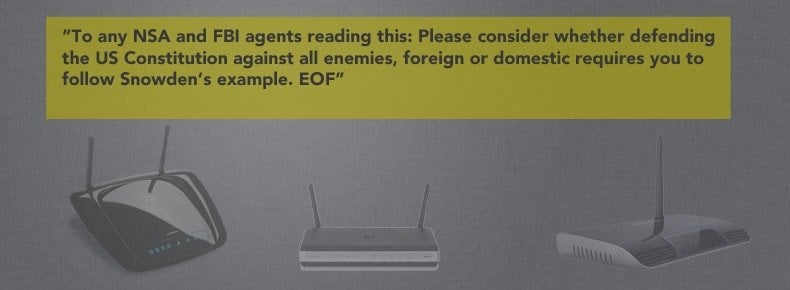
The creators of this malware strain even went so far as to write helpful messages into the code that display tips to users who may be engaging in activities that could put the device at risk such as using telnet. Other signs that point to the benevolent nature of Wifatch include a message to law enforcement officials found in the source code and an exploit module for Dahua DVR CCTV systems. The message to law enforcement reads: “To any NSA and FBI agents reading this: Please consider whether defending the US Constitution against all enemies, foreign or domestic, requires you to follow Snowden’s example. EOF” This message is a reference to the email signature of GNU guru Richard Stallman and indicates malware creators that aren’t trying to harm anyone with their programming creation.
As far as the CCTV exploit is concerned, Wifatch is designed to reboot the camera systems of these systems once per week. The popular theory as to why this exploit was included is that the malware is unable to protect this particular device from certain malware threats and that by rebooting the system regularly, the router is given a clean slate after each reboot (embedded device malware is not persistent and must be reinstalled after a reboot in most cases).
The author(s) of Wifatch provide even greater transparency by not obfuscating the source code. In fact, there are numerous debugging messages contained in the source code that make it easier for security researchers to follow the behavior of the program.
This is exactly the opposite of most malware strains where great care is taken by the malware authors to prevent security researchers from debugging the malware at all. Despite the seemingly benevolent nature of this particular malware strain, Symantec warns that Wifatch is still malware because it is installed without the end users consent and it contains numerous backdoors which the creators of Wifatch could use to carry out a malicious attack if so inclined. That said, researchers from Symantec have been watching this botnet for months and have yet to detect a single action that could be construed as malicious. Furthermore, the backdoors used by the malware to communicate with other nodes is cryptographically signed – meaning that the program can only get commands from the genuine author. This significantly reduces the likelihood of the malware being hijacked by a malicious third party with sinister intentions.
While having Wifatch installed on your router isn’t necessarily a bad thing, it is not a persistent threat. This means that simply resetting the router will remove Wifatch from the device. Interestingly enough, Symantec’s recommendation for preventing infection is exactly the same as the recommendation given by the malware itself: “Update your device firmware and change the default passwords.”
It’s certainly rare to have the words malware and beneficial in the same sentence, but Linux.Wifatch is a perfect example of this very phenomena in the wild. While it is still unclear who is behind the creation of Wifatch, the PC security community is glad that someone is looking out for these devices as they are being targeted with more regularity than ever before and the average PC user is not capable of identifying an embedded device infection in the first place. The Internet is a safer place because of Wifatch.
Share:

Karolis Liucveikis
Experienced software engineer, passionate about behavioral analysis of malicious apps
Author and general operator of PCrisk's News and Removal Guides section. Co-researcher working alongside Tomas to discover the latest threats and global trends in the cyber security world. Karolis has experience of over 8 years working in this branch. He attended Kaunas University of Technology and graduated with a degree in Software Development in 2017. Extremely passionate about technical aspects and behavior of various malicious applications.
PCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
DonatePCrisk security portal is brought by a company RCS LT.
Joined forces of security researchers help educate computer users about the latest online security threats. More information about the company RCS LT.
Our malware removal guides are free. However, if you want to support us you can send us a donation.
Donate
▼ Show Discussion